This is the first post solving HackTheBox challenges. We’re going to try to solve most of the challenges removed from the platform and this time it’s about a web challenge called HDC.
It’s a simple level challenge, but it will help us to see how the challenges we will face in the next days are. In it we will have to bypass a login page and finally, with the help of the ZAP Intruder, find the flag.
My nick at ‘HackTheBox’ is: ‘https://www.hackthebox.eu/home/users/profile/25205’. If you have any proposal or correction don’t hesitate to leave a comment, so we all learn.
Statement
We believe that a certain individual is using this website for shady purposes. Can you find out who it is and send them an email to check it out, using the website’s functionality?
Note: The flag is not an email address.
Solution
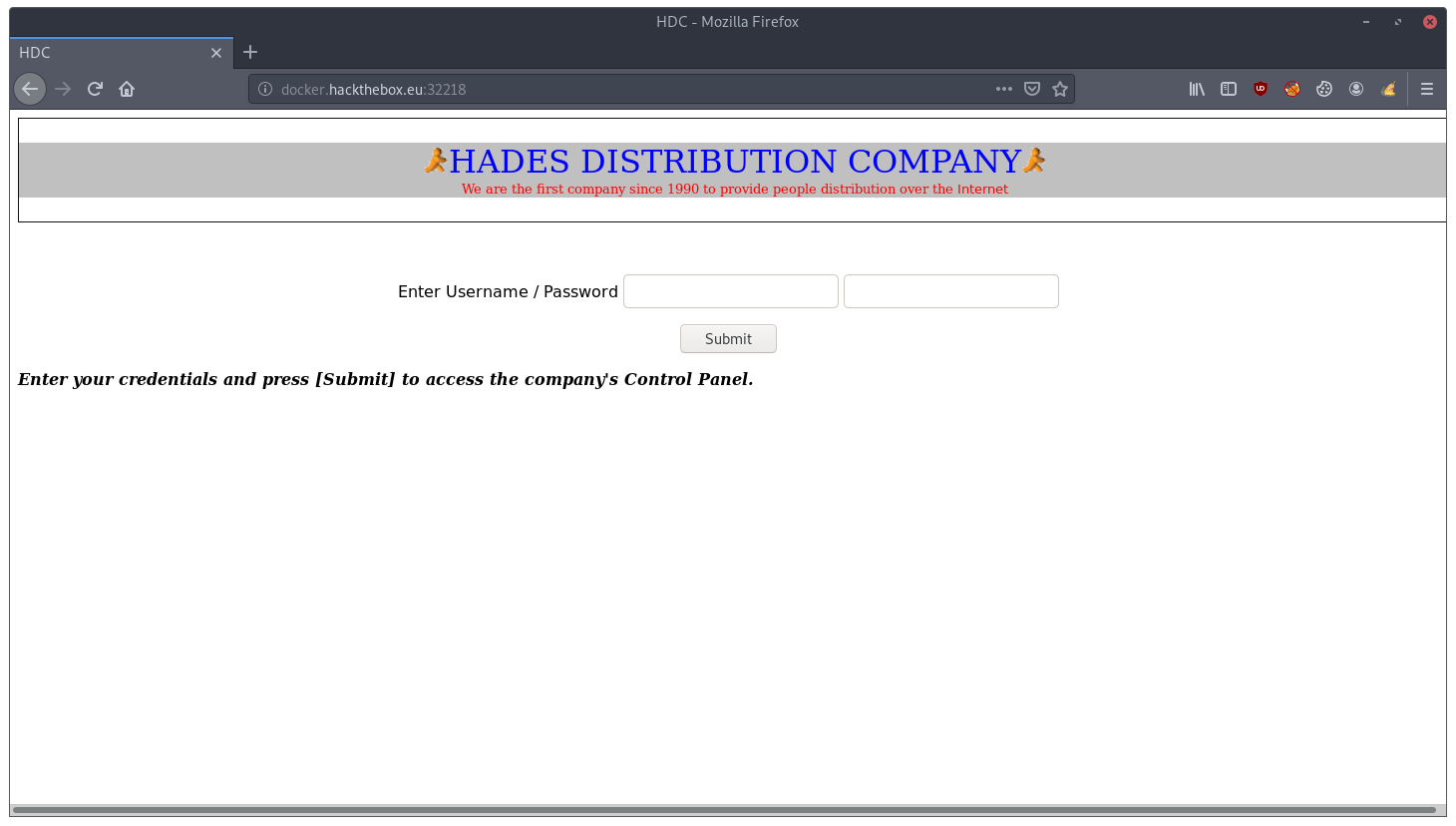
First we open the website in the browser:
Let’s review the source code:
[...]
<script src="jquery-3.2.1.js"></script>
<script src="myscripts.js"></script>
[...]
<form id='formaki' name='formaki' action="./main/index.php" method="post">
<p align="center">Enter Username / Password
<input type="text" name="name1" size="20">
<input type="text" Name="name2" size="20">
</p>
<p align="center">
<input type="hidden" value= name="name1">
<input type="hidden" value= name="name2">
<input type="button" value="Submit" onclick="doProcess()"/>
</p>
</form>
[...]
The javascript of the files “myscripts.js” and “jquery-3.2.1.js” are included. Now we check the code of “myscripts.js”:
function doProcess()
{
document.forms["formaki"].submit();
}
The function doProcess makes submit in the form. Let’s find out what .submit() does:
The submit method submits the form (same as clicking the Submit button).
As you can see, it does the same as when you click on the button, let’s look if in the jQuery there is any doProcess() function:
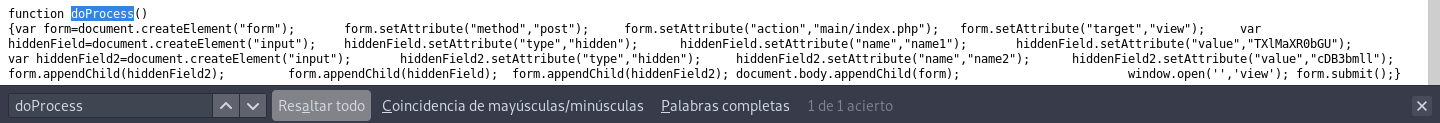
function doProcess() {
var form = document.createElement("form");
form.setAttribute("method", "post");
form.setAttribute("action", "main/index.php");
form.setAttribute("target", "view");
var hiddenField = document.createElement("input");
hiddenField.setAttribute("type", "hidden");
hiddenField.setAttribute("name", "name1");
hiddenField.setAttribute("value", "TXlMaXR0bGU");
var hiddenField2 = document.createElement("input");
hiddenField2.setAttribute("type", "hidden");
hiddenField2.setAttribute("name", "name2");
hiddenField2.setAttribute("value", "cDB3bmll");
form.appendChild(hiddenField2);
form.appendChild(hiddenField);
form.appendChild(hiddenField2);
document.body.appendChild(form);
window.open('', 'view');
form.submit();
}
In the function there are some credentials: TXlMaXR0bGU:cDB3bmll with which we access the platform.
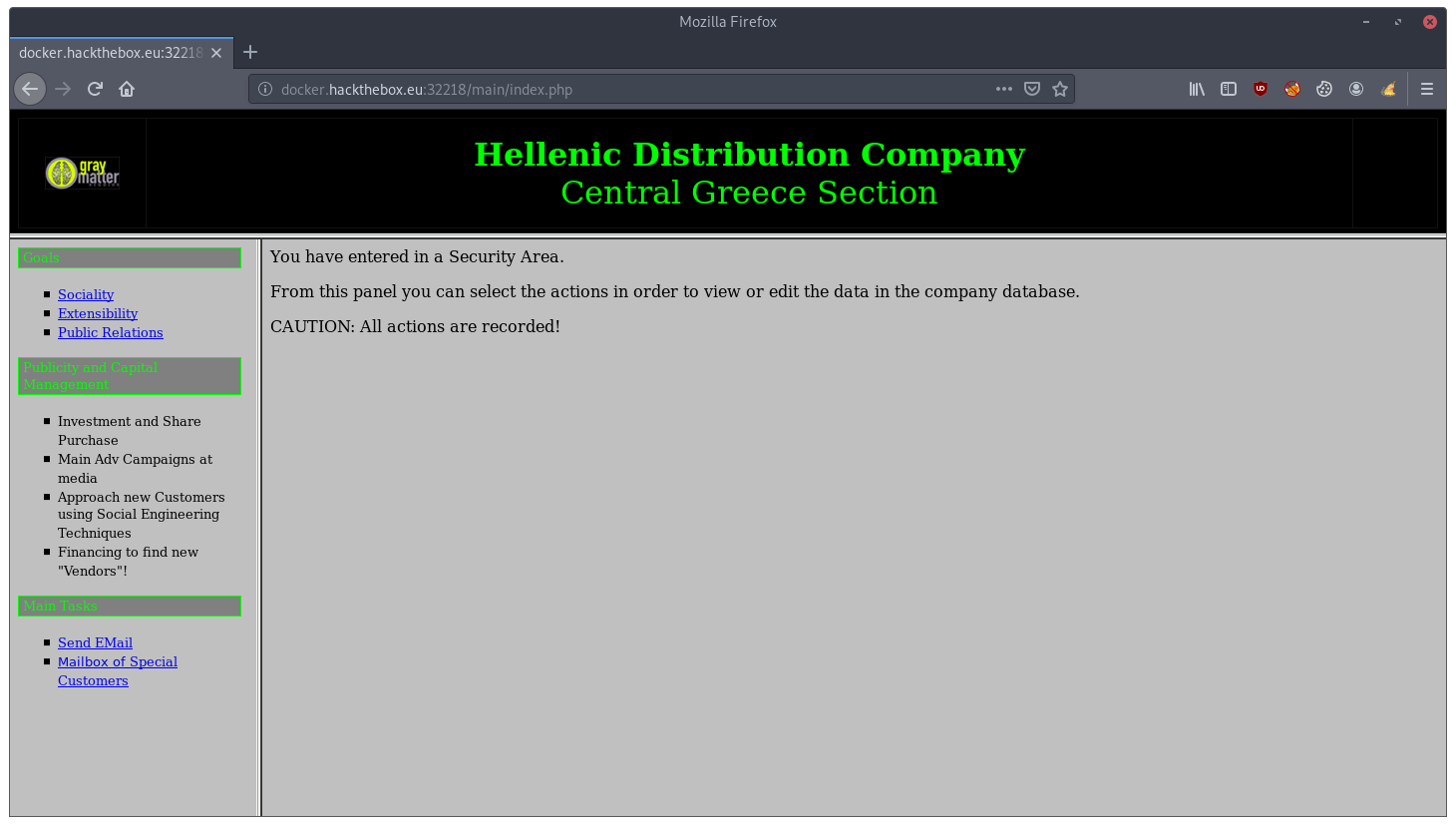
In this portal we find two tasks: “Send EMail” and “Mailbox of Special Customers”.
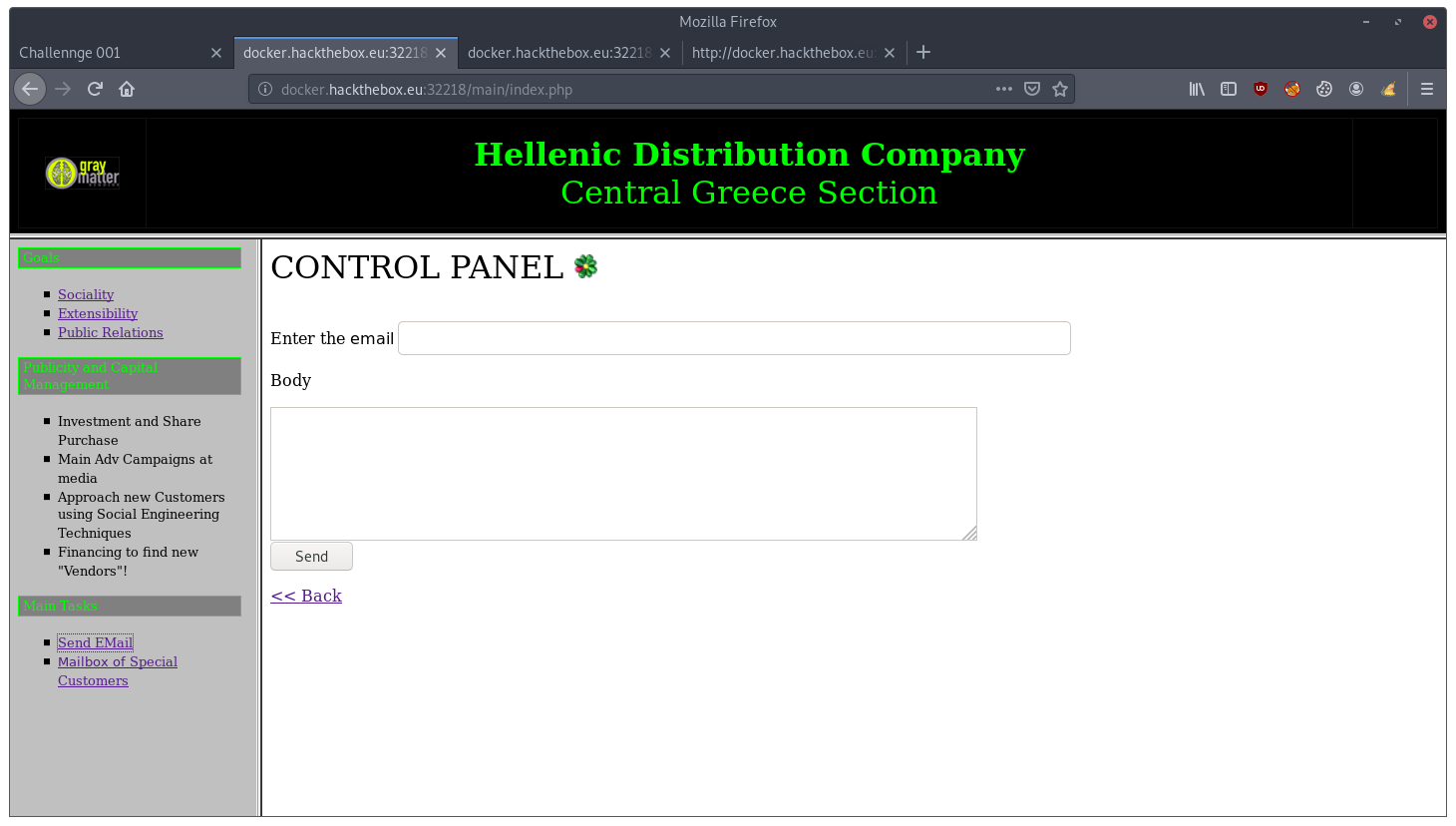
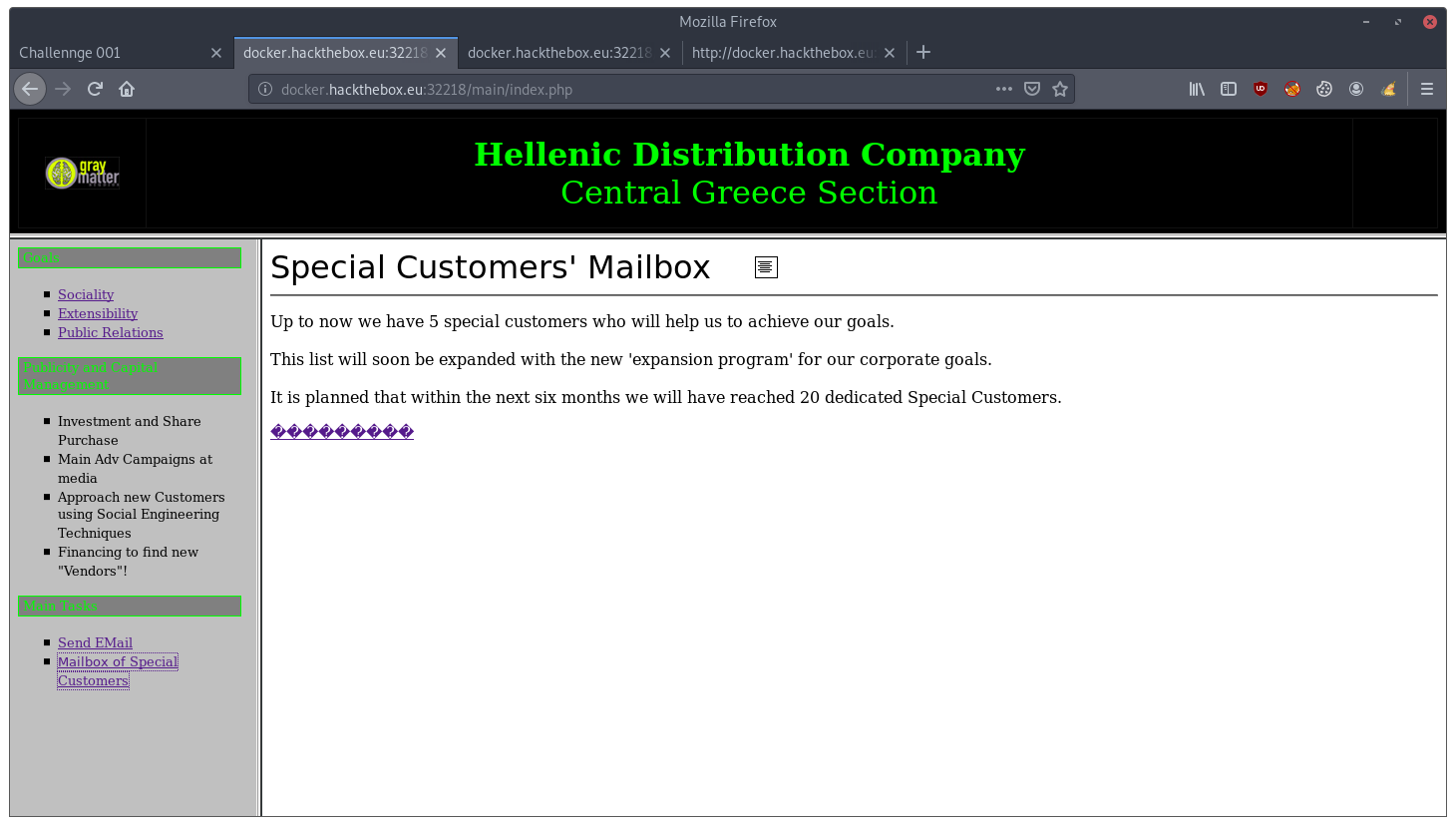
In the code of the second one we found something interesting:
</head><body><font size="6"><span lang="en-us">Special Customers' Mailbox</span></font><b><font size="6"> </font></b> <img src="./secret_area_/mails.gif" width="21" height="20" border="1"><hr><p> </p> <p>Up to now we have 5 special customers who will help us to achieve our goals.<br> <br> This list will soon be expanded with the new 'expansion program' for our corporate goals.<br> <br> It is planned that within the next six months we will have reached 20 dedicated Special Customers.<br> </p> <p><span lang="us"><a href="main.htm">���������</a></span></p>
The image mails.gif is in the directory /secret_area_, let’s see if there is something else:
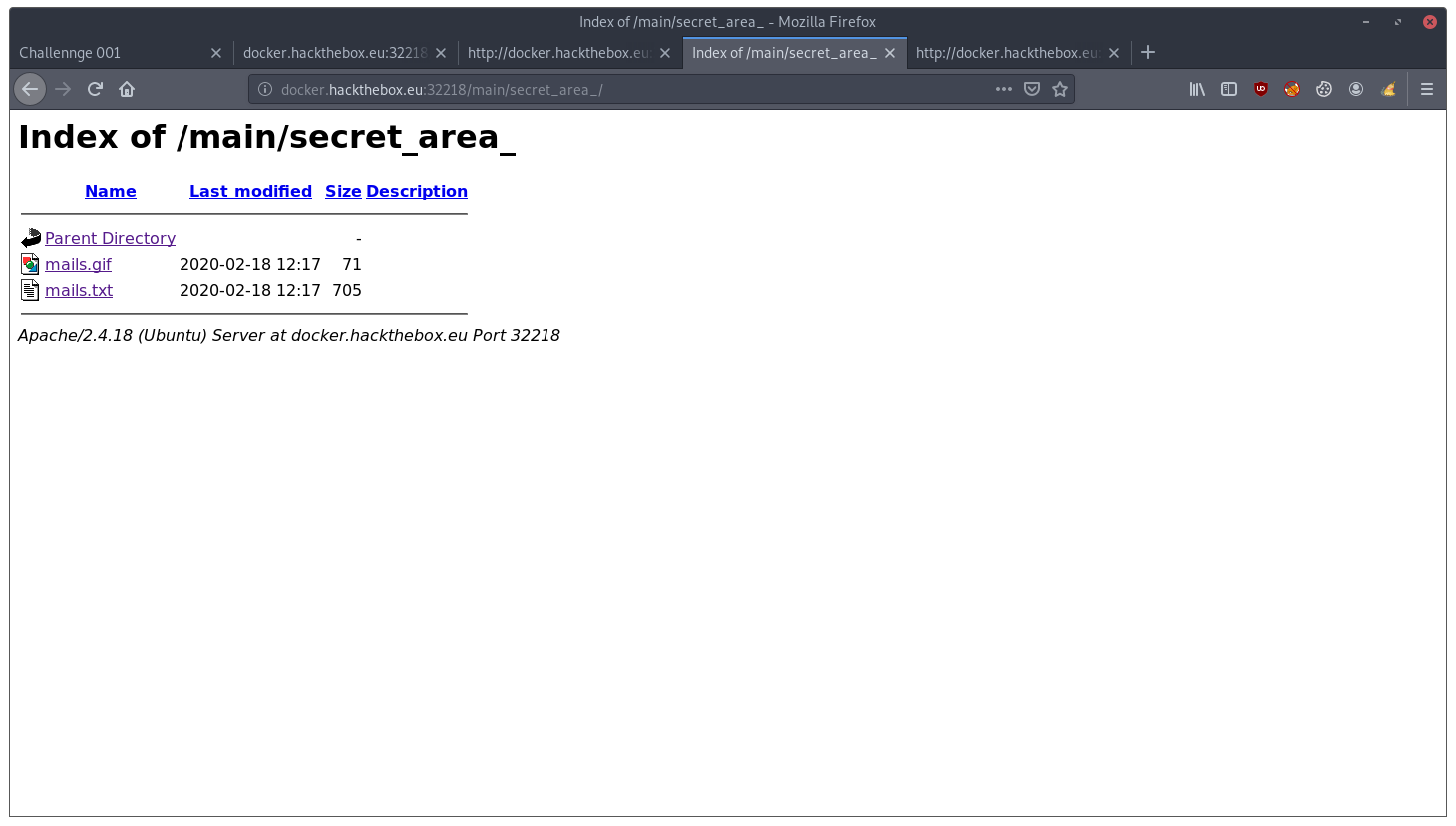
In mails.txt we find:
All good boys are here… hehehehehehe!
—————————————-
Peter Punk [email protected]
Nabuchodonosor [email protected]
Ilias Magkakos [email protected]
Nick Pipshow [email protected]
Don Quixote [email protected]
Crazy Priest [email protected]
Fishroe Salad [email protected]
TaPanta Ola [email protected]
Laertis George [email protected]
Thiseas Sparrow [email protected]
Black Dreamer [email protected]
Callme Daddy [email protected]
Aggeliki Lykolouli [email protected]
Kompinadoros Yannnnis [email protected]
Serafino Titamola [email protected]
Joe Hard [email protected]
Bond James [email protected]
Endof Text [email protected]
Now that we have the email list, let’s go over the statement: “Can you find out who he is and send him an email to check it out, using the functionality of the website?”
It seems that we have to use the functionality of ‘Send EMails’ with the addresses in this list.
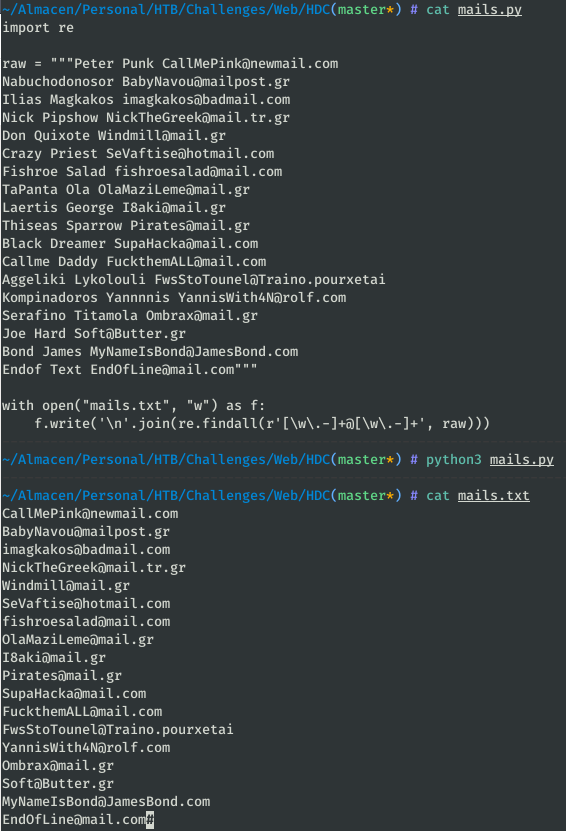
With a Python script we get the list of the emails and write it in a file to use in the Intruder of ZAP:
import re raw = """Peter Punk [email protected] Nabuchodonosor [email protected] Ilias Magkakos [email protected] Nick Pipshow [email protected] Don Quixote [email protected] Crazy Priest [email protected] Fishroe Salad [email protected] TaPanta Ola [email protected] Laertis George [email protected] Thiseas Sparrow [email protected] Black Dreamer [email protected] Callme Daddy [email protected] Aggeliki Lykolouli [email protected] Kompinadoros Yannnnis [email protected] Serafino Titamola [email protected] Joe Hard [email protected] Bond James [email protected] Endof Text [email protected]""" with open("mails.txt", "w") as f: f.write('\n'.join(re.findall(r'[\w\.-]+@[\w\.-]+', raw)))
We add the list to the ZAP Intruder:
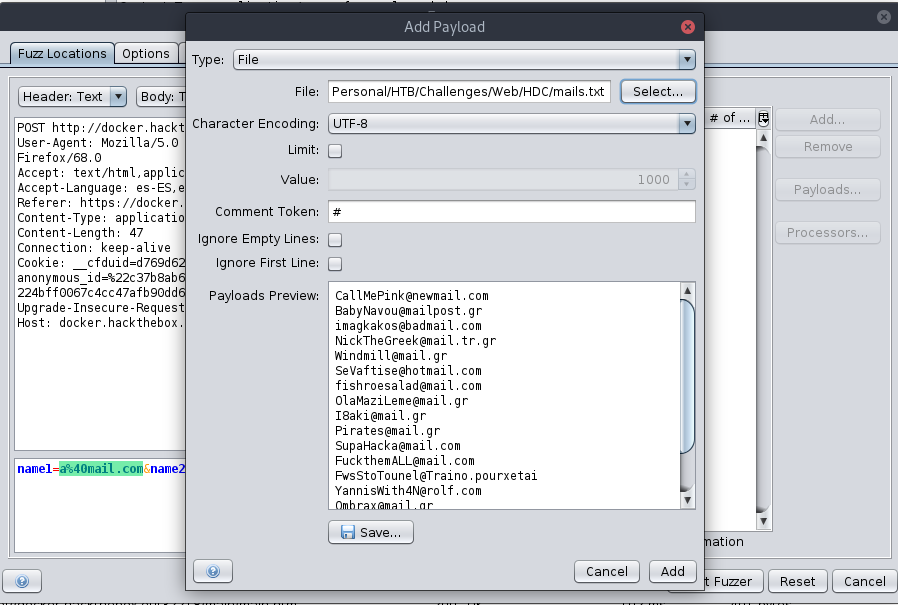
We execute the attack and order according to the size of the response. We do this to easily detect if the server responds differently to some requests.
We get a different answer with “[email protected]”
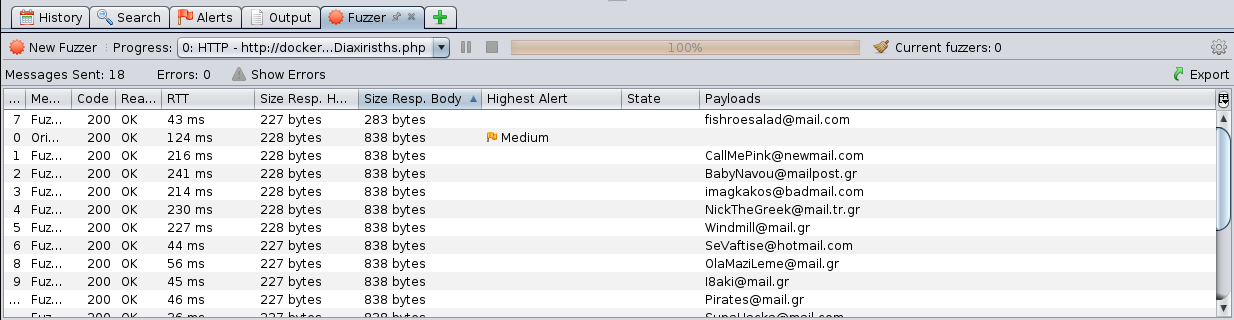
Let’s check the request output:
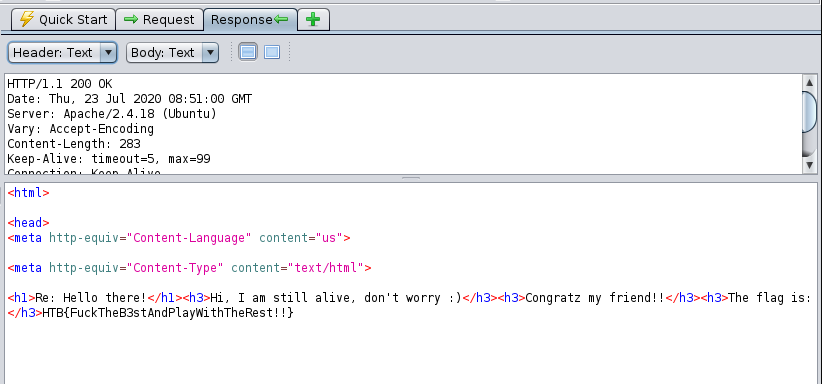
The flag is HTB{FuckTheB3stAndPlayWithTheRest!!}

 Español
Español





Learn how to hack wifi voucher
Learn how to hack wifi voucher