Frida is a dynamic and flexible instrumentation tool. This powerful application can inject into running processes across multiple platforms: Android, iOS, Windows, Mac y QNX.
The utilities of this tool are varied, from performing tests without altering the code, modifying the flow of execution of a program or simply used to observe the state of processes within an application. These utilities we will see them oriented to the search for vulnerabilities and as support for other tasks within the pentesting of Android mobile applications.
As an introduction to the tool the first step will be to create the right environment for the practice.
-
- Android device with root access or emulator
- If you don’t have root access you can follow this tutorial
- As an emulator i recommend Genymotion.
-
- ADB tools in our PC
-
If we have used the Android SDK we will have it, but simply install depending on our distribution or operating system.
apt install android-tools-adb
-
If we have used the Android SDK we will have it, but simply install depending on our distribution or operating system.
-
- Frida installed in our PC
-
For this, Python and its pip
packages utility will be necessary first of all.pip3 install frida-tools
-
For this, Python and its pip
-
- Frida-server in our Android device or emulator
-
For this it will be necessary to look for the binary according to our requirements
https://github.com/frida/frida/releases -
Once we have the binary we must place it in some folder in our device and execute it as root, for this we will use adb with the mobile or the emulator connected.

adb devices -l adb push frida-server /data/local/tmp/ adb shell his chmod +x /data/local/tmp/frida-server /data/local/tmp/frida-server
-
For this it will be necessary to look for the binary according to our requirements
Requirements:
Once all our requirements are met and we have our frida-server on our Android device running we can start with a series of introductory tests using an application that we have developed with different basic exercises.
You can get the app in here: APK
To be able to understand the operation and obtain the names of methods, classes and variables in this case we will use a decompiler that will facilitate the tasks. In this case we will use Jadx in its version with graphical interface.
Exercise 1- Call me!
To access exercise 1 press the button corresponding to exercise “Call me”. The purpose of this exercise is to use the functionality of Frida that allows us to call a method of a class.
Observing the source code we can see inside the activity Callme a series of functions, among them we find call_me_win().
Within the function the first flag is generated and will be shown to the user.
Accessing the application in the mobile to exercise 1 we see that nothing happens. If we read the activity code we can see that the function is never called to obtain the flag.
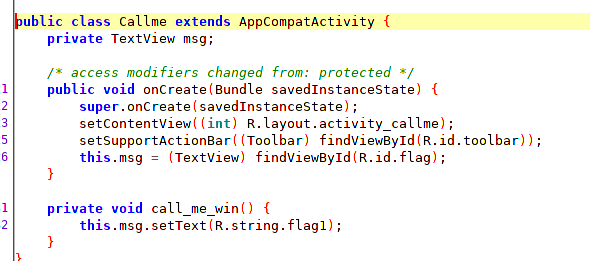
We will develop the javascript code that will look for an instance of the activity using the Java.choose method and we will work on it, the activity must be started, otherwise we will not find the activity.
Java.perform(function () {
Java.choose('com.ironhackers.androidlab.Callme', {
onMatch: function(instance) {
Java.scheduleOnMainThread(function () {
instance.call_me_win();
});
},
onComplete: function() {}
});
});
Once our javascript code is developed, we proceed to execute Frida on our PC.
frida -U --no-pause -l callme.js com.ironhackers.androidlab
As we can see we have obtained the flag!
Exercise 2- AlwaysTrue
The purpose of this exercise is to skip a function that performs a series of checks.
Observing the source code we can see inside the activity Always True that at the beginning a series of methods will be called to obtain the flag.
If we access the exercise in the application itself we will see that it returns an error message. If we read the activity code we can see that the flag is never shown because it calls a function that will make some impossible checks.
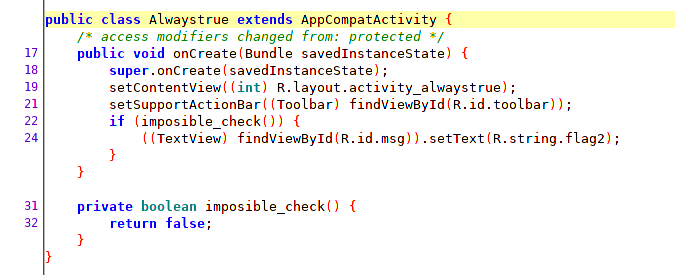
For this exercise we will overwrite the method impossible_check using the binding imposible_check.implementation = function () that returns a boolean so that it is always true. In this case we will execute the code and later we will open the activity since we do not use any instance.
Java.perform(function(){
var alwaystrueactivity= Java.use('com.ironhackers.androidlab.Alwaystrue');
alwaystrueactivity.impossible_check.implementation = function () {
return true;
}
});
Once our javascript code is developed we proceed to run Frida on our PC.
frida -U --no-pause -l alwaystrue.js com.ironhackers.androidlab
As we can see we have obtained the flag by overwriting the implementation of a method.
Exercise 3- CreateMe
In this activity we see a button for the purchase of ironcoins but pressing the purchase button tell us that we have no money.
Observing the code from the decompiler we see that it uses an object Person that contains a variable type Wallet but that in no case is instantiated by what will fail the verification of money.
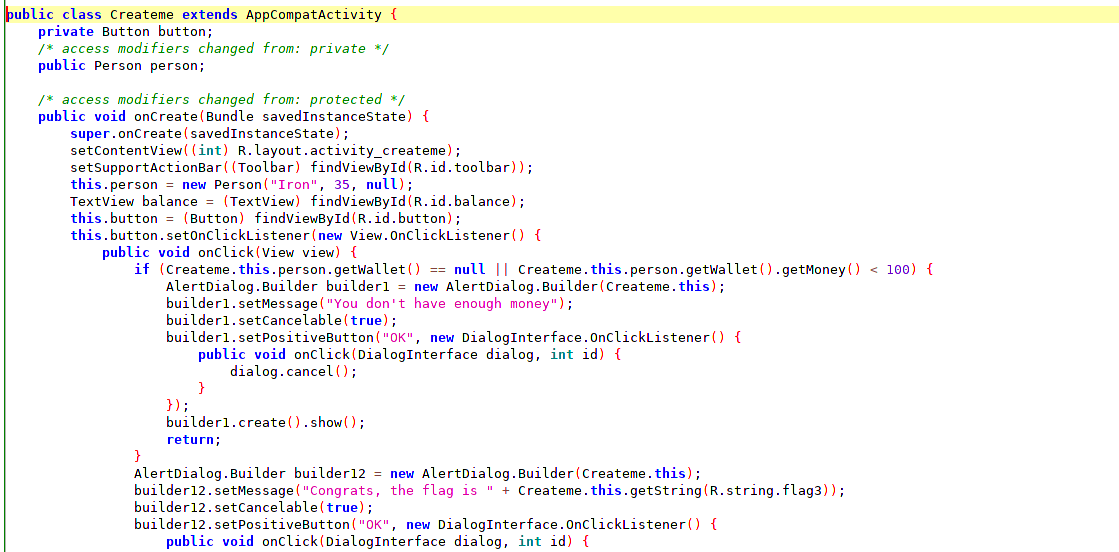
In this case we will need to create an object Wallet and load it with the Setter of the object person obtained through person.value, which we extract from an instance obtained with the search of Java.choose. In this way we can skip the check.
Java.perform(function(){
var wallet=Java.use("com.ironhackers.androidlab.Wallet");
Java.choose('com.ironhackers.androidlab.Createme', {
onMatch: function(instance) {
instance.person.value.setWallet(wallet.$new(100));
},
onComplete: function() {}
});
});
Once our javascript code is developed we proceed to run Frida on our PC.
frida -U --no-pause -l createme.js com.ironhackers.androidlab
As we can see we have obtained the flag and we have learned that we can create objects, call functions, etc through the binding of languages of Frida – Java.
Exercise 4- Sniff
In this activity we can see a text box and a button to check. First we must study the code through the decompiler to understand the objective.
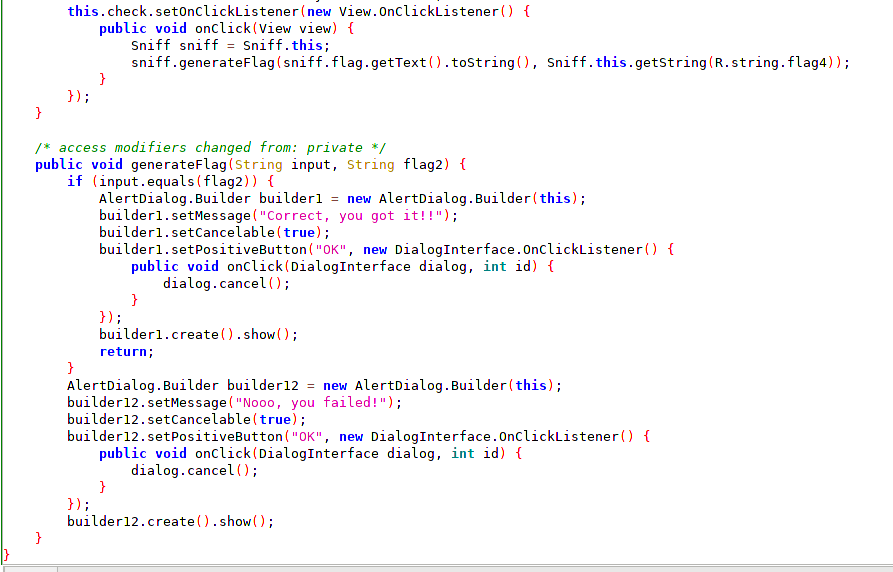
The goal is to enter the correct key in the text box for the flag to be displayed.
To achieve the objective we will capture the arguments that are passed by the function generateFlag and thus we will obtain the key to introduce in the text box.
Java.perform(function(){
Java.choose('com.ironhackers.androidlab.Sniff', {
onMatch: function(instance) {
instance.generateFlag.implementation = function (arg0,arg1) {
console.log("arg0 -> "+arg0+" | arg1 -> "+arg1);
this.generateFlag(arg0,arg1);
}
},
onComplete: function() {}
});
});
Once our javascript code is developed we proceed to run Frida on our PC.
frida -U --no-pause -l sniff.js com.ironhackers.androidlab
We can work with the arguments of the functions as if we were working in the native language. Once we have obtained the key of argument 2, we introduce it and we will obtain the flag.
This has been the introduction to Frida with a very basic exercise in which we could directly obtain all the flags of the decompiler without much difficulty but the good way is to do it using Frida.
The variety of uses is open to everyone, in the next part we will use Frida in an pentesting of a mobile application.
Tools: Frida docs, frida-tools Python, Jadx-GUI

 Español
Español





Leave a Reply